Problems with pfSense IPV6 DNS function (does it exist!?)
-
I agree that it sounds like that .... however
- I do not have ACL's
- I am not aware of any rules blocking explicitly the local DNS
- When doing a query from the same PC via the same vlan to using the same gateway
It works when I specify cloudfare and it does not work if I specify the local GW .....
If I do the test again, I see that the pass rule count is +1
If I activate logging for that rule
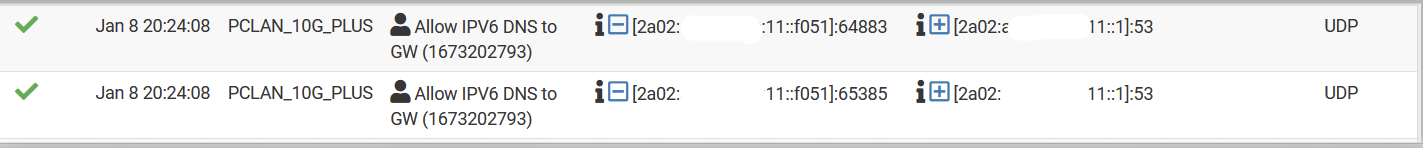
So somewhere is a problem, but where ...
-
-
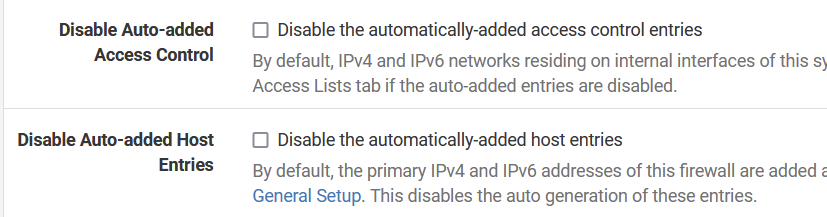
@louis2 they are auto created then for you - which maybe some issue with the auto created IPv6 rules.

I disable auto acls - I like to set my own. But if your getting refused in your query that points to your source IP not being in the ACL - that is the only reason off the top of my head that would cause unbound to send back refused.. But I am quite a few beers into watching football ;) hehehe
-
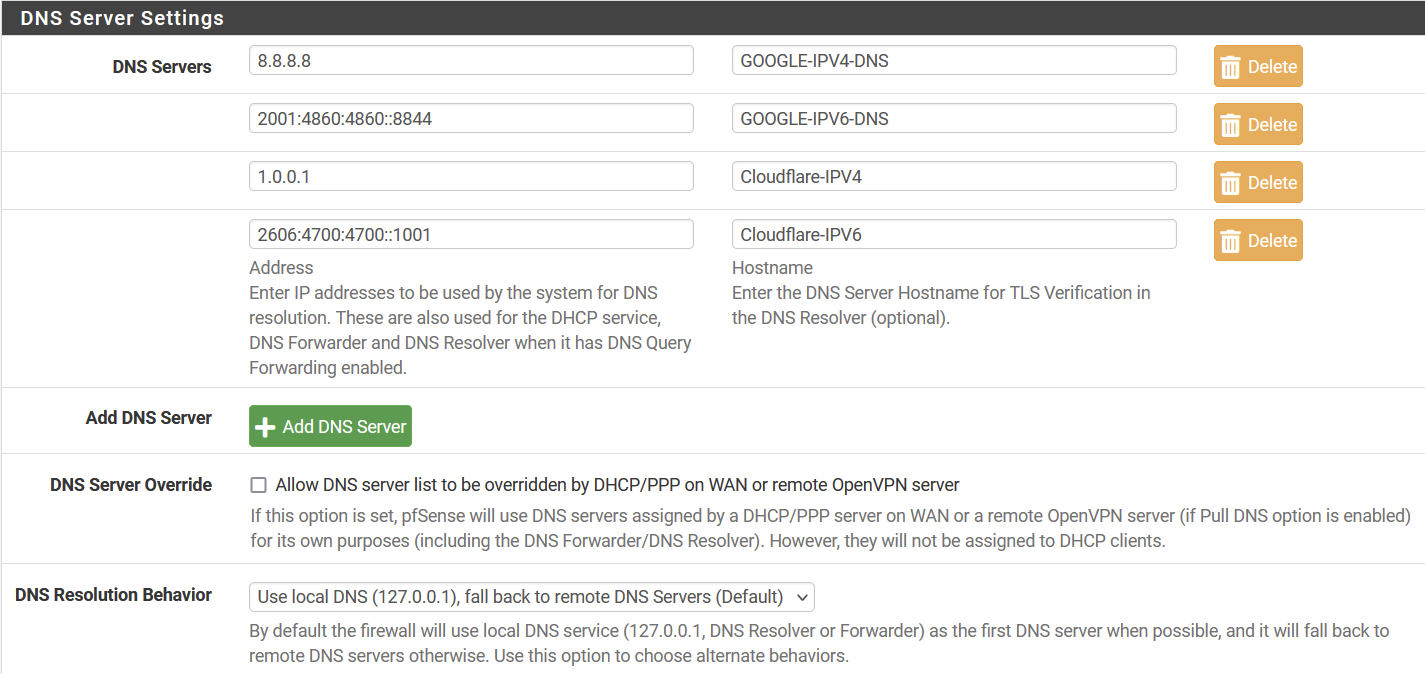
I left the related settings default and that works for IPV4. Perhaps not for IPV6

From the manual
Unbound requires access lists (ACLs) to control which clients are allowed to submit queries. By default, IPv4 and IPv6 networks residing on internal interfaces of this firewall are permitted. Additional networks must be allowed manually.And that is exactly what I did expect !! And since that is also what I do intent, there was never a reason to touch this!
Perhaps I will test what happens when I explicitly enable the test ranges, what is not OK / not the intention of course .....
-
