Pfsense Gre Tunnel with Mikrotik Router (Incomming Traffic Block by default deny rule pfsense)
-
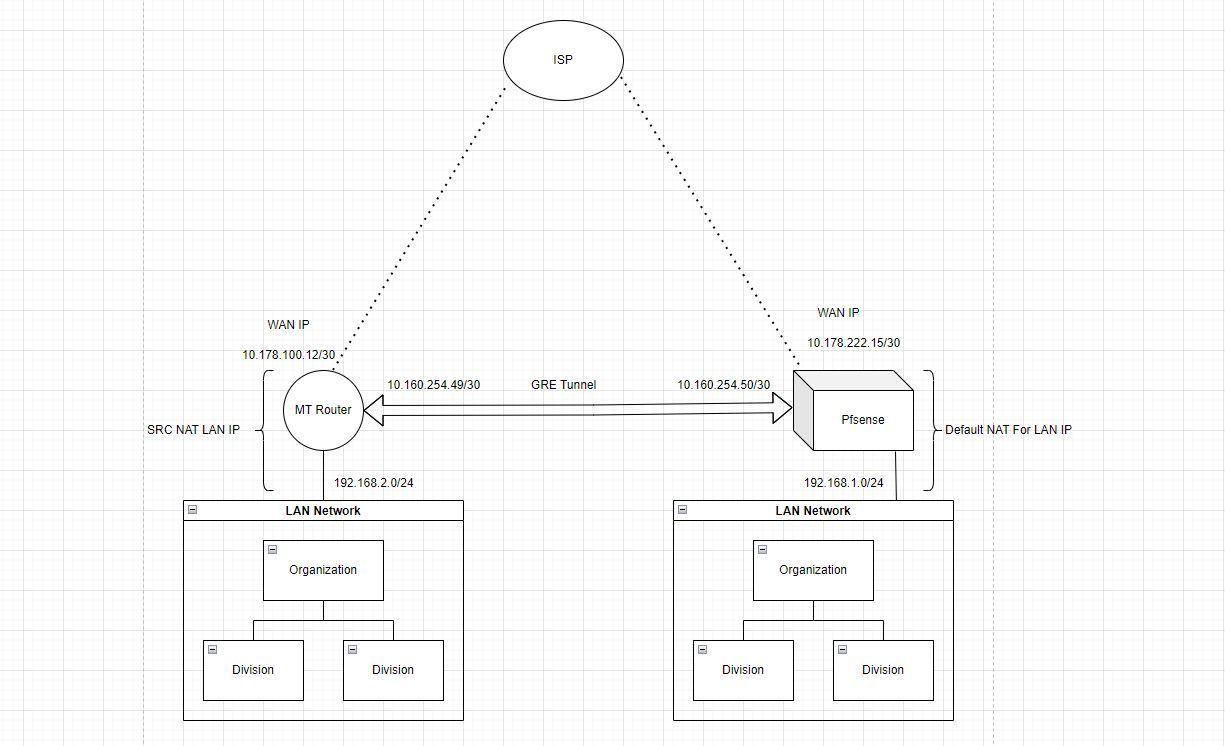
I have a pfsense and a router both have public wan ip and has NAT configure to each for LAN Network. i want to send traffic 192.168.2.0/24 from MKT router to Pfsense .
Here i have connected both the router and Pfsense through GRE tunnel and works fine .
The problem is Traffic incomming from GRE interface is blocked and i know this error due to Asymetric traffic. please help me to solve this problem i tried everything suggested from this forum.
