Static IP Setup on WAN with DHCP on LAN/LAN2/LAN3/LAN4 on Netgate 6100
-
@tonydutt yes the 6100 would be the dhcp server and hand out IPs to clients - but you would have to set an IP on the pfsense interface.. This would be static say say 192.168.2.1/24 you would then enable its dhcp server and it would hand out IPs say 192.168.2.2-254 and point clients to 192.168.2.1 as their gateway and for dns..
But you have to set the IP on the interface, and enable it to be dhcp server.
You would also then need to set rules on this interface to allow internet..
I would suggest getting devices working first, with an any any rule like defaults on lan. We can then go into locking down what you want.. For example this would be a set of rules that are locked down and only allow internet access.
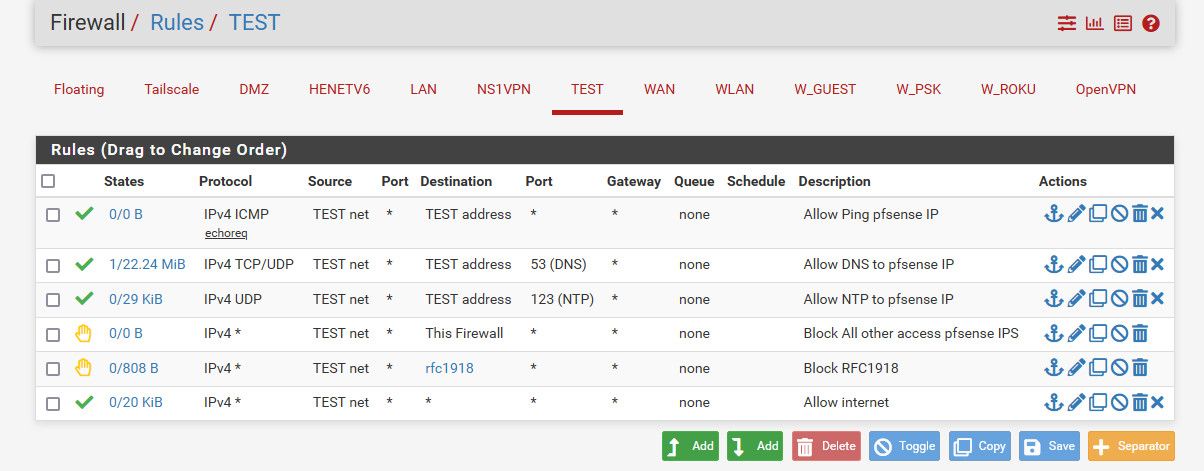
Once you have your different networks actually working, we can go through how to setup the rules to how you want to set them up. The above set of rules would not allow this network to talk to any of your other networks.. Only ping pfsense IP (for troubleshooting that you have connectivity) and use pfsense as dns and ntp.. And not be able to access pfsense web gui. But anything else on the internet would be allowed.
-
Awesome!! I will work on getting these working and report back when I do.
:):)
-
I might need some more rudimentary guidance on the port setup. Specifically, I have set up LAN2 and LAN3 identical to LAN with the exception of the IP addresses.
