Authenicated NTP
-
I have a PR open that incorporates the patches @LamaZ made (more or less) as well as adds a key ID field to the web GUI. If anyone is interested in testing it out to make sure I didn't miss anything, I can upload equivalent patch files here.
pfsense/pfsense#4658 -
@MatthewA1 That's amazing can you post the patch, I would like to test it on 23.05.01 "pfSense Plus"?
-
@JonathanLee Thanks! I tested on a CE 2.7.1 VM as I only have one Plus device, and it's very much a production device. Here are the three patch files. I'm not 100% sure they are compatible with Plus as I have not looked at the PHP source files for 23.09, but I don't believe there is any difference with the modified sections in CE vs Plus.
These are created based on master+9257345. It seemed to work fine with my NTP server, but it would probably be good if someone could test against NIST NTP servers (as I also just setup my GPS based NTP server, so it's possible it was misconfigured but worked anyways)
system.inc.patch
status_ntpd.php.patch
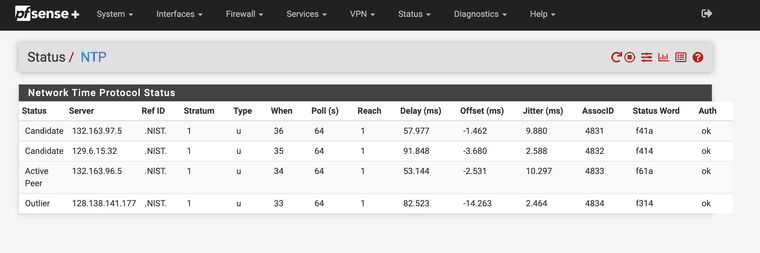
services_ntpd.php.patchAlso, the table on the NTP status page is wider than the title header. I'm not sure there is a way to fix that other than removing one of the columns. If anyone has suggestions, please do share.
-
@MatthewA1 @LamaZ his was the same way with the column issue see below.
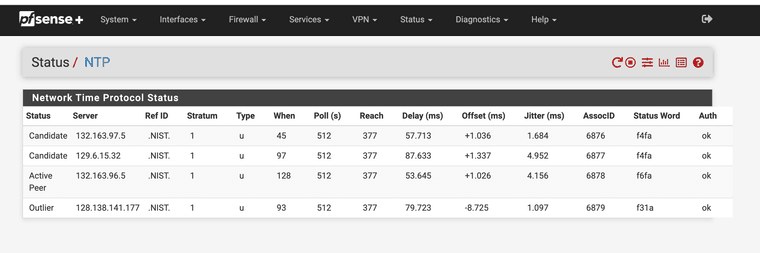
-
All of them show ok under debug thanks for doing this.
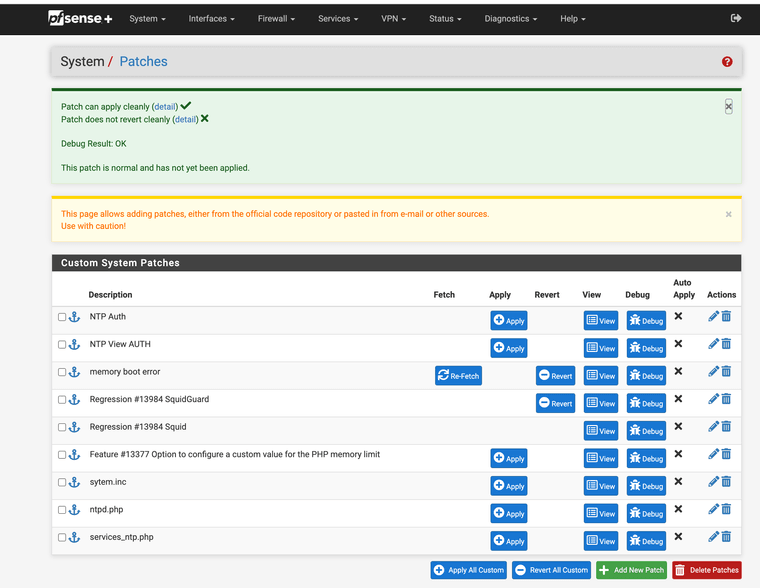
I had to remove /src from all the patches or they would not work with plus that was the only issue strip count zero
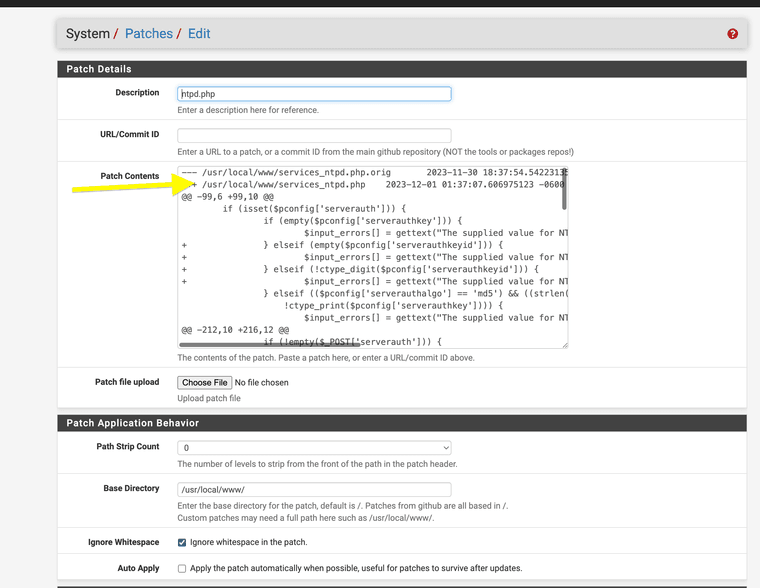
System works as expected for input area YEAH!!!
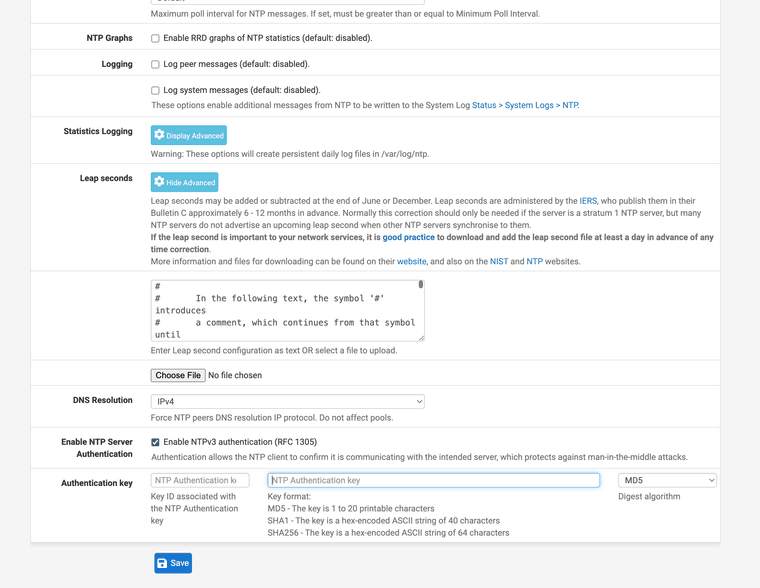
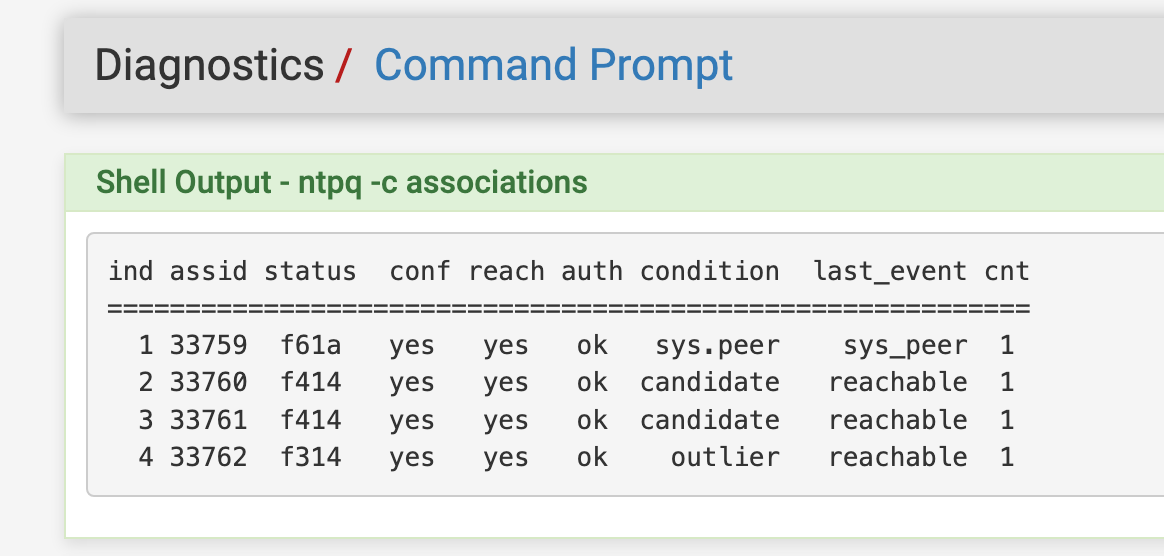
Time is showing AUTH under ntpq -c associations
This is great !!