here are some of the screen shot of pfsense
here is my static routes
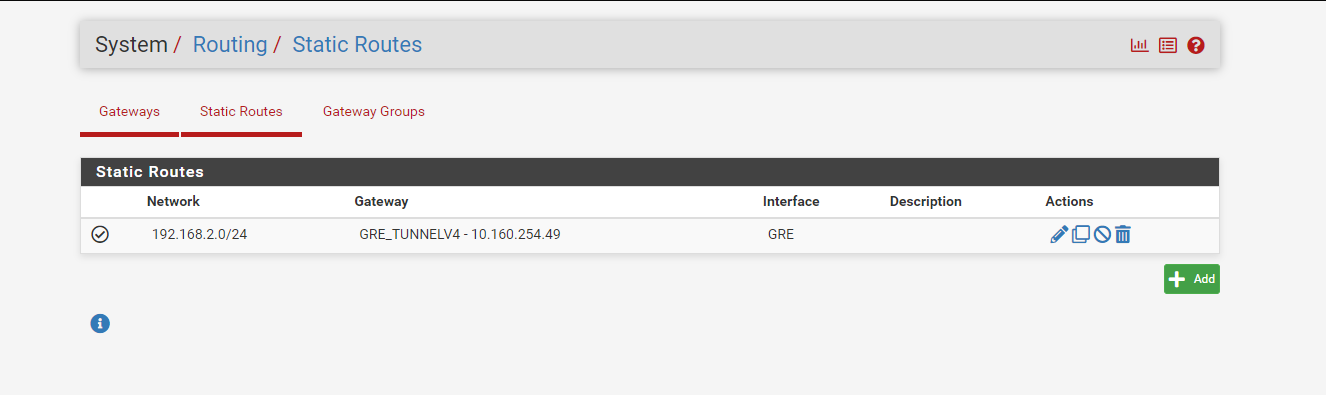
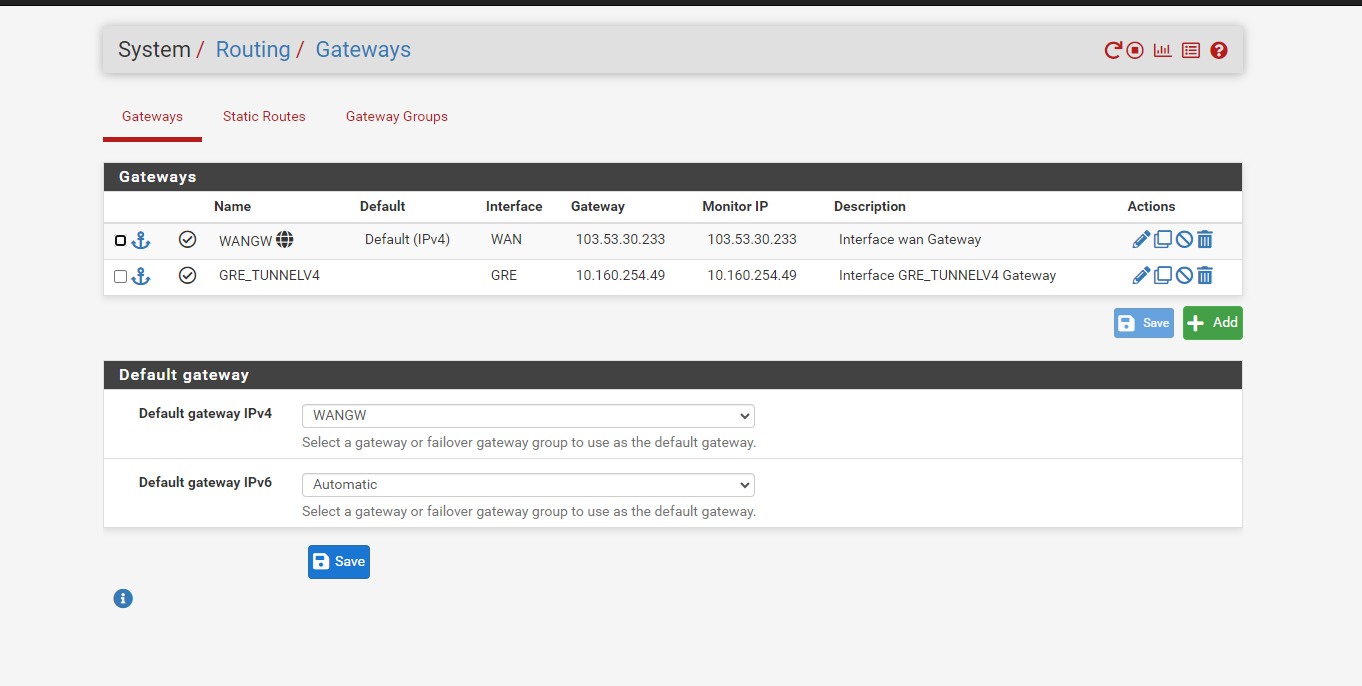
and my gateways
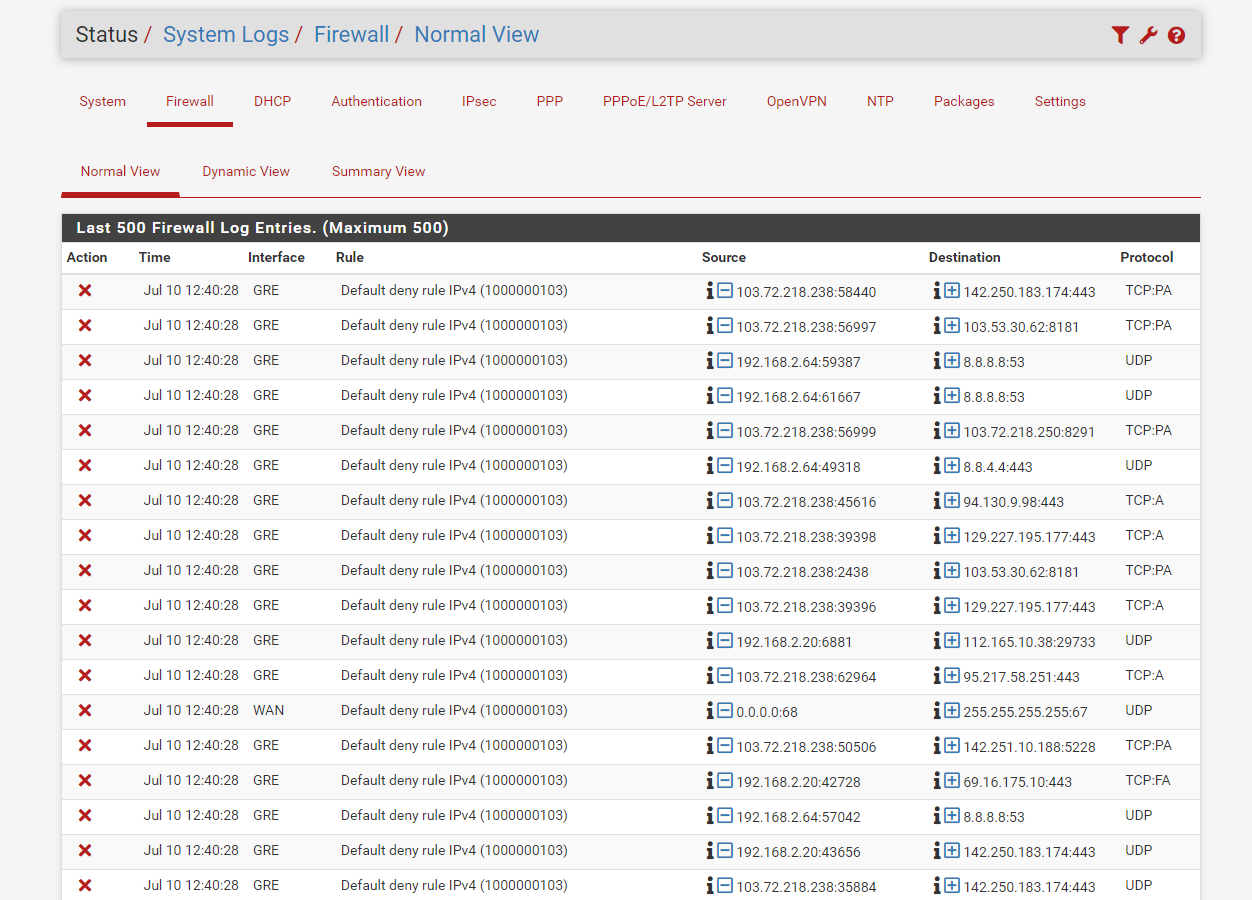
Firewall logs
-
From both side i can ping but Internet is not able to access from when traffic is passed through gre
-
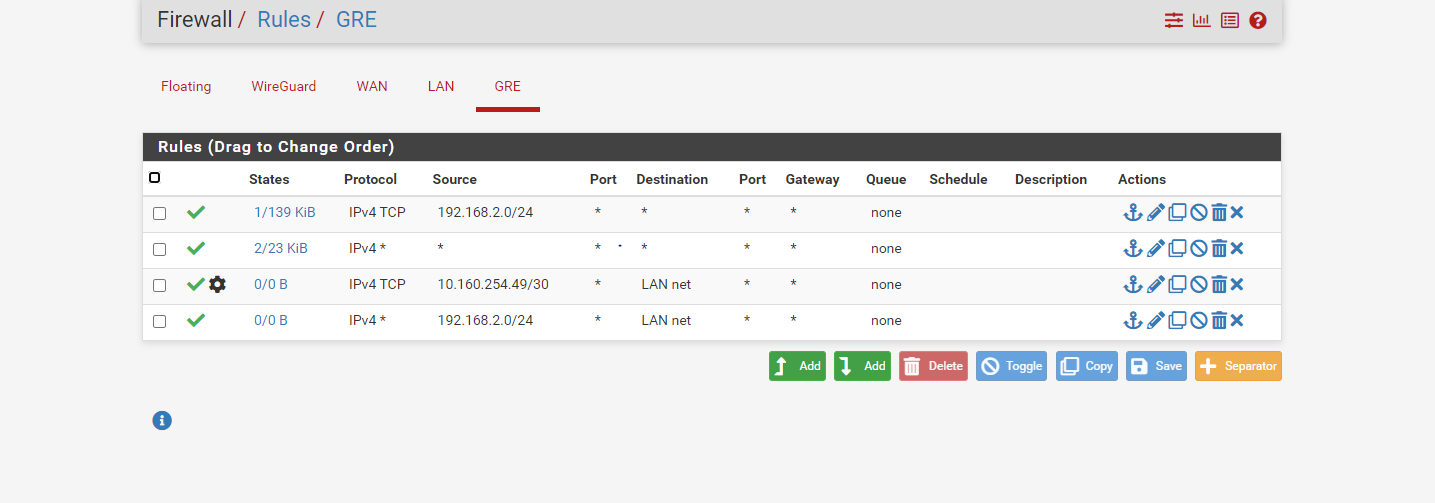
@Rohit-0 You are missing a “Allow Internet” Rule on your GRE Interface in RULES.
