Huawei AR161FG-L + PfSense 2.6.0 - ipsec s2s
-
@konstanti
перезагрузил обе стороны.
Вот лог ПфСенса. Как я понимаю все гладко и DPD работает?
Хотелось бы исключить хоть одну из сторон проблемы.Jan 23 15:55:09 charon 36623 06[IKE] <con1|2> nothing to initiate
Jan 23 15:55:09 charon 36623 06[IKE] <con1|2> activating new tasks
Jan 23 15:55:09 charon 36623 06[ENC] <con1|2> parsed INFORMATIONAL response 8 [ ]
Jan 23 15:55:09 charon 36623 06[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:55:09 charon 36623 07[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:55:09 charon 36623 07[ENC] <con1|2> generating INFORMATIONAL request 8 [ ]
Jan 23 15:55:09 charon 36623 07[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:55:09 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:55:09 charon 36623 07[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:55:09 charon 36623 07[IKE] <con1|2> sending DPD request
Jan 23 15:54:59 charon 36623 07[IKE] <con1|2> nothing to initiate
Jan 23 15:54:59 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:59 charon 36623 07[ENC] <con1|2> parsed INFORMATIONAL response 7 [ ]
Jan 23 15:54:59 charon 36623 07[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:54:59 charon 36623 07[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:54:59 charon 36623 07[ENC] <con1|2> generating INFORMATIONAL request 7 [ ]
Jan 23 15:54:59 charon 36623 07[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:54:59 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:59 charon 36623 07[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:54:59 charon 36623 07[IKE] <con1|2> sending DPD request
Jan 23 15:54:48 charon 36623 07[IKE] <con1|2> nothing to initiate
Jan 23 15:54:48 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:48 charon 36623 07[ENC] <con1|2> parsed INFORMATIONAL response 6 [ ]
Jan 23 15:54:48 charon 36623 07[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:54:48 charon 36623 07[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:54:48 charon 36623 07[ENC] <con1|2> generating INFORMATIONAL request 6 [ ]
Jan 23 15:54:48 charon 36623 07[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:54:48 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:48 charon 36623 07[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:54:48 charon 36623 07[IKE] <con1|2> sending DPD request
Jan 23 15:54:38 charon 36623 07[IKE] <con1|2> nothing to initiate
Jan 23 15:54:38 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:38 charon 36623 07[ENC] <con1|2> parsed INFORMATIONAL response 5 [ ]
Jan 23 15:54:38 charon 36623 07[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:54:38 charon 36623 07[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:54:38 charon 36623 07[ENC] <con1|2> generating INFORMATIONAL request 5 [ ]
Jan 23 15:54:38 charon 36623 07[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:54:38 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:38 charon 36623 07[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:54:38 charon 36623 07[IKE] <con1|2> sending DPD request
Jan 23 15:54:28 charon 36623 07[IKE] <con1|2> nothing to initiate
Jan 23 15:54:28 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:28 charon 36623 07[ENC] <con1|2> parsed INFORMATIONAL response 4 [ ]
Jan 23 15:54:28 charon 36623 07[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:54:28 charon 36623 07[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:54:28 charon 36623 07[ENC] <con1|2> generating INFORMATIONAL request 4 [ ]
Jan 23 15:54:28 charon 36623 07[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:54:28 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:28 charon 36623 07[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:54:28 charon 36623 07[IKE] <con1|2> sending DPD request
Jan 23 15:54:18 charon 36623 07[IKE] <con1|2> nothing to initiate
Jan 23 15:54:18 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:18 charon 36623 07[ENC] <con1|2> parsed INFORMATIONAL response 3 [ ]
Jan 23 15:54:18 charon 36623 07[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:54:18 charon 36623 07[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:54:18 charon 36623 07[ENC] <con1|2> generating INFORMATIONAL request 3 [ ]
Jan 23 15:54:18 charon 36623 07[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:54:18 charon 36623 07[IKE] <con1|2> activating new tasks
Jan 23 15:54:18 charon 36623 07[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:54:18 charon 36623 07[IKE] <con1|2> sending DPD request
