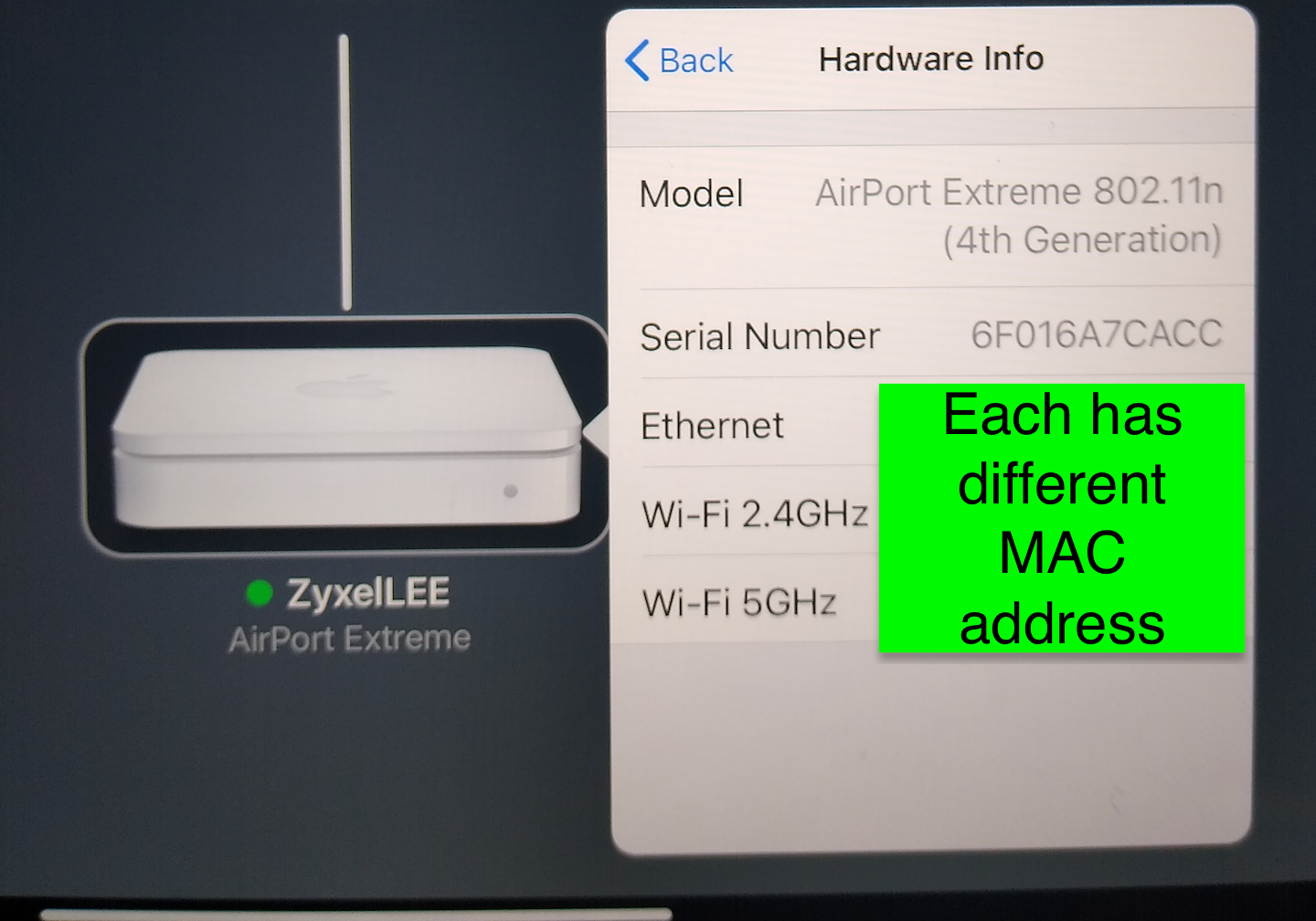
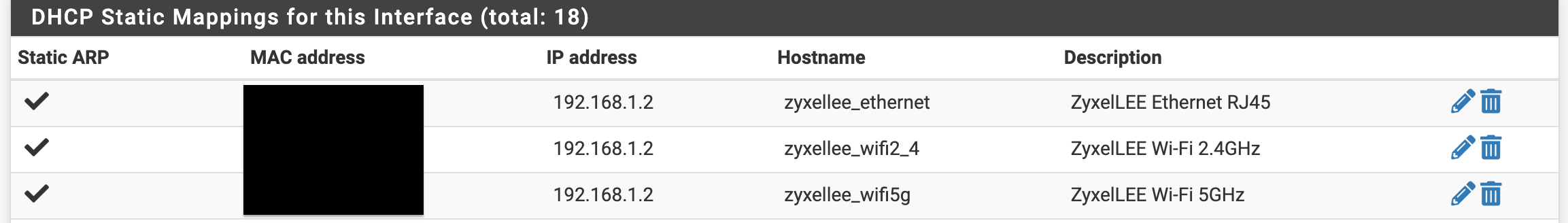
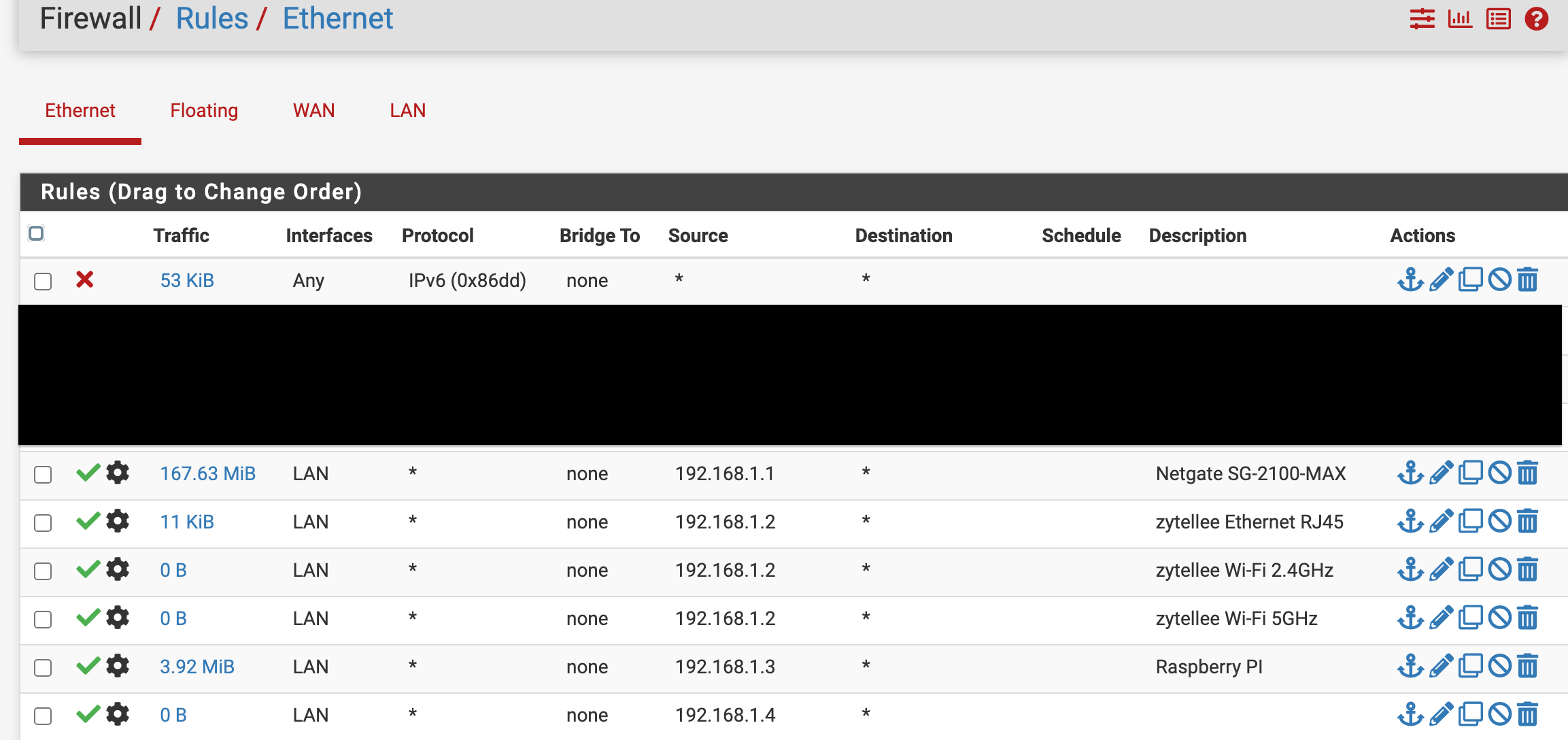
AP with onboard built in NAS abilities/multiple MAC Hardware Layer 2 addresses
-
@JKnott BSSID is what I am saying. That is the MAC mapping of that WiFi network.