Currently you are only allowing th 10.160.254.48/30 network access to Internet (And only with TCP). There is no clients located in that network. The Other rule you have gives the clientnetwork at the other end of the GRE access to your LAN, but not Internet. -
@keyser Thanks for the reply but as suggested i have applied another rule in GRE interface and still traffic is blocked .. any suggestion from your side
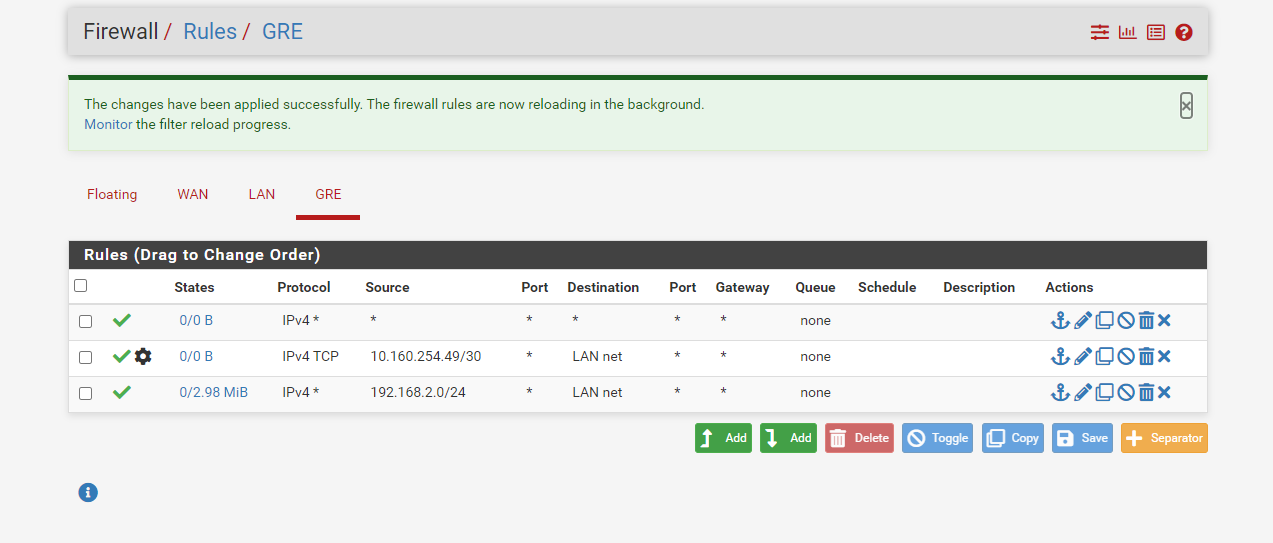
-
@Rohit-0 Your NAT rules also seems a little funcky - at least considering your other routing setup.
Do you intend to NAT all traffic to and from the GRE clients (192.168.2.0/24) when talking to LAN on your pfSense? I’m guessing you wanted them to be routed. -
@keyser Actually i'm planning jst to pass the traffic through pfsense , where i can monitor traffic of GRE traffic and also make 192.168.2.0/24 to access internet through pfsense.
can you suggest me how to achieve this -
@Rohit-0 Having looked further at your drawings and settings, I’m probably misunderstanding your intensions here. What do you intend to achieve here?
- Access between the client networks on the two locations in a routed fashion?
- Tunnel everything - including Internet traffic through GRE and access internet through pfSense?
Why not just break out internet locally on the remote location and avoid transporting everything through the GRE tunnel?
ALSO: A GRE tunnel is not encrypted, to transporting that accross the Internet is a very bad idea. You probably want to look into creating an IPSec/Wireguard Tunnel between the locations instead.
-
@keyser i'm trying to tunnel everything , i know GRE is not safe to use but for now this is the only method i'm trying to achieve
-
@Rohit-0 Hmm, well that going to get complicated then, because this is very bad network design in terms of Routing/NAT.
But your conundrum is that you need a tricky setup on your Microtik, because that needs to have a dual routing setup where it (itself) - using the first routing policy - has internet access through WAN - no NAT needed if it has a public IP.
Then it needs another routing policy that forwards ANY traffic from LAN (including internet destined) using the GRE tunnel without applying NAT. It should also treat any traffic that arrives on the GRE tunnel as part of the second policy (and not apply NAT to it)On your pfSense, you need to remove the auto created rules that applies NAT to any traffic leaving the GRE interface, and the manually created NAT rule for the GRE network is not needed (has no use if the Mikrotik is doing it’s routing as it should (without applying NAT).
The default pfSense NAT rules should cover internet destined traffic coming in through GRE, as it will also be considered an internal network because of your routing to 192.168.2.0/24But like I said, this will be a complicated setup
-
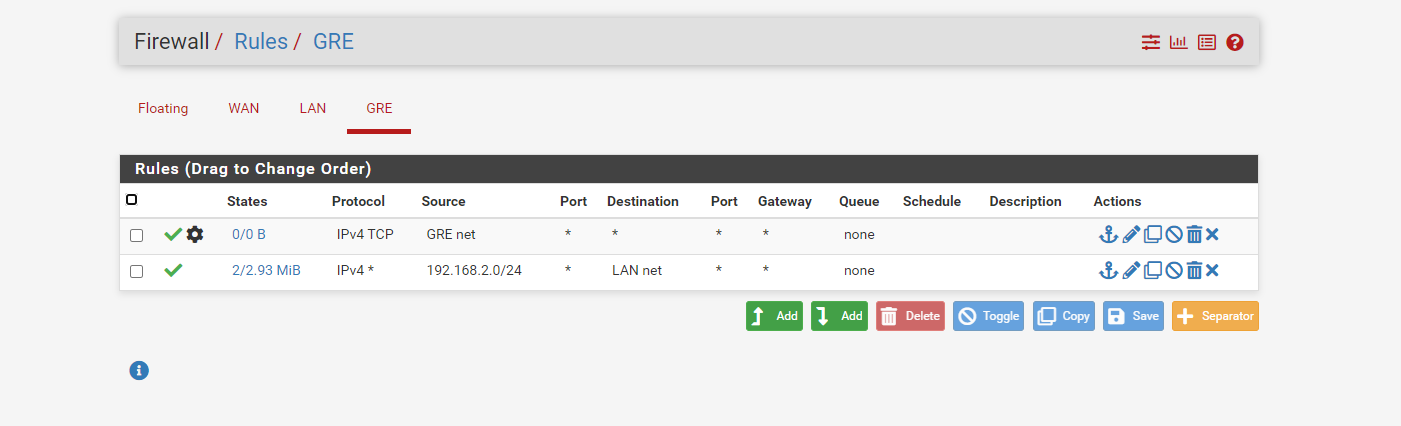
@keyser On my mikrotik router i have bypassed all the NAT and traffic 192.168.2.0/24 is going fine through GRE but pfsense is still blocking the traffic.
