SG-2100 23.01 update failed
-
@stephenw10 said in SG-2100 23.01 update failed:
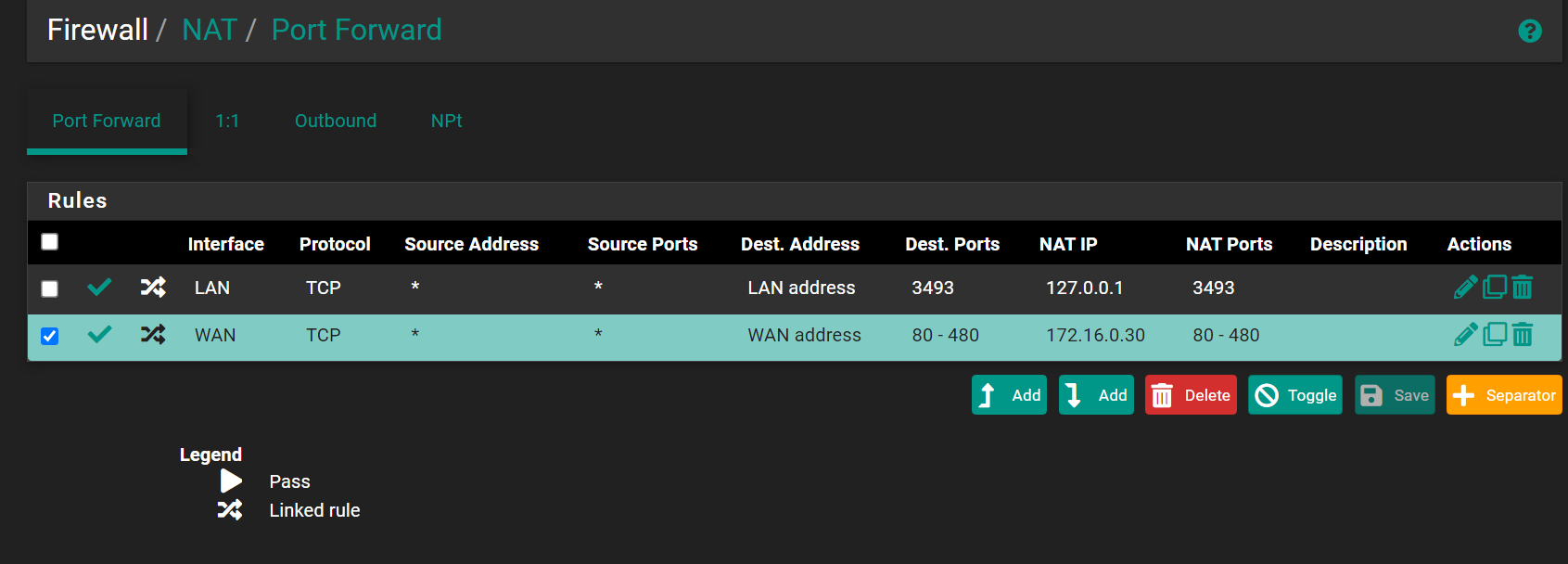
Try running ps -auxwwd on the firewall
Can you please tell me where I should run this? is it
Diagnostics -> command prompt? -
Yes, you can run it there or at the command line directly.
