Port Forward LAN to WAN
-
Been playing with this for a few hours, and not getting very far. Reviewed the forums and found this forum post, but for some reason it doesn't work for me. Hoping for someone smarter than me to help guide me to the proper solution.
Summary:
Trying to accomplish this setup: Have a LAN client connect to pfsense firewall's port 502, and that connection is actually forwarded to a ModbusTCP Server on WAN network.Details:
Allow a LAN (172.16.81.10/255.255.255.0) client to connect to pfsense LAN interface (172.16.81.68/255.255.255.0) on port 502 for ModbusTCP communication. In other words client 172.16.81.10 would connect to pfsense 172.16.81.68:502. PFSense would then port-forward 172.16.81.68:502 to WAN device 10.1.98.1:502 by using its WAN interface (10.1.90.1/255.255.0.0)There are no other devices on the WAN other than pfsense WAN interface (10.1.98.1/255.255.0.0) and the ModbusTCP server (10.1.90.1/255.255.0.0).
The internet is not involved at all here as both the WAN and LAN networks are private networks. However, the WAN network is untrusted other than the singular ModbusTCP Server's port 502. Theoretically the untrusted WAN network could have another device connected in the future and we would not trust that device, hence the desire for a firewall to block all communications except those to 10.1.98.1:502 and back to LAN client.
PFSense Version: 2.6.0-RELEASE
Fresh PFSense installCannot use pfsense as a gateway, hence port-forwarding is seen as the only other viable option.
Network layout:
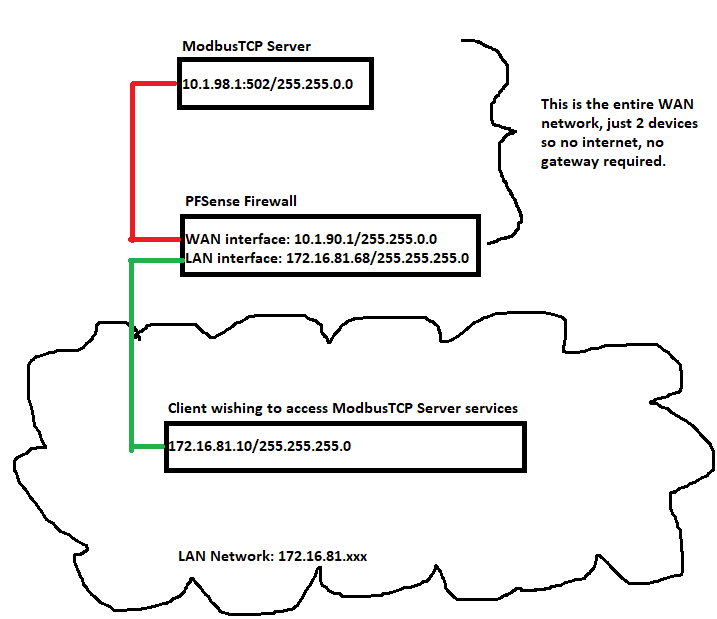
-
@mt_onsemi What you describe is what is done anyways on WAN, it will use outbound NAT...
-
@mt_onsemi
https://docs.netgate.com/pfsense/en/latest/recipes/modem-access.html -
@mt_onsemi said in Port Forward LAN to WAN:
PFSense would then port-forward 172.16.81.68:502 to WAN device 10.1.98.1:502 by using its WAN interface (10.1.90.1/255.255.0.0)
The pfSense WAN cannot communicate with the server as the IPs lies in different subnets.
Was thinking about a typo though, but your graphic shows the same IPs. -
@viragomann said in Port Forward LAN to WAN:
IPs lies in different subnets
No? The Mask is 255.255.0.0... :)
However, I don't see why NAT is necessary? Unless OP is trying to change port numbers...? The client on LAN should be able to connect directly to 10.1.x.x IPs.
IIRC, "Block private networks" doesn't even need to be unchecked on WAN because this is an outbound connection? On all the routers I have set up, I haven't needed to do anything to connect out to the ISP router private IP when bridging. Maybe that depends on how the ISP router is accomplishing that...
-
-
@steveits said in Port Forward LAN to WAN:
Unless OP is trying to change port numbers...?