"SSID, BSSID, and ESSID are all descriptions of wireless networks. However, these three terms have slightly different meanings which are described here. An access point is only one of many devices that make up a wireless network and the Basic Service Set Identifier (BSSID) refers to any device in the WLAN.
Basic Service Set Identifiers (BSSID) are 48-bit labels that identify which devices conform to MAC-48 conventions. These identifiers are usually linked with a wireless access points MAC address, like when the identifier is sent in an AP beacon but can not be seen without some type of signal analyzer or radio tool."
That's the MAC tied to my NAS usb drive within the airport extreme itself.
Ref: https://internetspeedtest.world/wiki/bssid
There for the reason for the mixed host name with multiple Mac IP mappings, and why I have configured pfSense this way it's for my airport extreme with NAS running in bridge mode. It just works better for me. Under normal non NAS APs, just one MAC would be needed here. However I need two layer 2 addresses because of the NAS for ARP requests to work for it.
Bridges work on the data link layer. This will send everything to the firewall even the ARP request to find the NAS.
-
@JonathanLee said in AP unit has multiple MAC Hardware Layer 2 addresses:
BSSID is what I am saying. That is the MAC mapping of that WiFi network.
Forget about the WiFi side. PfSense can't see it. All it can see is the Ethernet connection, which includes the MAC and IP addresses for that connection only. Beyond that, it can see the devices connected via WiFi. The WiFi frame carries the Ethernet frame as payload and adds it's own headers to it.
You can get books about WiFi, if you want to learn more about it. There are some 802.11 books by Matthew Gast, published by O'Reilly that have far more info than you'll ever want to know.
-
In access point mode it does usually just bridge the interfaces. Potentially I could imagine an AP using it's wifi interface as the DHCP client and hence that MAC. I'm pretty sure OpenWRT would do that if you configured it to do it. But I have have never tried nor have I ever seen that happen.
-
"According to the tech (apple support) the AirPort Extreme is "unpredictable" if you attempt to use USB drives when the router(AP) is in bridge mode.." The AP has a MAC mapped for it's NAS USB drive right? You state that PfSense can not see it again if it's in bridge mode under this configuration it still sees the same broadcast domains and arp requests to find that NAS correct?
Yes let's agree under normal APs without a NAS built in it wouldn't care and it would only need the one MAC for Ethernet and it passes the traffic normally.
But for a network attached storage plugged in by way of USB into the AP why would it act unpredictable per the AP developer when set to bridge mode? It still works.
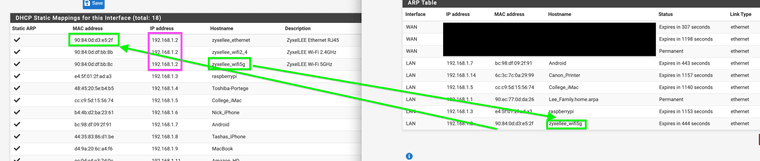
It creates a kind of weird condition here that I think would require both MACs to mapped. Again it does spot the other host name here meaning it saw and mapped it for a while before it changed the MAC when it updated the table and left the old hostname.