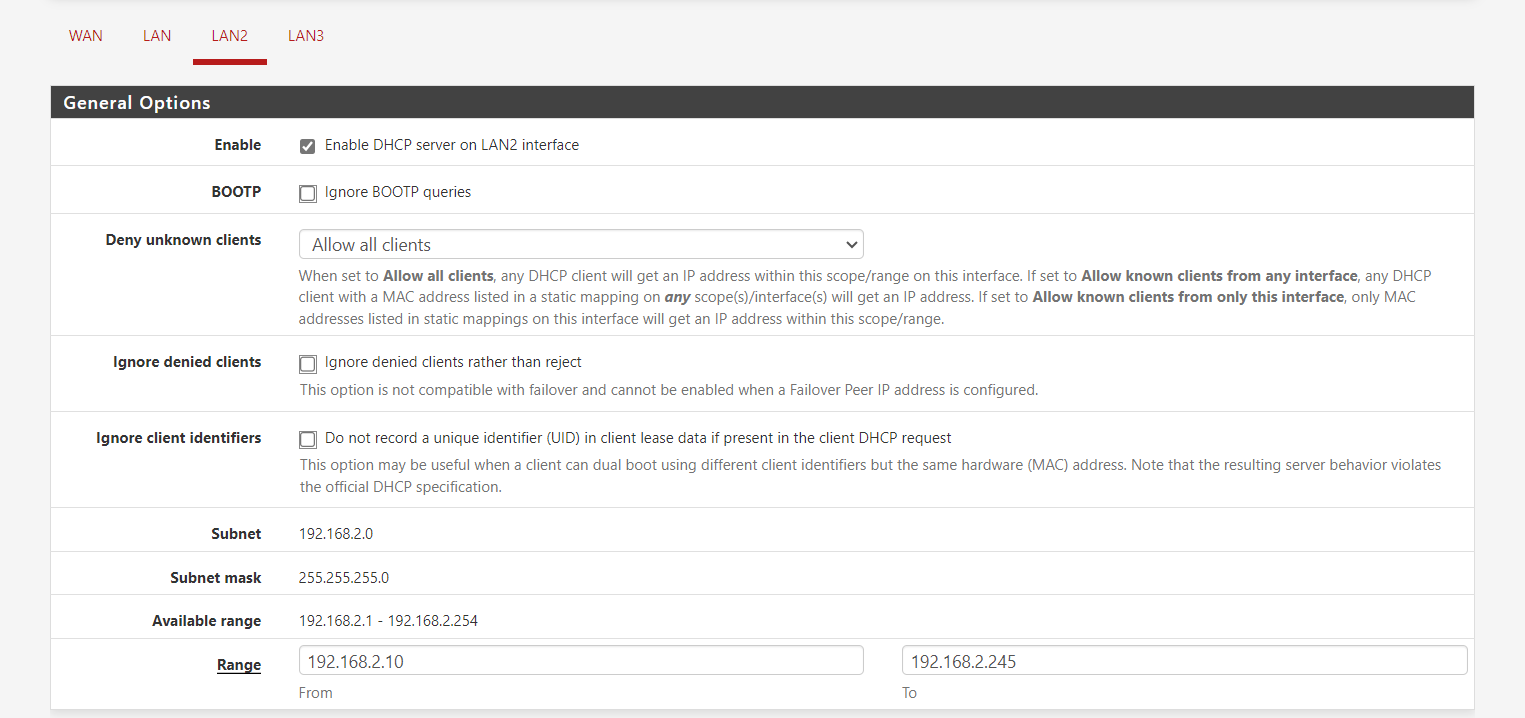
LAN2: static 192.168.2.1/24 with DHCP server range of 192.168.2.10 - 192.168.2.200
LAN3: static 176.100.10.1/24 with DHCP server range of 176.100.10.10-176.100.10.200
WAN is set to static IP with AT&T data. I need this to be static for VPN access.
DHCP server is enabled on each with the same DNS servers - Blank in the DHCP server setup for each interface (but the general setup is 8.8.8.8. and 8.8.4.4).