here is my packet tracer report from pfsense--->
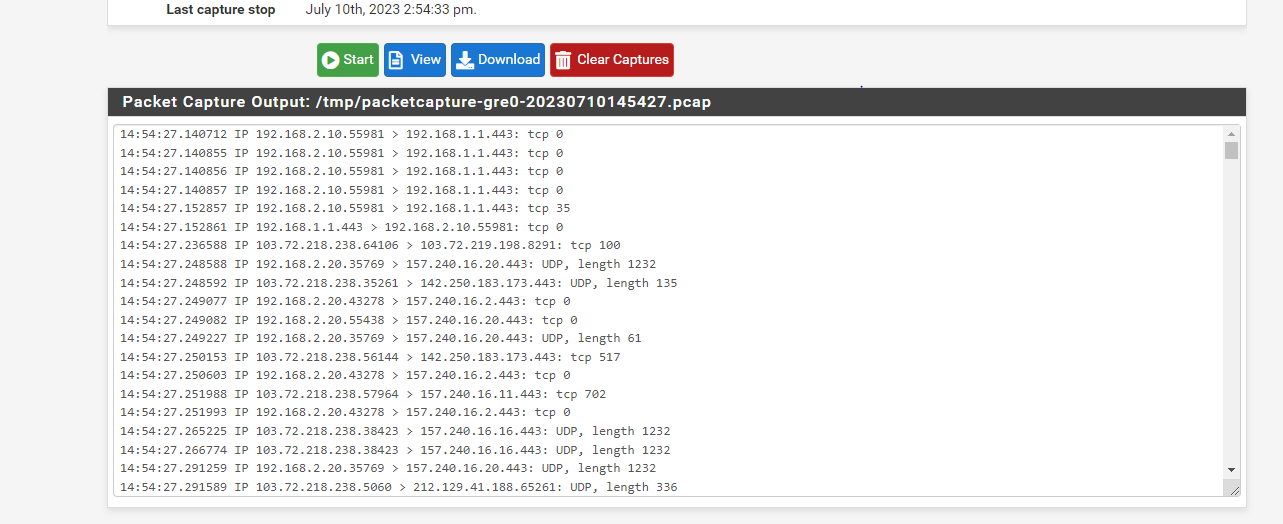
and here is my firewall log--->
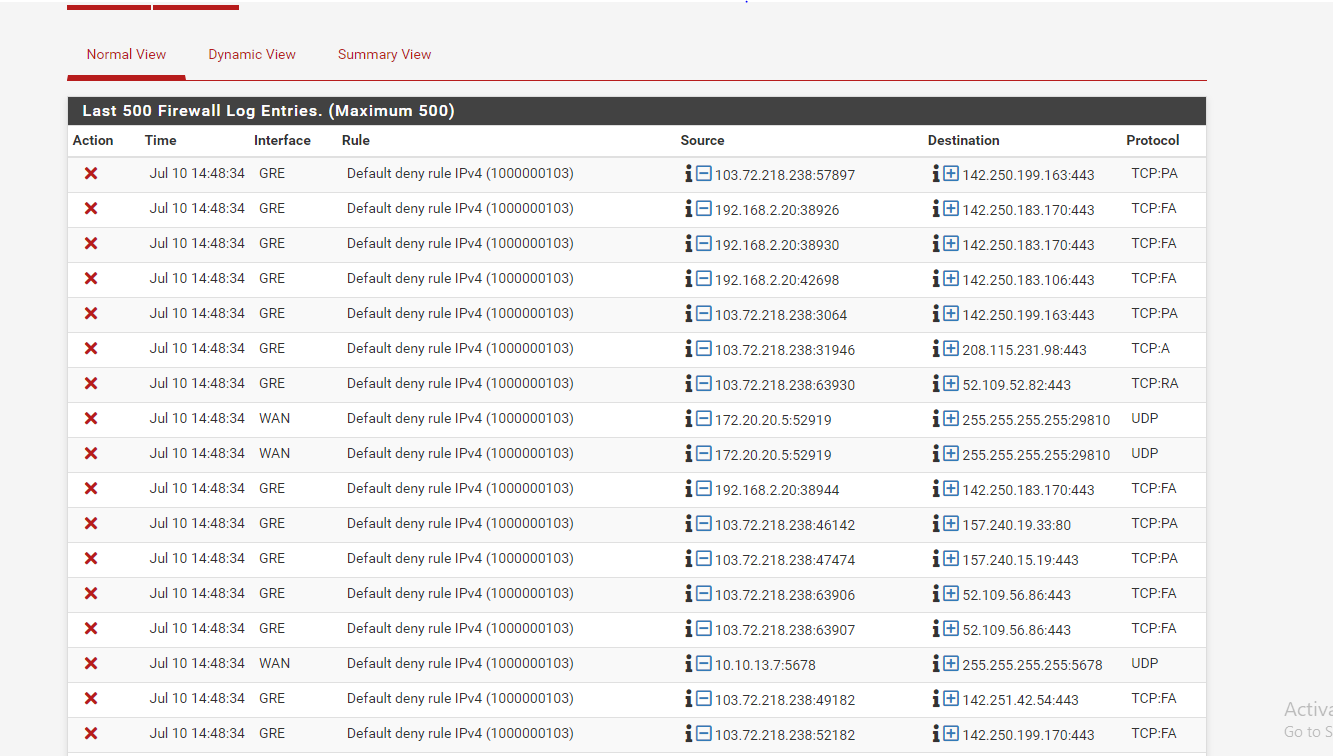
Note: I have remove all the OUT Bound NAT rules and allow all the traffic from GRE interface other setting intact. -
@Rohit-0 On mikrotik side i hve done all the routing and it work like a charm when tunnel with Netskope FW so i think i need some changes in pfsense.
-
@Rohit-0 Hmm, hard to tell what causes your issue then because I agree that your firewall log should not be hit with blocks like that since you created the right allow rule on the GRE interface - unless you created the GRE interface with the wrong settings.
