pfSense and NAS port opening
-
Yes, I think I'll follow your advice and choose the VPN route, even if it's a bit more complex than just opening the port. I was now doing some tests with only the port open and I was noticing that outside the Netgate network the connection works without problems, but from inside the clients are unable to connect to the NAS via DNS. But that's another problem...
-
@airone-0 said in pfSense and NAS port opening:
but from inside the clients are unable to connect to the NAS via DNS
You would want to make sure whatever your using for FQDN resolves to the internal IP when your internal, or use nat reflection if its going to resolve to your public IP.
-
@johnpoz hey there,
And that is also another advantage using vpn IMHO...you only need to configure your devices for internal IPs, no matter going via vpn or your (w)lan homenetwork.
:) -
Still: I would set it up as mentioned...VPN, if needed additional auth via FreeRADIUS, firewall rules...helps me sleep better :)
You may be best sorted in my eyes with a VPN to
your pfSense at home and set up the public IP only
on the pfSense and forward it from there to your NAS
with an internal private IP address.You may be perhaps need a so called jump host in the internet that is connected to your pfSense and able to
reach for you from else where.One open port can be ending for your NAS being a virus puller or spam puller at least. Stable, even online,....
-
Obviously the IPs I work with are dynamic, so I have no way of checking where the accesses come from.
If you can put a Dynamic DNS client on those PCs you could allow access by firewall rule using the hostnames.
I’m assuming the connection is encrypted for whatever you’re doing.
-
@steveits said in pfSense and NAS port opening:
If you can put a Dynamic DNS client on those PCs you could allow access by firewall rule using the hostnames.
I use to do this for my son's network when I managed his wifi unifi APs from my controller. It is a viable option.
-
@steveits said in pfSense and NAS port opening:
If you can put a Dynamic DNS client on those PCs you could allow access by firewall rule using the hostnames.
Excellent idea, but at this point could I also avoid using the VPN by directly controlling who accesses the port or would I still risk a spoofing attack?
-
@airone-0 the access would be locked down to what the fqdn resolves to, so say 1.2.3.4 for example.
If someone was able to get that fqdn to resolve to their IP 2.3.4.5 then sure the firewall would allow the traffic. But normally dynamic dns has some auth method. Also how would this would be attacker even know what fqdn to spoof?
If someone probed your port on your wan IP, the traffic would just get dropped - they wouldn't even know the port is open because their IP is not one you allow.
Use a dynamic dns that has good auth - cloudflare for example free.. You just need to own a domain you host dns with cloudflare to use it. Pretty sure they do some filtering on bad guys IP for sure, etc.
I use it currently to update some fqdn my users use to access some services I host off my connection. My wan IP doesn't change very often, but now and then the ISP does something, latest was when the isp merged with another company and the IP ranges got changed, etc.
-
Hello @johnpoz,
great, better that way. But now I have to solve the problem of the DNS used in the local network. As long as the PC is outside the pfSense network and connects to for example myDDNS.synology.com, there is no problem. But when the PC app tries to make the same connection from within the Netgate's network, the connection fails. Strangely, even if I enter the WAN IP instead of the DNS, the connection fails. At first I thought it was a DNS resolution problem, but if even with the IP it doesn't connect the problem must be elsewhere, but I don't know where.
-
@airone-0 Port forwarding needs reflection enabled on the rule, or better yet split DNS via a host override to point to the LAN IP.
-
@airone-0 said in pfSense and NAS port opening:
even if I enter the WAN IP instead of the DNS
Yeah that would fail unless you setup nat reflection, but as SteveITS mentions split dns is better solution normally.
So something.ddns.tld out on the internet resolves to public 1.2.3.4, but internally when your devices are asking your local dns then something.ddns.tld should resolve to say 192.168.1.100 (the local IP of your nas).. This is accomplished with a simple host override.
If your devices are not using your local dns, then yeah nat reflection would be needed to be setup.
