Block access to web GUI through external IP from guest net
-
Hi!
I have a pfsense router with multiple WAN:s & LAN:s. It works as expected, except for this one problem...
When I log on to for example the guest network and try to access the web GUI by writing the routers local IP for that LAN, I'm getting a connection refused error. Which is exactly what I expect. But when I instead write the external IP of that LAN I'm presented the web GUI...? I've tried to block access to the WAN_address through the firewall but it doesn't seem to make any difference...?
I also want to mention that I can't access the web GUI directly through WAN. It is only when I'm connected through a local network that I can access it through the WAN address.
But I've had problems when accessing services hosted locally on a different LAN through the firewall as it redirects to the routers IP address, as it sees that it is 'its own address'. I'm guessing that it is a similar problem here? Earlier I solved this by having different DNS records for the local network and WAN. So the local records pointed directly to the local IP address of the server that hosted the service, instead of pointing to the router. But that won't work here...
Thanks in advance!
Tell me if you need to know anything else!
Best regards
-
@a_nice_fella
pfSense has a nice variable "This Firewall", which includes all its interfaces IPs and can be used in rules.So best practice is to add a reject-rule for the destination "This Firewall".
To block any access, but the necessary port, add all desired ports into an alias and use this one in a pass rule above of the reject.
-
Hi! Thanks for your reply!
I've tried this before and I've just tried it again just to double check! This time I changed the action from reject to block and I now I don't get a rejected message in the browser when I access the web GUI through its local address. Which tells me that the rule in itself is working. But it still works when I access it through the WAN address? Is this a bug or could I be doing something wrong?

I added this rule to the guest VLAN maybe I should add it to another VLAN/interface?
-
@a_nice_fella said in Block access to web GUI through external IP from guest net:
But it still works when I access it through the WAN address?
Works here as expected.
Is this "WAN address" really assigned to pfSense itself or is it assigned to another router in front of it?
-
@viragomann
I have no other router than pfsense, so that can't be the case. But the WAN addresses are set through DHCP, don't know if that could cause any problems with this?
-
@a_nice_fella
Just tested it on my home pfSense, it's 2.6.0 and has a PPPoE WAN.
I've have a floating Quick reject rule on all interfaces, from which I want block access to my firewalls webGUI.I tried it from my phone. It is connected to one of these subnets, but which has any access is allowed from, except private IPs. But Access to the WAN IP (public) web configurator port is not possible. So it works as expected here.
Maybe someone else with a DHCP WAN can also test this. But I don't think, that there is a really bug with DHCP IP not included into the "This firewall" variable.
-
@a_nice_fella said in Block access to web GUI through external IP from guest net:
But the WAN addresses are set through DHCP
Which means the upstream DHCP server gives an IP, and a network.
The IP is known as your pfSense WAN IP, and that IP address is part of the the known WAN-network. Both are communicated by the DHCP server to the DHCP client. The 'network' is a range of IP addresses. WAN does not stand for the entire Internet, which is more something like 'any'.An guess what : pfSense has some predefined aliases that represent these networks :
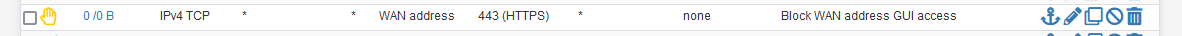
In this case, as 443 is my GUI access port, connected users from the network where this rule is place, can't use any WAN network address, and this includes the pfSense WAN address IP, whatever it is : if it was set statically by you, or assigned by DHCP.
Btw : you can also use the predefined 'This firewall (self)' which is everything in this list - except 'any'/'Single host/'/'Network':
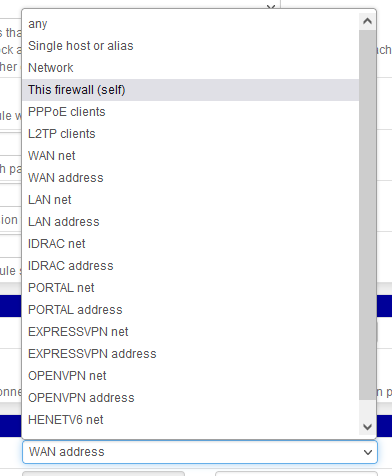
-
Thanks for your help!
Managed to solve it with a floating firewall rule! I only tried to block it from the interface that I thought the traffic originated from first. But now I tried to add a floating rule that blocked the traffic from all interfaces that shouldn't have access to it, and it worked!