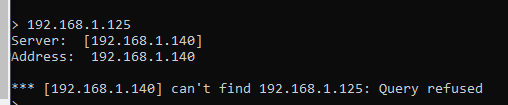
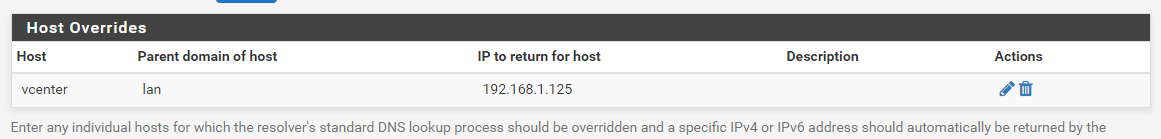
PFSense Query refused
-
@gertjan said in PFSense Query refused:
nslookup will ask for the hostname when an IP is givnn
Huh?? Nslookup will do the PTR for that IP..
set debug and see for yourself.
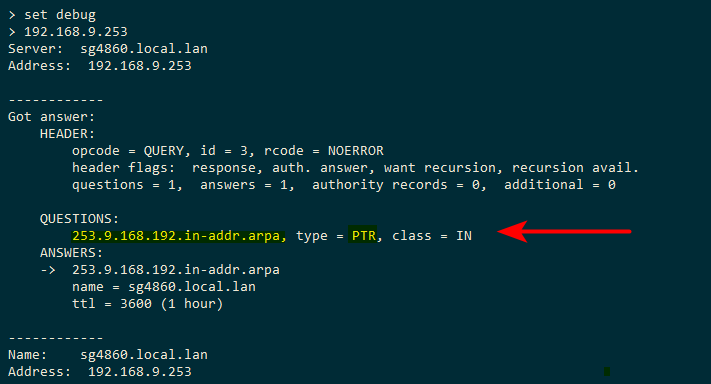
If your getting refused back, then yes that screams to ACL as problem.
-
@johnpoz : I just re discovered that, one hour ago.
I'm more a dig man. -
Yeah same here - not sure why anyone would use nslookup ;)
-
No ACLs set unless there is one out of the box. I was honest in the OP, I installed from ISO and the only changes made were the ones mentioned.
-
Where are you doing the query from? A device on the pfsense lan? Or some downstream network, a vpn connection?
Out of the box yes ACLs are set for the networks directly attached to pfsense. If its a downstream network, or a vpn tunnel IP then no you would not be able to query unbound on pfsense.
Pfsense IP is what? 192.168.1.140, what is your client IP that your running nslookup from?
-
@johnpoz client is 192.168.1.6, same network, directly connected, only thing between them is a switch.
This is part of why I was so baffled by the problem. I've set this up a million times before, on this network, with that switch, with this pfsense config.
Worth mentioning when I used diagnostics to have PFSense query itself it worked fine
-
Did you turn off the auto ACLs?
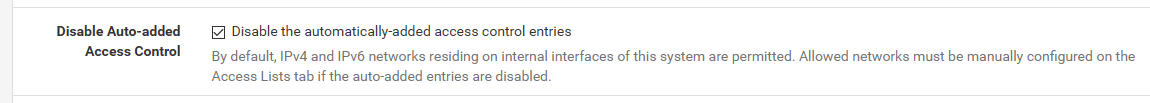
Under the resolver / advanced settings?
Do a query for pfsense name.. does that work?
-
@johnpoz I'll check that out! Thanks man!
-
@grantcurell said in PFSense Query refused:
I installed from ISO and the only changes made were the ones mentioned
and then you set up a network where :
@grantcurell said in PFSense Query refused:
in this case it isn't serving as the gateway
which means you left default (networking) settings.
That's perfectly fine.
And opens the door of all kind of situations.Please understand : install pfSense from scratch.
Hook up the WAN.
Hook up a PC on LAN.
It works.
So, tell us what changed, and we'll tell you what to do or undo. -
I Irk 0 referenced this topic on
-
@bingo600 said in PFSense Query refused:
Are you using unbound ?
I had to add my openvpn ranges to the access-lists section as allow , in order to be able to resolve DNS from those.
Seems like unbound default allows known nets (assigned to interfaces) , and refuses qureries from all other nets.
Add "unknown nets here" (Unbound settings)
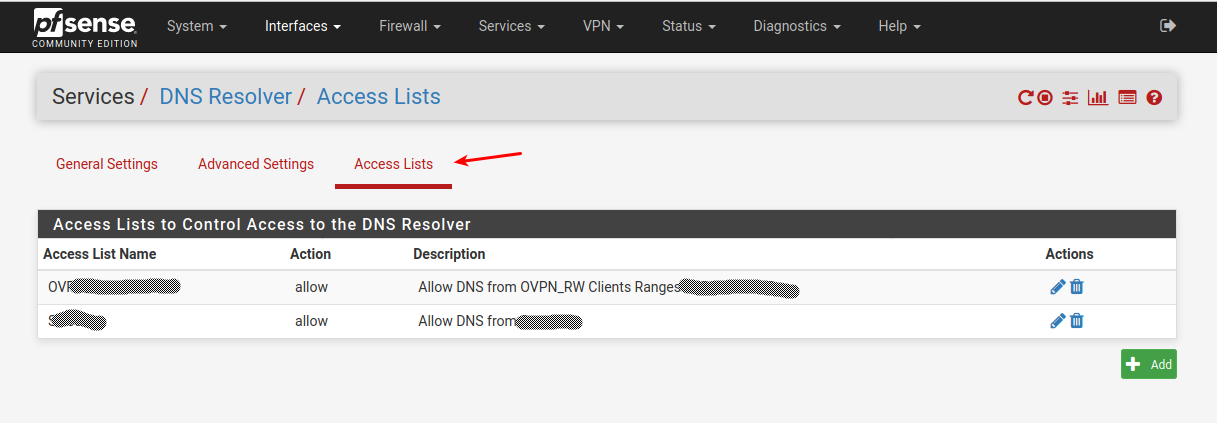
/Bingo
Worth noting this occured with a VLAN interface srced traffic... It might be because I need to bounce the unbound daemon, or whatever... adding the ACL allowed me to src traffic from a macvlan hosted docker container bound to a subint on a synology NAS. The tagged traffic was arriving, and I was seeing refused responses from pfsense at the LAN interface of the pfsense. Adding the subnet for the VLAN interface resolved the issue. Thank you!