NAT rule on LAN is actually mentioned in the docs:
https://docs.netgate.com/pfsense/en/latest/nat/port-forwards.html#traffic-redirection-with-port-forwards -
@SteveITS
I might be mistaken, and please correct me if I am, but for the LAN client to connect directly to 10.1.98.1:502 it would need to use the pfsense as a gateway the bridge the client's network (172.16.81.10/255.255.255.0) to the ModbusTCP Server network (10.1.98.1/255.255.0.0). I specifically cannot use pfsense as a gateway because:- there are other 10.1.x.x networks with gateways on the LAN, and clients are already using those gateways. I'd potentially have a more complex routing structure I'd like to avoid, not to mention the possibility of two 10.1.98.1 addresses in which case the client wouldn't know which gateway to use.
- most of the time the client will be a server that connects to 100's of different devices, and does not allow configuration of a different gateway for each separate IP address
-
@mt_onsemi Ah, I was assuming pfSense was the gateway. So yes you’ll need a NAT rule on LAN for that.
-
@mt_onsemi said in Port Forward LAN to WAN:
hence port-forwarding is seen as the only other viable option.
No not really, there are a few ways to skin this cat.
So you have this setup
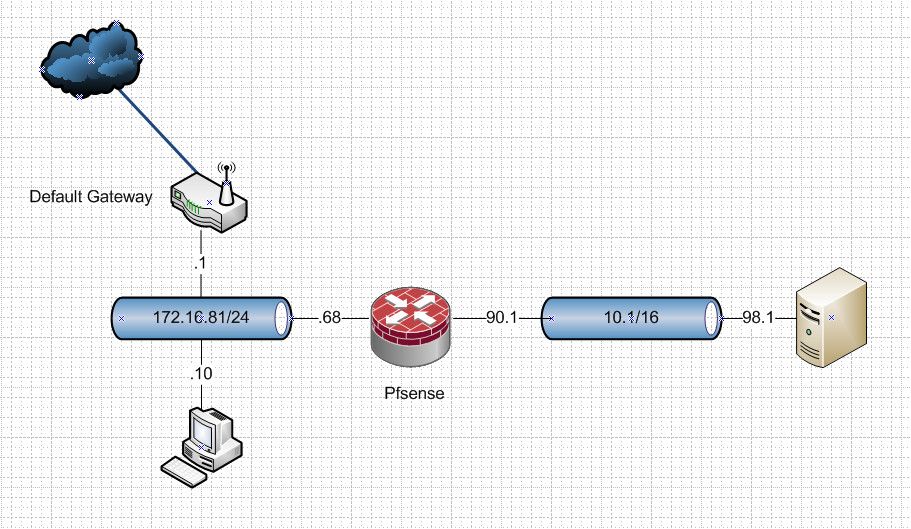
I really wouldn't call 10.1.90.1 interface pfsense "wan" a wan is something that is used to get to other networks, remote networks, like the internet for example. This 10.1/16 hanging off pfsense would really just be another network. So in your setup pfsense has no way to get to the internet? or will it leverage your lan router, shown on my drawing as the default gateway, and gave it an IP of 172.16.81.1 for reference only.
A cleaner setup would be to just use pfsense as your edge/default gateway. Why is it you can not just replace whatever your current router is with pfsense? And then just hang this 10.1/16 network off of it?
Or if whatever router this is can do more than 1 network, you could connect your 10.1 network there - so I am assuming this router is just some soho wifi router or an isp device that can do neither? Even if that was the case you could put pfsense behind it, even if double nat.. would be cleaner approach imho
Does this server at 98.1 not have a gateway set, if it pointed its gateway to pfsense at 90.1 all you would need is a simple port forward. If this server has no gateway then yes you would need a port forward, and also a nat so that this server sees the traffic from your 172.16.81.10 box as coming from the pfsense 10.1.90.1 IP.
If the 98.1 box pointed to pfsense as its gateway, you could remove any port forwards and or nats on pfsense and just setup a route oh the 172.16.81.10 box pointing 10.1/16 to pfsense 172.16.81.68 address.
There are multiple ways to skin the cat here, which one you use would be up to you. So more info on whatever this default gateway router you have now on your lan could be helpful in figuring out best way.
If it was me setting this up and had to use pfsense with an interface on your lan, this would be pfsense Wan IP, and the 10.1/16 would be pfsense "lan" This way pfsense could get to the internet for updates, or package installs, etc. I would set this server to use pfsense 90.1 as its gateway.. Now you could leverage internet access for this server as well, even if just for updates, etc. If you don't want the server to have internet, it would just be a simple rule on pfsense to stop it.