-
@stephenw10
Here is the output. Masked my IP as XXX.XX.XXXXUSER PID %CPU %MEM VSZ RSS TT STAT STARTED TIME COMMAND root 0 0.2 0.0 0 1008 - DLs 03:05 3:24.93 [kernel] root 11 182.4 0.0 0 32 - RNL 03:05 916:31.14 - [idle] root 12 0.6 0.0 0 272 - WL 03:05 3:50.49 - [intr] root 2 0.1 0.0 0 32 - WL 03:05 5:43.31 - [clock] root 1 0.0 0.0 11328 1192 - ILs 03:05 0:00.15 - /sbin/init unbound 48358 0.3 3.4 132176 116364 - Ss 03:06 4:00.19 |-- /usr/local/sbin/unbound -c /var/unbound/unbound.conf root 280 0.0 0.1 12668 2392 - S 12:00 0:00.07 |-- /usr/bin/tail_pfb -n0 -F /var/log/filter.log root 324 0.0 1.3 72556 44428 - S 12:00 0:01.13 |-- /usr/local/bin/php_pfb -f /usr/local/pkg/pfblockerng/pfblockerng.inc filterlog root 381 0.0 0.9 113504 29952 - Ss 03:05 0:01.64 |-- php-fpm: master process (/usr/local/lib/php-fpm.conf) (php-fpm) root 627 2.1 1.4 147436 48808 - S 03:06 0:04.78 | |-- php-fpm: pool nginx (php-fpm) root 57391 0.0 0.1 13516 3212 - R 12:03 0:00.01 | | `-- ps -auxwwd root 382 0.0 1.4 147308 48240 - I 03:05 0:04.19 | |-- php-fpm: pool nginx (php-fpm) root 383 0.0 1.4 147308 48312 - I 03:05 0:05.15 | `-- php-fpm: pool nginx (php-fpm) root 430 0.0 0.1 13276 2900 - INs 03:05 0:00.02 |-- /usr/local/sbin/check_reload_status root 431 0.0 0.1 13276 2668 - IN 03:05 0:00.00 | `-- check_reload_status: Monitoring daemon of check_reload_status (check_reload_status) root 623 0.0 0.1 11548 2272 - Ss 03:05 0:00.09 |-- /sbin/devd -q -f /etc/pfSense-devd.conf root 14285 0.0 0.1 12708 2468 - Is 03:06 0:00.19 |-- /usr/local/sbin/dhcp6c -d -c /var/etc/dhcp6c.conf -p /var/run/dhcp6c.pid mvneta0 root 15001 0.0 0.2 20564 8476 - Is 03:06 0:00.00 |-- sshd: /usr/sbin/sshd [listener] 0 of 10-100 startups (sshd) root 20686 0.0 0.1 13448 3564 - Ss 03:06 0:16.44 |-- /usr/local/sbin/filterlog -i pflog0 -p /var/run/filterlog.pid root 22302 0.0 0.2 16268 5784 - Is 03:06 0:00.00 |-- /usr/local/sbin/upsmon uucp 22408 0.0 0.2 16404 6108 - S 03:06 0:02.16 | `-- /usr/local/sbin/upsmon root 28861 0.0 0.1 13440 3504 - Is 03:06 0:00.32 |-- /usr/local/sbin/xinetd -syslog daemon -f /var/etc/xinetd.conf -pidfile /var/run/xinetd.pid root 34470 0.0 0.1 13448 2792 - Is 03:06 0:10.28 |-- /usr/local/bin/dpinger -S -r 0 -i WANGW -B XXX.XX.XXX.XXX -p /var/run/dpinger_WANGW~XXX.XX.XXX.XXX~XXX.XX.XXX.XXX.pid -u /var/run/dpinger_WANGW~XXX.XX.XXX.XXX~XXX.XX.XXX.XXX.sock -C /etc/rc.gateway_alarm -d 1 -s 500 -l 2000 -t 60000 -A 1000 -D 500 -L 20 XXX.XX.XXX.XXX root 39049 0.0 0.2 18788 8144 - Ss 03:06 0:03.24 |-- /usr/local/sbin/upsd -u root uucp 39751 0.0 0.1 13632 3356 - Ss 03:06 0:20.54 |-- /usr/local/libexec/nut/usbhid-ups -a ups root 42208 0.0 0.2 18040 7564 - S 03:06 0:01.68 |-- /usr/local/sbin/lighttpd_pfb -f /var/unbound/pfb_dnsbl_lighty.conf root 42429 0.0 1.2 72556 40428 - I 03:06 0:00.85 | |-- /usr/local/bin/php -f /usr/local/pkg/pfblockerng/pfblockerng.inc dnsbl root 42607 0.0 1.2 72556 40440 - I 03:06 0:00.85 | `-- /usr/local/bin/php -f /usr/local/pkg/pfblockerng/pfblockerng.inc index root 45844 0.0 1.2 72556 41716 - S 03:06 0:37.04 |-- /usr/local/bin/php -f /usr/local/pkg/pfblockerng/pfblockerng.inc