Local DNS resolution & blocking of a domain & pfblockerng
-
@droidus the first setting is for pfSense itself.
How are you testing? If a browser you may need to block DOH…see pfSense doc at https://github.com/jpgpi250/piholemanual
-
@droidus well your first rule you show there doesn't show any hits - the 0/0, maybe you have an existing state, maybe you have something above it in floating that allows?
As to dns - maybe your browser is using doh? Many a browsers love to use doh, without much notification to the user if any, etc.
if your client fails to ask pfsense either unbound or dnsmasq that your running on it, then no your host override would never work - again doh comes to mind.
I would use your fav dns client, nslook, dig, host on one of your clients and do a directed query for that fqdn.. Does that answer?
example - I created your same host override.
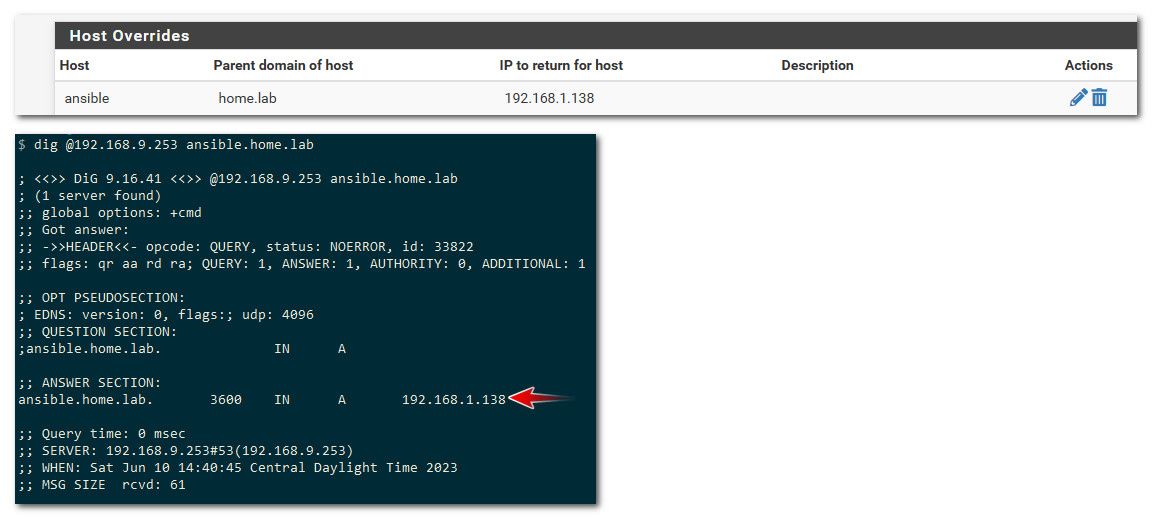
-
@johnpoz I tried pinging, nslookup, and browsing via my browser. None of them was able to resolve. My browser was using DoH, and I turned it off before testing.
I did a check on what DNS servers my client is using, and it has the two public dns servers listed that I have listed in pfsense. -
@droidus said in Local DNS resolution & blocking of a domain & pfblockerng:
it has the two public dns servers listed that I have listed in pfsense.
Well that is wrong - your client should point to pfsense if you want to resolve local resources, or like host overrides - then you can forward to those from unbound (resolver) or dnsmasq (forwarder) if you so desire.
But if your clients are directly asking some public dns - then no your client would never be able to resolve your host overrides.
My clients ask pi-hole, because I like the eye candy it provides. pihole then forwards to pfsense (unbound) and then unbound resolves..
So as you can see, simple nslookup on my pc asks my pihole (192.168.3.10) and I still resolve that host override I created.
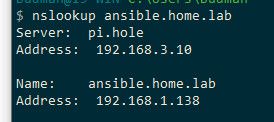
Because the pihole forwards to unbound on pfsense - what you have unbound do either resolve or forward to some outside dns is up to you.. But your clients need to be asking unbound to resolve your host overrides, or any other local resources that unbound would know about, like the IP of pfsense it self via its fqdn..
$ nslookup sg4860.local.lan Server: pi.hole Address: 192.168.3.10 Name: sg4860.local.lan Addresses: 2001:470:snipped:9::253 192.168.9.253 -
@johnpoz said in Local DNS resolution & blocking of a domain & pfblockerng:
So as you can see, simple nslookup on my pc asks my pihole (192.168.3.10) and I still resolve that host override I created.
