PfSense HAProxy certificate export import
-
-
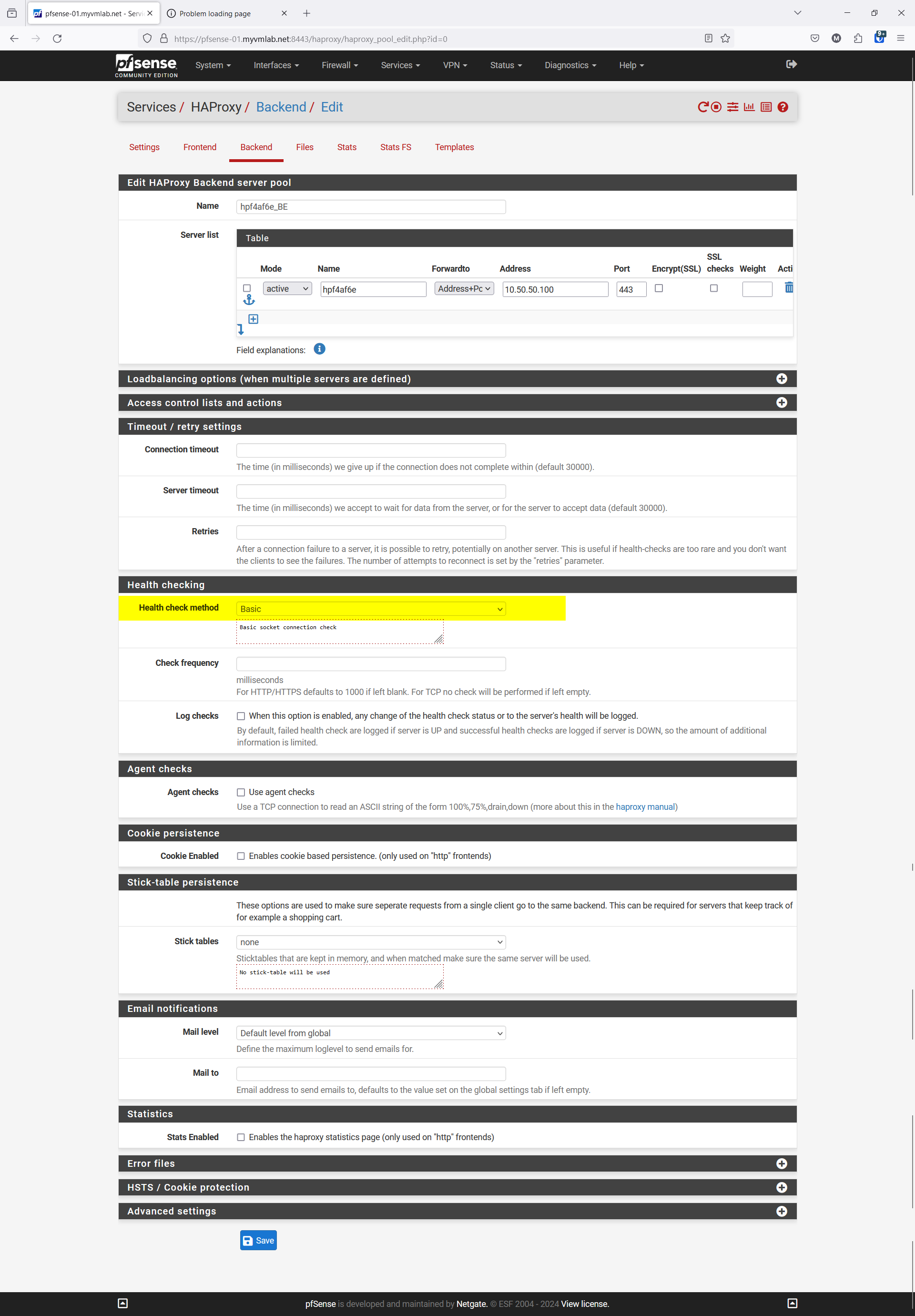
Backend I changed it to Basic Health Check. Works now
-
Frontend I change it to port 443 ( I was confused as to the port to use ) It's all on 443 now.
1st off Thank you for all your help so far. You have been very kind.
Firewall Rule as I don't 100% understand that part yet. So I am stuck Firewall Rule and i thing I should have it working after that.