queries root 52208 0.0 0.1 12888 2620 - Is 03:06 0:01.22 |-- /usr/sbin/cron -s root 53090 0.0 0.2 21644 7008 - Ss 03:06 0:04.43 |-- /usr/local/sbin/ntpd -g -c /var/etc/ntpd.conf -p /var/run/ntpd.pid root 53854 0.0 0.2 28636 7588 - Is 03:06 0:00.00 |-- nginx: master process /usr/local/sbin/nginx -c /var/etc/nginx-webConfigurator.conf (nginx) root 54298 0.3 0.3 31196 9800 - S 03:06 0:00.55 | |-- nginx: worker process (nginx) root 54142 0.0 0.2 28636 8312 - S 03:06 0:00.02 | `-- nginx: worker process (nginx) dhcpd 63464 0.0 0.3 25028 11624 - Ss 03:06 0:06.09 |-- /usr/local/sbin/dhcpd -user dhcpd -group _dhcp -chroot /var/dhcpd -cf /etc/dhcpd.conf -pf /var/run/dhcpd.pid mvneta1 mvneta1.4084 root 63586 0.0 0.1 12636 2412 - Is 03:06 0:00.11 |-- /usr/local/sbin/radvd -p /var/run/radvd.pid -C /var/etc/radvd.conf -m syslog root 67599 0.0 0.1 12716 2896 - Ss 03:06 0:16.76 |-- /usr/sbin/syslogd -s -c -c -l /var/dhcpd/var/run/log -P /var/run/syslog.pid -f /etc/syslog.conf root 67598 0.0 0.1 13336 2888 - Is 11:39 0:00.02 | `-- /bin/sh /usr/local/sbin/sshguard -i /var/run/sshguard.pid root 68273 0.0 0.1 12568 2264 - I 11:39 0:00.01 | |-- /bin/cat root 68366 0.0 0.1 19232 5188 - IC 11:39 0:00.01 | |-- /usr/local/libexec/sshg-parser root 68658 0.0 0.1 13208 2832 - IC 11:39 0:00.02 | |-- /usr/local/libexec/sshg-blocker root 68832 0.0 0.1 13336 2892 - I 11:39 0:00.00 | `-- /bin/sh /usr/local/sbin/sshguard -i /var/run/sshguard.pid root 68954 0.0 0.1 13336 2896 - I 11:39 0:00.01 | `-- /bin/sh /usr/local/libexec/sshg-fw-pf root 72936 0.0 0.1 12564 2140 - Is 03:06 0:00.00 |-- /usr/local/bin/minicron 240 /var/run/ping_hosts.pid /usr/local/bin/ping_hosts.sh root 73200 0.0 0.1 12564 2160 - I 03:06 0:00.03 | `-- minicron: helper /usr/local/bin/ping_hosts.sh (minicron) root 73338 0.0 0.1 12564 2136 - Is 03:06 0:00.00 |-- /usr/local/bin/minicron 300 /var/run/ipsec_keepalive.pid /usr/local/bin/ipsec_keepalive.php root 73409 0.0 0.1 12564 2156 - I 03:06 0:00.02 | `-- minicron: helper /usr/local/bin/ipsec_keepalive.php (minicron) root 73639 0.0 0.1 12564 2136 - Is 03:06 0:00.00 |-- /usr/local/bin/minicron 3600 /var/run/expire_accounts.pid /usr/local/sbin/fcgicli -f /etc/rc.expireaccounts root 74026 0.0 0.1 12564 2160 - I 03:06 0:00.00 | `-- minicron: helper /usr/local/sbin/fcgicli -f /etc/rc.expireaccounts (minicron) root 74227 0.0 0.1 12564 2136 - Is 03:06 0:00.00 |-- /usr/local/bin/minicron 86400 /var/run/update_alias_url_data.pid /usr/local/sbin/fcgicli -f /etc/rc.update_alias_url_data root 74676 0.0 0.1 12564 2160 - I 03:06 0:00.00 | `-- minicron: helper /usr/local/sbin/fcgicli -f /etc/rc.update_alias_url_data (minicron) root 36272 0.0 0.1 13336 2836 u0- IN 03:06 0:15.20 |-- /bin/sh /var/db/rrd/updaterrd.sh root 52404 0.0 0.1 12564 2060 - INC 12:03 0:00.00 | `-- sleep 60 root 48872 0.0 0.1 13096 2848 u0 Is 03:06 0:00.04 `-- login [pam] (login) root 49943 0.0 0.1 13336 3176 u0 I 03:06 0:00.03 `-- -sh (sh) root 56717 0.0 0.1 13336 2900 u0 I+ 03:07 0:00.02 `-- /bin/sh /etc/rc.initial root 3 0.0 0.0 0 48 - DL 03:05 0:00.00 - [crypto] root 4 0.0 0.0 0 48 - DL 03:05 