Please post your current:
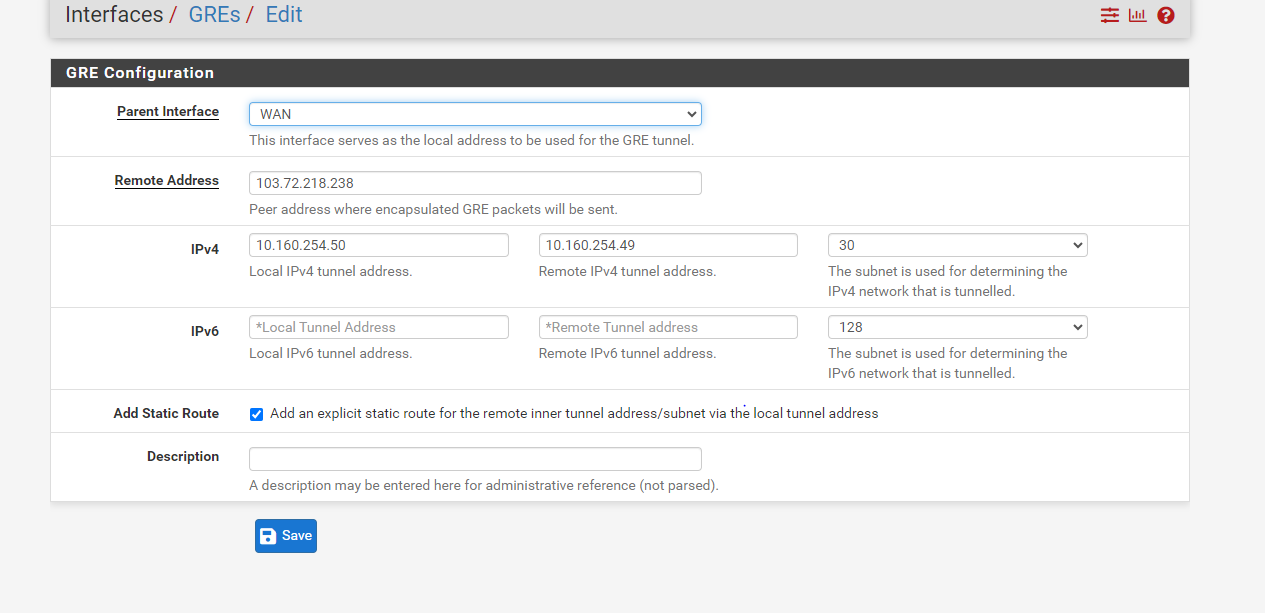
- GRE interface definition
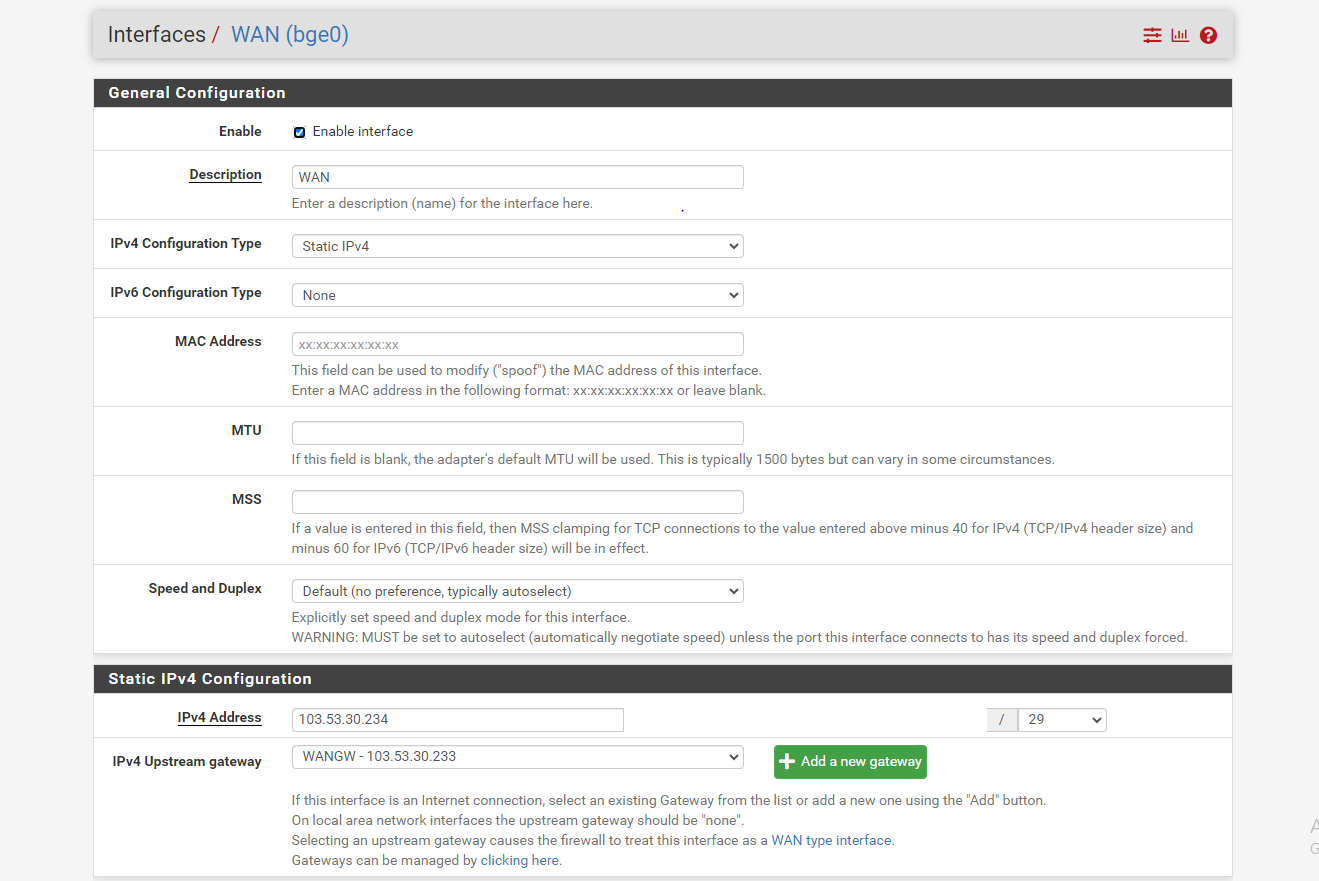
- Current WAN Interface addresses in both ends.
- Current pfSense outbound NAT rules
- Current pfSense GRE interface Rules
A few other observations.