-
To tell the truth yesterday I had tried, but having had no result I had deleted it. I've re-entered it now, set the dns and local ip address of the NAS, but nothing has changed.
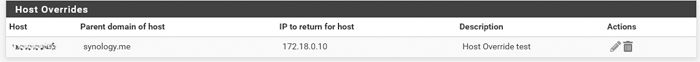
It's possible that being a beginner with these issues I'm doing something wrong. Anyway, thank you for the support you are giving me.
-
@airone-0 so make sure your client is actually using pfsense as its dns, that its not pointing else where, or if app or browser sort of app make sure its not using doh
Also validate that your host override is working, use your fav dns tool, host, nslookup, dig and do a query for that fqdn does it return the IP you put in for the override.
-
The IP I entered in the override is the local one of the NAS, the DNS entered in the override (host name + host domain) is currently resolved with the same IP reported for the WAN on the dashboard. The PC I'm using now is connected to the Netgate LAN (192.168.0.x) and via local addresses it also see the NAS and its servers, while the NAS is connected to LAN2 (172.18.0.x). If I disconnect the local network from this PC and connect it to an external network (via mobile wifi), the App on the PC immediately connects to the NAS server. I hope I have explained the situation clearly.
-
@airone-0 said in pfSense and NAS port opening:
currently resolved with the same IP reported for the WAN
So then your PC is either not using pfSense for DNS, or your PC is caching the answer (Windows: ipconfig /flushdns) or the override is not configured correctly.
Run "nslookup hostname ip-of-pfsense" and see what it answers.
Screenshot of the override?
You may also need a firewall rule allowing from LAN to the NAS_IP:port although by default all traffic is allowed on LAN.
-
@steveits said in pfSense and NAS port opening:
Screenshot of the override?
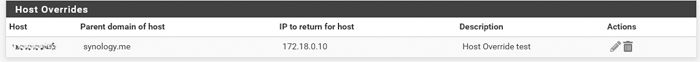
@steveits said in pfSense and NAS port opening:
Run "nslookup hostname ip-of-pfsense" and see what it answers.
PS C:> nslookup hostname xx.yy.zz.218 Server: host-xx-yy-zz-218.retail.telekom.it Address: xx.yy.zz.218 *** host-xx-yy-zz-218.retail.telekomi.it non è in grado di trovare hostname: Non-existent domain PS C:>Well, now what? Why "Non-existent domain"?
-
@airone-0 Sorry, I meant to use your hostname and the LAN IP of pfSense. So
nslookup yours.synology.me 192.168.0.1
that will show you what pfSense is providing for DNS.
-
@airone-0 said in pfSense and NAS port opening:
xx.yy.zz.218
That is IP address of pfsense.. You didn't even ask for the fqdn you put in which is something.synology.me
Here..
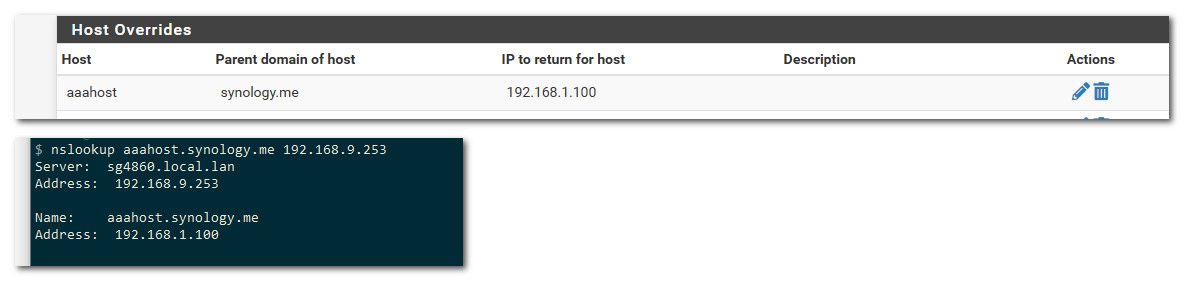
Where 192.168.9.253 is the IP address of my pfsense where unbound (resolver) where I put in the host override.