@louis2 possible your IPv6 changed or something... If it works with you creating a specific acl for your IPv6 - then we can dig into why the acl was not created, etc.
Did you actually validate its listening on your specific IPv6 address? But refused really points to no acl that allows your query.
I have never used the auto acls - I have always had it disabled, because I create my own acls ;)
-
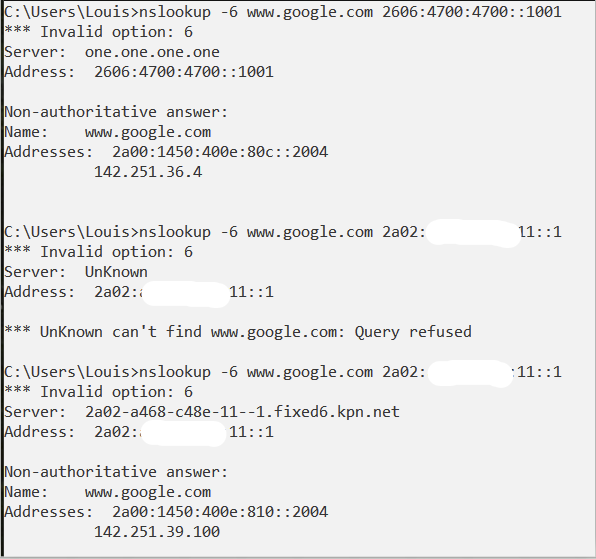
It is clear the DNS ACL's are the problem!
Below you see three tests:
- using cloudfare DNS
- using the pfSense GW without explit ACL
- using the pfSense GW with an ACL added
So its a bug
Also note wonder
- if these ACL's are implemented via unbound
- or that it is in a normal FW-rule ... under the surface ......
-
Hum, I was looking for the config files below the DNS ...
Found /etc/resolv.conf
nameserver 127.0.0.1
nameserver 8.8.8.8
nameserver 2001:4860:4860::8844
nameserver 1.0.0.1
nameserver 2606:4700:4700::1001
search lanfind / -name unbound.conf
/var/unbound/unbound.conf
/usr/local/share/strongswan/templates/config/plugins/unbound.conf
/usr/local/etc/strongswan.d/charon/unbound.conf
/usr/local/etc/unbound/unbound.confWhere /var/unbound/unbound.conf turned out to be the used config ...
The content of the /var/unbound/remotecontrol.conf
remote-control:
control-enable: yes
control-interface: 127.0.0.1
control-port: 953
server-key-file: "/var/unbound/unbound_server.key"
server-cert-file: "/var/unbound/unbound_server.pem"
control-key-file: "/var/unbound/unbound_control.key"
control-cert-file: "/var/unbound/unbound_control.pem"I will create a bug report, referring to this thread
-
@louis2 said in Problems with pfSense IPV6 DNS function (does it exist!?):
So its a bug
Users always jumping on the its a bug wagon..