-
The NAS function should still use the Ethernet MAC IMO. If it randomly uses any MAC from the bridge that sounds like a bug.
The only reason I could imagine it using a wireless interface directly would be if it's running as a wireless NAS. But that's quite an extreme edge case.Probably the best thing here is don't use a WIFI AP as a NAS.

-
It's still using the Ethernet MAC in that screenshot. But because you have 3 hostnames configured for the same IP address it's probably just showing the last matched.
-
@stephenw10 yeahhh that was the goal so it could find the MAC-IP map when needed and the Ethernet MAC-IP map. Yeahhh
 so it's updating when needed again it leaves the hostname when it updated to the other MAC in the Arp table but the point is the wireless AP's NAS is mapped.
so it's updating when needed again it leaves the hostname when it updated to the other MAC in the Arp table but the point is the wireless AP's NAS is mapped. -
@stephenw10 it's essentially a wireless NAS it's part of the AP. It's the airport extreme AP/ apple time machine software.
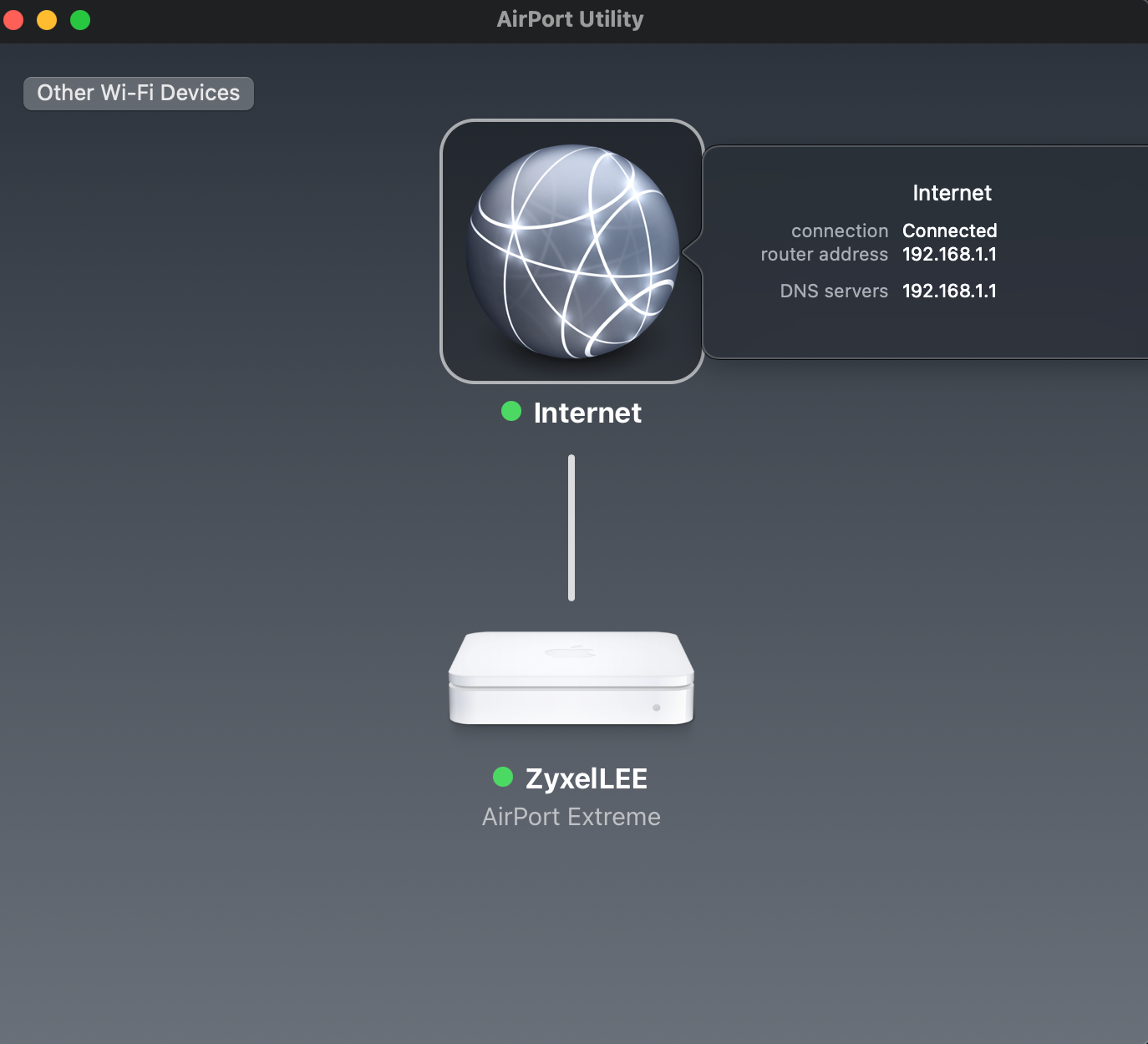
(AP bridge mode to pfSense Firewall)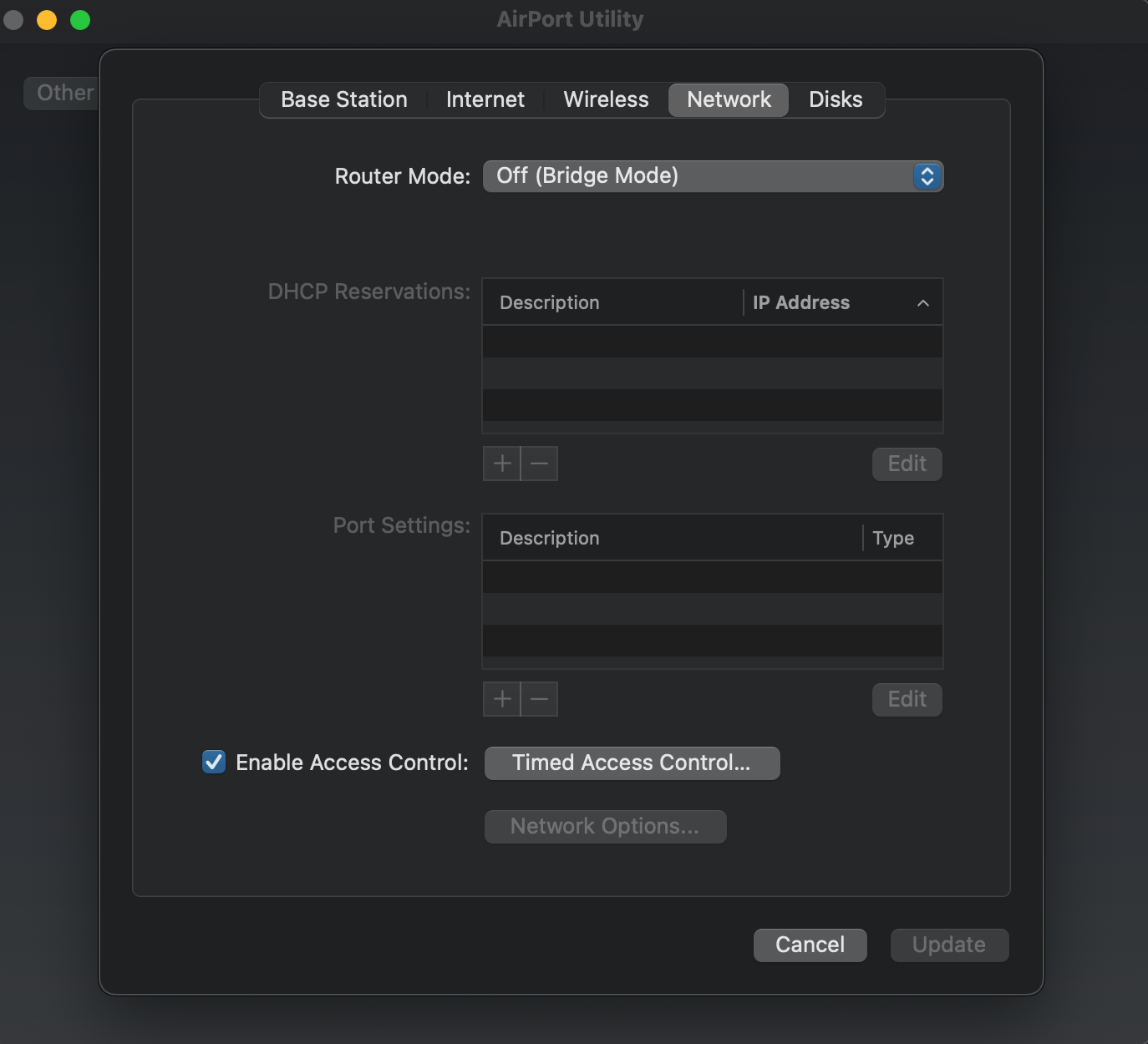