When you don't actually use the actual fqdn, host.doman.tld with nslookup it quite often will use a search suffix and ask for whatever domain your machine is in..
example see where I only ask for aaahost, but the question that gets asked to dns is with my local domain name attached.
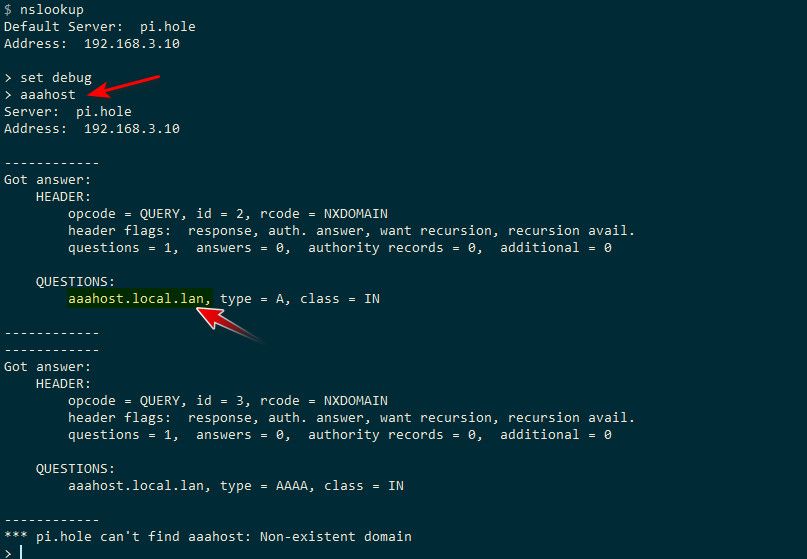
set debug shows you the details of what is being asked, what is returned, etc.
you can also set where you ask other then your default NS.
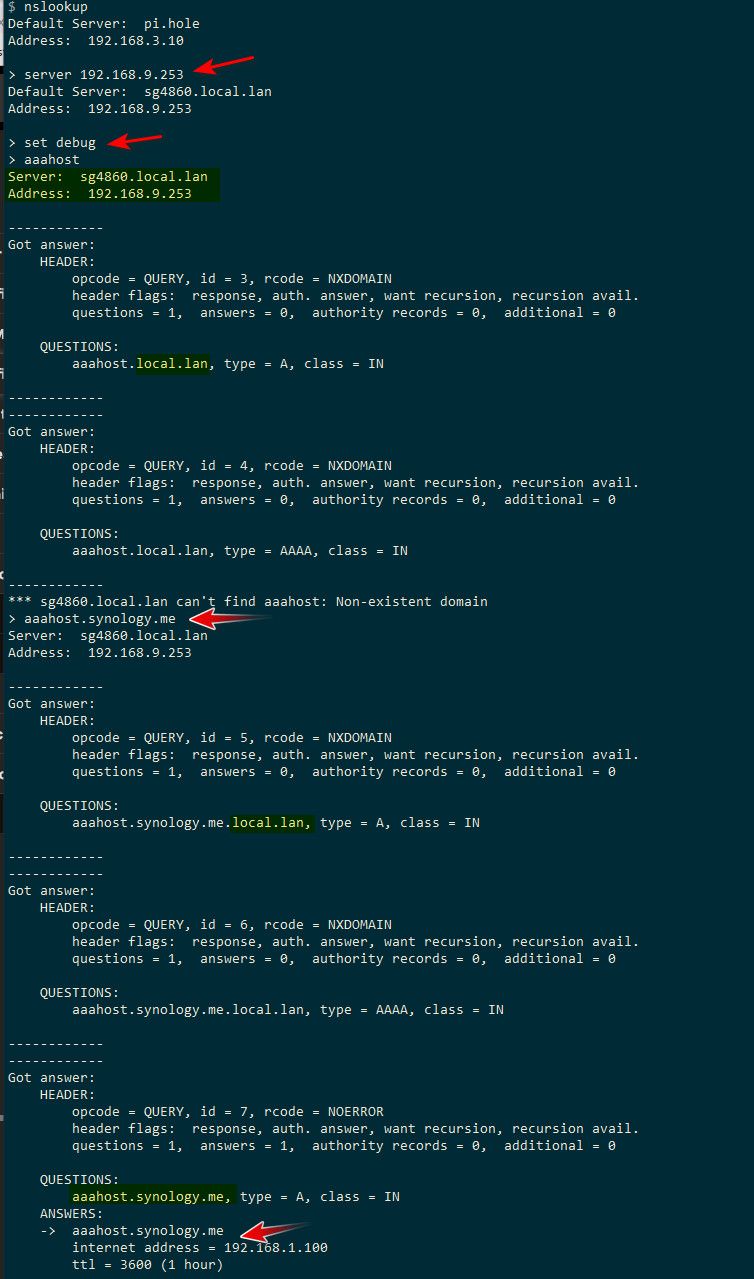
-
Now I'm in total confusion, too much information.
Anyway...> myname.synology.me Server: host-xx-yy-zz-218.retail.telekom.it Address: xx.yy.zz.218 ------------ Got answer: HEADER: opcode = QUERY, id = 7, rcode = NXDOMAIN header flags: response, want recursion, recursion avail. questions = 1, answers = 0, authority records = 1, additional = 0 QUESTIONS: myname.synology.me.NetgateDomain, type = A, class = IN AUTHORITY RECORDS: -> (root) ttl = 2855 (47 mins 35 secs) primary name server = a.root-servers.net responsible mail addr = nstld.verisign-grs.com serial = 2023042800 refresh = 1800 (30 mins) retry = 900 (15 mins) expire = 604800 (7 days) default TTL = 86400 (1 day) ------------ ------------ Got answer: HEADER: opcode = QUERY, id = 8, rcode = NXDOMAIN header flags: response, want recursion, recursion avail. questions = 1, answers = 0, authority records = 1, additional = 0 QUESTIONS: myname.synology.me.NetgateDomain, type = AAAA, class = IN AUTHORITY