What version of pfsense are you even using? Are you using 2.7 or 23.01 beta? Or stable release?
-
My actual version is 2.7 built on Fri Jan 06 06:05:17 UTC 2023
And even if the problem is only related to the 2.7 build, it is still a bug / something to be fixed.
-
@louis2 said in Problems with pfSense IPV6 DNS function (does it exist!?):
it is still a bug / something to be fixed.
What snap are you on - for all we know it was already taken care of.. Your whole thread should of been in the dev section if your using a snapshot/beta..
I agree it needs to be corrected if it an actual problem - but before going taking the time to report a "bug" I would bring up your issue in the dev section for 2.7, what snap are you using, etc.
edit: should prob move this whole thread to here
https://forum.netgate.com/category/88/ce-2-7-0-development-snapshots
And you can add what snapshot your on, and see if anyone else seeing the problem - then they can fix it, etc. For all we know it was a temp issue on your specific snap
edit: I moved this thread to 2.7 dev - could you post up your snapshot version your using, and update to the current snap and validate it still an issue with auto acls adding IPv6, etc.
-
 J johnpoz moved this topic from DHCP and DNS on
J johnpoz moved this topic from DHCP and DNS on
-
I do not know if the problem is only related to the 2.7 release. Perhaps I doubt.
I also did not know if I did something stupid or that it was a bug in first instance.
But If you think it should be in the def section two things:
- be so kind to test first if it does work on a stable release
- and if so be my guest move this thread to the dev section, that is something I can not do
-
@louis2 I have moved it.. If it was an issue with stable I would think would of been reported long ago.. But sure I can test it on my 2.6 vm install and my 22.05 main setup.
-
Not related .... but :
These are not comment fields for you own usage.
If you fill them in, use the real host name.
To find out :[22.05-RELEASE][root@pfSense.wth.net]/root: host 1.0.0.1 1.0.0.1.in-addr.arpa domain name pointer one.one.one.one. [22.05-RELEASE][root@pfSense.wth.net]/root: host 8.8.8.8 8.8.8.8.in-addr.arpa domain name pointer dns.google. etc. -
@louis2 I'm having the same problem with dev plus 23.01 and dev CE 1/06.
When using DNS Resolver (Enable Forwarding Mode on and off) to the LAN ipv6 address I get a query refused. ipv4 LAN address works fine
If I switch to DNS Forwarder both ipv4 and ipv6 return results as expected.
The symptoms I first noticed was, when loading sites in chrome I would get dns_probe_finished_nxdomain for 2-3 secs and then the site would load. ios and andriod devices would have problems too.
My setup is pretty much default.
-
@cursixx you get a refused returned or dns just fails? Refused is indication that acls are not allowing your query, fail or timeout would point to possible other issue. I do believe there has been some issues related to unbound and using IPv6 in general.
-
@johnpoz yes unbound returns "query refused" only with ipv6 LAN address as the DNS. I'm not sure when this started but it has been going on for at least a few weeks for me. I update dev just about everyday but switch back to stable from time to time.
Anything you want me to test with this?
-
Thanx! I did enter that a while back not reading, just assuming what should be there

At this moment I doubt a bit about what should be there
- 1.0.0.1.in-addr.arpa or
- one.one.one.one. (with or without ending dot !?)
For now I defined it as shown in the picture below.
nslookup one.one.one.one. with and without dot function both !??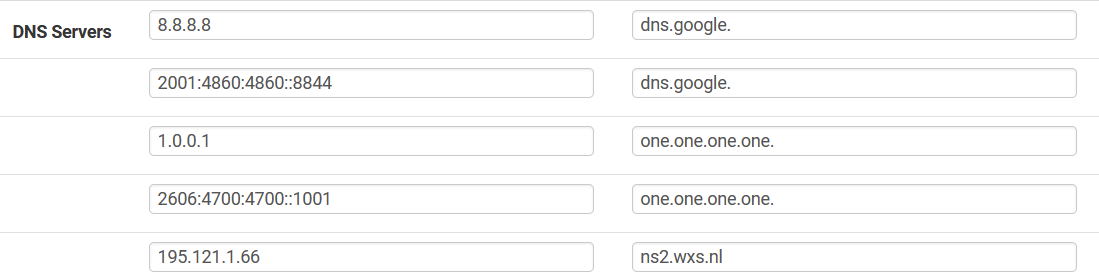
-
@cursixx said in Problems with pfSense IPV6 DNS function (does it exist!?):
Anything you want me to test with this?
