pfSense and NAS port opening
-
Hello a,
I have a NAS that through its proprietary app (Synology Drive Client) backs up live certain folders of some PCs when they are modified. The problem is that to do this, since the possibility of creating a VPN for a single port has not yet been invented, I am forced to open one port to the world. Not knowing pfSense very well (I'm a novice) I was wondering if there was any safe (or almost safe) method to make a port public. Obviously the IPs I work with are dynamic, so I have no way of checking where the accesses come from.
Thank you. -
@airone-0 so your saying these pc are out on the internet, and not where your nas is?
-
@airone-0
I'd recommend one of these methods mentioned here in the docs: Virtual Private Networks -
@airone-0 as @viragomann mentions you could setup a vpn to pfsense for allowing this - but also pretty sure Synology drive client can connect via the quickconnect option, so you really don't need to open any unsolicited inbound traffic on pfsense.
-
@johnpoz said in pfSense and NAS port opening:
so your saying these pc are out on the internet, and not where your nas is?
Some of them can also be on the same network as pfSense and NAS, others around the world.
A VPN connection I don't think is practical because clients would only be allowed access to port XXX and nothing else.
-
Hey,
I recommend VPN as well...
You could open that needed port for Synology's Drive, then this port is open to public...not good.
You could use a VPN. And yes, that means opening another port (for reaching your VPN server). But you could secure access, let's say by using freeRADIUS with 2fa (username, passwort, TOTP) and additionally use pfblocker's IP blocking, so access to your VPN server ports is allowed from certain country-related IP ranges PLUS that access is rather secure thanx to radius with 2fa.Something HAS to be open, otherwise you could not reach it... :)
Just make sure the right ports are opened in the most secure way...Or: use Synology's Quick Connect as relay (which I personally do not like that much)
btw:
@airone-0 said in pfSense and NAS port opening:
A VPN connection I don't think is practical because clients would only be allowed access to port XXX and nothing else.
I do not get your point there. Clients could access your LAN / vlans...you can then go and create firewall rules, so that your VPN clients only reach those subnets / vlans you chose to allow...or am I misunderstanding your point?
-
@the-other said in pfSense and NAS port opening:
Or: use Synology's Quick Connect as relay (which I personally do not like that much)
Not a fan either to be honest, but it should be slightly more secure then just opening up any IP on the planet to hit your nas on that service port for DS..
And makes for simple connectivity with all kinds of different devices, be it phone or pc, etc.
The most secure method would be via vpn to pfsense, be it openvpn, wireguard, tailscale, etc. This allows for secure auth before anyone could talk to your nas DS port.. But it does increase the complexity of connecting a remote device.
-
@johnpoz yeah, that is a good (and important) point you mentioned there:
it is certainly more complex to set up and configure.
On the other hand, once set it usually just works and setting up a connection is done easily.
Still: I would set it up as mentioned...VPN, if needed additional auth via FreeRADIUS, firewall rules...helps me sleep better :) -
Yes, I think I'll follow your advice and choose the VPN route, even if it's a bit more complex than just opening the port. I was now doing some tests with only the port open and I was noticing that outside the Netgate network the connection works without problems, but from inside the clients are unable to connect to the NAS via DNS. But that's another problem...
-
@airone-0 said in pfSense and NAS port opening:
but from inside the clients are unable to connect to the NAS via DNS
You would want to make sure whatever your using for FQDN resolves to the internal IP when your internal, or use nat reflection if its going to resolve to your public IP.
-
@johnpoz hey there,
And that is also another advantage using vpn IMHO...you only need to configure your devices for internal IPs, no matter going via vpn or your (w)lan homenetwork.
:) -
Still: I would set it up as mentioned...VPN, if needed additional auth via FreeRADIUS, firewall rules...helps me sleep better :)
You may be best sorted in my eyes with a VPN to
your pfSense at home and set up the public IP only
on the pfSense and forward it from there to your NAS
with an internal private IP address.You may be perhaps need a so called jump host in the internet that is connected to your pfSense and able to
reach for you from else where.One open port can be ending for your NAS being a virus puller or spam puller at least. Stable, even online,....
-
Obviously the IPs I work with are dynamic, so I have no way of checking where the accesses come from.
If you can put a Dynamic DNS client on those PCs you could allow access by firewall rule using the hostnames.
I’m assuming the connection is encrypted for whatever you’re doing.
-
@steveits said in pfSense and NAS port opening:
If you can put a Dynamic DNS client on those PCs you could allow access by firewall rule using the hostnames.
I use to do this for my son's network when I managed his wifi unifi APs from my controller. It is a viable option.
-
@steveits said in pfSense and NAS port opening:
If you can put a Dynamic DNS client on those PCs you could allow access by firewall rule using the hostnames.
Excellent idea, but at this point could I also avoid using the VPN by directly controlling who accesses the port or would I still risk a spoofing attack?
-
@airone-0 the access would be locked down to what the fqdn resolves to, so say 1.2.3.4 for example.
If someone was able to get that fqdn to resolve to their IP 2.3.4.5 then sure the firewall would allow the traffic. But normally dynamic dns has some auth method. Also how would this would be attacker even know what fqdn to spoof?
If someone probed your port on your wan IP, the traffic would just get dropped - they wouldn't even know the port is open because their IP is not one you allow.
Use a dynamic dns that has good auth - cloudflare for example free.. You just need to own a domain you host dns with cloudflare to use it. Pretty sure they do some filtering on bad guys IP for sure, etc.
I use it currently to update some fqdn my users use to access some services I host off my connection. My wan IP doesn't change very often, but now and then the ISP does something, latest was when the isp merged with another company and the IP ranges got changed, etc.
-
Hello @johnpoz,
great, better that way. But now I have to solve the problem of the DNS used in the local network. As long as the PC is outside the pfSense network and connects to for example myDDNS.synology.com, there is no problem. But when the PC app tries to make the same connection from within the Netgate's network, the connection fails. Strangely, even if I enter the WAN IP instead of the DNS, the connection fails. At first I thought it was a DNS resolution problem, but if even with the IP it doesn't connect the problem must be elsewhere, but I don't know where.
-
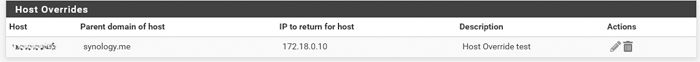
@airone-0 Port forwarding needs reflection enabled on the rule, or better yet split DNS via a host override to point to the LAN IP.
-
@airone-0 said in pfSense and NAS port opening:
even if I enter the WAN IP instead of the DNS
Yeah that would fail unless you setup nat reflection, but as SteveITS mentions split dns is better solution normally.
So something.ddns.tld out on the internet resolves to public 1.2.3.4, but internally when your devices are asking your local dns then something.ddns.tld should resolve to say 192.168.1.100 (the local IP of your nas).. This is accomplished with a simple host override.
If your devices are not using your local dns, then yeah nat reflection would be needed to be setup.
-
To tell the truth yesterday I had tried, but having had no result I had deleted it. I've re-entered it now, set the dns and local ip address of the NAS, but nothing has changed.
It's possible that being a beginner with these issues I'm doing something wrong. Anyway, thank you for the support you are giving me.