Functions with the status patch also for nist.gov authenticated NTP project.
I had to originally get approved by NIST to even be able to use authenicated NTP with them.
This is an amazing addition to pfSense for time protection from the aging non autheniticated NTP protocol.
-
Ah I had been using Path Strip Count = 1 when I was testing. It probably makes more sense to just edit the patch file.
Here they are corrected (it won't let me edit the previous post):
system.inc.patch
status_ntpd.php.patch
services_ntpd.php.patch -
@MatthewA1 After so many posts in the forum you can edit old posts I think it has been a while for me.
-
i was fully onboard until i realized access requires the requestor to furnish the following:
- Name and postal street address of the organization or individual
- Name and contact information for the system operator and an alternate name if possible. These should include the e-mail addresses and the preferred contact method.
- Network IP address of the client system that will be used to query the NIST server. A network name is desirable but not required, since the system will authenticate the request using IP addresses only. Users may request up to 4 contiguous IP addresses that will share the same key.
you can't claim tinfoil hat and then furnish a full government and USPS street address to the Feds!
all seriousness though, these patches could easily be modified to configure a private authenticated NTP provider. good stuff, OP. i agree they should be added to base install.
-
@cyberconsultants The patches are not specific to NIST's authenticated NTP service, as NIST just implements authentication per the NTP RFCs. In fact, I tested these with my own NTP server which sources time from GPS and provides authenticated NTP service. The difference is, if you control your own NTP server, you can get by with only using key ID 1 (currently hard coded in the pfSense source) whereas using NIST's (or likely anyone's) public service, you have to be able to set a different key ID.
Side note: For anyone who doesn't want to go to the trouble of sending a letter or finding a fax machine, unlike what the NIST website says, they now do the key process all via email (and their file transfer site).
-
@cyberconsultants I can tell you projects that seek to improve aging protocols (NTP) take time (no pun intended) and trusted testers. I personally had issues with NTP getting hacked and having 10-15 jumps durring college tests without use of authentication (checked with analog gear clocks). I have not had that issue once it was moved to NIST authenticated time. It's a great project that seeks to fix issues like this. So far I have not had issues with use of these services. Again I was taking cyber security tests so I would expect the class wanted to drip students toes into some of the major issues, and gage how they resolved it. For me I flat moved to authenticated time. I trust it, it works it's secure. They even renewed my keys for me. Thank you NIST. I have not had time jumps now and I pray it stays that way.
From a university network perspective, the use of authenticated NTP with NIST is an improvement over the non authenticated version. Deployment of it requires it be tested, and a GUI that is easily accessible. Again the key should be hidden from prying eyes
 . It's that important. Make a new username hide the key from everyone that access the firewall important.
. It's that important. Make a new username hide the key from everyone that access the firewall important.With that thought

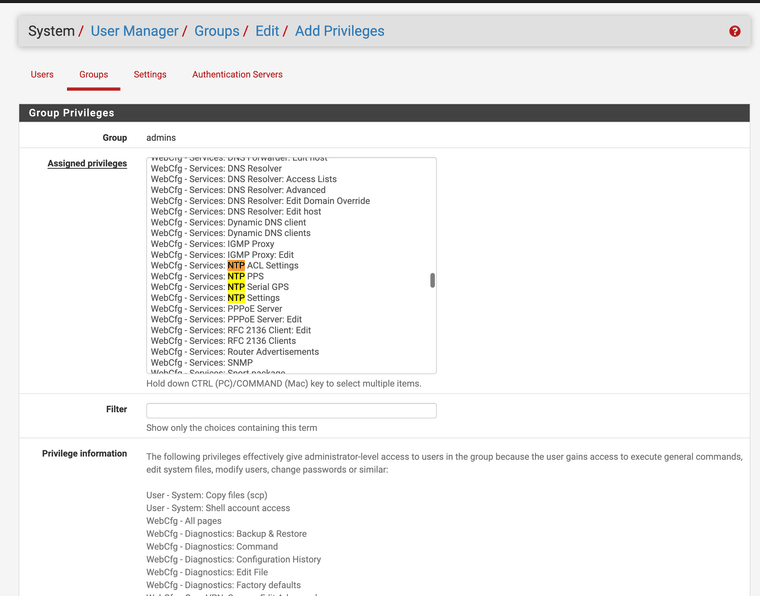
@stephenw10 can NTP options be specifically assigned in user manager and be blocked for others? With reflections on this GUI patch I just tested maybe it is also a good time to check with you. I do not think many admin have had the ability to use it without custom patches. Maybe the user manager does not list it yet.
