Captive Portal is broken?
-
Some colleagues have experienced this behavior (but I cannot confirm) :
It seems when a user open the captive portal page, the network access is blocked for others users, until this user is authenticated :- Already authenticated users were blocked (no ping)
- Another unauthenticated user had the captive portal auth page opened
- Once this user was authenticated, the network access was unblocked for the other users (the ping was OK)
-
@damiengombaultrecia said in Captive Portal is broken?:
Users reported losing network access randomly (no Internet, no ping, no gateway access).
Check you Wifi and cables used up to the pfSEnse portal NIC.
Or the NIC itself.
Dono what else to say as their is not much info ...@damiengombaultrecia said in Captive Portal is broken?:
This seems to happen at the same time on all interfaces with captive portal enabled.
You are using a multiple portals, each with an individual interface ?
@damiengombaultrecia said in Captive Portal is broken?:
It seems when a user open the captive portal page, the network access is blocked for others users, until this user is authenticated :
Can't reproduce this.
If opened a login page on my phone right now for the last 10 minutes or so.
Already connected portal users are not interrupted.
Btw : when you load a page, the connection is stopped as soon as the page is shown by the browser. When the browser posts back, because you entered login credentials and hit 'Enter', the server is contacted again with this info, a login happens (the users IP and MAC are added to the firewall). This does not (should not) influence other, already connected portal users.As shown above https://www.test-domaine.fr/munin/brit-hotel-fumel.net/pfsense.brit-hotel-fumel.net/index.html#portalusers
Btw : I used the classic Youtube captive portal video's from Netgate (old, but still useful).
I used FreeRadius for the accounting and authentication, but I don't really need to do so, the local pfSense user manager works fine. -
@gertjan said in Captive Portal is broken?:
Check you Wifi and cables used up to the pfSEnse portal NIC.
Or the NIC itself.
Dono what else to say as their is not much info ...There is no problem with Wi-Fi, cables or NIC.
It worked perfectly with 22.01, this problem happened with the 22.05 upgrade.
The network accesses are unblocked immediately when the captive portal is disabled.
The interfaces/networks without captive portal works normally when this problem is triggered on interfaces/networks with captive portal enabled.The captive portal is now disabled and it works normally.
@damiengombaultrecia said in Captive Portal is broken?:
You are using a multiple portals, each with an individual interface ?I have multiple interfaces, some with captive portal enabled, some without captive portal.
I have 3 captive portal zones on 3 interfaces, with LDAP auth.@damiengombaultrecia said in Captive Portal is broken?:
It seems when a user open the captive portal page, the network access is blocked for others users, until this user is authenticated :
Can't reproduce this.
If opened a login page on my phone right now for the last 10 minutes or so.
Already connected portal users are not interrupted.
Btw : when you load a page, the connection is stopped as soon as the page is shown by the browser. When the browser posts back, because you entered login credentials and hit 'Enter', the server is contacted again with this info, a login happens (the users IP and MAC are added to the firewall). This does not (should not) influence other, already connected portal users.As shown above https://www.test-domaine.fr/munin/brit-hotel-fumel.net/pfsense.brit-hotel-fumel.net/index.html#portalusers
Btw : I used the classic Youtube captive portal video's from Netgate (old, but still useful).
I used FreeRadius for the accounting and authentication, but I don't really need to do so, the local pfSense user manager works fine.I hadn't time to diagnose, I cannot confirm what I have said before, this is just some elements told by my coworkers.
I can live with the captive portal disabled.
It's difficult to reproduce because I can't enable the captive portal again because it blocks network access for a hundred people multiple times a day.Lots of thing have changed with captive portal (ipfw replacement with pf) with 22.05.
It may be a bug with pf rules generation with captive portal enabled.Another user on Reddit (https://www.reddit.com/r/PFSENSE/comments/x0f43m/captive_portal_is_broken/) also said :
"It is hilariously broken, if a user on my network signs on to the CP it takes my whole network down."The 22.05 version is recent.
The captive portal/pf/iwfp changes is not yet on the released opensource version 2.6.0, it will be in 2.7.0.
I will wait the 2.7.0 be released, I think more users will have this problem. -
@damiengombaultrecia Hi, the same happen on my sites. How to troubleshoot this?
-
@georgecz58 said in Captive Portal is broken?:
troubleshoot
It exists. Here it is : Troubleshooting Captive Portal.
Start by installing the System_Patches pfSense package 2.0_6. It permits you to apply changes that are made avaible without having to wait for the next release.
Some patches are already prospoed in the System_Patches upon upgrade of this package. Other can be obtained as they are created (source : this forum, redmine or Github).Take note : as of today, September 1st, there are no available patches for 22.05.