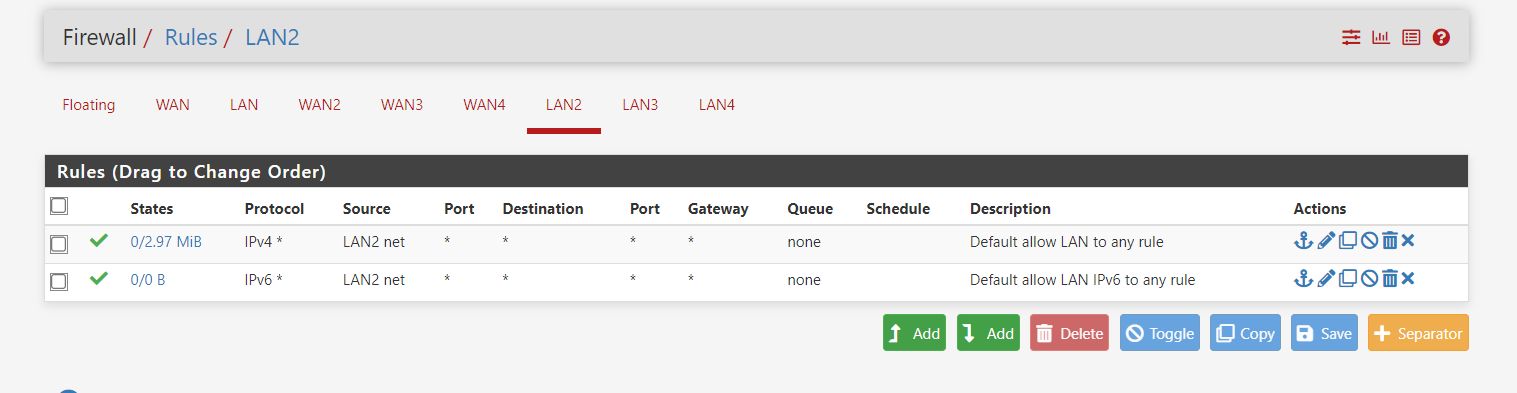
I copied the firewall rules from LAN1 to LAN2 and LAN3 and made sure the rules applied to LAN2/LAN3. Note - I did not create these rules - they are IPv4 and IPv6 DHCP allow rules. The only difference is LAN has anti-lockout rule and LAN2/LAN3 does not.
I disabled IPv6 for now.When connected to LAN - I have full internet access
When connected to LAN2 or LAN3 no internet access, although the connected machine will pull an IP address in the range I set up. The error seems to be associated with DNS resolution according to MS Network troubleshooter. I tried disable/enable the network adapter - no help. Because LAN connects to internet and LAN2/LAN3 does not, it seems like there is another setting that I am missing. Not sure what that might be.
Is there another rule i need to set up or other setting?
I am sure these are amateur level questions. I tried to watch some YouTube videos and the pfsense Wiki and nothing seems obvious.
-
@tonydutt said in Static IP Setup on WAN with DHCP on LAN/LAN2/LAN3/LAN4 on Netgate 6100:
LAN3: static 176.100.10.1/24 with DHCP server range of 176.100.10.10-176.100.10.200
Is there a specific reason you chose this range? This is a public IP range that, while you can use it, means you cannot access any of the services on that network.
@tonydutt said in Static IP Setup on WAN with DHCP on LAN/LAN2/LAN3/LAN4 on Netgate 6100:
When connected to LAN2 or LAN3 no internet access, although the connected machine will pull an IP address in the range I set up
Did you specify rules on the LAN2 and LAN3 Firewall Rules pages that allow traffic? If so please provide screenshots of the rules you created.
-
@tonydutt said in Static IP Setup on WAN with DHCP on LAN/LAN2/LAN3/LAN4 on Netgate 6100:
LAN3: static 176.100.10.1/24
Yeah as @rcoleman-netgate points out - that is not a IP range you should be using.. Use a network in rfc1918 address space.
https://en.wikipedia.org/wiki/Private_network
Is there another rule i need to set up or other setting?
As already stated - yes you would have to create rule(s) to allow what you want.. As I mentioned just duplicate the default rule like on your lan, an any any rule - see the bottom of the example locked down rules that allows everything.. Do the same sort of rule on your new interfaces.
