DNS and ISP provider
-
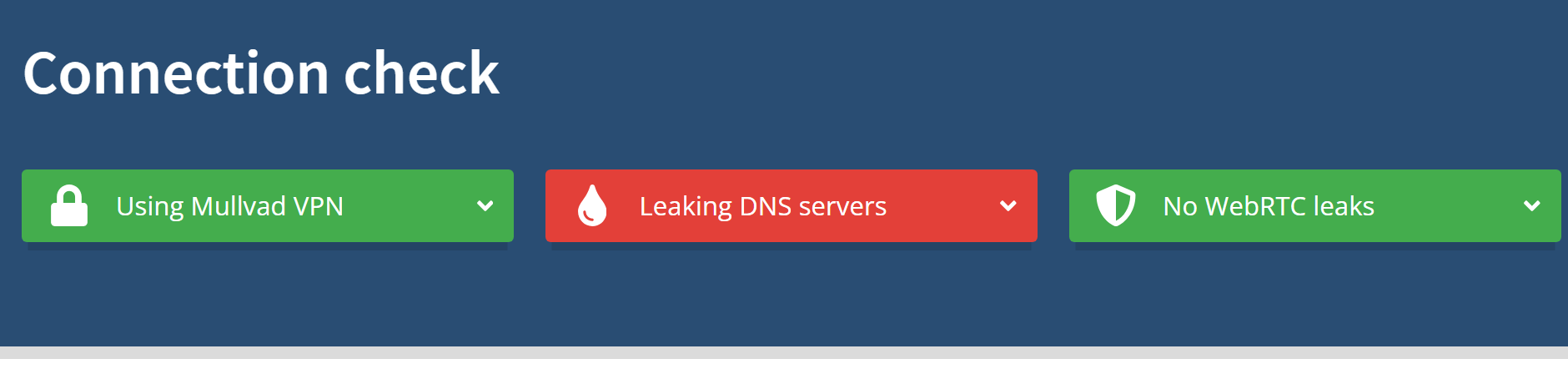
Are you using a VPN?
-
This interface yes but still have dns leakage, but if even use interface on LAN this ISP to able block or censuuring requests
-
@Antibiotic said in DNS and ISP provider:
If set to dns forwarding can reach this sites.
How did you configure this?
-
@The-Party-of-Hell-No resolves fine here
$ dig www.mk.ru ; <<>> DiG 9.16.50 <<>> www.mk.ru ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 36767 ;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;www.mk.ru. IN A ;; ANSWER SECTION: www.mk.ru. 3600 IN CNAME mk.ru. mk.ru. 3600 IN A 85.193.70.146 ;; Query time: 414 msec ;; SERVER: 192.168.3.10#53(192.168.3.10) ;; WHEN: Mon May 06 17:10:04 Central Daylight Time 2024 ;; MSG SIZE rcvd: 68Does it actually resolve? do a dig on pfsense for that fqdn, does it resolve, do a dig or nslookup or host or doggo whatever your fav tool is does it resolve?