(Set to Bridge Mode)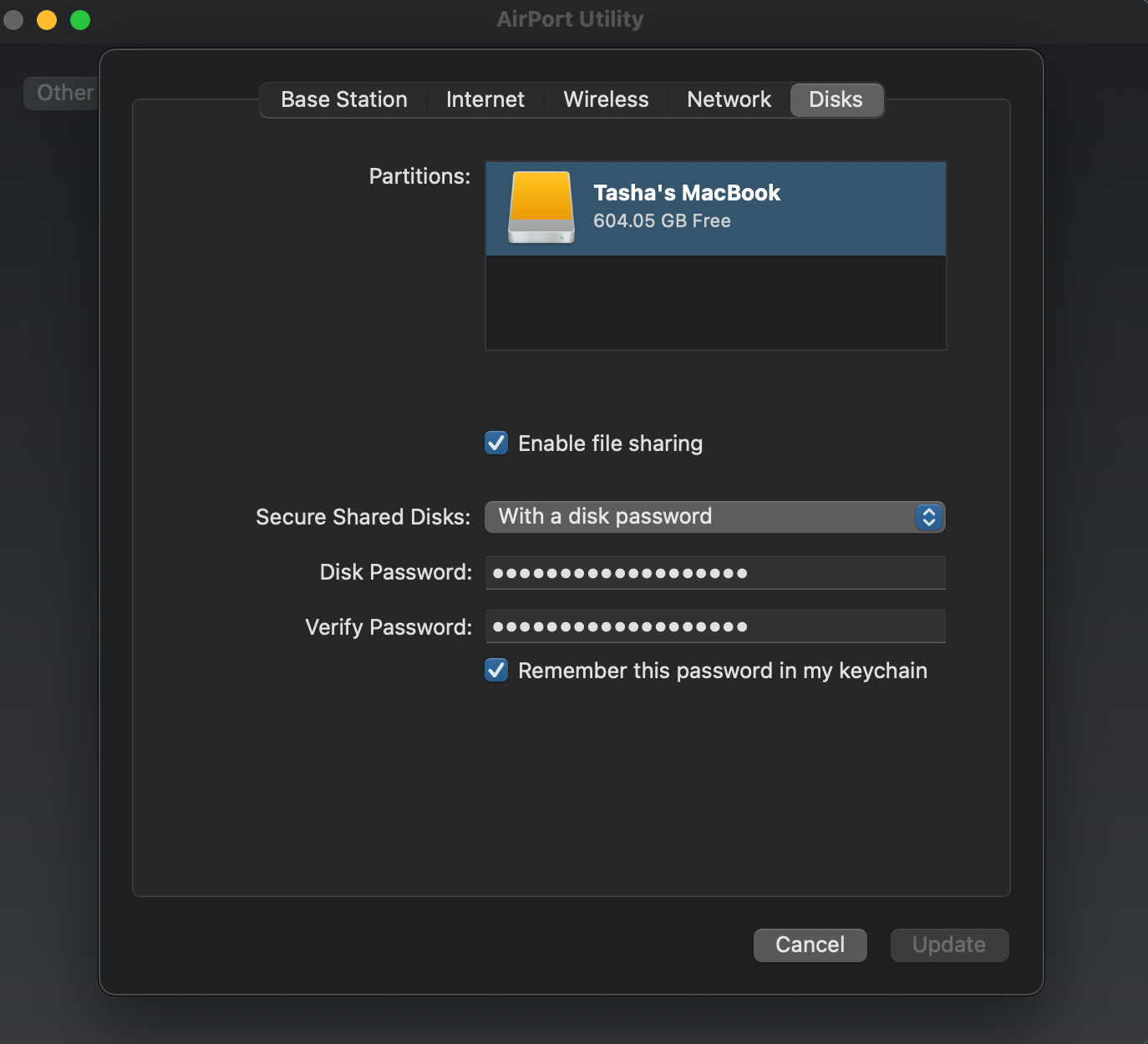
(NAS within the AP itself)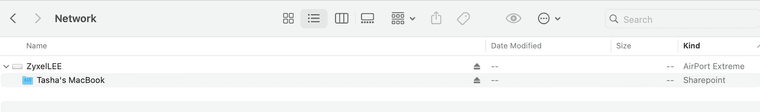
(Accessible NAS within bridge mode set AP) -
@stephenw10 I made a Redmine ticket for the hostname mix ups because it should update the hostname or block inputting different ones because logs could be wrong if it doesn't use the right hostnames.
-
@JonathanLee said in AP with onboard built in NAS abilities/multiple MAC Hardware Layer 2 addresses:
I made a Redmine ticket for the hostname mix ups
And what is this redmine number? Seems like lack of understanding of basic concepts if you ask me vs some issue with pfsense.
-
If there's a bug here it's probably that you shouldn't be able to add the same IP address to multiple dhcp static mappings.
But you can't ever prevent all config errors.
-
@stephenw10 we can try to prevent all the errors

-
@johnpoz https://redmine.pfsense.org/issues/14516
Opened
-
"With Multiple static ARP MAC-IP pairing to the same IP address"
So you don't see the problem with this? Thought you wanted to reduce traffic?
So if I create multiple entries for say 192.168.1.100 for like 3 different mac addresses.. And then I want to send traffic to 192.168.1.100 - so I will put 3 packets on the wire? Sending to all 3 mac addresses?