So I guess that's where the complexity lies. I imagine the flow like this. Client request -> pfsense box -> local checks (like host overrides) (pfblockerng only operates off of the WAN interface, correct?) -> If still not resolved, THEN forward to the public DNS servers defined.
So maybe do I need to have my DHCP server tell clients the DNS server is ONLY pfsense, and then pfsense handles it, and only it knows of the public dns servers?
-
@droidus your last sentence is correct.
pfBlocker has firewall rules via feeds, or DNSBL via the pfSense DNS server.
-
@SteveITS So in theory, shouldn't this work then?
nslookup ansible.home.lab <pfsense-ip>
Instead, it hangs, then fails. -
yes that should work, if you allow access to unbound via firewall rule, its actually running - and you setup the host override in it - have seen users set up the override in dnsmasq (forwarder) when they are using unbound (resolver) or vise versa.
$ nslookup ansible.home.lab 192.168.9.253 Server: sg4860.local.lan Address: 192.168.9.253 Name: ansible.home.lab Address: 192.168.1.138What error do you get - something like this?
$ nslookup ansible.home.lab 192.168.9.254 DNS request timed out. timeout was 2 seconds. Server: UnKnown Address: 192.168.9.254 DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. *** Request to UnKnown timed-out -
@johnpoz All I get is this:
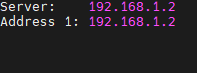
1.2 is the IP of the pfsense box.
Here's the LAN fw rules I have enabled:
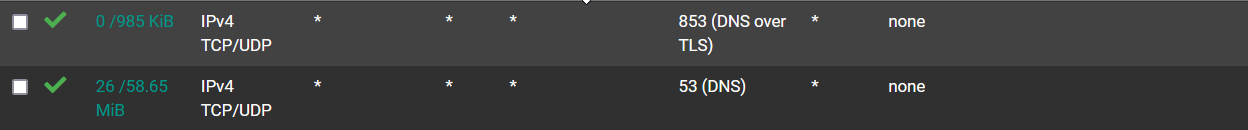
-
@droidus it never comes back with any sort of error or timeout?
just type nslookup, what does it come back with?
example: here I just type nslookup, then change the server and ask for the host override
$ nslookup Default Server: pi.hole Address: 192.168.3.10 > server 192.168.9.253 Default Server: sg4860.local.lan Address: 192.168.9.253 > ansible.home.lab Server: sg4860.local.lan Address: 192.168.9.253 Name: ansible.home.lab Address: 192.168.1.138 >When you change the server to the IP of pfsense, it should come back with pfsense name - if not then that is indication there is something wrong. See how mine comes back with sg4860.local.lan when I change to my pfsense IP.
If unbound doesn't answer, then your client should give a timeout.. If it talked to unbound then you should get some sort of answer, nx, serv fail, something..
For example if I ask for something that just isn't going to resolve..
> lsjfsldf.soldjfsdsldf.com Server: sg4860.local.lan Address: 192.168.9.253 *** sg4860.local.lan can't find lsjfsldf.soldjfsdsldf.com: Non-existent domain -
@johnpoz I'm not sure if this is good practice or not (at least for home use) or even possible, but is it possible to just use "ansible" instead of including the sld&tld? Ie "ansible.home.lab"? For example, I would be able to "ping ansible".
BTW, I got the resolution working now!
-
@droidus if you want to just type in ansible then you could setup your OS to use a search suffix so it would auto add home.lab, and or other suffixes you would use.
So for example if I just ping ansible notice it doesn't work.
$ ping ansible Ping request could not find host ansible. Please check the name and try again.But if I add home.lab to my suffix search.
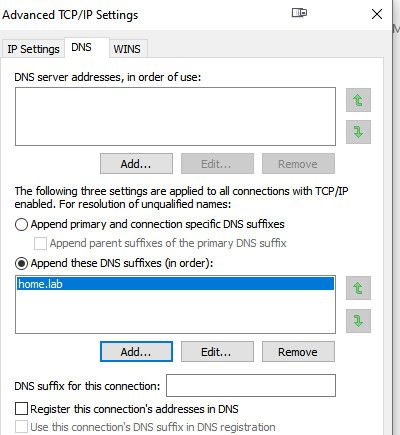
$ ping ansible Pinging ansible.home.lab [192.168.1.138] with 32 bytes of data:What was wrong - what did you change, why wasn't it working before?
-
@johnpoz Got it. Was just wondering if there was any way to modify the request so that I don't have to go to every server/machine and do mods like that. Will have to look into how to do that for linux.... I believe it's the resolv.conf file.
