reaching firewall itself via ipv6
-
Sorry for the basic question but I'm another verizon customer who just got IPv6 working.
I understand that it is typical for the WAN interface to only receive a link local address where my LAN and VLAN interfaces get internet addressable addresses (beginning with 2600).
How would I reach the firewall itself from the internet i.e. for remote VPN access? If I use a dynamic DNS service, which address would be added to their database?
Thanks,
Devan
-
You should be able to use the LAN interface address.
-
That worked. Somewhat troubling that my entire network on IPv6 is addressable from the internet.
Is there an easy way to provide outgoing IPv6 access and limit ingoing requests? It seems that all the IPv6 tutorials say you need to allow all traffic on the interfaces with IPv6 clients.
-
@ddbnj All IPv6 connections from the internet are blocked by default. If they are passing it is because rules were placed to do so. This is no different than the IPv4 rules except that there is usually no NAT involved in IPv6 so there is one less step to making things work.
-
Thank you.
I tightened up the rule I got from the IPv6 hangout from jimp (2015). Changed source "*" to source LAN_net.
I estimate there's about 10,000 pfsense users who got IPv6 this week.
-
@ddbnj What rule are you talking about?
Any rule allowing connections in from the internet would be on WAN. Connections into WAN would never come from source LAN Net. If they did they are spoofed and should be blocked.
-
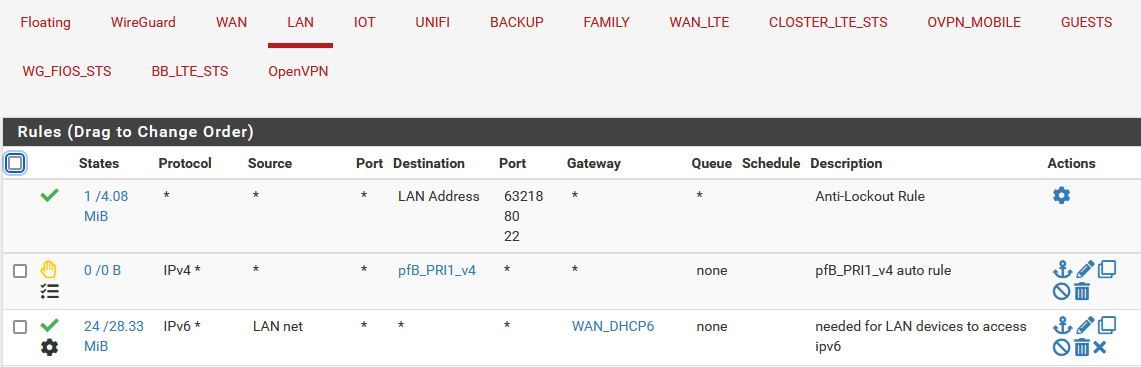
If I don't have that rule on LAN, the clients no longer have ipv6 access. Initially I had "*" as the source.
-
@ddbnj OK I get that but that is not enabling access from the internet. I probably misunderstood you here:
Somewhat troubling that my entire network on IPv6 is addressable from the internet.
It's addressable but connections will be blocked unless firewall rules pass them. Outbound connections (to the internet) are generally governed by LAN rules. Inbound connections (from the internet) are generally governed by WAN rules.
-
Thanks for the clarification. Since with ipv6, any device can be addressed, I did get a little confused as to which interface needed which rule. Frankly, no devices on my networks should accept anything from the internet. Only the firewall itself for wireguard and openvpn.
Since my ISP does not provide my WAN an IPv6 address, where do I place firewall rules to allow access to the firewall itself? Should I point vpn clients to the ipv6 address of the LAN interface as suggested from @JKnott
I just broke my dynamic DNS trying to point to the ipv6 address of the LAN.
Ugh.
Thanks
Devan
-
Your local LAN is not accessible, unless you allow it. PfSense is a firewall, which allows only what it's configured to allow. In your case, a rule allowing OpenVPN was automagically created, when you set up your VPN server.
NAT has caused a lot of people to really dumb down in that they don't understand how things are supposed to work. NAT was created to get around the IPv4 address shortage. Prior to that, IPv4 was used in exactly the same way as IPv6 is, though in the early days security wasn't as much of a concern. I used to work at IBM Canada in the late 90s. Back in those days, my computer at work had a static address, which I could reach from my home, as there was no firewall blocking it. At home, I didn't bother with NAT, until I had more than one computer, but only one public address.
