Huawei AR161FG-L + PfSense 2.6.0 - ipsec s2s
-
@rnduser
не работает как ?
если добавить новое правило или убрать ip из правила 5 ? -
@rnduser
сделайте так
добавьте в ACL 3999
такое правило
rule 6 permit ip source 10.9.20.0 0.0.0.255 destination 10.9.30.0 0.0.0.255итого , будет 2 правила в acl 3999
-
@konstanti
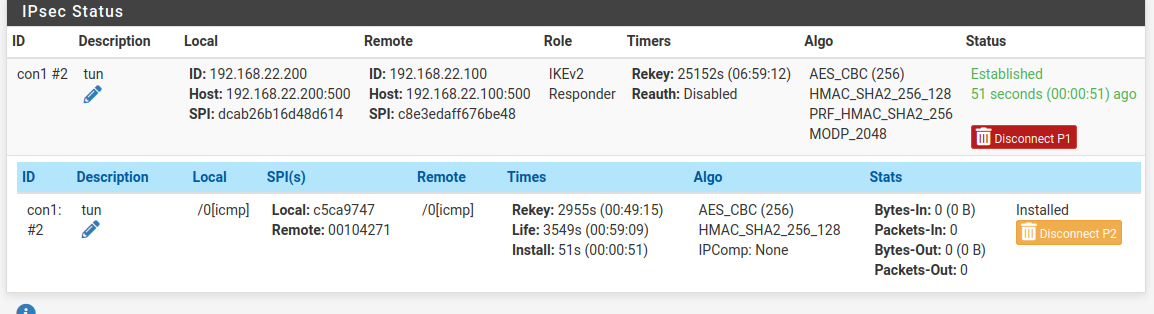
пробовал, и заменить и добавить. -
сделайте : как я написал
добавьте в ACL 3999 зеркальное правило -
@konstanti
Новый текстовый документ (4).txtв туннель не заворачивается(
счетчики по нулям -
ICMP ,насколько я понимаю, немного не IP , может быть в этом причина того , что HW не заворачивает его в туннель
Я верно понимаю , что если добавить в ACL 3999 правилоrule 6 permit icmp source 10.9.30.0 0.0.0.255 destination 10.9.20.0 0.0.0.255
то туннель не поднимается ?
-
@konstanti said in Huawei AR161FG-L + PfSense 2.6.0 - ipsec s2s:
то туннель не поднимается ?
поднимается, но в логах ошибки
-
@rnduser
обе фазы или только одна ?
какие ошибки ? -
@konstanti не поднималась вторая фаза. лог уже потер, и вернул как было
-
@konstanti вот что интересно.:
nat outbound?, это базовый ацл разрешающий все ip наружу с Gi0/0/4
поди и туннельный пакеты туда же летят?
К этому же интерфейсу прикручена айписек политика... -
а что за ACL 2999 ?
-
@konstanti
вот что nat session table all выдает когда пингуешь хост за ПфСенсом.
ACL 2999 - Basic ACL, вида permit any. т.е. направление - только исходящее.Protocol : ICMP(1)
SrcAddr Vpn : 192.168.22.100
DestAddr Vpn : 10.9.20.220
Type Code IcmpId : 8 0 44004
NAT-Info
-
@konstanti или нет?
ничего не понимаю уже.
Вот пинг на ту сторону. вот вывод NAT[router001-k85]display nat session destination 10.9.20.220
NAT Session Table Information:
Protocol : ICMP(1)
SrcAddr Vpn : 10.9.30.220
DestAddr Vpn : 10.9.20.220
Type Code IcmpId : 8 0 1
NAT-Info
New SrcAddr : 192.168.22.100
New DestAddr : ----
New IcmpId : 10425
-
@rnduser
Все верно , по какой-то причине ICMP пакеты не заворачиваются в туннель и идут дальше на выход через ВАН интерфейс , где проходят через NAT и ..... теряются -
@konstanti получается нужно поправить ACL прикрученый NATом к Gi0/0/4
интересно, так прокатит?[router001-k85]display acl 3001
Advanced ACL 3001, 2 rules
Nat outbound
Acl's step is 5
rule 10 deny ip source 10.9.30.0 0.0.0.255 destination 10.9.20.0 0.0.0.255
rule 20 permit ip
-
@rnduser штош. с этим ACL пингов на ту сторону нет, но и в NAT трансляции не попадает icmp запрос до хоста за pfsense...