-
@droidus just use fqdn when you looking for something.. Much better than having suffix search, which will quite often add that to every single query be you need them or not..
So for example if you were looking for www.google.com, you end up with an query as well for www.google.com.home.lab
-
Op should modify firewall rule to be more specific and exact...source - LAN.net Destination - THIS FIREWALL
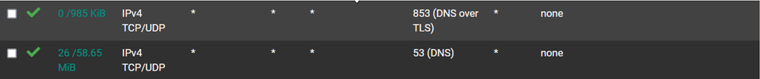
-
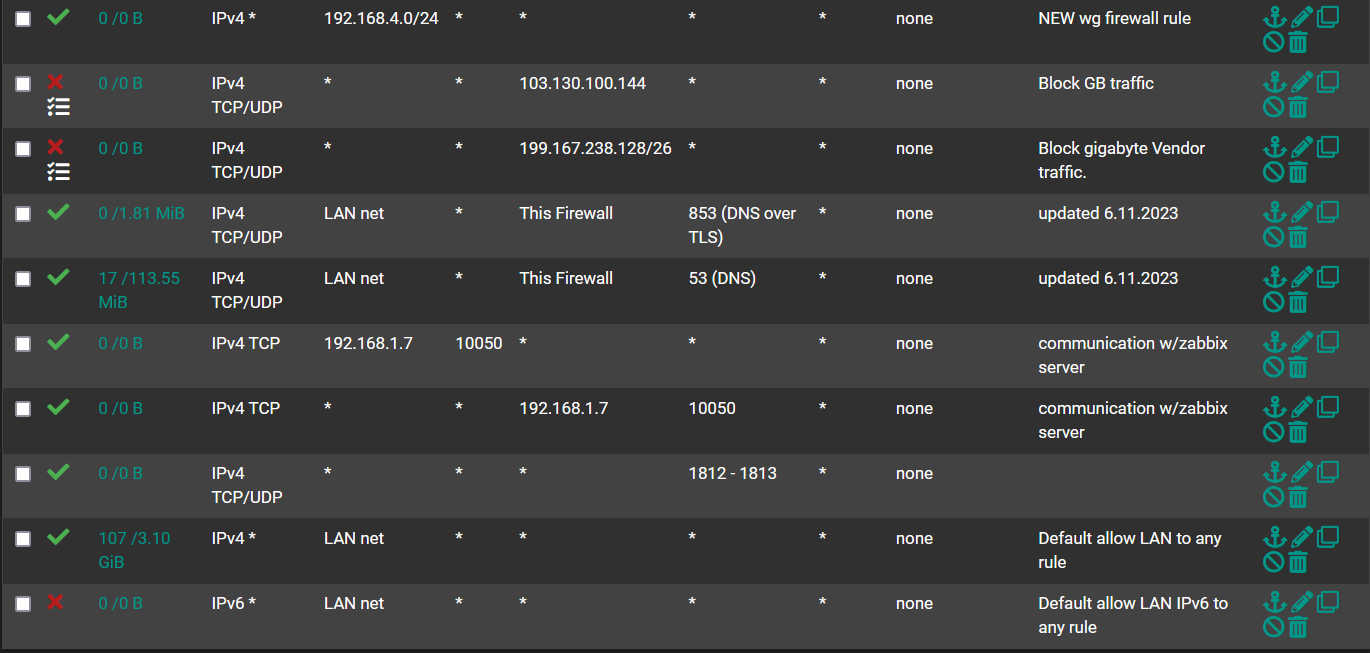
@NollipfSense Got it, thank you. I've updated those two rules. Should I apply the same logic to any other rules, such as the ones surrounding them?:
-
@droidus said in Local DNS resolution & blocking of a domain & pfblockerng:
such as the ones surrounding them?:
You should always be as specific as possible with rules.. This firewall is not specific to be honest. If this is your lan net, that would be the IP it would be talking to for dns, ie lan address. Why would something on your lan be talking to say opt X on pfsense IP for dns? or you wan IP? "This firewall" is an alias that has all the IPs on pfsense.
Do you use this lan net as a transit network? How would something be talking to your lan interface from the lan net coming from any IP other than lan net? There is no reason to have any as the source, unless the interface is a transit network, and even then it should be limited to the IPs as source, why would you not know your downstream networks using this interface as a transit..
Also what client would be using dot? (853) Clients use doh, dot is more for resolvers or forwarders to use.. Also for you to use dot from a client do you have that setup with cert that your clients would trust?
What do you have behind pfsense that is using dot? And for that matter why would you need to encrypt dns queries across your own network?