22.05-RELEASE (amd64) Unable to check for updates?
-
If unbound is running in resolving mode then, yes, you should see see answers from 127.0.0.1 when querying a host.
You can't enter an IP in DNS Lookup though.
If you still can't resolve anything then something is blocking outgoing DNS.
You mentioned you have a VPN provider. Did you add any rules to force DNS queries over a VPN?
Or specific rules to block DNS leaving over the WAN? -
@stephenw10 In the past (see above) I've enter firmware.netgate.com in DNS Lookup and got a response but get nothing now.
I have no rules anywhere that have anything to do with port 53 or 853.
I previously setup a Gateway that sent ONLY my SABnzbd traffic through the VPN and it worked just fine. That has quit working and my VPN provider says it's because 'Per Logs, DNS on pfsense is failing to resolve the hostname.'
-
Hmm, so no configured DNS servers are responding at all when you test there now?
Is Unbound actually running in Status > Services? -
Try dig from Client and pfsense if you capture on WAN with Port 53, do you see DNS querys in the pcap?
You found Package Capture in the Diag Menu.
-
@stephenw10 Status > Services, Unbond, DNS Resolver is checked.
-
Ok, check the state tables in Diag > States for traffic from the firewall only on port 53 when you try to resolve something in Diag > DNS Lookup.
Something must be blocking or at least re-routing that traffic.
-
You don't have a UniFi device with ad blocking enabled, do you? Because if you do, it redirects all 53/UDP traffic to it's own resolver regardless what you have configured on your client devices.
-
@stephenw10 It's weird DNS Lookup will find things and now I just ran it again with 'firmware.netgate.com' and I get 'could not be resolved'.
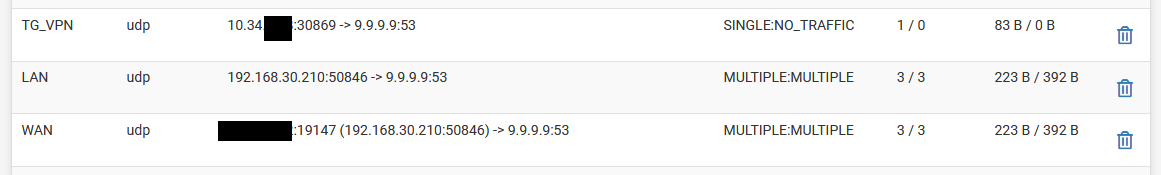
-
Ok, so there you've got a LAN client successfully connecting to 9.9.9.9 creating states on LAN and WAN.
And you have an unsuccessful connection via the TG_VPN interface.Is Unbound configured to use TG_VPN as it's outbound interface? And that interface is down?
The fact it's connecting to 9.9.9.9 there though means it's not Unbound resolving directly. Is it still set to forwarding mode?
All of that looks like you might have followed some instructions from a VPN provider at some point. Is that possible?
Steve
-
@stephenw10
Is Unbound configured to use TG_VPN as it's outbound interface? And that interface is down?
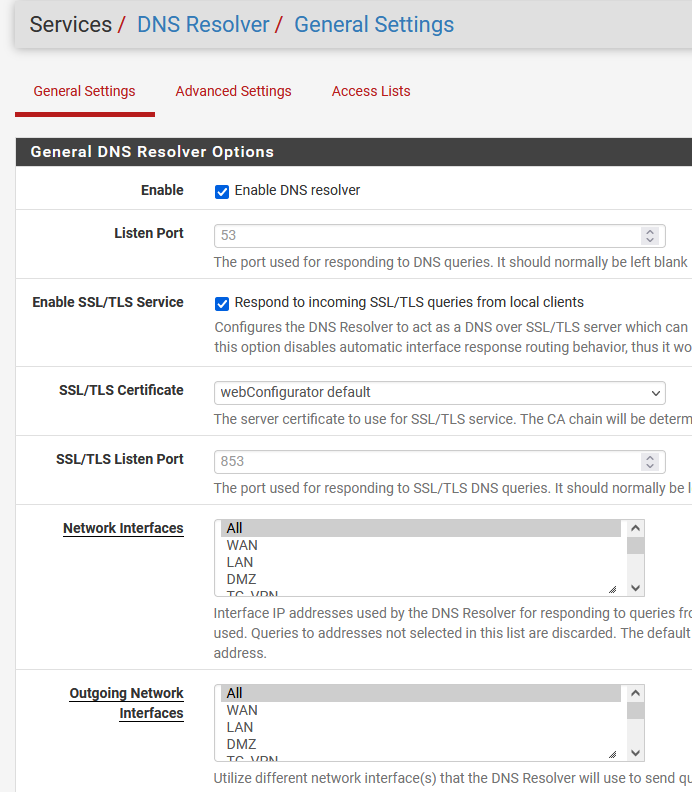
The fact it's connecting to 9.9.9.9 there though means it's not Unbound resolving directly. Is it still set to forwarding mode?
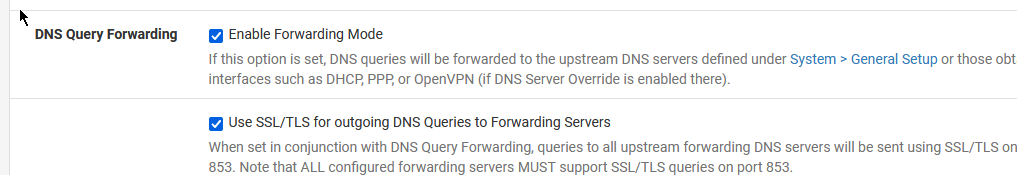
All of that looks like you might have followed some instructions from a VPN provider at some point. Is that possible?
Yes, but I've set a rule to force a single source (192.168.30.117) through the TorGuard VPN gateway
https://torguard.net/article/254/how-to-setup-the-latest-pfsense-openvpn-client.html -
H haraldinho referenced this topic on
-
-
If you disable forwarding mode and ssl/tls does it then resolve correctly?
-
@stephenw10 firmware.netgate.com could not be resolved.
I would be glad to take a phone call on this if you ever do that. DM me if you want.
-
Do you at least see states on WAN on port 53 when you try to resolve it?
-
@stephenw10
Like this?
WAN tcp 96.46.xx.xx:31132 (192.168.30.112:45300) -> 8.8.4.4:53 FIN_WAIT_2:FIN_WAIT_2 4 / 4 277 B / 409 B -
I dumped 23.05 from my backup pfSense computer and reloaded 2.6.0 CE and an old config and everything is working perfectly. This backup computer is identical hardware to my primary pfSense unit.
- System reports it's on the latest version (2.6.0-RELEASE)
- DNS Lookup doesn't time out
- Package Manager reports installed packages
- VPN is working and is routing traffic according my my filters
- Jumping between menus / tabs is way faster
If anyone has suggestions fixing the 23.05 issues listed above I'd be glad to jump back to my primary pfSense 23.05 box and try them out.
-
@TAC57 said in 22.05-RELEASE (amd64) Unable to check for updates?:
Like this?
WAN tcp 96.46.xx.xx:31132 (192.168.30.112:45300) -> 8.8.4.4:53 FIN_WAIT_2:FIN_WAIT_2 4 / 4 277 B / 409 BNot like that. That's a connection from a LAN side client that's being NAT'd. Unbound would be using the WAN directly with no NAT.
The only issue with Unbound I'm aware of only applied to DoT only so disabling that would have removed it.
https://redmine.pfsense.org/issues/14056You can try the workaround there: https://redmine.pfsense.org/issues/14056#note-6 However I wouldn't expect it to do anything to a default resolver config.
Steve