но и теперь трафик вроде попадает куда нужноTotal quantity of nonempty ACL number is 4
Basic ACL GigabitEthernet0/0/4 2999, 1 rule
Acl's step is 5
rule 5 permitAdvanced ACL 3001, 2 rules
Nat outbound
Acl's step is 5
rule 10 deny ip source 10.9.30.0 0.0.0.255 destination 10.9.20.0 0.0.0.255 (2 matches)
rule 20 permit ip (15 matches)Advanced ACL 3990, 3 rules
allow ipsec to local
Acl's step is 5
rule 10 permit icmp (52 matches)
rule 30 permit udp destination-port eq 500 (24 matches)
rule 35 permit udp destination-port eq 4500Advanced ACL p_GigabitEthernet0/0/4_1 3999, 1 rule
Acl's step is 5
rule 5 permit ip source 10.9.30.0 0.0.0.255 destination 10.9.20.0 0.0.0.255 (130 matches)
-
@rnduser
Ну, не только одними пингами мир живет . Попробуйте другой вид трафика .
По acl Вы все делаете по инструкции ( си в интернете ) те должен быть 1 acl в Вашем случае . И пинги должны бегать
Может быть сбой какой-то … перегрузить устройство не пробовали ? -
This post is deleted! -
@konstanti
перезагрузил обе стороны.
Вот лог ПфСенса. Как я понимаю все гладко и DPD работает?
Хотелось бы исключить хоть одну из сторон проблемы.Jan 23 15:55:09 charon 36623 06[IKE] <con1|2> nothing to initiate
Jan 23 15:55:09 charon 36623 06[IKE] <con1|2> activating new tasks
Jan 23 15:55:09 charon 36623 06[ENC] <con1|2> parsed INFORMATIONAL response 8 [ ]
Jan 23 15:55:09 charon 36623 06[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:55:09 charon 36623 07[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:55:09 charon 36623 07[ENC] <con1|2> generating INFORMATIONAL request 8 [ ]
Jan 23 15:55:09 charon 36623 07[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:55:09 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:55:09 charon 36623 07[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:55:09 charon 36623 07[IKE] <con1|2> sending DPD request
Jan 23 15:54:59 charon 36623 07[IKE] <con1|2> nothing to initiate
Jan 23 15:54:59 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:59 charon 36623 07[ENC] <con1|2> parsed INFORMATIONAL response 7 [ ]
Jan 23 15:54:59 charon 36623 07[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:54:59 charon 36623 07[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:54:59 charon 36623 07[ENC] <con1|2> generating INFORMATIONAL request 7 [ ]
Jan 23 15:54:59 charon 36623 07[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:54:59 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:59 charon 36623 07[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:54:59 charon 36623 07[IKE] <con1|2> sending DPD request
Jan 23 15:54:48 charon 36623 07[IKE] <con1|2> nothing to initiate
Jan 23 15:54:48 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:48 charon 36623 07[ENC] <con1|2> parsed INFORMATIONAL response 6 [ ]
Jan 23 15:54:48 charon 36623 07[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:54:48 charon 36623 07[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:54:48 charon 36623 07[ENC] <con1|2> generating INFORMATIONAL request 6 [ ]
Jan 23 15:54:48 charon 36623 07[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:54:48 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:48 charon 36623 07[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:54:48 charon 36623 07[IKE] <con1|2> sending DPD request
Jan 23 15:54:38 charon 36623 07[IKE] <con1|2> nothing to initiate
Jan 23 15:54:38 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:38 charon 36623 07[ENC] <con1|2> parsed INFORMATIONAL response 5 [ ]
Jan 23 15:54:38 charon 36623 07[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:54:38 charon 36623 07[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:54:38 charon 36623 07[ENC] <con1|2> generating INFORMATIONAL request 5 [ ]
Jan 23 15:54:38 charon 36623 07[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:54:38 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:38 charon 36623 07[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:54:38 charon 36623 07[IKE] <con1|2> sending DPD request
Jan 23 15:54:28 charon 36623 07[IKE] <con1|2> nothing to initiate
Jan 23 15:54:28 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:28 charon 36623 07[ENC] <con1|2> parsed INFORMATIONAL response 4 [ ]
Jan 23 15:54:28 charon 36623 07[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:54:28 charon 36623 07[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:54:28 charon 36623 07[ENC] <con1|2> generating INFORMATIONAL request 4 [ ]