Bottom line, with IPv6, we're no longer forced to hide behind NAT, which means every address is potentially reachable from the rest of the world and we use firewalls to limit that access.
-
@ddbnj said in reaching firewall itself via ipv6:
I just broke my dynamic DNS trying to point to the ipv6 address of the LAN
With many ISPs the IPv6 prefix is pretty much static, do you may not need dynamic DNS. Mine has survived replacing, at different times, both my modem and the computer I run pfSense on. I use a regular DNS server, for devices I want to be reachable from outside. As far as the outside world is concerned, there is no difference between your LAN interface and any other device on your LAN. They are all equally reachable, subject to firewall rules.
-
@ddbnj Depends on what they delegate to you. If it's a /56, take a /64 out of it and dedicate it to VIPs on the localhost interface. Then just tell OpenVPN to bind to that and pass the traffic to it into WAN.
-
Why assign a prefix to local host, when using the LAN address works?
-
Thank you for introducing me to some more tools.
Verizon provides a /56.
Never had the need to use VIPs before so that's something I'll have to read about tomorrow.
Can you bind any app to any VIP? Do I have to assign the VIP to an interface before I can bind openvpn to it? I don't think wireguard has a way to bind it to a specific interface. Too bad because that's the main site to site tunnel. Openvpn is a backup.
Take care,
Devan
-
@ddbnj said in reaching firewall itself via ipv6:
Since my ISP does not provide my WAN an IPv6 address,
Is that really the case? Do you have IPv6 working on LAN and don't have an address on WAN? Show it please, you have been wrong before.
-
I don't think you need to use a VIP for this. Just point the VPN server to your LAN interface. Any valid address on pfSense will work. In another thread, someone else mentioned my method worked for him.
-
@jknott Why not?
Nobody is saying your method will not work, but why not put services bound to addresses on the firewall in their own IPv6 interface "domain" disconnected from services off the firewall? One day you might want to, say, filter them differently. Maybe move that localhost /64 to another node.
So, Why not?
-
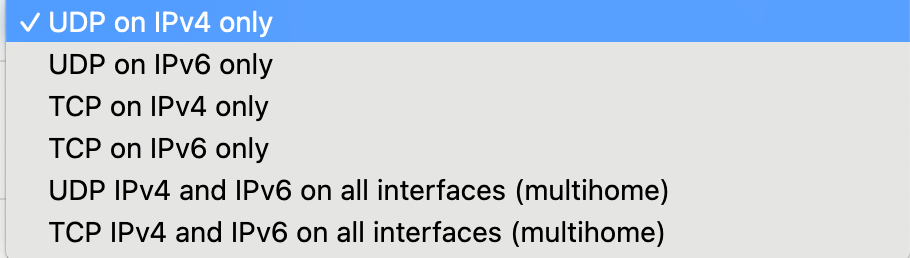
@ddbnj Well, with OpenVPN you have three choices:
Bind to a specific IPv4 interface address or IPv4 VIP
Bind to a specific IPv6 interface or IPv6 VIP
Bind to any address on the firewall.*The third method is the only way a single OpenVPN server can accept connections on both IPv4 and IPv6 addresses. So the 5th choice here...
-
@bob-dig said in reaching firewall itself via ipv6:
Is that really the case? Do you have IPv6 working on LAN and don't have an address on WAN? Show it please, you have been wrong before.
Yes, Verizon does not provide a global IPv6 address to the WAN interface. On their own routers, they use the "ff" prefix ID and assign a global address from that prefix to the WAN interface (usually ::1).
It had been thought that they might be using RFC 6603 (prefix exclude) for this, but a user in another forum with an OpenWRT router (which supports that RFC) said this doesn't appear to be the case, so we're not sure how they're picking that prefix for the purpose (might just be hard-coded in their routers).
I've basically done the same thing by putting a VIP on my WAN interface. It works, but if my prefix ever changes, I'll need to manually update the VIP with the new prefix.
-
@bob-dig said in reaching firewall itself via ipv6:
@ddbnj said in reaching firewall itself via ipv6:
Since my ISP does not provide my WAN an IPv6 address,
Is that really the case? Do you have IPv6 working on LAN and don't have an address on WAN? Show it please, you have been wrong before.
Thanks,
I didn't want to be wrong again.
Devan