Fresh Screenshots w/ Highlighted Changes for reference as of this post
FYI.. This is the YouTube Video I am working from:
link text
-
-
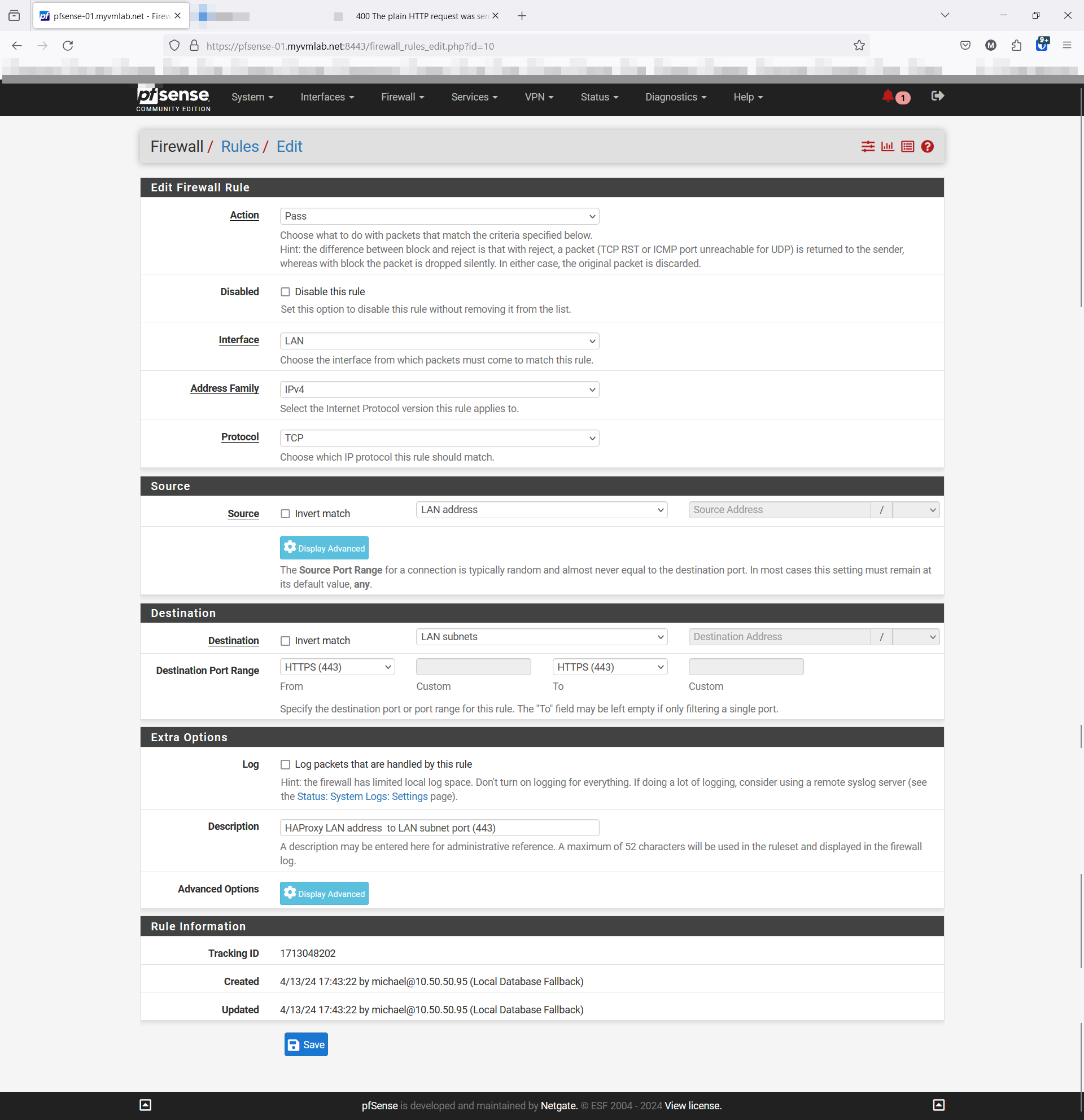
Here is my interpretation of the Firewall rule
Action: Pass
Interface: LAN
Address Family: IPv4
Protocol: TCP
Source:: LAN address
Destination: LAN subnet
Destination Port Range: HTTPS (443)
-
@VMlabman said in PfSense HAProxy certificate export import:
Frontend I change it to port 443 ( I was confused as to the port to use ) It's all on 443 now.