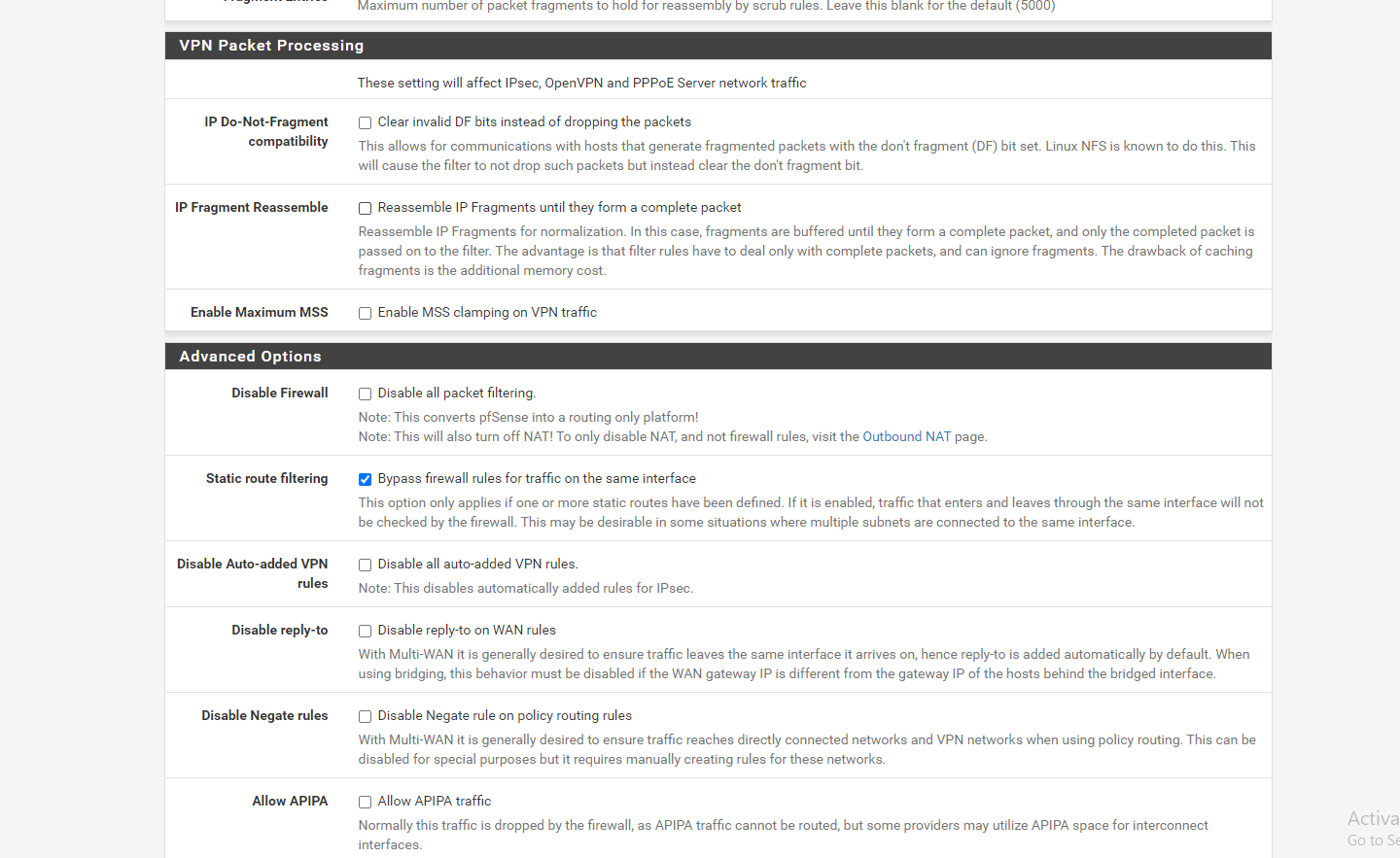
1: There is somthing wrong with your Microtik config as traffic sourced from 103.72.218.238 also gets forwarded over your GRE tunnel
2: There is no need to tick “Static Route filtering” in advanced settings. This GRE Tunnel does not need that. -
@Rohit-0 Anyways - since the firewal log blocks TCP:FA from 192.168.2.20 towards the internet, there seems to be something causing assymetric routing as that packet is not matched to an existing state. That can be many things, but it is quite often related to faulty NAT config in either end of the setup.
-
@keyser i will look into why public address is being forwarded ,
here are my pfsense setting snapshot