0:10.25 - [cam] root 5 0.0 0.0 0 16 - DL 03:05 0:00.00 - [busdma] root 6 0.0 0.0 0 704 - DL 03:05 0:46.90 - [zfskern] root 7 0.0 0.0 0 16 - DL 03:05 0:35.76 - [pf purge] root 8 0.0 0.0 0 16 - DL 03:05 0:04.18 - [rand_harvestq] root 9 0.0 0.0 0 16 - DL 03:05 0:00.19 - [task: mx25l flash] root 10 0.0 0.0 0 16 - DL 03:05 0:00.00 - [audit] root 13 0.0 0.0 0 32 - DL 03:05 0:00.00 - [ng_queue] root 14 0.0 0.0 0 48 - DL 03:05 0:00.04 - [geom] root 15 0.0 0.0 0 16 - DL 03:05 0:00.00 - [sequencer 00] root 16 0.0 0.0 0 160 - DL 03:05 0:08.29 - [usb] root 17 0.0 0.0 0 16 - DL 03:05 0:00.00 - [mmcsd0: mmc/sd card] root 18 0.0 0.0 0 16 - DL 03:05 0:00.00 - [mmcsd0boot0: mmc/sd] root 19 0.0 0.0 0 16 - DL 03:05 0:00.00 - [mmcsd0boot1: mmc/sd] root 20 0.0 0.0 0 48 - DL 03:05 0:07.05 - [pagedaemon] root 21 0.0 0.0 0 16 - DL 03:05 0:00.00 - [vmdaemon] root 22 0.0 0.0 0 48 - DL 03:05 0:01.03 - [bufdaemon] root 23 0.0 0.0 0 16 - DL 03:05 0:00.56 - [syncer] root 24 0.0 0.0 0 16 - DL 03:05 0:00.38 - [vnlru] root 25 0.0 0.0 0 16 - DL 03:05 0:00.00 - [ALQ Daemon] -
@stephenw10 said in SG-2100 23.01 update failed:
Most of those are outside that range.
Try running ps -auxwwd on the firewall and see if it shows you what has started those services.All these :
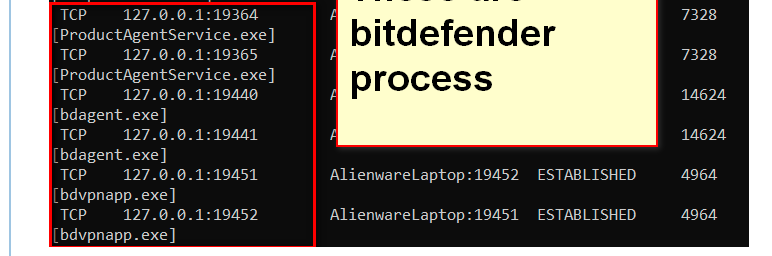
is not on pfSense.
It's a PC (called AlienwareLaptop) connecting it's LAN IP to 127.0.0.1 or the other way around.
IMHO, the image doesn't show anything that involves pfSense. -
What do you see in /var/etc/xinetd.conf?
cat /var/etc/xinetd.conf -
@stephenw10 said in SG-2100 23.01 update failed:
What do you see in /var/etc/xinetd.conf?
This is a long list and all of them I assume is my laptop (127.0.0.1) -- bitdefender anti virus I assume. Since the list is pretty big here is the linke
-
@netboy 127.0.0.1 is a loopback address that means "myself"...so it depends where you are running the commands. On pfSense that would be pfSense. On your laptop, your laptop.
What is 172.16.0.30?
-
Hmm the fact it starts at port 80 makes me think that could be config error. It's quite common to see a range entered incorrectly like 80-443 when that should be just ports 80 and 443.
-
@steveits said in SG-2100 23.01 update failed:
What is 172.16.0.30?
172.16.0.30 is tied to my external domain - run some applications....
-
-
@steveits said in SG-2100 23.01 update failed:
@netboy 127.0.0.1 is a loopback address that means "myself"...so it depends where you are running the commands. On pfSense that would be pfSense. On your laptop, your laptop.
-
Yeah you almost certainly don't want all those ports forwarded. If you need several ports you should create a ports alias and then use that in the rule instead.
I imagine you have NAT reflection enabled specifically in the rule too. That's what's creating the xinetd entries. I would remove that too unless you really need it.Steve
-
@stephenw10
My external domain points to 172.16.0.30 port 80(http) and 443(https). I access this from outside like https://subdomain.mydomain.com.
I guess I need to open this port to access https://subdomain.mydomain.com?Is this correct?