That network is owned by
inetnum: 176.100.0.0 - 176.100.31.255 netname: PAUTINA-UA country: UA -
That is good to know on 176.100. I will change that. LAN3 was just to see if LAN2 had issues. I think if I get LAN2 running LAN3/4 will be easy to setup.
here are the LAN firewall rules:
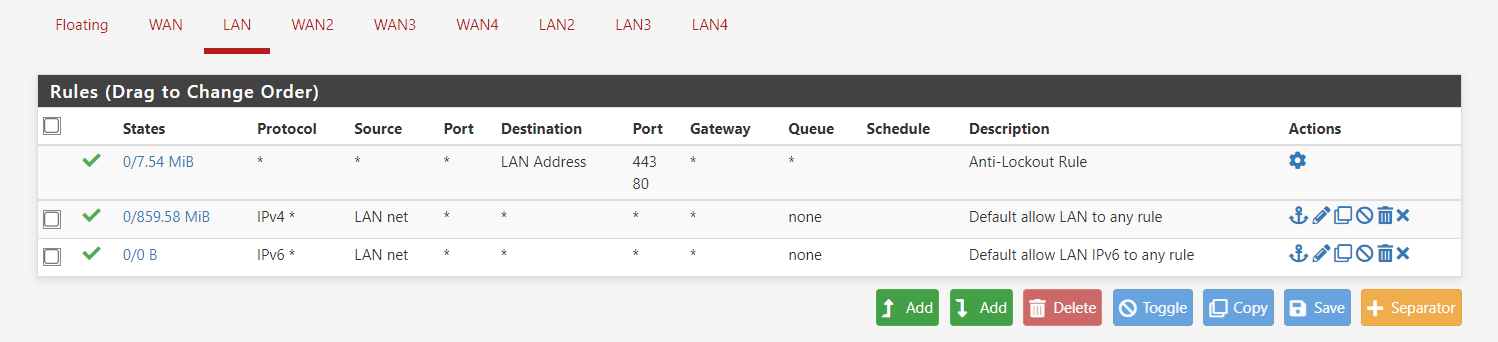
Here are the LAN2 firewall rules (duplicated from LAN)
Here is the LAN2 DHCP Server setup:
-
UPDATED LAN2 Firewall Rules:
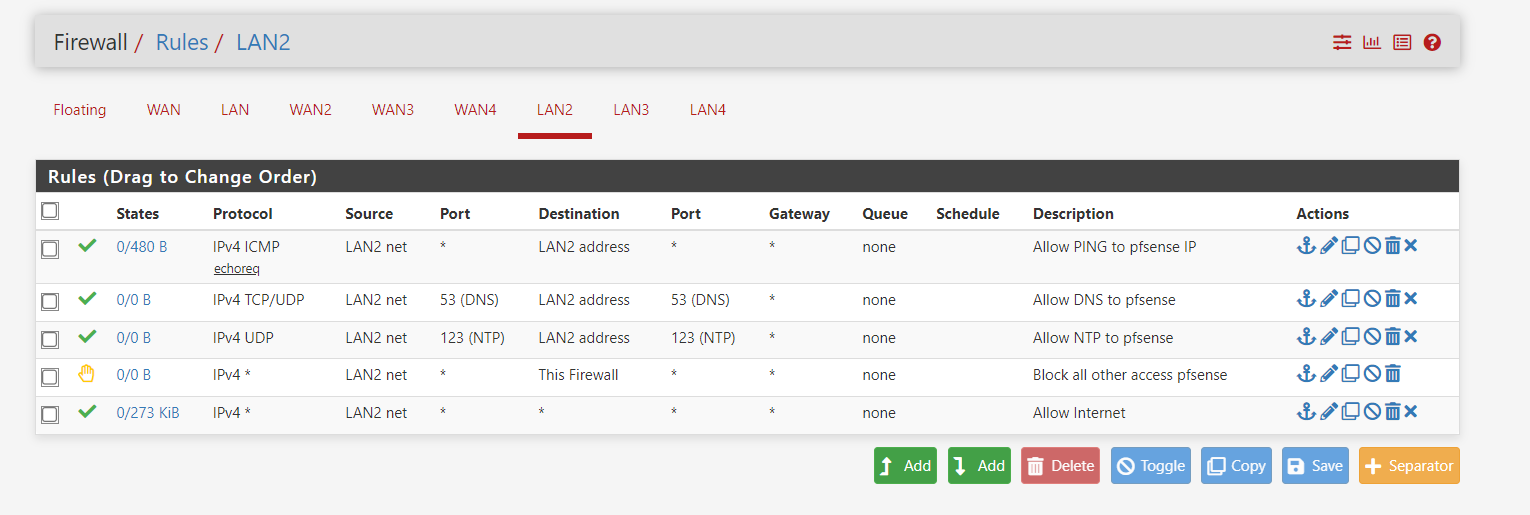
The DNS issue persists with these rules set as they are.