@MatthewA1 maybe your GUI option should also be included in a user manager feature.
You know that song

 one thing leads to another...
one thing leads to another... -
https://redmine.pfsense.org/issues/15073
I just submitted a feature request for new user NTP keys privileges profile to be added. It should specifically list NTP keys so super admin can hide them from settings.
-
@JonathanLee I'm thinking maybe this should be done as part of a larger update such as this:
- The NTP key management should be it's own tab on the Services > NTP page
- New permissions are for accessing this page
- Multiple keys may be specified
- An optional field for key ID field is added to the NTP Settings page on a per server/pool/peer basis. This would let users manage what key is used with which server so that
- Different keys can be used for different servers (including no key for some servers)
- A user with permission to configure NTP servers can use the keys without actually knowing the key values
-
@MatthewA1 I couldn't agree with you more. YES

-
Are there authenticated NTP servers for public use other than the NIST ones? I wanted to test this and see what the generated ntp conf files look like, but not if the only option is to fax/snailmail a request. To be honest, it seems to me that time would be better spent implementing NTS instead.
-
@marcosm NIST actually does it completely by email now, but the website is out of date. I just got a key last week actually, and it was about a 3 day turnaround. You just email internet-time-service@nist.gov with the same information they previously wanted by mail or fax.
As far as I know, there is not anyone else (aside from one-off NTP servers) that provides authenticated NTP services, or at least not for free. NTP.org does not support it for sure. It looks like Canada's NRC does but for a significant fee. -
Did the GitHub package get merged with the updates? I saw you submitted them this morning. EPIC!!!
-
Did this github ever get merged?
847e417b5612f28bc1e84ca028a980df9c5c57a7
I can pull it in patches now
-
 J JonathanLee referenced this topic on
J JonathanLee referenced this topic on
-
@JonathanLee It has not, and I have not seen any further feedback.
I agree these aren't all the changes that it would be nice if were implemented, but it at least takes it from an almost useless feature (because you are never going to get the key ID 1 from a shared system) to something with some problems.
I'm willing to add some of the missing pieces (e.g., per server authentication) but I'm not inclined to do so if it isn't going to be reviewed. As I mentioned in the Redmine issue, if someone can tell me what the most important changes needed for this to be accepted are, I'd take care of them.
@marcosm Sure, I think NTS would be great, but for now, at least as far as I can tell, none of the major time providers support NTS, and I doubt many GPS based time systems will support it for some time (at least the lower-end systems) -
@MatthewA1 Netgate I have been told has a very small staff and strict budget, they will get to it eventually. Don't be discouraged.
-
I made an update where authentication can be enabled or disabled per server/peer (and it actually validates that you didn't enable authentication for a pool).
The latest version can be applied using the package patch using this URL if anyone wants to test:
https://github.com/pfsense/pfsense/pull/4658.diffSide note: I would like to further improve this by allowing multiple keys to be configured and then have a dropdown for each server to select the key (or no authentication), but I don't see any way to do that without making some significant changes to the config.xml format. I don't think I should go down that road without input from Netgate first though.
I think this needs to be done anyways to resolve some other issues such as:- Like @marcosm pointed out on Redmine, there are two places to configure NTP servers, but they edit the same config option while implying they are separate settings
- Disabling the NTP server from Services > NTP results in ignoring time servers set in System > General Setup, but there is no indication of that on the General Setup page
I'll add a couple more notes on this to the Redmine. I'm not sure if this should be a separate ticket or not either, but I think I don't want them in the same branch/PR for now.