As said already above, I've added one patch.
Read about here https://redmine.pfsense.org/issues/13323
This is the patch I used as a patch ID : https://github.com/pfsense/pfsense/commit/add6447b9dc801144141bb24f8c264e03a0e7cae.patchThis patch is useful when you have to add 'bypass' MACs.
I'm not using those right now on my portal.True, some functionality doesn't work well or not at all.
See here : FreeRadius and quotas, doesn't work since 22.05 and if you use multiple portals (thus multiple interfaces) : Problem with multiple Interfaces since Version 22.05
For the last issue, there is a redmine present - and isn't even a patch proposed : just edit the file ( add a dot somewhere ;) )I know it's easy to say that the captive portal doesn't work.
Keep in mind it's also easy to say it works. Just have a look here : https://www.test-domaine.fr/munin/brit-hotel-fumel.net/pfsense.brit-hotel-fumel.net/index.html#portalusersThe connected users are not my kids, neither my family, neither my collogues. I even never meet most of these people, I don't know what devices these people uses. I just trust they can find our SSID : 'myhotel', connect to it and that the captive portal login page shows up.
They can enter a 3 digit room number - and a password that is shown in the room.
And that's all. People can use our captive portal.It doesn't "break" my company network, which lives on other local networks like 192.168.1.1/24 and 192.168.3.1/24. Why should it ?
My portal configuration is a little bit above 'bare minimum' as I choose to use a https portal login page. This needs a domain name for local usage, and the pfSense acme package.
It's a bit silly to protect the connection to portal web server this way, as no sensitive information is to be hidded : the password and room number are nearly public info. IPs used are RFC1918.
The thing is : most browsers want a trusted (= trusted web server certificate) https connection these days. They will yell when a http is used.I'm using also the FreeRadius package and a mysql server 'scratch-pad' because "why not ?". For my usage, I can very well use the local pfSense user manager, making my pfSense system way easier to maintain.
I've mentioned the "classic Youtube captive portal video's from Netgate" above.
With the instructions from these videos, you should have a captive portal working.
If not .... well, the trouble shoot page should tell you that your DNS setup isn't what you want for a captive portal.
The pfSense default DNS setup - is mandatory - if you want the portal to work.The captive portal trouble shoot page should be used to troubleshoot ;) If you find a something not clear, then that info should be used to post questions here.
Questions with details, of course.Details are needed, so the cycle "you say it doesn't work" and "I say it does work" can be broken.
Otherwise I have to come over and redo your portal setup myself and call it a day. ( I'm joking of course).
Keep in mind : we all use the same software. Only our settings are different. -
Hi.
Some bugs related to captive portal with version 22.05 were reported on the pfSense Redmine issue tracker.
The most interesting one is : https://redmine.pfsense.org/issues/13488Captive Portal: All users are given the same dummynet pipe pair
The reporter tells :[...]
It also means that when a user is disconnected the pipe pair is deleted and all users are unable to pass traffic.
This can happen either via a manual disconnect or via a timeout.
This actually affects all users with or without bandwidth limiting set.
When there is no limit set all user are passed through an unlimited pipe but that still gets removed when one user is disconnected. -
Yep, that was this one ( see above ):
@gertjan said in Captive Portal is broken?:
See here : FreeRadius and quotas, doesn't work since 22.05 and if you use multiple portals (thus multiple interfaces) : Problem with multiple Interfaces since Version 22.05
For the last issue, there is a redmine present - and isn't even a patch proposed : just edit the file ( add a dot somewhere ;) ) -
is there a Patch available?
-
No official patches as of today.
If needed do the editing yourself. -
what i have to edit? i cant find it :=)
-
@opit-gmbh said in Captive Portal is broken?:
i cant find it :=)
Scroll upwards, see the second post if this thread for the 'bas switch!' patch.
See this one for another patch.Also look post number 12.
You will have to edit the /etc/inc/captiveportal.inc to apply it.If you do not use (FreeRadius) quotas, don't bother patching.
-
and which one should i use? Iam not using any Radius Setup. Just Bandwidth limitations...
-
Open this file : /usr/local/captiveportal/index.php and locate this line ( around line 251)
$pipeno = captiveportal_get_next_dn_ruleno('auth', 2000, 64500, true);change true for false :
$pipeno = captiveportal_get_next_dn_ruleno('auth', 2000, 64500, false);save.
Now, pipes are working per user as it should be.
Btw : this my quick and dirty hack. I'm using this 'false' for several weeks no : it works.
I see now Limiters and Schedulers per user under Diagnostics >Limiter Info.
-
THX, it seams to work.