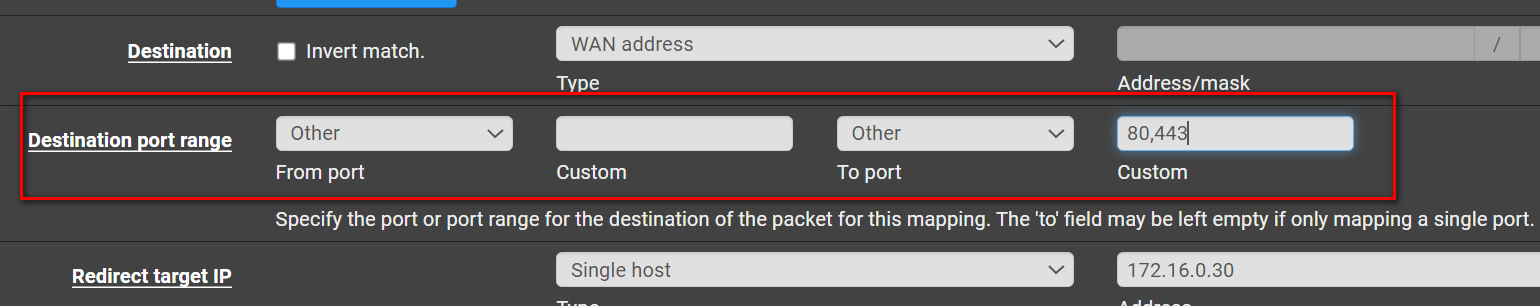
Should I disable NAT Reflection?
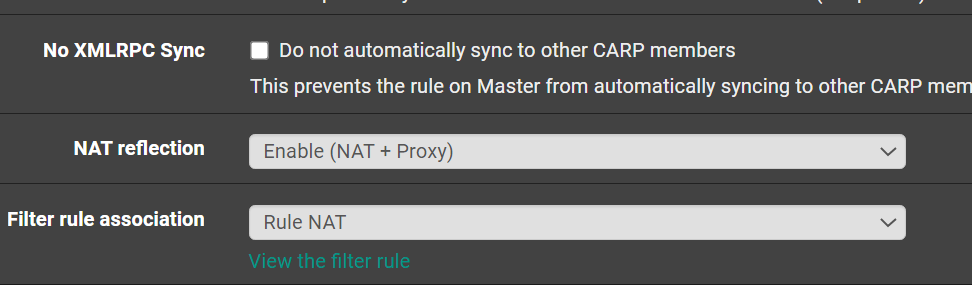
-
No. You can only enter one port there or an alias that has multiple ports.
If you only need 2 ports forwarding just make one port forward for each port.
-
@stephenw10
My understanding is create 2 entries - As an example for 80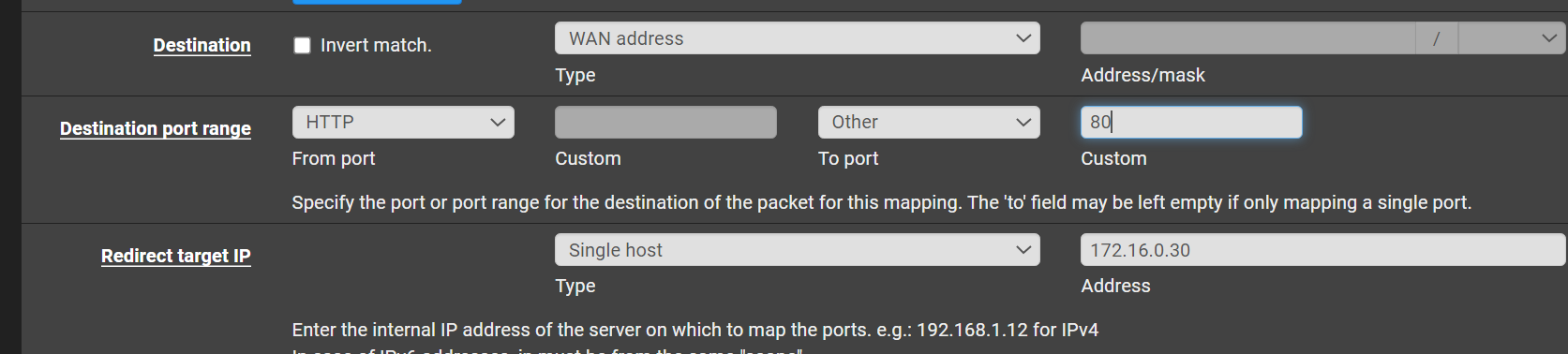
And do the above one for 443 as well
And for both NAT reflection must be enabled I guess (to access from outside) - kindly confirm
-
Yes. Though you can just put 'http' in both from and to port fields, port 80 is the http port.