Thanks for all the help. I am really appreciative.
-
@tonydutt Ok so now... Status > System Logs and click on the Firewall tab.
Is any of your traffic showing up as blocked there?
-
@rcoleman-netgate
Yes, there is a long list of denied access. Looks like the majority are from LAN2 and LAN3.Of note - there are no rules on the WAN other than block BOGON. So all inbound connections will be blocked is what the message says. Are there some WAN setups I need for outbound connections? The challenge I am having is LAN access internet but LAN2 does not with the same WAN.
-
@tonydutt said in Static IP Setup on WAN with DHCP on LAN/LAN2/LAN3/LAN4 on Netgate 6100:
Yes, there is a long list of denied access. Looks like the majority are from LAN2 and LAN3.
OK... and why is that? What are they? Copy a screen cap into the channel showing them and we can help you troubleshoot it some.
-
@tonydutt
I think I solved it. Enable DNS Forwarding Mode under: Services/DNSResolver/General Settings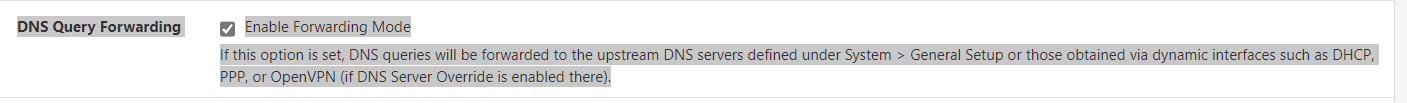
Curious - if there is any issue with this setting?
Thanks.
-
@tonydutt you shouldn't need to enable forwarding mode, how was lan working without forwarding mode? Was your lan clients pointing to something else for dns other than pfsense?
-
@johnpoz
I will check and see if that will work. I have a Windows Server installation doing updates right now, so cant try it just yet. But, thanks for getting back to me. Outside of that one setting, I have gotten most of the system up and running. Now it is down to getting all of the functionality I want. I am really happy with the Netgate purchase so far.I would like to take you up on your other off to help me get the right settings in NETGATE. I might start a new thread in a different area if that is best.
Basic architecture:
Negate 6100 connected to Cisco 8 port managed business switch with 1 trunk line (right now) with teh following downstream:- Dell R640 - Windows Server 2019 Active Directory VM and File Server VM. Both installations are virtualized on HyperV Server and managed from my computer. 4 NICs.
- Dell R630 - Ubuntu Server with immutable backup from File Server via VEEAM. 4 NICs.
- Synology NAS - Secondary Backup from file server.
- Wifi - Ubiquiti Amplifi
- Local Computer - on LAN downstream of Netgate not WiFi.
- Local Printer
- Remote employees VPN into AD to access file server. Only files - no VMs.
- i have multiple unmanaged switches available.
My goals:
- Dell R630 Ubuntu never sees the internet. Only internal communications from R640 fileserver VEEAM for daily backups.
- Dell R640 access the internet for VPN, Windows Updates, Antivirus updates.
- Keep both iDRACs for Dell servers isolated from internet and only accessible internally for management purposes - which should be minimal.
- Synology NAS has access to internet - only for Synology services.
- Minimize VLAN/PVLANs.
- Use L2TP/IPSec for VPN service for ease of remote worker deployments.
If you have any thoughts on setting these up properly, I would be grateful. I have sketched it out, but, have not figured out all of the inner workings.
Thanks very much!!