443 is the default port for HTTPS. If you use a different one you would have to state it in the URL, e.g. https://nas.local.lan:11443.
A basic idea of a reverse proxy is to share default ports for multiple backends.
This presumes that the single frontend is configured to determine, which backend you want to use. This is mostly achieved by the host header.When using port 443 for the HAproxy frontend, you have to ensure, that the pfSense web Configurator listens on a different port (443 is default, when enabling HTTPS). It can be changed in System > Advanced > Administration. Doing so you have to state the port in the browser then.
Here is my interpretation of the Firewall rule
What do you want to achieve? I guess, you want your LAN devices to allow access to HAproxy, which is listening on the LAN address.
Hence the source has to be "LAN subnets", the destination "LAN address".However, out of the box there is an allow-any-to-any rule on LAN:
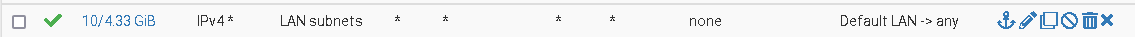
If you didn't remove or restrict this, it would allow the access to HAproxy already and there would be no need to add an additional rule for it. -
Hello,
I added the Firewall Rule and I get : ( Warning: Potential Security Risk Ahead )
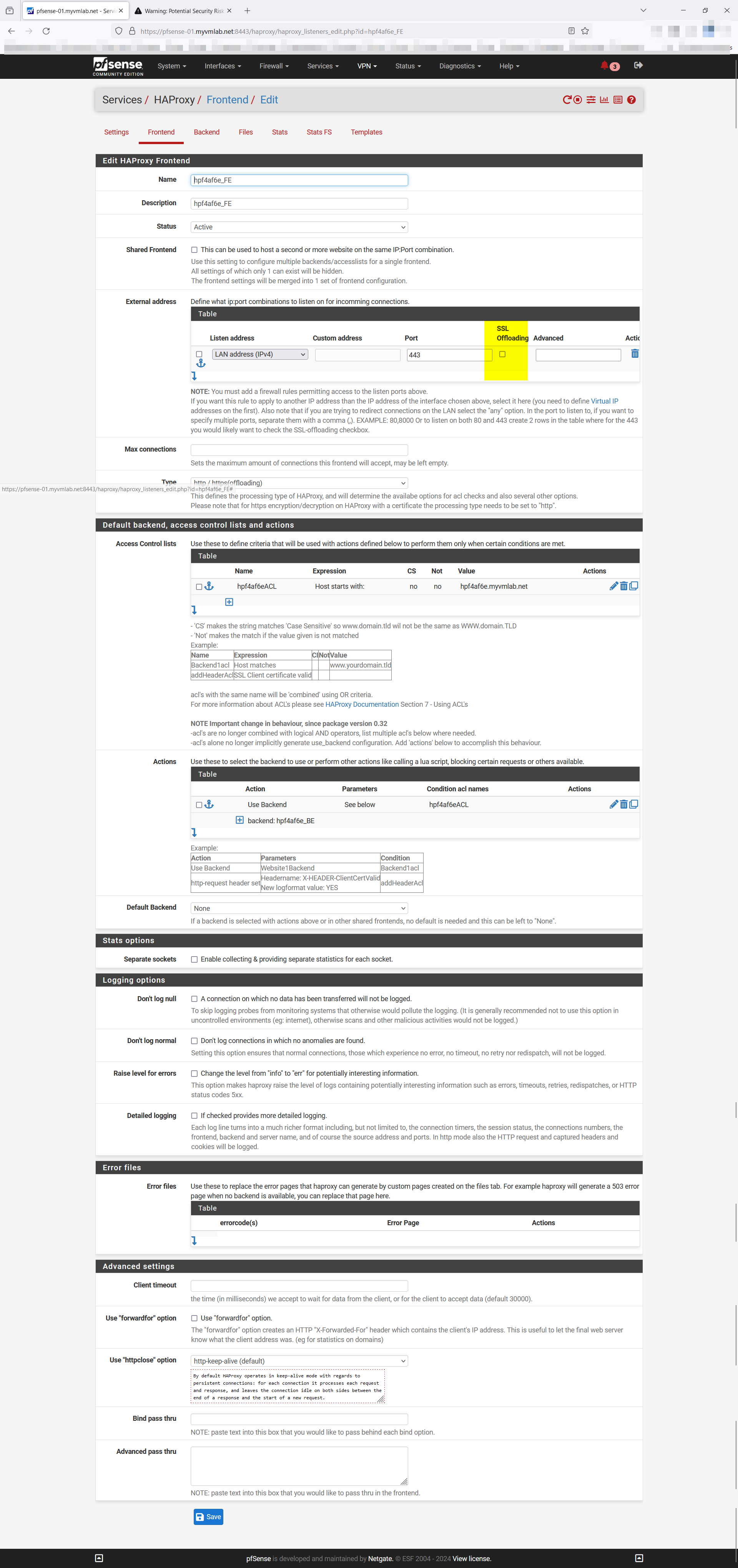
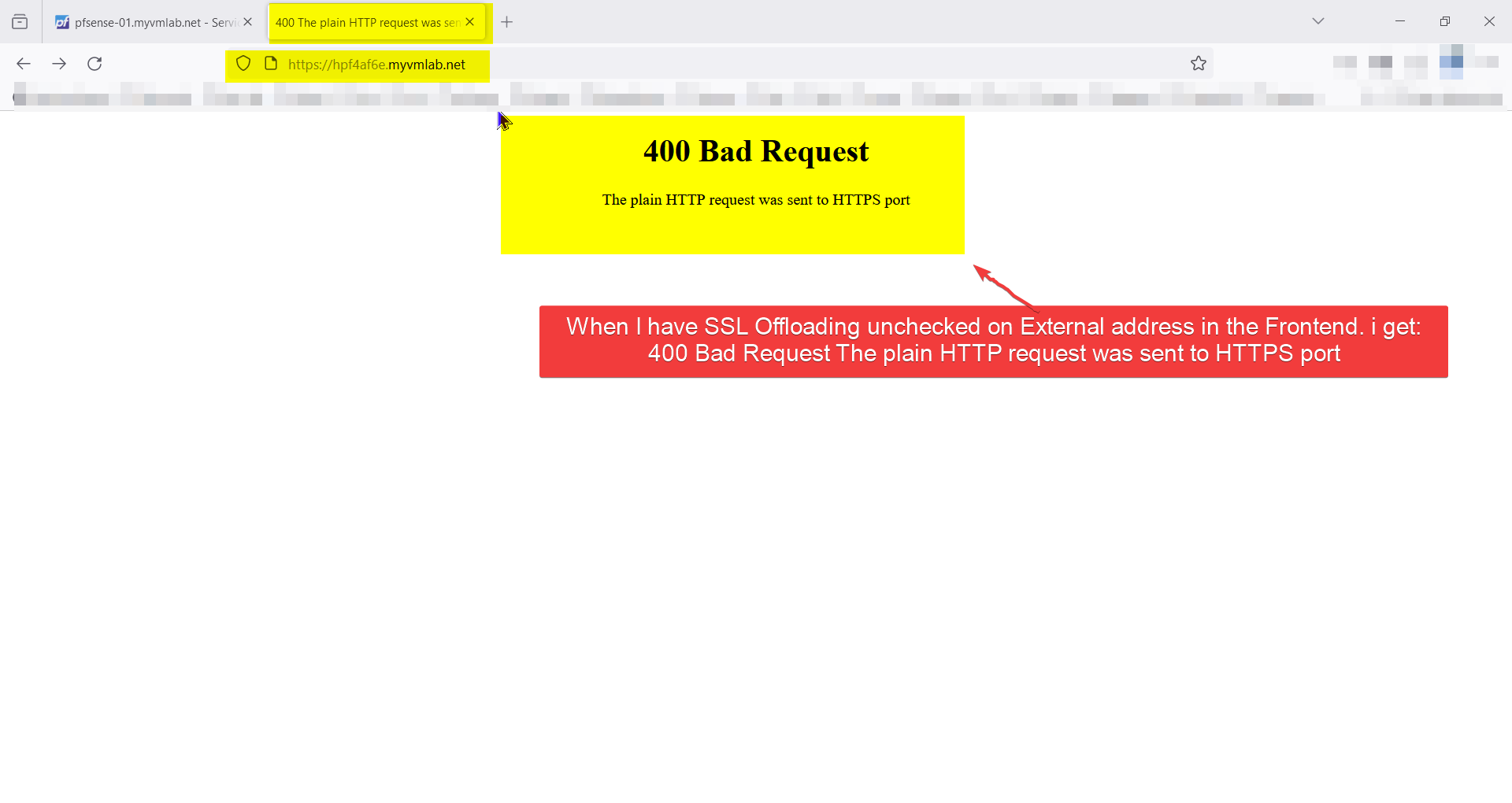
When I have SSL Offloading Checked on External address in the Frontend. i get:
( Warning: Potential Security Risk Ahead )When I have SSL Offloading unchecked on External address in the Frontend. i get:
400 Bad Request The plain HTTP request was sent to HTTPS portI tried to add my NAS device in as a test to see what if might work and I can't get the Backend to start no matter what I set the Health check method to Basic or HTTP. I did come across this digging around on the forums to find there may be an issue with changing the setting in the Backend and having to copy it or re build it. I did both with out a change in the error. I even used a different Frontend to test too. https://forum.netgate.com/topic/182581/may-have-found-a-bug-in-haproxy-using-ssl-backend-ssl-health-check link text
WARNING] (12356) : config : Server Qnap-01_BE_ipvANY/qnap-01 is DOWN, changed from server-state after a reload. 0 active and 0 backup servers left. 0 sessions active, 0 requeued, 0 remaining in queue.
I am going to try to re install the package from package manager to see it it fixes anything.
