[Solved] Problems with Proxmox/vlan-tagging/SG-2100 Switch config
-
@furom If you’re trying to create a separate interface this guide will do it: https://docs.netgate.com/pfsense/en/latest/solutions/netgate-2100/configuring-the-switch-ports.html
If the server is connected directly to the 2100 you don’t need to tag the packets. The guide assumes this is a separately wired network hence “4,5t”.
-
@steveits said in Problems with Proxmox/vlan-tagging/SG-2100 Switch config:
If the server is connected directly to the 2100 you don’t need to tag the packets. The guide assumes this is a separately wired network hence “4,5t”.
Yes, PVE is directly connected, and could probably use native lan on the port, but would still need the vlan tags for it's virtual machines, as they live on different networks. I tried the config you suggested and did not get it to work any better unfortunately. The way Proxmox is configured now, it uses a tag on its own interface, and are also supposed to make all the other tags available to the VMs to use. The latter is is not the case at the moment...
-
This isn't working right. Would this config create a "trunk" of tagged vlans on ports 3 & 4 on the the 2100?
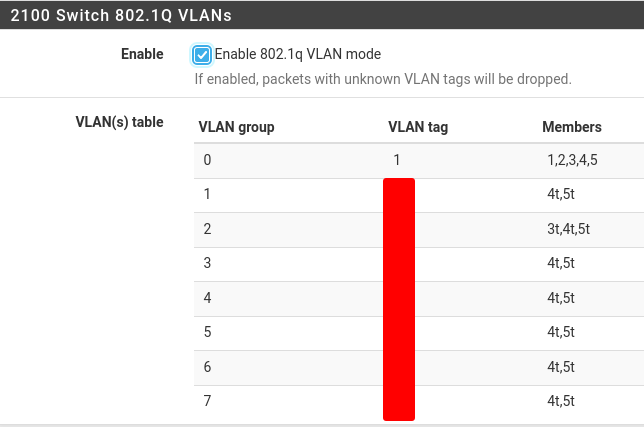
Sorry for going at it, but really need this to work... :/ Any hint would be nice, thanks -
@furom
Assuming pfSense is configured well, how did you configure Proxmox?
What is your intention with the VLAN on Proxmox? Assigning it to the host or to VMs? -
@viragomann said in Problems with Proxmox/vlan-tagging/SG-2100 Switch config:
@furom
Assuming pfSense is configured well, how did you configure Proxmox?
What is your intention with the VLAN on Proxmox? Assigning it to the host or to VMs?Yes, I want to assign vlans to the guest VMs. I used what I hoped should work from Proxmox manual, like this;
auto lo iface lo inet loopback iface eno1 inet manual auto vmbr0.5 iface vmbr0.5 inet static address 10.10.10.2/24 gateway 10.10.10.1 auto vmbr0 iface vmbr0 inet manual bridge-ports eno1 bridge-stp off bridge-fd 0 bridge-vlan-aware yes bridge-vids 2-4094 -
@furom
Seems to be a copy of the example from the Proxmox doc.
I expect this to work, of course, but the question was your actual configuration.And all it shows, is the VLAN ID 5 configured on the host.
But you say, you want to assign VLANs to the VMs. Which method? To you want Proxmox to do the VLAN tag tagging and untagging or do you want to configure VLANs within the VMs?What exactly does not work?
-
@viragomann said in Problems with Proxmox/vlan-tagging/SG-2100 Switch config:
@furom
Seems to be a copy of the example from the Proxmox doc.True, it is a copy of that. My config is exactly the same, apart from the vlan number and IP, everything else is identical.
By not working; If I try to install a VM using Ubuntu ISO for example, and have assigned a vlan tag to the machines NIC, it will not get an IP during the DHCP provisioning step. I even add the same vlan tag, but nothing.
Oh, so that only configures IP for the host... ? Then I misunderstood. An have no clue what I am missing for VMs to take part of provisioned vlans....
I would like to be able to assign a VMs NIC a vlan tag, essentially untagging it for the VM
-
@furom
The "bridge-vlan-aware yes" in the bridge settings gives you the VLAN option in the VM network settings. Check VLAN there and enter the ID.
This way Proxmox does the tagging and untagging and the VM OS is not aware of the VLAN.
It's like you can do on a VLAN capable switch. -
@viragomann said in Problems with Proxmox/vlan-tagging/SG-2100 Switch config:
@furom
The "bridge-vlan-aware yes" in the bridge settings gives you the VLAN option in the VM network settings. Check VLAN there and enter the ID.