Jan 23 15:54:28 charon 36623 07[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:54:28 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:28 charon 36623 07[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:54:28 charon 36623 07[IKE] <con1|2> sending DPD request
Jan 23 15:54:18 charon 36623 07[IKE] <con1|2> nothing to initiate
Jan 23 15:54:18 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:18 charon 36623 07[ENC] <con1|2> parsed INFORMATIONAL response 3 [ ]
Jan 23 15:54:18 charon 36623 07[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:54:18 charon 36623 07[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:54:18 charon 36623 07[ENC] <con1|2> generating INFORMATIONAL request 3 [ ]
Jan 23 15:54:18 charon 36623 07[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:54:18 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:18 charon 36623 07[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:54:18 charon 36623 07[IKE] <con1|2> sending DPD request
Jan 23 15:54:08 charon 36623 08[IKE] <con1|2> nothing to initiate
Jan 23 15:54:08 charon 36623 08[IKE] <con1|2> activating new tasks
Jan 23 15:54:08 charon 36623 08[ENC] <con1|2> parsed INFORMATIONAL response 2 [ ]
Jan 23 15:54:08 charon 36623 08[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:54:08 charon 36623 08[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:54:08 charon 36623 08[ENC] <con1|2> generating INFORMATIONAL request 2 [ ]
Jan 23 15:54:08 charon 36623 08[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:54:08 charon 36623 08[IKE] <con1|2> activating new tasks
Jan 23 15:54:08 charon 36623 08[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:54:08 charon 36623 08[IKE] <con1|2> sending DPD request
Jan 23 15:53:58 charon 36623 08[IKE] <con1|2> nothing to initiate
Jan 23 15:53:58 charon 36623 08[IKE] <con1|2> activating new tasks
Jan 23 15:53:58 charon 36623 08[ENC] <con1|2> parsed INFORMATIONAL response 1 [ ]
Jan 23 15:53:58 charon 36623 08[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:53:58 charon 36623 08[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:53:58 charon 36623 08[ENC] <con1|2> generating INFORMATIONAL request 1 [ ]
Jan 23 15:53:58 charon 36623 08[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:53:58 charon 36623 08[IKE] <con1|2> activating new tasks
Jan 23 15:53:58 charon 36623 08[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:53:58 charon 36623 08[IKE] <con1|2> sending DPD request
Jan 23 15:53:48 charon 36623 08[IKE] <con1|2> nothing to initiate
Jan 23 15:53:48 charon 36623 08[IKE] <con1|2> activating new tasks
Jan 23 15:53:48 charon 36623 08[ENC] <con1|2> parsed INFORMATIONAL response 0 [ ]
Jan 23 15:53:48 charon 36623 08[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:53:48 charon 36623 08[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:53:48 charon 36623 08[ENC] <con1|2> generating INFORMATIONAL request 0 [ ]
Jan 23 15:53:48 charon 36623 08[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:53:48 charon 36623 08[IKE] <con1|2> activating new tasks
Jan 23 15:53:48 charon 36623 08[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:53:48 charon 36623 08[IKE] <con1|2> sending DPD request
Jan 23 15:53:38 charon 36623 08[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (224 bytes)
Jan 23 15:53:38 charon 36623 08[ENC] <con1|2> generating IKE_AUTH response 1 [ IDr AUTH N(ESP_TFC_PAD_N) SA TSi TSr ]
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> CHILD_SA con1{4} state change: INSTALLING => INSTALLED
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> CHILD_SA con1{4} established with SPIs c053b3ac_i 005ade22_o and TS 10.9.20.0/24|/0 === 10.9.30.0/24|/0
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> SPI 0x005ade22, src 192.168.22.200 dst 192.168.22.100
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> adding outbound ESP SA
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> SPI 0xc053b3ac, src 192.168.22.100 dst 192.168.22.200
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> adding inbound ESP SA
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> using HMAC_SHA2_256_128 for integrity
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> using AES_CBC for encryption
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> CHILD_SA con1{4} state change: CREATED => INSTALLING