Any suggestions ?
Thank you,
-
@VMlabman
In the pfSense GUI or in the browser?
If in the browser, from where?
Something more then this? -
I will include screenshots as well
On pfSense in HAProxy When I have SSL Offloading Checked on External address in the Frontend. i get: ( Warning: Potential Security Risk Ahead )

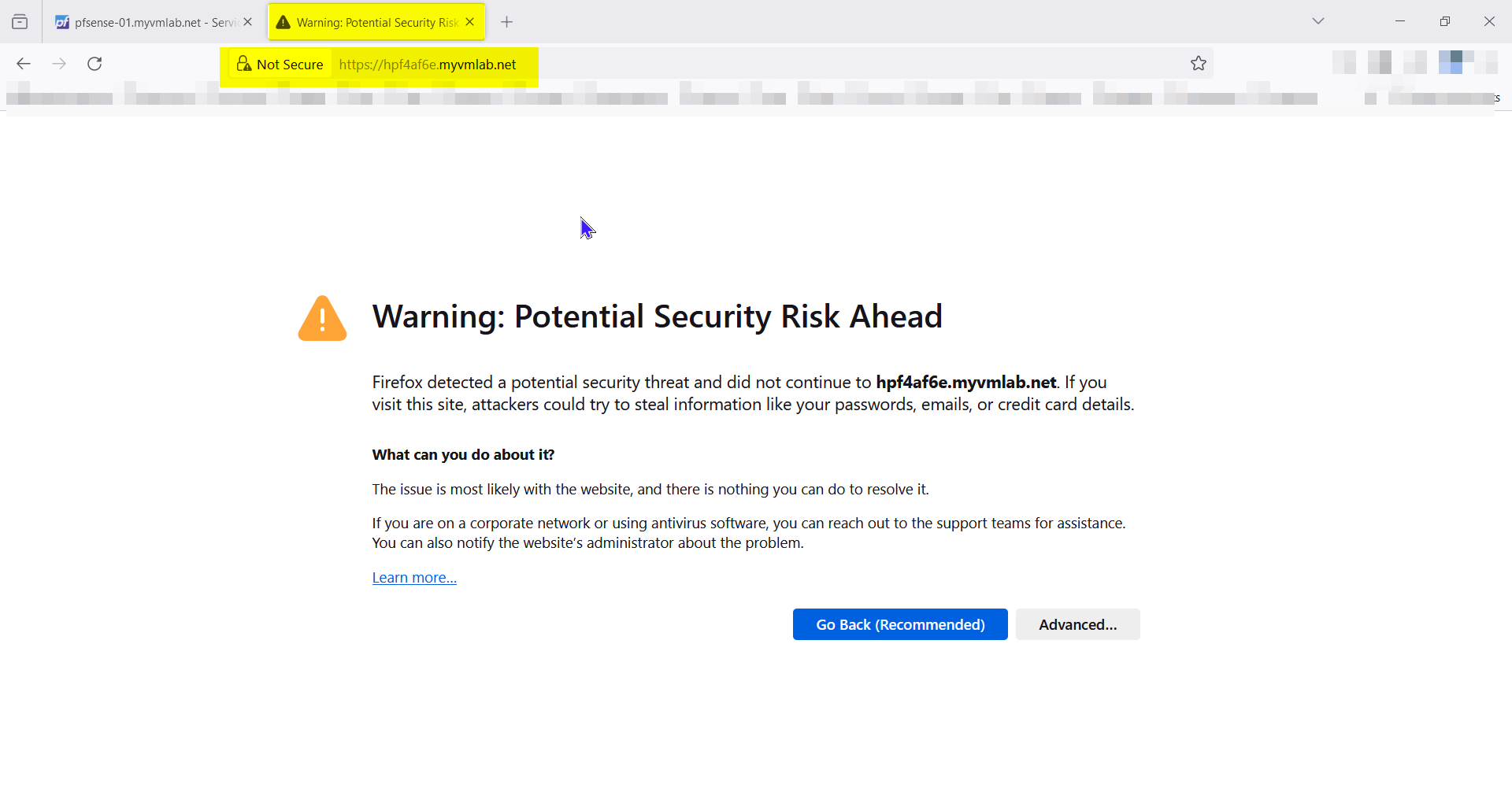
When I have SSL Offloading unchecked on External address in the Frontend. i get:
400 Bad Request The plain HTTP request was sent to HTTPS port
-
@VMlabman
I guess, your browser is not accepting the SSL certiificate, if SSL is enabled.
Hit the Advanced button to show error details. Also you can show the certificate.You need to assign a certificate from a trusted CA to the frontend to load the page in the browser without issues.
If you disable SSL, it would be a wrong configuration, so forget this error 400. If the browser tries to connect to https site (port 443) it's expecting to get an SSL certificate.
-
I am using a .wildcard certificate from my pfSense trusted CA to the frontend. I also imported the same Cert into the Printer and NAS. I can create a Cert individually for each of them. I see where in the Edit HAProxy