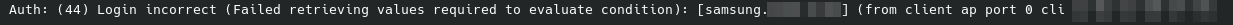
freeradius / eap-tls / Android 13
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom said in freeradius / eap-tls / Android 13:
(4) eap_tls: (TLS) EAP Done initial handshake
(4) eap_tls: (TLS) recv TLS 1.2 Alert, fatal internal_error
(4) eap_tls: ERROR: (TLS) Alert read:fatal:internal error
(4) eap_tls: (TLS) Server : Need to read more data: error
(4) eap_tls: ERROR: (TLS) Failed reading from OpenSSL: error:14094438:SSL routines:ssl3_read_bytes:tlsv1 alert internal error
(4) eap_tls: (TLS) In Handshake Phase
(4) eap_tls: (TLS) Application data.
(4) eap_tls: ERROR: (TLS) Cannot continue, as the peer is misbehaving.Well that for sure would explain why your eap-tls is not working... But your saying you got your old tablet working.. Are you not using the same certs that you used for server and same CA?
So something wrong with the client cert, or how the client is sending it?
Glad to hear it makes some sense at least. Not looking great, so much I do understand... :)
No, I created a second cert for the new tablet as I may want them both still...
I now copied the cert I used on the old tablet (working with WPA2-Enterprise/eap-tls/Android 7) to the new one, and errors are identical
-
@furom Perhaps a fragmentation problem ?
Try to edit eap.conf and set fragment_size = 1344A nanoHD and a unifi6-lite only worked with wpa2-enterprise after doing this change.
-
@furom I looked up if they plan on updating my P11 plus to 13, and doesn't look like it - they list 12 as last, and actually eol security updates 11/23, so that not good.. But the little * says
Lenovo tablets get updates for security issues documented in Android Security bulletin.
Its only my train tablet so not too worried about it, but would be nice if could update to 13 and test..
So this tablet doesn't even work with wpa2 enterprise? I would prob just go with wpa3 personal and call it a day then.. wpa3 personal brings "Simultaneous Authentication of Equals (SAE)." so that is good for any sort of offline attack on the password.
-
@mcury said in freeradius / eap-tls / Android 13:
eap.conf and set fragment_size = 1344
Mine is set to
fragment_size = 1024Not having any issues.. I do not have a U6-lite, and furom has a uap-ac-lite, which I also have.. I am not seeing any issues with connecting on any of my ap, the lite, the pro or the lr - all just uap-ac, no U6...
I do have a flex HD I could test with, but its currently inactive..
-
@johnpoz said in freeradius / eap-tls / Android 13:
Not having any issues.. I do not have a U6-lite, and furom has a uap-ac-lite, which I also have.. I am not seeing any issues with connecting on any of my ap, the lite, the pro or the lr - all just uap-ac, no U6...
I do have a flex HD I could test with, but its currently inactive..I did have issues with the default values..
At that time, I decided to perform a packet capture and noticed a lot of EAP packets, when it shouldn't have that amount.
After some research, found that changing that value to 1344 fixed all the issues.
https://lists.freeradius.org/pipermail/freeradius-users/2012-January/058297.html
-
@mcury said in freeradius / eap-tls / Android 13:
@furom Perhaps a fragmentation problem ?
Try to edit eap.conf and set fragment_size = 1344A nanoHD and a unifi6-lite only worked with wpa2-enterprise after doing this change.
It would be interesting to test... Where do I find "eap" in freeRadius on pfSense?
-
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom the eap file would be here
/usr/local/etc/raddb/mods-enabled
@mcury the way I read what you linked seems too says to lower it ;) hehe
"The simplest thing to try is to see eap.conf, and change fragment_size
to something smaller."Well, I set it through the gui and restarted in debug mode. Now verified the value in the file file indeed reads "1344", but same error unfortunately.
It was a good try, thanks for that
-
@johnpoz said in freeradius / eap-tls / Android 13:
@mcury the way I read what you linked seems too says to lower it ;) hehe
"The simplest thing to try is to see eap.conf, and change fragment_size
to something smaller.Indeed, but that pointed me to the right direction, from there I decided to perform a packet capture.
Once I set it to 1344, it worked, no more fragmentation.I suppose it was here that I got the suggestion for this value from:
https://community.ui.com/questions/Issue-with-WPA2-Enterprise-Across-sites/7070e262-c2c6-403b-a61d-a98ad3b3db53 -
@mcury that seems to be talking about
"Framed-MTU and set it to 1344 and issue was resolved."
That is different than the fragment size.. Pretty sure that framed -mtu is calculated, I see different values when in debug mode
(3) Framed-MTU = 1400
Different one
(5) User-Name = "tablet.home.arpa"
(5) Framed-MTU += 994Could you post your full output when you run in debug mode @furom attach as a .txt file.
-
Could this be of relevance?
