Creating Separate Network for VOIP Traffic
-
Just to preface this post, I have been in IT for almost 18 years, but I am relatively new to PFSense. I have been using NGFirewall (Untangle) for years but am unhappy with the recent sale to Arista and the direction that software is headed. So I am attempting to move all of my clients to PFSense. Just so happens, I started with my most complicated one first.
So the NGFirewall box in production has 4 ports.
eth0 - WAN - (Public IP)
eth1 - LAN - 192.168.22.0/24
eth2 - VOIP - 192.168.2.0/24
eth3 - not usedBoth the eth1 and eth2 have access to the web are isolated from each other. They also both have their own DHCP servers for their networks.
The PFSense box I am using is installed on a small firewall appliance with 6 network ports.
em0 - WAN
em1 - LAN
em2 - VOIP
em3-5 - not usedHow to I setup a DHCP server for em2?
How do I route traffic from em2 to em0 and keep it isolated from em1?Thank you in advance for your time!
-
DHCP.. Go to Services- DHCP Server. Choose your interface on the tab at the top under the header.
Interfaces...
All interfaces will route between each other by default.. Control their activity with firewall rules. Firewall rules parse from the top down.
Deny Rule- source- Interface 2 destination interface 1.
Allow Rule- Souce- Interface 2.. Allow all
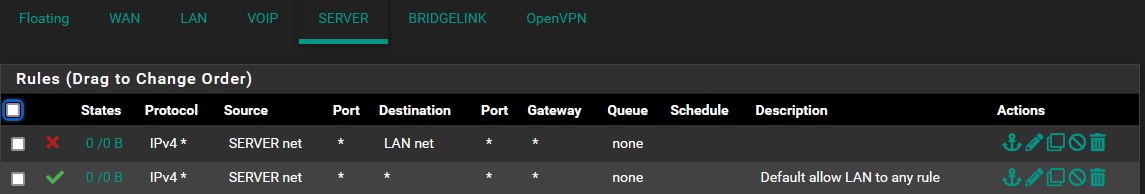
-
Or-
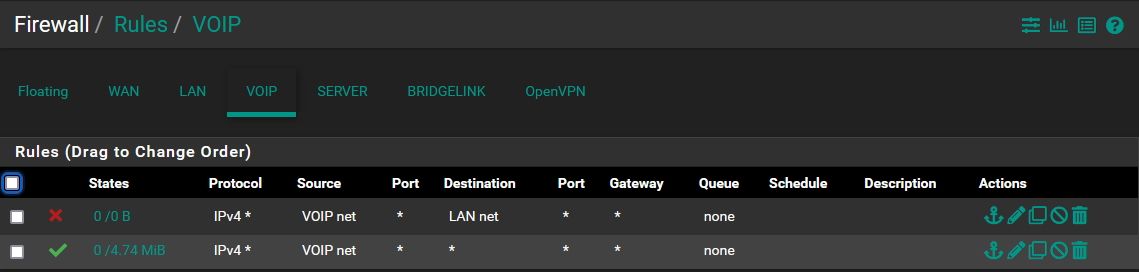
-
@chpalmer said in Creating Separate Network for VOIP Traffic:
All interfaces will route between each other by default.. Control their activity with firewall rules. Firewall rules parse from the top down.
All interfaces will NOT route between each other by default.. Control their activity with firewall rules. Firewall rules parse from the top down.
LAN is the only interface will a default allow any rule.And it wouldn't be the OR unless you want the LAN to access the VOIP.
Rules are applied to the inbound traffic on all interfaces. So if you want to block traffic from voip to lan and from lan to voip you need the deny rules placed on both interfaces.
-
I just found my first mistake when setting this up. When I setup my static IP for the VOIP LAN, I set the correct IP but 32 bit subnet mask. Upon doing so, the DHCP option wasn't available for that plug. Once I fixed it, the tab in DHCP appeared. I guess I was thinking too far ahead instead of paying attention to what I was doing.
Now the firewall rules. I will set them and see what I get.
-
@jarhead said in Creating Separate Network for VOIP Traffic:
All interfaces will NOT route between each other by default.. Control their activity with firewall rules.
It’s probably semantics but I would say the routing is automatic in that one doesn’t need to manually configure routes.
However the default firewall rules block from all “not the LAN” interfaces to any so as you noted traffic isn’t passed by default.
@RutReturns The /32 gets people sometimes, you’re not the first. Not sure what the argument is for not using /24, perhaps because in many cases /24 is wrong and it could be way too wide. Remember pfSense doesn’t know if you’re configuring another local network or a second WAN. But, glad you caught it.
-
OK so the routing rules DO NOT allow ANY traffic without rules. I couldn't even ping the VOIP IP on PFSense (192.168.2.1)
I had to set a rule to allow all traffic : Any protocol, IPv4+6, from VOIP NET to ANY destination.
That rule allowed traffic to start flowing on the VOIP network and to the web. It also allowed traffic back and forth to the LAN so I had to set 1 rule on the LAN NET to Block all traffic to VOIP NET.
Then I set another rule on the VOIP NET to block all traffic to the LAN NET.
This left all traffic flowing freely back and forth from LAN or VOIP to WAN but blocked all traffic between LAN and VOIP.
This was exactly what I was after!
Thank you all for your input!!
-
@rutreturns If you take it another layer down, if you want to prevent VOIP from accessing the pfSense GUI you could make a rule blocking from VOIP to “this firewall” (alias for all its IPs) ports 443, 80, 22. But allow DNS TCP+UDP.
-
In this client's office I have another scenario that I was just thinking about. In the building there are 2 separate offices. Both have their own complete networks but share a single server closet. Both networks are setup the same with similar hardware.
1 server room
1 server rack
2 servers
4 network switches (1 LAN and 1 VOIP for each)
2 firewalls
2 ISP connectionsAlthough they work as separate offices, they do sort of work together. For ease in the initial setup, I just used OpenVPN to connect the two offices together. It is funny though because their firewalls literally sit 2 ft apart mounted to the wall.
So, in this routing stuff we were doing for VOIP NET, it made me wonder if I could do the same thing on the backside to connect the office together without the overhead of a VPN.
Firewall 1
eth0 - WAN (Public IP)
eth1 - LAN - 192.168.22.1/24
eth2 - VOIP - 192.168.2.1/24Firewall 2
eth0 - WAN (Public IP)
eth1 - LAN - 192.168.44.1/24
eth2 - VOIP - 192.168.4.1/24Plug in eth3 from firewall 1 to firewall 2
Then set up eth3 on both like...
Firewall 1
eth3 - TOBIZ2 - 192.168.44.2/24Firewall 2
eth3 - TOBIZ1 - 192.168.22.2/24If I created rules on both sides to allow all traffic from eth3 to ANY, and blocking rules from eth3 to VOIP and block eth3 to WAN, do you think that would work?
The default gateways would stay the same on each side so hopefully each LAN would know to use their .1 to access WAN but will traffic pass to eth3?Has anyone tried this? Will it even work?
-
Yes, you could certainly route between the firewalls. But you need to use a separate transport subnet between the two firewall interfaces and then add gateways and static routes between them.
That way you avoid asymmetric routing and can properly filter traffic at both ends.If they have separate ISP uplinks you can also setup each as a failover for the other.
Steve