This way Proxmox does the tagging and untagging and the VM OS is not aware of the VLAN.
It's like you can do on a VLAN capable switch.Oh... So essentially this?
bridge-vlan-aware yes bridge-vids 2 5 10I thought the notation "2-4094" meant every vlan between 2 and 4094... I will try this at the earliest, thanks for sharing! :)
-
No, the VM part is to be done in the GUI.
I thought the notation "2-4094" meant every vlan between 2 and 4094.
That's correct. With this option you can limit the VLANs to certain on the brigde. But for your purpose you can also keep the whole range here, I think.
-
@viragomann Then I'm confused. That is how I have done it... Server broke down on me so can't give screenshots, but the dialog you show is the one when configuring the VM, correct? In Hardware, on the NIC, I have "... tag=45" for instance. But it will not give the machine an IP on that network. That is why I thought the Proxmox config was off. But with what you say, Proxmox config is fine... Then the only thing left would be pfSense and/or the Netgate switch...
-
@furom Is your PVE connected directly to the 2100 or through a second switch?
-
@rcoleman-netgate said in Problems with Proxmox/vlan-tagging/SG-2100 Switch config:
@furom Is your PVE connected directly to the 2100 or through a second switch?
Yes, PVE is directly connected to the 2100's built-in switch port #3, (pic above)
-
This is the config of one VM which won't get an IP on defined vlan (in fact no IP at all to be exact);
And the Proxmox config;auto lo iface lo inet loopback iface eno1 inet manual auto vmbr0.22 iface vmbr0.22 inet static address 192.168.22.2/28 gateway 192.168.22.1 auto vmbr0 iface vmbr0 inet static bridge-ports eno1 bridge-stp off bridge-fd 0 bridge-vlan-aware yes bridge-vids 2-500Edit: I just now tried editing the last line, just specifying two vland id's, like "bridge-vids 30 44", but still refuse to work...
What am I missing? I read and read and test, still not working. And I'm repeatedly told I won't need any rules for DHCP...
-
@furom Do an unfiltered packet capture on the VLAN on pfSense (https://docs.netgate.com/pfsense/en/latest/diagnostics/packetcapture/index.html) and filter against UDP 68 with a limit of 0 packets and see if the traffic is even getting there... or if it is getting there and responding...
I suspect the issue is in your PVE config
-
@rcoleman-netgate said in Problems with Proxmox/vlan-tagging/SG-2100 Switch config:
@furom Do an unfiltered packet capture on the VLAN on pfSense (https://docs.netgate.com/pfsense/en/latest/diagnostics/packetcapture/index.html) and filter against UDP 68 with a limit of 0 packets and see if the traffic is even getting there... or if it is getting there and responding...
I suspect the issue is in your PVE config
Just so I get this right, I am supposed to do this from a VLAN that is not working, or from pfSense? I'm not used capturing other than quite simple tcpdumps, but will figure it out I hope :)
Edit: I tried this from pfSense, and started a machine that should've requested an IP - nothing.
[root@pfSense ~]# tcpdump -ni mvneta1.30 udp port 68 -
@furom the GUI in pfSense makes the PCAP easier... that's why I linked you to how to perform the packet capture in our documentation.
-
@rcoleman-netgate Sorry. I used the GUI and I can see Proxmox trying something from its own GUI, I don't get anything in the PCAP....
-
@furom
You have enabled the Firewall on the VMs virtual NIC. Did you also configure it properly to allow access? -
@viragomann said in Problems with Proxmox/vlan-tagging/SG-2100 Switch config:
@furom
You have enabled the Firewall on the VMs virtual NIC. Did you also configure it properly to allow access?That is on by default I think, but turning it off makes no difference unfortunately, was hoping it would... Still not seeing any captured packets though. Something is quite weird. Even tried "promiscous" mode, leaving Port blank... That should show something, right?
Edit: Only when I select WAN as interface I get some capture... :/ I don't get this. If I remove port and protocol I get some activity, but none on the one for Proxmox VM..
Removing Port & protocol on vlan 30 on which I am trying to setup an ubuntu, this was all it captured;
19:25:03.205680 IP 192.168.1.3 > 224.0.0.1: igmp 19:26:03.820911 IP 192.168.1.3 > 224.0.0.1: igmp