Like I said lack of understanding of basic concepts is the issue here.
-
@johnpoz Why does the GUI allow it? Leading to, it does allow it. Therefore, why does it map to the wrong host names? If only one shows as an active DHCP lease at a time wouldn't it only send packets to that device? It also would not recognize active leases with multiple entries it shows them offline. Hypothetical situation, an admin has a list of thousands of static DHCP entries, wouldn't he want some type or control for multiple entries and or a way to log the correct hostname that in use at that particular time if he needed multiple entries? It didn't list the right hostname in my example. The PfSense system software now has experimenatal layer 2 Ethernet filtering rules as of 23.05, shouldn't we start to research this? Spoofed MAC addresses so on?
-
There's only so much input validation and error checking we can do. But it seems like this might be possible.
Ultimately the user can configure pfSense in any number of broken ways we can't prevent.
Steve
-
@stephenw10 yes we can agree the user can configure it wrong all over. Again, an administrator might fat finger a large static DHCP list with a couple entries thus causing hostname mix ups. That for one would be very hard to pinpoint. Moreover, we know the amount of hours system administrators work. It's a lot of hours. This would make PfSense have a ease of use software functionality built in. I assumed that if pfSense allowed multiple duplicate entries, it was done for a situation when two devices need to be swapped in and out and need the same IP address, in this mindset PfSense should still log the correct hostnames. Again, if that was the reason for PfSense allowing the GUI duplicate entries.
Weird thing to research, but the hostnames mixup was what I was after and or why
PfSense would allow the duplicate entries in the first place. Let's agree admins have monster static dhcp lists that are updated and changed all the time within a secure setting. This situation would want controls in place for hostnames. Finally, logs for the hostnames could get bonkered up and with a monster list and that would be hard to track down why hostnames are wrong. We know PfSense now has experimental layer 2 Ethernet filtering.