No EAP Start, assuming it's an on-going EAP conversationJust prior to that it tries to match an email (containing a "@") and fails. So perhaps a username must be an email? Worth a try I suppose
-
@furom said in freeradius / eap-tls / Android 13:
So perhaps a username must be an email? Worth a try I suppose
I see the same notices.. And not having any issue..
(4) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/default (4) authorize { (4) [preprocess] = ok (4) [chap] = noop (4) [mschap] = noop (4) [digest] = noop (4) suffix: Checking for suffix after "@" (4) suffix: No '@' in User-Name = "tablet.home.arpa", skipping NULL due to config. (4) [suffix] = noop (4) ntdomain: Checking for prefix before "\" (4) ntdomain: No '\' in User-Name = "tablet.home.arpa", skipping NULL due to config. (4) [ntdomain] = noop (4) eap: Peer sent EAP Response (code 2) ID 192 length 82 (4) eap: No EAP Start, assuming it's an on-going EAP conversation (4) [eap] = updated (4) files: users: Matched entry tablet.home.arpa at line 17 (4) [files] = ok -
@johnpoz said in freeradius / eap-tls / Android 13:
(3) Framed-MTU = 1400
This value is set in eap.conf, inside: tls-config tls-common {
# fragment_size = 1024
fragment_size = 1344 -
@mcury Your 2nd link talked about editing the framed-mtu, not the fragment size.. But I believe the framed mtu is normally calculated I thought, I sure don't have a framed-mtu in my eap file, and its seems to be calculating the different framed mtu size based on what size its seeing.
I don't really think its related to that - but something with his android version, seems their are a lot of discussion about android 11 or above and wpa enterprise.. What I have seen seems to be should have a problem in 12 as well. But I think some of these things are handled by the maker changes to their release for their devices.
I am using a lenovo with 12, and @furom is using a samsung with 13.. etc..
What versions of android are you using @mcury and your using eap-tls?
-
@johnpoz said in freeradius / eap-tls / Android 13:
Could you post your full output when you run in debug mode @furom attach as a .txt file.
Sure, just trying to figure what to mask...
Edit:
This is the output from the run; out.txt -
@johnpoz said in freeradius / eap-tls / Android 13:
What versions of android are you using @mcury and your using eap-tls?
Tested with Android 11, 12, Macbook air M1, Iphone 11 pro (I'm almost sure it is an iphone 11) and Windows 10 and 11 22H1.
Yes, using EAP-TLS (lets encrypt certificate), I just renew it within a 90 day period and upload it to freeradius server.
Let me enable the server here in my lab so I can post the debug for you.
-
@mcury Yeah not having any issues with iphone (13), ipad (air 5th gen) both running ios 16.5, windows 10 pro 22H2, acer chromebook running whatever latest os is as of day or two ago, and android lenovo p11+ tablet running 12.
Not sure what the issue is with his.. He got his android 7 working with wpa2 enterprise..
@furom did you get your windows test box working? Did you say you found an issue on your switch? So I assume you got your linux and windows and old tablet all working with wpa2-ent
I don't use amce for my certs for eap-tls, all certs via cert manger in pfsense (23.01) using ECDSA with prime256v1 for both the CA and the server and client certs.
Running unifi controller 7.4.156 and uap-ac-pro, lite and lr AP all on 6.5.54 firmware.
edit: here is output of rad -X and my tablet connecting.
Looks like this time it authed connecting to my LR - so have seen valid connections on all 3 of my different APs.
-
@johnpoz said in freeradius / eap-tls / Android 13:
@mcury Yeah not having any issues with iphone (13), ipad (air 5th gen) both running ios 16.5, windows 10 pro 22H2, acer chromebook running whatever latest os is, and android lenovo p11+ tablet running 12.
Not sure what the issue is with his.. He got his android 7 working with wpa2 enterprise..
@furom did you get your windows test box working? Did you say you found an issue on your switch? So I assume you got your linux and windows and old tablet all working with wpa2-ent
I gave up on the windows client. Issue I had with the Netgate switch was not assigning the correct lan, so when corrected old tablet started working (issue then was it did not get an IP), which is the only client so far
-
@furom well maybe you want to try the amce certs, there shouldn't be anyway the tablet doesn't trust those.. Not exactly sure how you get a client cert, would assume just need to be able to validate your fqdn via dns would get you the client cert, just like your server cert, etc.
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom well maybe you want to try the amce certs, there shouldn't be anyway the tablet doesn't trust those.. Not exactly sure how you get a client cert, would assume just need to be able to validate your fqdn via dns would get you the client cert, just like your server cert, etc.
I have though of it before, but that would require a domain and public DNS, which I don't have.
I really do appreciate you guys trying to find some sense in this. There is a beta of Android 14, not sure if I could load that on my tablet, but could be something. Hopefully this would be fixed in 14, but will hold my breath just a little while longer... :)But as said earlier, 13 is a lot pickier with trusting the CA's. So I would not be surprised if 'let's encrypt' would work right away, as it is trusted by browsers by default