Backend server pool Under Backend I can set a CA: and/or a Client certificate: Shouuld I create the Certs and import them into the devices and list them under the Backend for each host?
Here are some screenshots of the Browser Errors I get in FireFox and Google Chrome. Maybe shis will point at somthing.
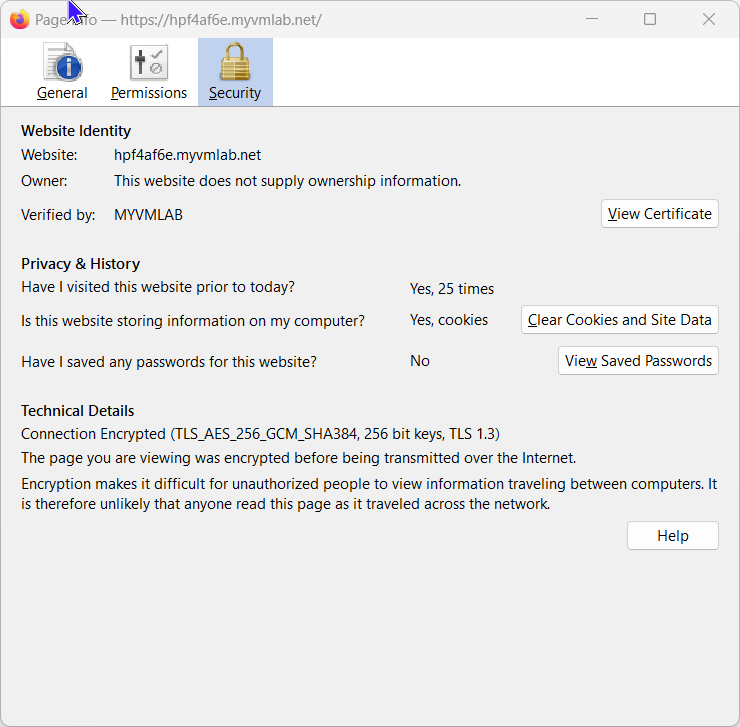
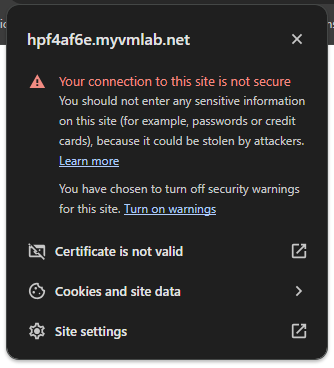
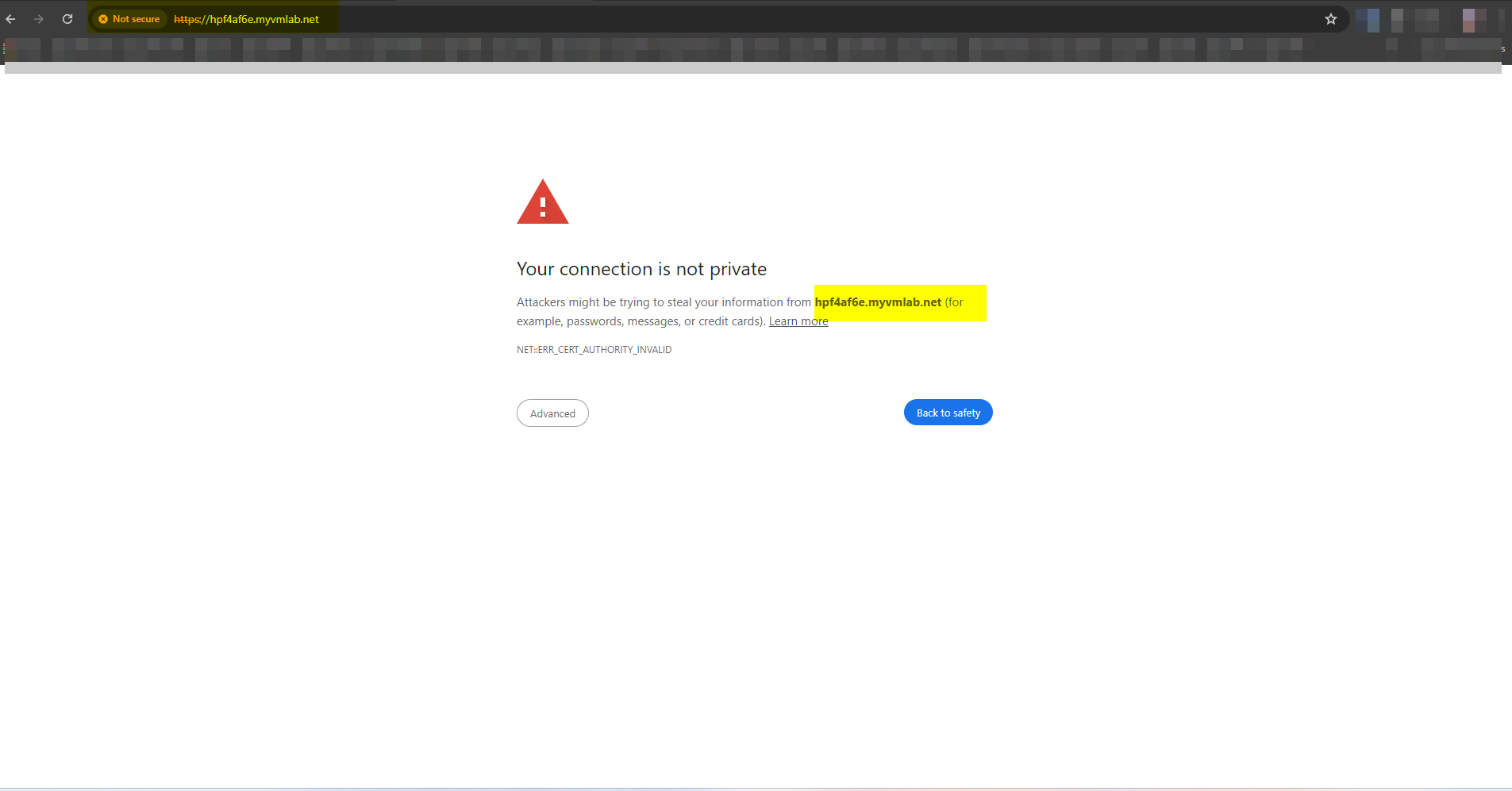
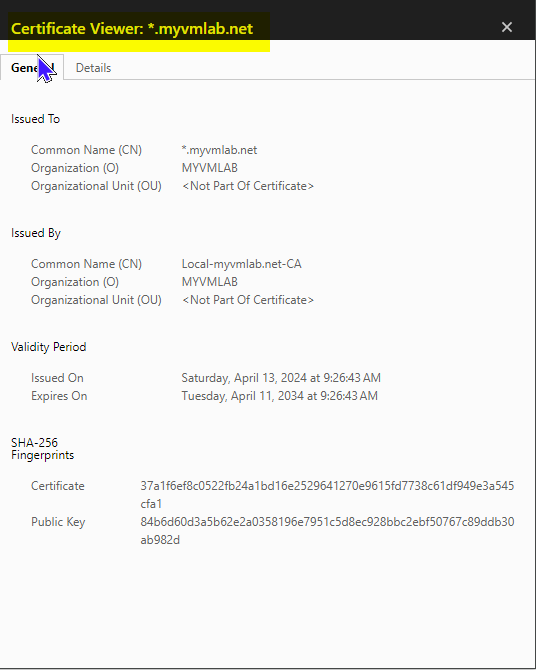
-
@VMlabman
So this is a self-signed certificate and the browsers will not trust it.
You can install the CA certificate in the browser to trust all certs issued by it. However, you have to do this on each unique browser, which you want to access HAproxy.In your initial post you wrote that you enable ACME. So my assumption was, that you got a Lets Encrypt certificate to use in HAproxy.
However, you will need a real public domain name to do this.My suggestion with the local CA was to secure the traffic inside your network. As I wrote above, you can issue (long validity period) certificates from it and install it on your backend devices. So HAproxy can access the backend servers via HTTPS, and will trust the certs, since they issued from a CA on pfSense itself.