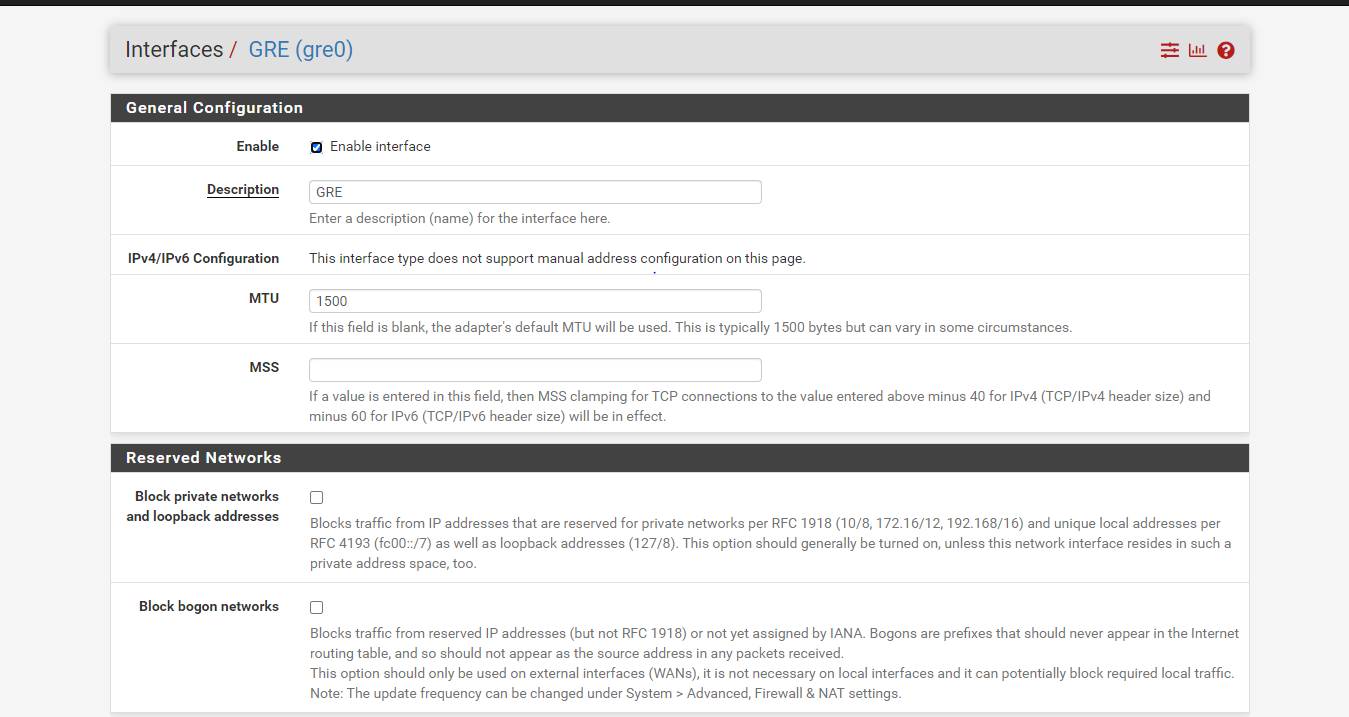
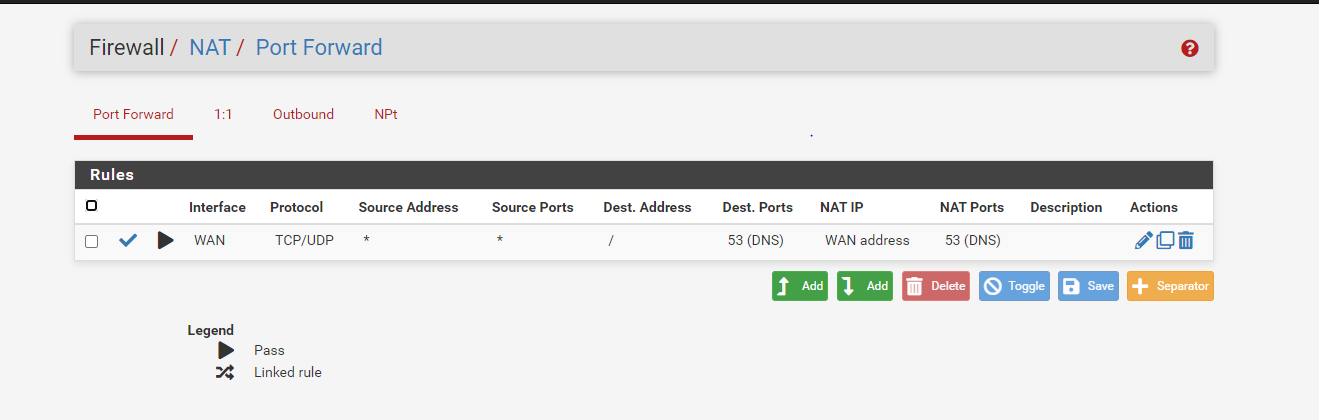
-
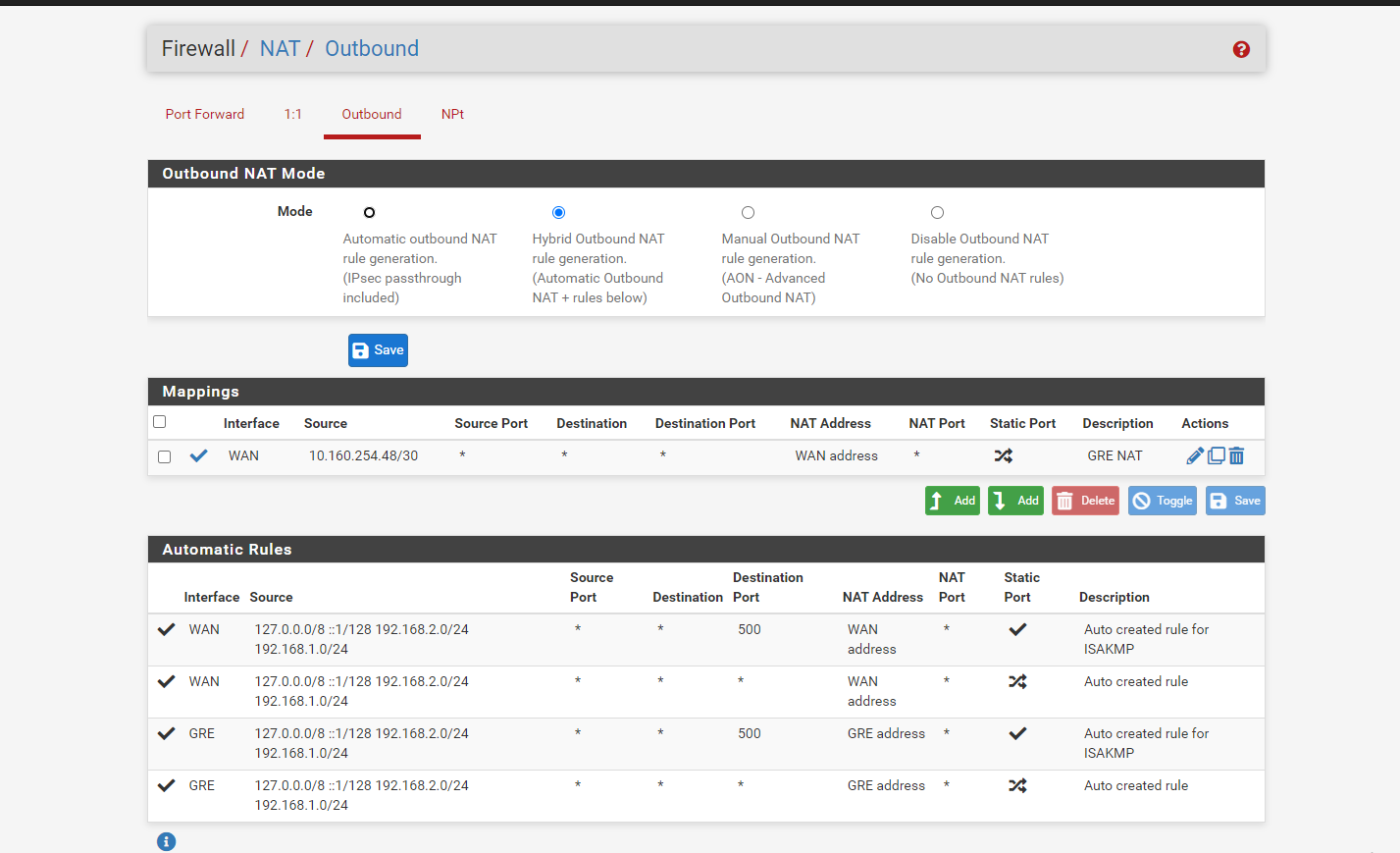
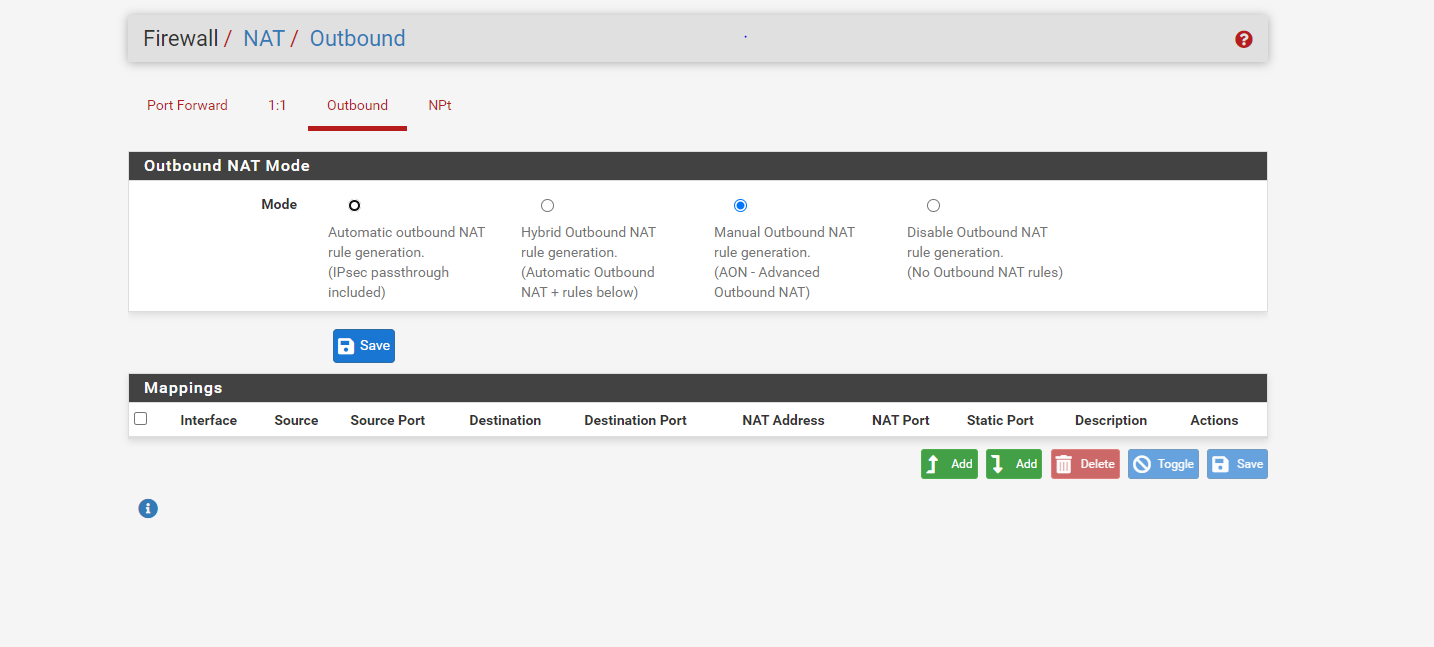
@Rohit-0 Right now you are missing outbound NAT rules intirely. You need to have pfSense NAT both you local pfSense Networks and the Remote Mikrotik client network. I think clicking “Automatic outbound NAT rule generation” should do it as your routing setup should make pfSense include the remote mikrotik network in the NAT for WAN outbound traffic.
But if it does create automatic rules for NAT’ing on the GRE interface as well, you instead need to create a manual NAT rule on Interface WAN stating that all 192.168.1.0/24 and 192.168.2.0/24 (according to your drawing) should be NAT’ed using the IWAN interfaces address.
