TP-Link Easy Smart Switch security question
-
hi,
last time i checked it was possible to remove the port from any membership or vlan 1
gonna look up where this switch (sg-108e) is doin his job right now ... and check back
keep you postedbr np
-
@noplan Any luck?
Are you removing the ports using the web gui or @tpham3783 's guide for hexadecimal hacking a config backup?
EDIT: I was able to set a port to 2 to a different VLAN and it stopped showing for VLAN1:

-
@NicklyJohn You are confusing port based VLAN and 802.1q based VLAN.
However, since v3.0 it is possible to remove any port from VLAN1 in 802.1q VLAN Tag. -
Hey
I have TL-SG105E v5.0. My firmware doesn't work.
Can someone share a flash dump for the EN25H16 dice? I am from Poland and my English is not good.Thank
-
@devport said in TP-Link Easy Smart Switch security question:
TL-SG105E v5.0.
Your saying they are back to their nonsense of not allowing removal of vlan1?
-
@johnpoz sorry model is TL-SG108E v5.0. My faul. No this problem. My problem is not run switch. Boot start -> processing -> supply diode 2x flash -> and reset boot sequence. No connect switch all lan port. So i looking for software from flash but from site TP-Link is not image SPI flash.
-
@devport You may can use .bin image from TP-Link website to build a .bin with entire 2MB memory flash size. But first you need read your flash to preserve bootloader (if not yet damaged) and copy & paste all content from TP-Link .bin upgrade image, starting paste in proper offset on the dump file. If your bootloader if damaged, you need a good dump from working v5 and change/write your Switch's MAC address in correct offset before write the dump. You can send me your dump and when have time i will inspect it.
-
Just curious why would you spend more than say 10 minutes on say trying to flash the firmware.. Its a $27 switch on amazon, you could have a new one tmrw ;) I don't see spending more than a few minutes on trying to get something like that to work..
A 200$ ok, might be worth spending some time on.. But a $30 switch.. not worth more than a few minutes of time if you ask me.
-
@Apocalypse I don't know if the bootloader is broken, so I asked if anyone has a flash memory dump file. I don't know how to check it, the beginning of the Hex code is different than in the file from the TP-Link website.
@johnpoz if rescue the switch i so happy. it interests me. -
@Apocalypse My dump File:
https://www.mediafire.com/file/siafjrigd2d19cy/TL-SG108E_V5_Flash.bin/fileMAC address at offset 0x1FC000 (filled in with "AA BB CC DD EE AB"). I Change it.
-
@devport I will examine it when I can. It is normal for the Dump not to begin as the firmware file. From 0x0 to at least 0x1000 is the bootloader. In the update file there is no bootloader.
-
@devport The dump file looks correct. I think this is a hardware problem.
-
@Apocalypse Thanks
-
@warheat1990 said in TP-Link Easy Smart Switch security question:
Hello,
I'm planning to buy TP-Link Easy Smart lineup (TL-SG1016DE and TL-SG108E) so I can separate my LAN. Here's the current setup in my house.
modem -> pfSense -> unmanaged switch (will replace this with easy smart switch) -> patch panel -> keystone jack / wall plate across several rooms in the house -> devices
So what I'm trying to achieve is devices from other room won't be able to access the devices in my room. For example my sister laptop won't be able to access my NAS or PC.
However I look around the internet and found this post on reddit about the easy smart switch lineup.
I have one of these and it's a huge hassle to get it working just so you can change the default password at minimum.
And more importantly the VLAN stuff, while obstensibly working, doesn't do network separation; an attacker on VLAN1 can spoof the ARP table for other VLANs. So it works but not for security, so it's useless.source: https://www.reddit.com/r/homelab/comments/4tym2z/best_cheap_gigabit_switch_4060/d7pvtxc/
Is this true?
I read the whole 14 pages I found in this forum : https://forum.pfsense.org/index.php?topic=76022.0 but I can't seem to find anyone mention it.
Is there better alternative beside these easy smart lineup with similar price range?