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> config: 10.9.30.0/24|/0, received: 10.9.30.0/24|/0 => match: 10.9.30.0/24|/0
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> selecting traffic selectors for other:
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> config: 10.9.20.0/24|/0, received: 10.9.20.0/24|/0 => match: 10.9.20.0/24|/0
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> selecting traffic selectors for us:
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> proposal matches
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> selecting proposal:
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> found matching child config "con1" with prio 10
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> candidate "con1" with prio 5+5
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> 10.9.30.0/24|/0
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> proposing traffic selectors for other:
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> 10.9.20.0/24|/0
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> proposing traffic selectors for us:
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> looking for a child config for 10.9.20.0/24|/0 === 10.9.30.0/24|/0
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> maximum IKE_SA lifetime 27708s
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> scheduling rekeying in 24828s
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> IKE_SA con1[2] state change: CONNECTING => ESTABLISHED
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> IKE_SA con1[2] established between 192.168.22.200[192.168.22.200]...192.168.22.100[192.168.22.100]
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> successfully created shared key MAC
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> authentication of '192.168.22.200' (myself) with pre-shared key
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> authentication of '192.168.22.100' with pre-shared key successful
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> selected peer config 'con1'
Jan 23 15:53:38 charon 36623 08[CFG] <2> candidate "con1", match: 1/20/3100 (me/other/ike)
Jan 23 15:53:38 charon 36623 08[CFG] <2> looking for peer configs matching 192.168.22.200[%any]...192.168.22.100[192.168.22.100]
Jan 23 15:53:38 charon 36623 08[ENC] <2> parsed IKE_AUTH request 1 [ N(SET_WINSIZE) N(ESP_TFC_PAD_N) IDi AUTH SA TSi TSr ]
Jan 23 15:53:38 charon 36623 08[NET] <2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (240 bytes)
Jan 23 15:53:37 charon 36623 09[NET] <2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (448 bytes)
Jan 23 15:53:37 charon 36623 09[ENC] <2> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(CHDLESS_SUP) N(MULT_AUTH) ]
Jan 23 15:53:37 charon 36623 09[CFG] <2> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Jan 23 15:53:37 charon 36623 09[CFG] <2> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Jan 23 15:53:37 charon 36623 09[CFG] <2> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Jan 23 15:53:37 charon 36623 09[CFG] <2> proposal matches
Jan 23 15:53:37 charon 36623 09[CFG] <2> selecting proposal:
Jan 23 15:53:37 charon 36623 09[IKE] <2> IKE_SA (unnamed)[2] state change: CREATED => CONNECTING
Jan 23 15:53:37 charon 36623 09[IKE] <2> 192.168.22.100 is initiating an IKE_SA
Jan 23 15:53:37 charon 36623 09[IKE] <2> received Cisco FlexVPN Supported vendor ID
Jan 23 15:53:37 charon 36623 09[ENC] <2> received unknown vendor ID: 48:55:41:57:45:49:2d:49:4b:45:76:31:44:53:43:50
Jan 23 15:53:37 charon 36623 09[IKE] <2> remote endpoint changed from 0.0.0.0 to 192.168.22.100[500]
Jan 23 15:53:37 charon 36623 09[IKE] <2> local endpoint changed from 0.0.0.0[500] to 192.168.22.200[500]
Jan 23 15:53:37 charon 36623 09[CFG] <2> found matching ike config: 192.168.22.200...192.168.22.100 with prio 3100
Jan 23 15:53:37 charon 36623 09[CFG] <2> candidate: 192.168.22.200...192.168.22.100, prio 3100
Jan 23 15:53:37 charon 36623 09[CFG] <2> looking for an IKEv2 config for 192.168.22.200...192.168.22.100
Jan 23 15:53:37 charon 36623 09[ENC] <2> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) V V ]
Jan 23 15:53:37 charon 36623 09[NET] <2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (457 bytes) -
@rnduser
тут все ок
проблема именно в HW - по какой-то причине трафик не попадает в туннель