Seemingly Unusual Port Forwarding
-
Been struggling with what seems like a very simple idea, but am getting no success. I need the pfSense firewall to forward port 502 requests from it's LAN interface to a WAN interface device (10.1.98.1, port 502) and then return any replies back to the LAN client. Other than that one need, the pfSense firewall should deny (but log) all other requests from WAN to LAN or LAN to WAN.
Network Layout
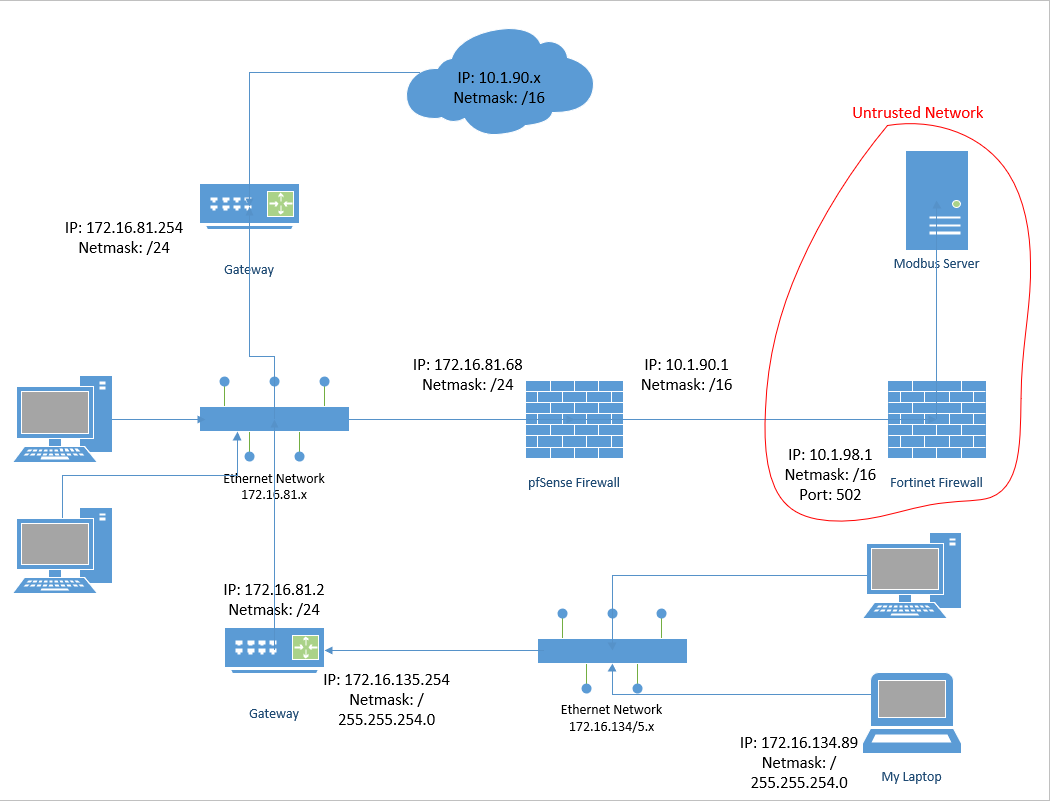
Constraints
- I have no control over network topology, IP addresses, or network configuration other than the pfSense firewall itself
- In the drawing, the network marked as "Untrusted Network" should have no access to any device on pfSense's LAN interface
- The entire network layout is all private networks, with no connectivity to the Internet
- There is another, main, 10.1.x.x network so using pfSense as a gateway to the Modbus Server on 10.1.x.x is out.
Safe Assumptions
- Fresh new pfSense install, with default installation settings, and I have complete control over how pfSense would be configured.
- The untrusted network functions correctly, since unplugging the ethernet cable from pfSense's WAN interface and into a temporary computer with the same 10.1.90.1/16 IP address allows me to ping and query the Modbus Server as required.
- In the drawing, the pfSense Firewall and the Fortinet Firewall are the only two devices on the 10.1.90.1/255.255.0.0 subnet
- I can get to pfSense's web GUI from "My Laptop" without issue.
- pfSense can successfully ping the Fortinet Firewall (10.1.98.1)
- Interestingly I cannot ping pfSense from "My Laptop"
Attempts so Far
- About a month ago I attempted to get some help from this great forum here, but never really resolved the issue. Been trying off and on for the past month without success. The lack of success, combined with a slight network topology change forced upon me has led me to a fresh post.
- Looked at pfSense docs and found the Example Redirect Port Forward for a Squid HTTP proxy. Seems very similar to what I need but unfortunately that method does not work for some reason.
- I've been through the Network Address Translation docs a few times now, still not finding that nugget of knowledge needed to get this to work.
-
If you can hit the pfSense webgui but can't ping it on the same IP then something it blocking that.
You said the firewall rules should block all other LAN to WAN traffic so that might be something you've set in pfSense but if not it's something in the gateway device in between.What is the default route at your laptop? At the gateway? In the Fortinet Firewall? The Modbus server?
Does pfSense have a route to 172.16.134.0/23 via 172.16.81.2?
If it doesn't then you may have some asymmetry happening on replies which may or may not be a problem. If the intermediate gateway is also NATing that won't be an issue. Since you can hit the webgui it probably isn't a problem but you should avoid it anyway.So you want to be able to enter 172.16.81.68:502 on your laptop and hit the modbus server?
You only need a port forward on the pfSense LAN to forward that traffic. You would also need an outbound NAT rule on the WAN assuming the Fortinet/Modbus have no route back to 172.16.x.x via pfSense? That would be usually be added by default in pfSense unless there is no static route and the intermediate gateway is not NATing. In which case you would need to add one for 172.16.134.0/23.
Add the port forward. Try to connect then check Diag > States. What states for port 502 have been created?
Steve
-
Outbound NAT was the key, thank you kindly.
I added an Outbound NAT for the WAN interface, with the Source set to Network (172.16.81.x). Translation was set to Address = Interface Address.
-
S SteveITS referenced this topic on