-
I am going to go with your suggestion and use HAProxy and pfSence CA's for the few devices. So that is my goal here a Printer and a NAS. I takeing it alittle bit at a time this go at it.
-
Create CA Root in pfSense
-
Create CA Intermediate in PfSense
-
Create / Sign / Export Devise Certs
-
Get Certs onto Devices
-
HAProxy Basic Setup
Thank you,
-
-
Question when I am creation a Certificate Request from the device and filling in the Common Name Field. Is is case sensitive and is it the FQDN or just the HIOSTNAME?
Thank you,

-
@VMlabman
The common name has to be the FQDN. -
thanks
-
@VMlabman
When you enter the FQDN into the browser with "https://" in front of it, the browser expects to get a certificate from the server, in which the common name matches the entered / requested host name (FQDN) in the address line.
If they don't match the browser will not load the website. -
Thank you so much for everything. I actually got it working thanks to a lot of your help. It is now successfully working on my printer. Also, in the Certificates I realized everything was case sensitive.
Once again, thank you for the education and all your time and effort definitely appreciated
-
@VMlabman
Glad that you got it working as desired finally. -
Another question re this same project. Does HAProxy support self signed Certificates? If so anything special I need to keep in mind when creating it? The NAS can’t do a CSR. I am having issues adding the my QNAP NAS to HAProxy. Yet, I know HAProxy is working on my printer so I am just adding a new backend and adding it the the same frontend. Other then the NAS is on port 5553 os easy change on that part in the Backend.
Thanks you,

-
@VMlabman said in PfSense HAProxy certificate export import:
Does HAProxy support self signed Certificates?
Yes, if you have "SSL checks" unchecked.
The NAS can’t do a CSR.
Does it also not support the import of a certificate?
If you generate the certificate from a CA on pfSense, HAproxy should trust it anyway.
-
However, if I uncheck the SSL box and AJ proxy, does that make the connection between AA proxy and the Cell science certificate unencrypted
-
@VMlabman
If you enable the encryption in the backend, HAproxy requires an SSL certificate from the backend server to connect and the traffic is then encrypted based on this cert, whether it's validated or not.