Please post the revised NAT setup
-
@keyser here is my revised NAT rule and let me check
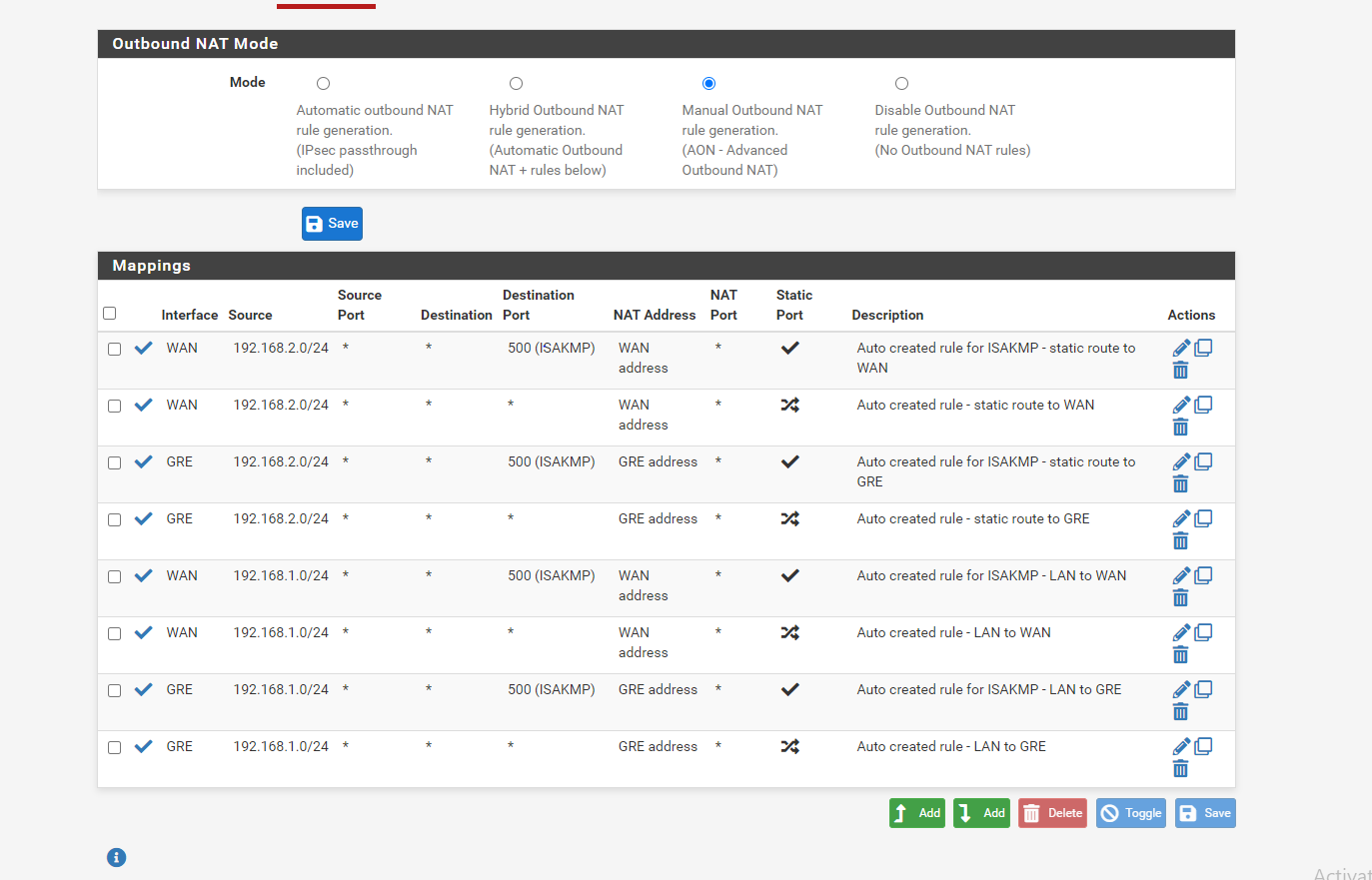
-
@Rohit-0 Still i'm getting blocked for GRE traffic
-
@Rohit-0 Thanks it was my mistake from mikrotik side i should not allow fast path in GRE setting , Thanks again for everything
-
@Rohit-0 My pleasure - but the Outbound NAT rules are still wrong - it will work, but not like you intend (fully routed).
You need to remove the four rules assigned with the GRE interface. They are not needed and will cause all traffic from the mikrotik network to appear as being sent from 10.160.254.50 -
@keyser thanks again