Any help will be appreciated and apologize for bad english
for basic home use i wouldn't worry about what that statement is saying. this comment is referring to someone plugging a physical hardware device into the switch, and hopping between vlans that pass through it. your layout appears to put your new managed switch someone not out in the open?
as for preventing devices from communicating between the vlans/subnets, you'll have to put in a firewall rule to prevent that. the switch has nothing to do with that in this case. by default pfsense lets each interface/vlan go anywhere so it can access the internet. you will need to setup a rule so the subnet you put your sisters laptop on can "go anywhere except the network the NAS is on". i think you can also setup a rule on the nas network to not allow access from the interface your sisters laptop is on. i haven't played around enough yet to tell you which is better or the correct way to go about it sorry.
these switches are cheap but they do their jobs. i have the 8port managed and 5 port managed from tplink. super easy interface once you figure out how the vlans work and how to assign ports properly. just use vlan1 as your lan, tied to your pfsense lan. tag all vlans on port 1 so the switch receives all vlans. then just untag each port you want to be that vlan. if you use multiple switches, keep them all on vlan1 untagged ports connecting them with static ip's tied to your LAN interface on pfsense (if this is where you keep all your network based item ip range). if you give a 2nd switch a static ip of say, 172.30.9.1, but plug it into a port untagged for say, 10.10.1.1, internet will still pass through but you'll lose access to the web interface.
these are my settings on the first switch out of pfsense
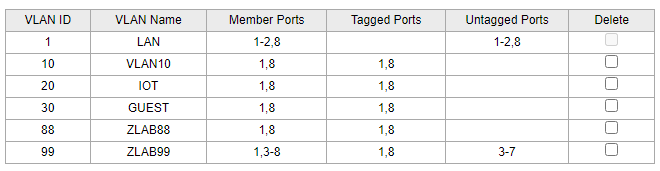
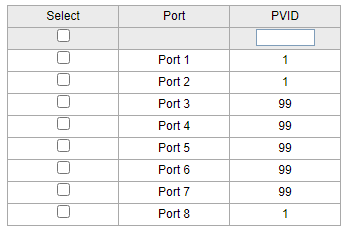
then 2nd switch going out of port8 as vlan1 untagged, but tagged with all vlans going in port1 of switch 2 as vlan1 untagged again, but carrying all tags. then you can assign switch2 to any of your vlans.
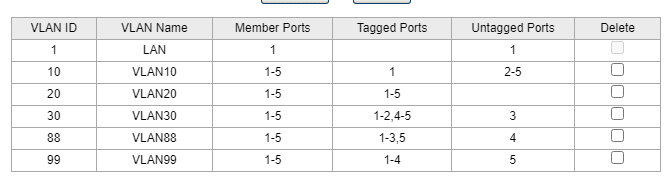
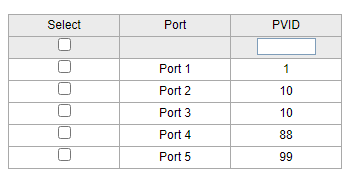
-
said in TP-Link Easy Smart Switch security question:
https://www.reddit.com/r/homelab/comments/4tym2z/best_cheap_gigabit_switch_4060/d7pvtxc/
I think what that is talking about is their old and before when they wouldn't let you remove vlan 1 from ports.. Yeah that is moronic - and they did finally fix it. And makes a vlan capable switch pretty freaking useless..
While not a fan of the tplink switches, as long as the model you have allows for removing vlan 1 when you want to put it on a different vlan you should be fine..
-
@johnpoz darn. i sorted from newest to oldest and somehow replied to the first post from 2016! how bout that effort for a first post hah. whelp the info still applies and can hopefully be helpful to others using these cheap things
-
Hello,
I've just completed setting up VLANs using a TL-SG105e switch. Despite encountering issues with the switch management software being accessible on every port within each VLAN, I found a solution. I created an additional VLAN called "LINK" with a subnet mask of /30 (in my case, 192.168.10/30) on my Netgate 1100 router. I didn't set up DHCP for this VLAN. The Netgate router was assigned 192.168.10.1, and the switch was given 192.168.10.2.
I'm not a network security expert, so I can't vouch for how secure this setup is, but at least it prevents unauthorized access to the switch admin panel. However, a drawback is that if you need to reconfigure something, you must temporarily expand the subnet mask to /29, assign an IP alias, make your changes, and then return to the "secure" settings.