RECORDS: -> (root) ttl = 2855 (47 mins 35 secs) primary name server = a.root-servers.net responsible mail addr = nstld.verisign-grs.com serial = 2023042800 refresh = 1800 (30 mins) retry = 900 (15 mins) expire = 604800 (7 days) default TTL = 86400 (1 day) ------------ ------------ Got answer: HEADER: opcode = QUERY, id = 9, rcode = NOERROR header flags: response, auth. answer, want recursion, recursion avail. questions = 1, answers = 1, authority records = 0, additional = 0 QUESTIONS: myname.synology.me, type = A, class = IN ANSWERS: -> myname.synology.me internet address = 172.18.0.10 ttl = 3600 (1 hour) ------------ ------------ Got answer: HEADER: opcode = QUERY, id = 10, rcode = NOERROR header flags: response, auth. answer, want recursion, recursion avail. questions = 1, answers = 0, authority records = 0, additional = 0 QUESTIONS: myname.synology.me, type = AAAA, class = IN ------------ Nome: myname.synology.me Address: 172.18.0.10 >It would appear that the binding set by Host Override between myname.synology.me and the internal IP of the NAS exists (last two lines). Big problem for me, how do we get out of this?
-
@airone-0 said in pfSense and NAS port opening:
Big problem for me, how do we get out of this?
out of what? That seems like working fine to me.. Windows loves to add suffix to queries - you could put a . on the end of your fqdn if you don't want to let windows add its search suffix domains.
Or you could setup windows NOT to ever do that..