Jan 23 15:54:08 charon 36623 08[IKE] <con1|2> nothing to initiate
Jan 23 15:54:08 charon 36623 08[IKE] <con1|2> activating new tasks
Jan 23 15:54:08 charon 36623 08[ENC] <con1|2> parsed INFORMATIONAL response 2 [ ]
Jan 23 15:54:08 charon 36623 08[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:54:08 charon 36623 08[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:54:08 charon 36623 08[ENC] <con1|2> generating INFORMATIONAL request 2 [ ]
Jan 23 15:54:08 charon 36623 08[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:54:08 charon 36623 08[IKE] <con1|2> activating new tasks
Jan 23 15:54:08 charon 36623 08[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:54:08 charon 36623 08[IKE] <con1|2> sending DPD request
Jan 23 15:53:58 charon 36623 08[IKE] <con1|2> nothing to initiate
Jan 23 15:53:58 charon 36623 08[IKE] <con1|2> activating new tasks
Jan 23 15:53:58 charon 36623 08[ENC] <con1|2> parsed INFORMATIONAL response 1 [ ]
Jan 23 15:53:58 charon 36623 08[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:53:58 charon 36623 08[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:53:58 charon 36623 08[ENC] <con1|2> generating INFORMATIONAL request 1 [ ]
Jan 23 15:53:58 charon 36623 08[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:53:58 charon 36623 08[IKE] <con1|2> activating new tasks
Jan 23 15:53:58 charon 36623 08[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:53:58 charon 36623 08[IKE] <con1|2> sending DPD request
Jan 23 15:53:48 charon 36623 08[IKE] <con1|2> nothing to initiate
Jan 23 15:53:48 charon 36623 08[IKE] <con1|2> activating new tasks
Jan 23 15:53:48 charon 36623 08[ENC] <con1|2> parsed INFORMATIONAL response 0 [ ]
Jan 23 15:53:48 charon 36623 08[NET] <con1|2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (80 bytes)
Jan 23 15:53:48 charon 36623 08[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (80 bytes)
Jan 23 15:53:48 charon 36623 08[ENC] <con1|2> generating INFORMATIONAL request 0 [ ]
Jan 23 15:53:48 charon 36623 08[IKE] <con1|2> activating IKE_DPD task
Jan 23 15:53:48 charon 36623 08[IKE] <con1|2> activating new tasks
Jan 23 15:53:48 charon 36623 08[IKE] <con1|2> queueing IKE_DPD task
Jan 23 15:53:48 charon 36623 08[IKE] <con1|2> sending DPD request
Jan 23 15:53:38 charon 36623 08[NET] <con1|2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (224 bytes)
Jan 23 15:53:38 charon 36623 08[ENC] <con1|2> generating IKE_AUTH response 1 [ IDr AUTH N(ESP_TFC_PAD_N) SA TSi TSr ]
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> CHILD_SA con1{4} state change: INSTALLING => INSTALLED
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> CHILD_SA con1{4} established with SPIs c053b3ac_i 005ade22_o and TS 10.9.20.0/24|/0 === 10.9.30.0/24|/0
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> SPI 0x005ade22, src 192.168.22.200 dst 192.168.22.100
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> adding outbound ESP SA
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> SPI 0xc053b3ac, src 192.168.22.100 dst 192.168.22.200
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> adding inbound ESP SA
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> using HMAC_SHA2_256_128 for integrity
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> using AES_CBC for encryption
Jan 23 15:53:38 charon 36623 08[CHD] <con1|2> CHILD_SA con1{4} state change: CREATED => INSTALLING
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> config: 10.9.30.0/24|/0, received: 10.9.30.0/24|/0 => match: 10.9.30.0/24|/0
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> selecting traffic selectors for other:
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> config: 10.9.20.0/24|/0, received: 10.9.20.0/24|/0 => match: 10.9.20.0/24|/0
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> selecting traffic selectors for us:
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> proposal matches
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> selecting proposal:
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> found matching child config "con1" with prio 10
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> candidate "con1" with prio 5+5
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> 10.9.30.0/24|/0
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> proposing traffic selectors for other:
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> 10.9.20.0/24|/0
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> proposing traffic selectors for us:
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> looking for a child config for 10.9.20.0/24|/0 === 10.9.30.0/24|/0
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> maximum IKE_SA lifetime 27708s
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> scheduling rekeying in 24828s
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> IKE_SA con1[2] state change: CONNECTING => ESTABLISHED
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> IKE_SA con1[2] established between 192.168.22.200[192.168.22.200]...192.168.22.100[192.168.22.100]
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> successfully created shared key MAC
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> authentication of '192.168.22.200' (myself) with pre-shared key
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
Jan 23 15:53:38 charon 36623 08[IKE] <con1|2> authentication of '192.168.22.100' with pre-shared key successful
Jan 23 15:53:38 charon 36623 08[CFG] <con1|2> selected peer config 'con1'
Jan 23 15:53:38 charon 36623 08[CFG] <2> candidate "con1", match: 1/20/3100 (me/other/ike)
Jan 23 15:53:38 charon 36623 08[CFG] <2> looking for peer configs matching 192.168.22.200[%any]...192.168.22.100[192.168.22.100]
Jan 23 15:53:38 charon 36623 08[ENC] <2> parsed IKE_AUTH request 1 [ N(SET_WINSIZE) N(ESP_TFC_PAD_N) IDi AUTH SA TSi TSr ]
Jan 23 15:53:38 charon 36623 08[NET] <2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (240 bytes)
Jan 23 15:53:37 charon 36623 09[NET] <2> sending packet: from 192.168.22.200[500] to 192.168.22.100[500] (448 bytes)
Jan 23 15:53:37 charon 36623 09[ENC] <2> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(CHDLESS_SUP) N(MULT_AUTH) ]
Jan 23 15:53:37 charon 36623 09[CFG] <2> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Jan 23 15:53:37 charon 36623 09[CFG] <2> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Jan 23 15:53:37 charon 36623 09[CFG] <2> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Jan 23 15:53:37 charon 36623 09[CFG] <2> proposal matches
Jan 23 15:53:37 charon 36623 09[CFG] <2> selecting proposal:
Jan 23 15:53:37 charon 36623 09[IKE] <2> IKE_SA (unnamed)[2] state change: CREATED => CONNECTING
Jan 23 15:53:37 charon 36623 09[IKE] <2> 192.168.22.100 is initiating an IKE_SA
Jan 23 15:53:37 charon 36623 09[IKE] <2> received Cisco FlexVPN Supported vendor ID
Jan 23 15:53:37 charon 36623 09[ENC] <2> received unknown vendor ID: 48:55:41:57:45:49:2d:49:4b:45:76:31:44:53:43:50
Jan 23 15:53:37 charon 36623 09[IKE] <2> remote endpoint changed from 0.0.0.0 to 192.168.22.100[500]
Jan 23 15:53:37 charon 36623 09[IKE] <2> local endpoint changed from 0.0.0.0[500] to 192.168.22.200[500]
Jan 23 15:53:37 charon 36623 09[CFG] <2> found matching ike config: 192.168.22.200...192.168.22.100 with prio 3100
Jan 23 15:53:37 charon 36623 09[CFG] <2> candidate: 192.168.22.200...192.168.22.100, prio 3100
Jan 23 15:53:37 charon 36623 09[CFG] <2> looking for an IKEv2 config for 192.168.22.200...192.168.22.100
Jan 23 15:53:37 charon 36623 09[ENC] <2> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) V V ]
Jan 23 15:53:37 charon 36623 09[NET] <2> received packet: from 192.168.22.100[500] to 192.168.22.200[500] (457 bytes) -
@rnduser
тут все ок
проблема именно в HW - по какой-то причине трафик не попадает в туннель -
@konstanti после правки NAT Acl - попадает, только не ходит.
-
это что значит - поясните , Пожалуйста
-
@rnduser said in Huawei AR161FG-L + PfSense 2.6.0 - ipsec s2s:
Advanced ACL p_GigabitEthernet0/0/4_1 3999, 1 rule
Acl's step is 5
rule 5 permit ip source 10.9.30.0 0.0.0.255 destination 10.9.20.0 0.0.0.255 (130 matches)имею ввиду вот эту политику. 130 срабатываний.
- трафик перехватывается
- в таблице NAT outbound sessions - адреса интересующих сетей - отсутствуют.
-
@konstanti уезжал на несколько часов. оставил как есть. приехал, а влогах вон что:
Time: Jan 23 19:24:21
IP: 10.9.30.254
Host: 2023-1-23
Facility: local7
Priority: notice
Tag:
Message: 16:24:17 router001-k85 %%01IKE/5/IKE_NEGO_FAIL(l)[858]:IPSec tunnel negotiation fails. (IfIndex=7, SeqNum=0, PeerAddress=192.168.22.200, PeerPort=500, Reason=receive proposal mismatch or use sm in ikev2)буду сверять настройки сторон.
-
@konstanti ну получилось вроде бы. уже завтра проверю еще раз.
-
Добрый
@rnduser
Сменить хуавей на пф можно в будущем?