Limiters:
02002: 2.048 Mbit/s 0 ms burst 0
q133074 100 sl. 0 flows (1 buckets) sched 67538 weight 0 lmax 0 pri 0 droptail
sched 67538 type FIFO flags 0x0 16 buckets 0 active
02003: 2.048 Mbit/s 0 ms burst 0
q133075 100 sl. 0 flows (1 buckets) sched 67539 weight 0 lmax 0 pri 0 droptail
sched 67539 type FIFO flags 0x0 16 buckets 0 active
02000: 2.048 Mbit/s 0 ms burst 0
q133072 100 sl. 0 flows (1 buckets) sched 67536 weight 0 lmax 0 pri 0 droptail
sched 67536 type FIFO flags 0x0 16 buckets 0 active
02001: 2.048 Mbit/s 0 ms burst 0
q133073 100 sl. 0 flows (1 buckets) sched 67537 weight 0 lmax 0 pri 0 droptail
sched 67537 type FIFO flags 0x0 16 buckets 0 activeI see here 4 Limiters but i just have 2 Captive Portal Users, is this OK? Is this because one is for Upload and one for Download or?
-
@opit-gmbh
For each user, one down and one upload limiter. -
cool thx.
here is my Patch what iam using under System > Patches
diff --git a/opit/usr/local/captiveportal/index.php b/opit/usr/local/captiveportal/index.php
--- a/opit/usr/local/captiveportal/index.php
+++ b/opit/usr/local/captiveportal/index.php
@@ -249,7 +249,7 @@
$context = 'first';
}- $pipeno = captiveportal_get_next_dn_ruleno('auth', 2000, 64500, true);
- $pipeno = captiveportal_get_next_dn_ruleno('auth', 2000, 64500, false);
/* if the pool is empty, return appropriate message and exit */
if (is_null($pipeno)) {
$replymsg = gettext("System reached maximum login capacity");
-
@gertjan said in Captive Portal is broken?:
Hi, I'm using 22.05 on a SG 4100. In the past, I was using 2.6.0 on a home made pfSense device.
If my captive portal wasn't working, I would lose my job - sort-of, as I use the portal for a hotel.
Last time I looked, it worked.
I'm using a dedicated interface for my portal, and as LAN has already 192.168.1.1/24, my portal uses 192.168.2.1/24 - DHCP pool 192.168.2.5 -> 254.
I use the Resolver, nearly default settings.
The pfSense patches packages has one patch for the portal :
This is the patch ID to be used : https://github.com/pfsense/pfsense/commit/add6447b9dc801144141bb24f8c264e03a0e7cae.patch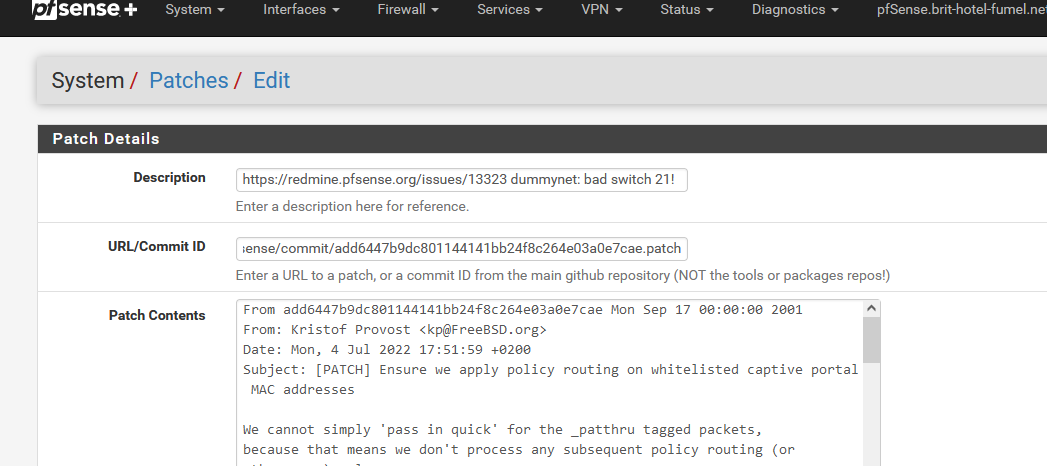
after install patch - same error
dummynet: bad switch 21!
dummynet: bad switch 21! -
O OpIT GmbH referenced this topic on
-
O OpIT GmbH referenced this topic on
-
O OpIT GmbH referenced this topic on
-
O OpIT GmbH referenced this topic on
-
O OpIT GmbH referenced this topic on
-
O OpIT GmbH referenced this topic on
-
O OpIT GmbH referenced this topic on
-
O OpIT GmbH referenced this topic on