NAT reflection allows internal clients to access the resource using the external destination. It's not required for access from external clients.
Steve
-
@stephenw10
I disabled NAT reflection and this is how it looks now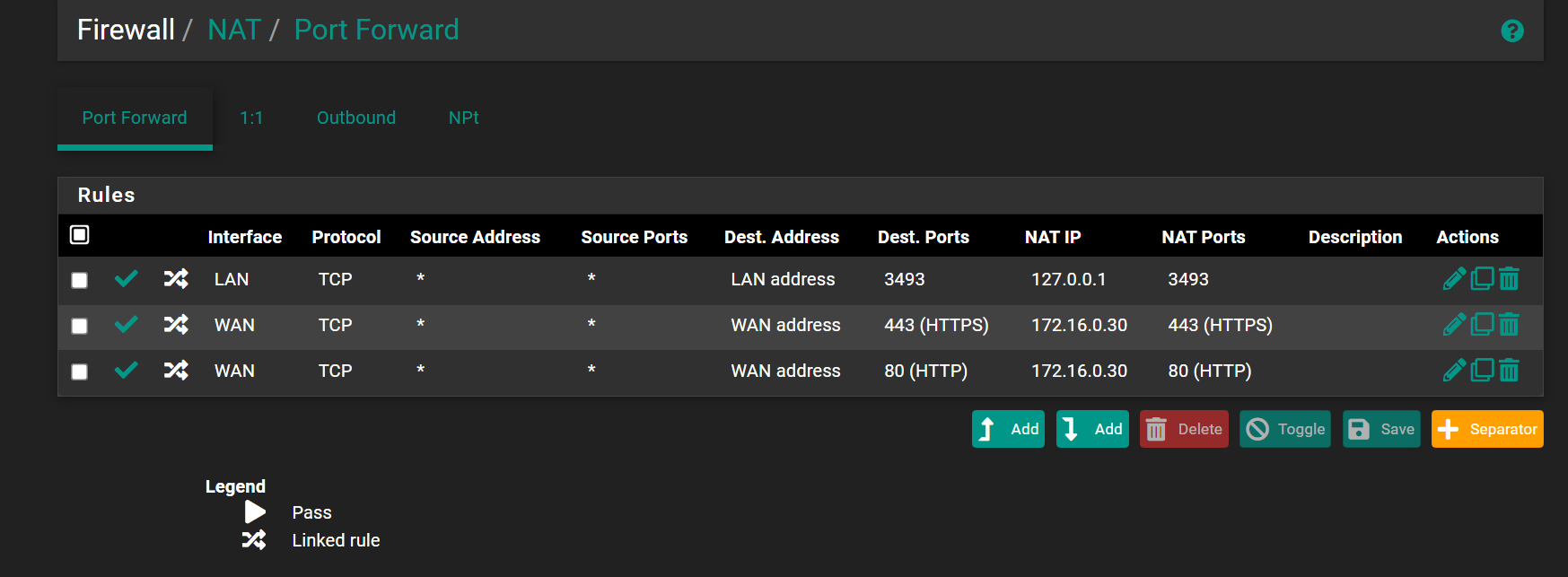
However now if I enter https://mysubdomain.mydomain.com I see pfsense login not 172.16.0.30?
I want https://mysubdomain.mydomain.com to point to 172.16.0.30
Any changes I must do to accomplish this?
-
@netboy Presumably you're testing from inside the network if disabling it changes anything. ("not required for access from external clients")
Consider split DNS:
https://docs.netgate.com/pfsense/en/latest/nat/reflection.html#split-dns
Or just use reflection as discussed on that page. -
@steveits You are right.....
When I used tor browser .....https://subdomain.mydomain.com points to 172.16.0.30!!
All good - Thanks a ton
cat /var/etc/xinetd.conf output is blanks
-
Yeah, if you need to access the resources from inside using the external URL it's better to use split DNS:
https://docs.netgate.com/pfsense/en/latest/recipes/port-forwards-from-local-networks.html#method-2-split-dns
But if you need to use NAT reflection you can almost always use PureNAT mode rather than NAT+Proxy. PureNAT mode does not use xinetd (nc) instances.Steve