If you use unbound without pfBlockerng-devel, you could set Services > DNS Resolver > Advanced Settings log level to 4, 5 or even 6.
Be careful : don't leave your system in this sate forever. unbound now start to log a lot (like a huge load of a lot) log lines. These will get rotated very often, but still, see this as a test - and stay onto it.
Or, if you have unbound and pfBlockerng-devel, and you use the python mode, : go here : Firewall > pfBlockerNGLog > Browser and select the dns_reply.log.As soon as you detect an issue, go check the log file and see if unbound received the DNS request (you have the domain name, so search for it) and see what unbound received the request, and what it did with it.
Check also your device's IPv6, which should match with what you find here : /var/unbound/access_lists.conf
Example :
I used nslookup to resolve :nslookup www.google.es. 2001:470:1f13:beef:2::1where 2001:470:1f13:beef:2::1 is the LAN IPv6 of my LAN.
In the dns_reply.log I saw :DNS-reply,Jan 9 16:29:34,reply,A,A,300,www.google.es,2001:470:1f13:5c0:2::88,74.125.140.94,US DNS-reply,Jan 9 16:29:35,reply,AAAA,AAAA,300,www.google.es,2001:470:1f13:5c0:2::88,2a00:1450:4007:81a::2003,IEand that was correct, nslookup was asking for the A and the AAAA.
@louis2 said in Problems with pfSense IPV6 DNS function (does it exist!?):
nslookup one.one.one.one. with and without dot function both !??
Look in the dns_reply.log file and you have you answer ;)
When you do a :
nslookup somethingspecial.tldYou will see this (these) line(s) :
DNS-reply,Jan 9 16:36:43,reply,A,SOA,3600,somethingspecial.tld.my-pfsense-local-domain.net,192.168.1.2,SOA,unkIf you don't stop with a dot, unbound (nslookup probably) will add the device's local network domain.
That why this works :
C:\Users\gwkro>nslookup gauche2 Serveur : pfSense.my-pfsense-local-domain.net Address: 192.168.1.1 Nom : gauche2.my-pfsense-local-domain.net Addresses: 2001:470:1f13:beef:2::c7 192.168.1.6"gauche2" is a PC in my pfSense LAN.
I could (should !) also ask :
gauche2.my-pfsense-local-domain.net.
which is de fully qualified host name of that device. -
This sounds like a mis-configuration somewhere rather than a bug. For reference, the ACLs are stored in
/var/unbound/access_lists.conf. It works correctly here:#> nslookup google.com 2001:db8::1 Server: gw.home.arpa Address: 2001:db8::1 Non-authoritative answer: Name: google.com Addresses: 2607:f8b0:4023:1006::64 2607:f8b0:4023:1006::65 2607:f8b0:4023:1006::8a 2607:f8b0:4023:1006::8b 142.251.32.238 -
Yep thanks explaining where the config file is. However, yep there are no IPV6-entrys appart of the test one I entered manually.
[2.7.0-DEVELOPMENT][root@pfSense.lan]/root: cat /var/unbound/access_lists.conf
access-control: 127.0.0.1/32 allow_snoop
access-control: ::1 allow_snoop
access-control: 10.128.244.0/22 allow
access-control: 127.0.0.0/8 allow
access-control: 192.168.1.0/24 allow
access-control: 192.168.2.0/24 allow
access-control: 192.168.2.1/24 allow
access-control: 192.168.5.0/24 allow
access-control: 192.168.9.0/24 allow
access-control: 192.168.10.0/24 allow
access-control: 192.168.11.0/24 allow
access-control: 192.168.13.0/24 allow
access-control: 192.168.14.0/24 allow
access-control: 192.168.17.0/24 allow
access-control: 192.168.18.0/24 allow
access-control: 192.168.88.0/24 allow
access-control: 192.168.100.0/24 allow
access-control: 192.168.110.0/24 allow
access-control: 192.168.111.0/24 allow
access-control: 192.168.120.0/24 allow
access-control: 192.168.130.0/24 allow
access-control: ::1/128 allow
#IPV6-test
access-control: 2a02:xxxx:yyyy:11::/64 allow