Пф умеет ipsec vti, что гораздо удобнее в плане pbr. -
@werter
Добрый день.
Нет , конкретно в этом случае с обной стороны туннеля должен быть аппаратный маршрутизатор. -
@rnduser
так все заработало или как ?
в чем была проблема ? -
@konstanti доброго дня.
Кроме не верной настройки NAT, когда траффик предназначался туннелю, но попадал на NAT Outbound, видимо, была проблема в proposal на первой фазе. причем, в дефолтном режиме детализации ipsec не было никаких сообщений о проблеме (вы и сами лог видели). А со стороны Huawei в "ike error-log" были сообщения о "ike mismatch".
В итоге снова пересобрал ipsec profile и сверил с PfSense, вроде работает. Теперь нужно всё ещё раз перепроверить и разобраться с настройкой Firewall, меня терзают сомнения... -
@werter
Вы не поверите, но на этом сайте стоял PfSense с той стороны туннеля (OpenVpn s2s), но это было так: ProxMox + PfSense+WinServer+ip surveillance. В итоге потребность сократилась до Маршрутизатора и ip-surveillance. -
@konstanti
в итоге вот рабочий сеттинг со стороны PfSense
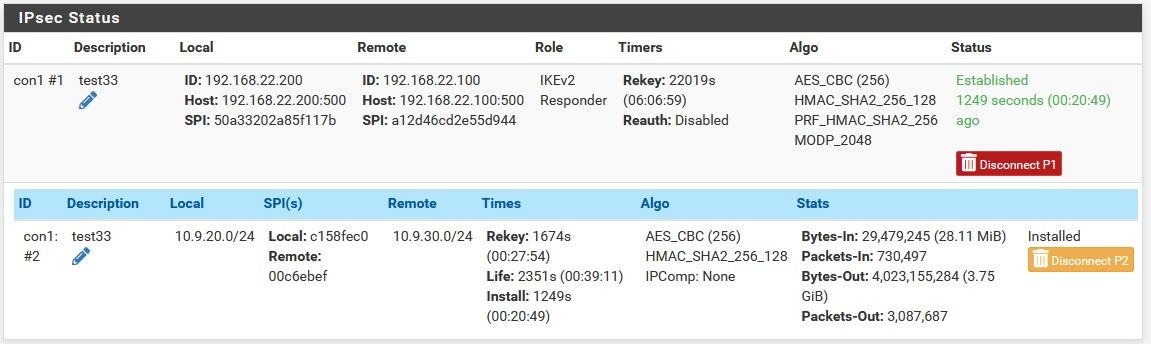
погонял трафик, вроде все корректно, заглянул в enc0 и em0 (wan-iface) - ходит куда нужно.
в тестовой лабе, Huawei <--> PfSense (Celeron J3455, AES-NI) , 250-290Mbit/s. Между двумя одинаковыми Хуавеями- 530Mbit/s ))
Спасибо всем за помощь. -
@konstanti добрый день.
А если нужно больше одной сети пробрасывать в туннель, добавляем дополнительные записи в Phase2 ? -
@rnduser
Да, все верно , добавляем отдправило а acl или запись со стороны pf в настройках фазы-2 ( или играемся маской подсети /wildcard если такое позволяет адресация ) -
@konstanti пока не пойму как со стороны хуавея это сделать?
за ним две сети:- 10.12.200.0/24
- 10.12.202.0/24
Добавлять ещё одно правило в ACL Policy или накрывать обе сети wildcard. Если wildcard, то какая маска? что-то не соображу? 0.0.252.255?
-
Или добавляем правило в ацл и запись в пф
Итого 2 записи с каждой стороны
Или правим существующую с обеих сторон
Начать эксперимент можно с
Pf 10.12.0.0/16
Hw 10.12.0.0 0.0.255.255Потом уже можно менять маску , если надо
-
@konstanti said in Huawei AR161FG-L + PfSense 2.6.0 - ipsec s2s:
Pf 10.12.0.0/16
Hw 10.12.0.0 0.0.255.255ну нет. сильно широко )
-
@konstanti said in Huawei AR161FG-L + PfSense 2.6.0 - ipsec s2s:
Итого 2 записи с каждой стороны
да, это понятно.
к Фазе1 добавляем две записи Фазы2 соответствующие интересующим нас сетям.
На хуавее добавляем в ACL Policy ещё одну запись. -
@rnduser
Это для эксперимента
Потом маску сделаете меньше и настроете как Вам надо