Then it would just be a matter of simple port forward on pfsense .68 interface.
-
@SteveITS
You are correct, pfSense is not the gateway. That's the hang-up I seem to get when talking with others to help resolve this. Everyone assumes pfSense is the gateway :)I have tried the NAT rule for LAN interface a few different ways with a few differnet configurations, all have failed. I know it's because I'm still new to pfSense, but superficially the various configuration I've tried all make sense to me so I'm at a loss as where to go next. Don't suppose you know of a reference I could look at, a wiki page I could review, or perhaps could give me a few detailed clues as to what exactly I would need to configure and how?
@johnpoz
You are correct in your network setup. The "Default Gateway" is actually on another IP address other than .1, but that's irrelevant to this conversation.I was thinking pfSense's 10.1.90.1 interface is a WAN because in my mind WANs are untrusted networks, and that's exactly what the 10.1.xxx.xxx network is. Perhaps my mental model of WAN vs LAN is incorrect. In my setup pfSense has no way to get to the internet, everything it sees and knows are private networks. You mentioned package installs and updates...no additional packages are anticipated to be needed and updates would be done offline. The firewall's entire job is to allow only ModbusTCP (ie port 502) through from the 172.16.81.xxx network to the 10.1.xxx.xxx network and back again. Everything else should be prevented. WebGUI access should only be via the 172.16.81.xxx network and not the 10.1.xxx.xxx network.
Unfortunately due to who owns what network (various different company entities own various different networks), it would take an act of God to move this 10.1.xxx.xxx onto the "default gateway" (in your picture it is 172.16.81.1). That "default gateway" is not owned by my group, so other than an IP address I have no knowledge nor access to its capabilities.
The server at 10.1.98.1 is not owned by my company, it is a product supplier's device. We are trying to access some process data on their systems, and ModbusTCP is a very simple protocol that is often used for this sort of work. However, because it is provided as-is there is very little configuration changes we can do, such as setting it up with a gateway.
I may be mistaken, but going through your various options seems to lead me back to the NAT port forwarding solution. However, I cannot seem to make it work. I know enough about networking to generally make things work, and hence be dangerous, but evidentally just shy of what's needed to get pfSense to work for me in this situation :( Either that, or it's a shortcoming in my knowledge of how to configure pfSense.
Finally, in an attempt to address your last comment. Because the ModbusTCP server (ie 10.1.98.1) is owned by one of our suppliers, we should not and indeed cannot provide it internet access for updates. That may compromise the suppliers system and/or may create bugs that come along with the updates. Perhaps it's easier to think of this setup as the following: the 10.1.xxx.xxx network consists of 2 devices with no access to any other network or device, ever. The 172.16.81.xxx network has other gateways on it leading to other networks, including another 10.1.xxx.xxx network. Additionally the 172.16.81.10 client cannot have a per IP address gateway assigned (the software package simply doesn't have this ability). Because of these latter two restrictions, I do not believe pfSense can act as a gateway for 172.16.81.10 and absolutely should not be acting as a gateway for 10.1.98.1 which would give product supplier access to our network, a no-no.
Do very much appreciate everyone's time and energy in helping to look at this one!
-
@mt_onsemi said in Port Forward LAN to WAN:
interface is a WAN because in my mind WANs are untrusted networks
While that is not untrue - it might not always be the case.. A wan is a network that allows you to get to more networks, wide area network..
If want to set it up how drawn, in the big picture doesn't really matter if either of those interfaces are pfsense "wan" or not. But your 10 network is wan, it really should work out of the box. The only problem you could be having is if no gateway set for pfsense as its gateway on its wan interface it might not actually bring that interface up, it would consider it down because it can't talk to gateway, especially if you do not even have one setup.
Here is what needs to happen for your connections to work.. On the 172 network interface you would have to setup a port forward sending whatever port you want to your 10.x server address. when traffic hits pfsense address on that interface, the .68
Now you need an outbound nat on the 10 interface that nats traffic to that interfaces address.
-
How many clients in the 172.16.81 network need to access the 10.1/16 ? If it's not many, why not just use a static route for them, and they connect using the real destination IP.
-
M mt_onsemi referenced this topic on