If not resolving on pfsense dig, add +trace to see where it fails.. if your sending yoru dns out through your vpn there has been multiple threads about where vpn was intercepting dns..
Even if you can resolve it - if your sending your traffic out a vpn there are many sites that block many of the well known vpn IP ranges.
If you do a dig @1.2.3.4 www.netgate.com and get an answer your dns is being intercepted.. 1.2.3.4 does not provide dns service, if you get an answer asking 1.2.3.4 then your dns was intercepted.
-
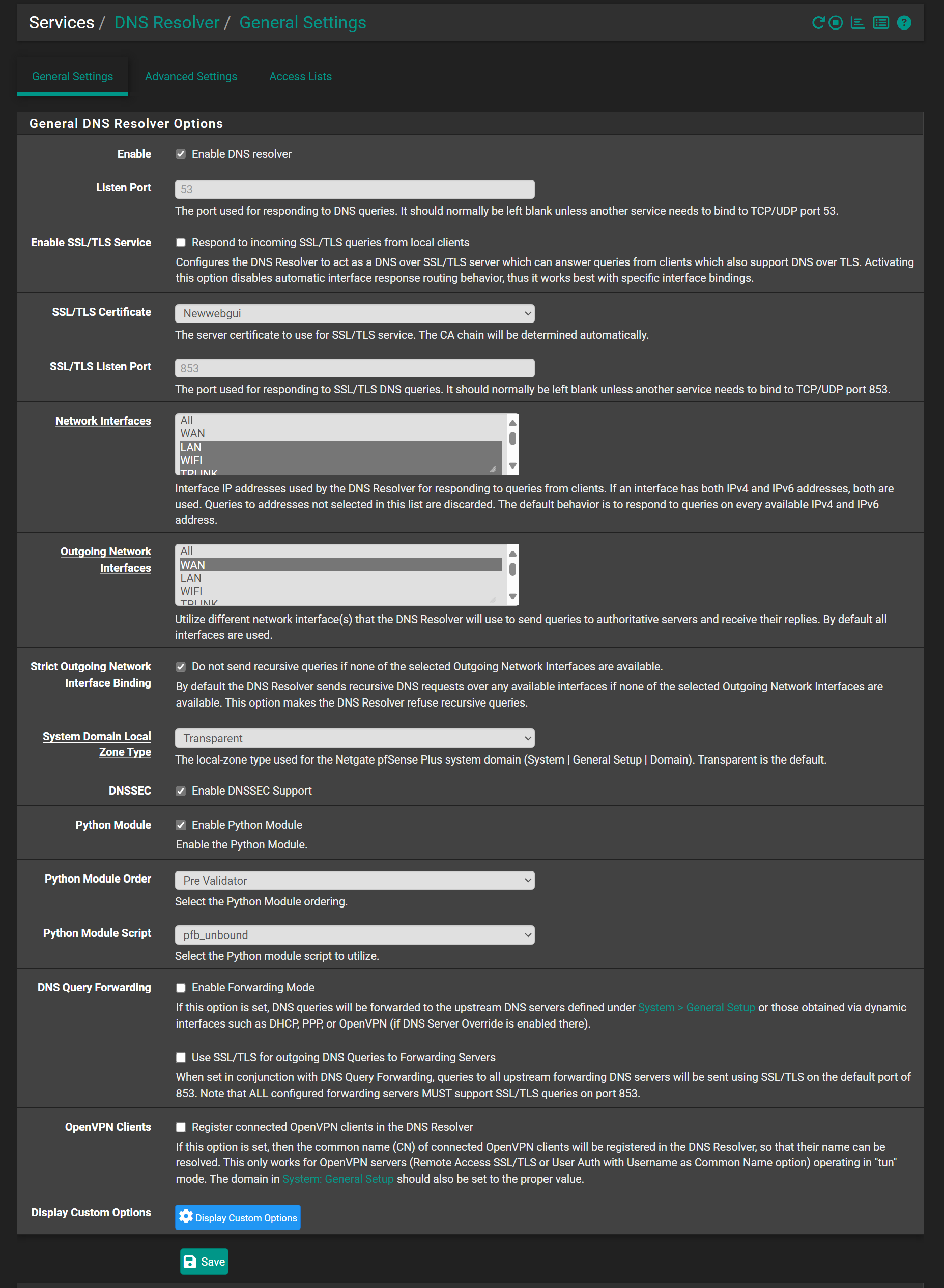
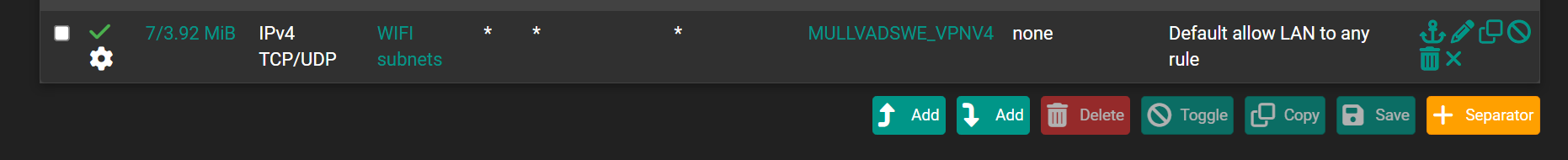
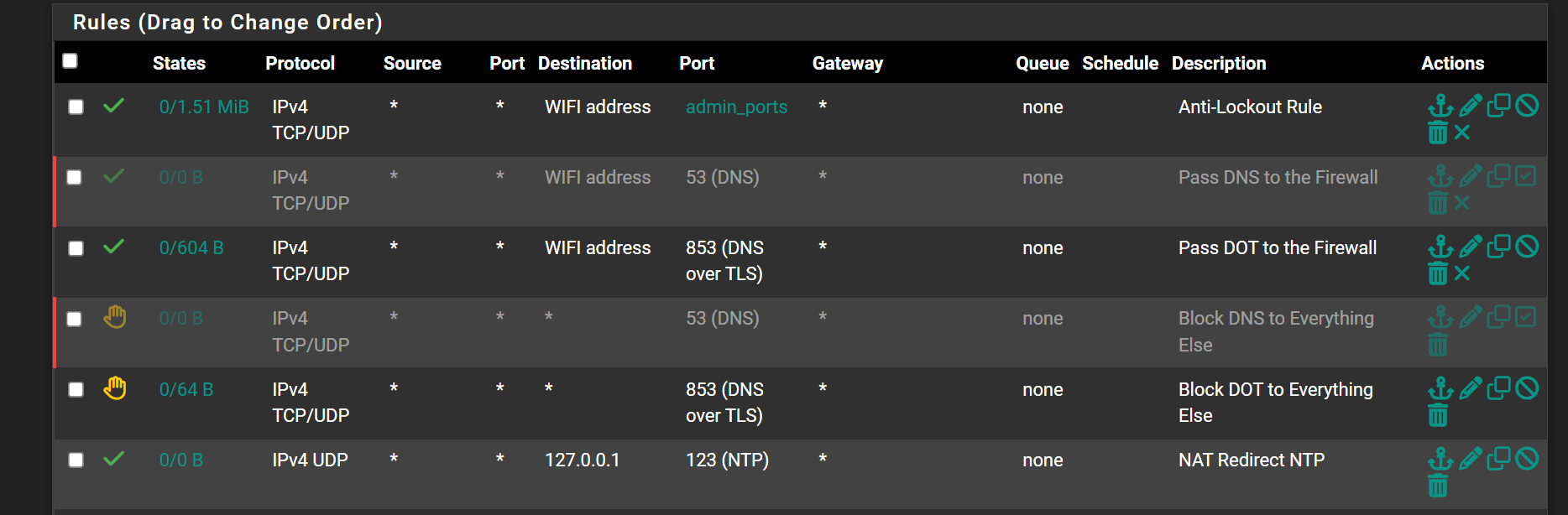
@viragomann Unbound forwarding, not dnsmasq forward and everything open
-
@johnpoz No, its ISP doing censuring. If just replace DNS going open. I trying to understand how they are doing this, if me do not use them DNS
-
@Antibiotic
DNS over TLS? -
@viragomann Please check image above
-
@Antibiotic
Nothing there, but since you removed the settings, I don't know from there. -
-
-
@Antibiotic
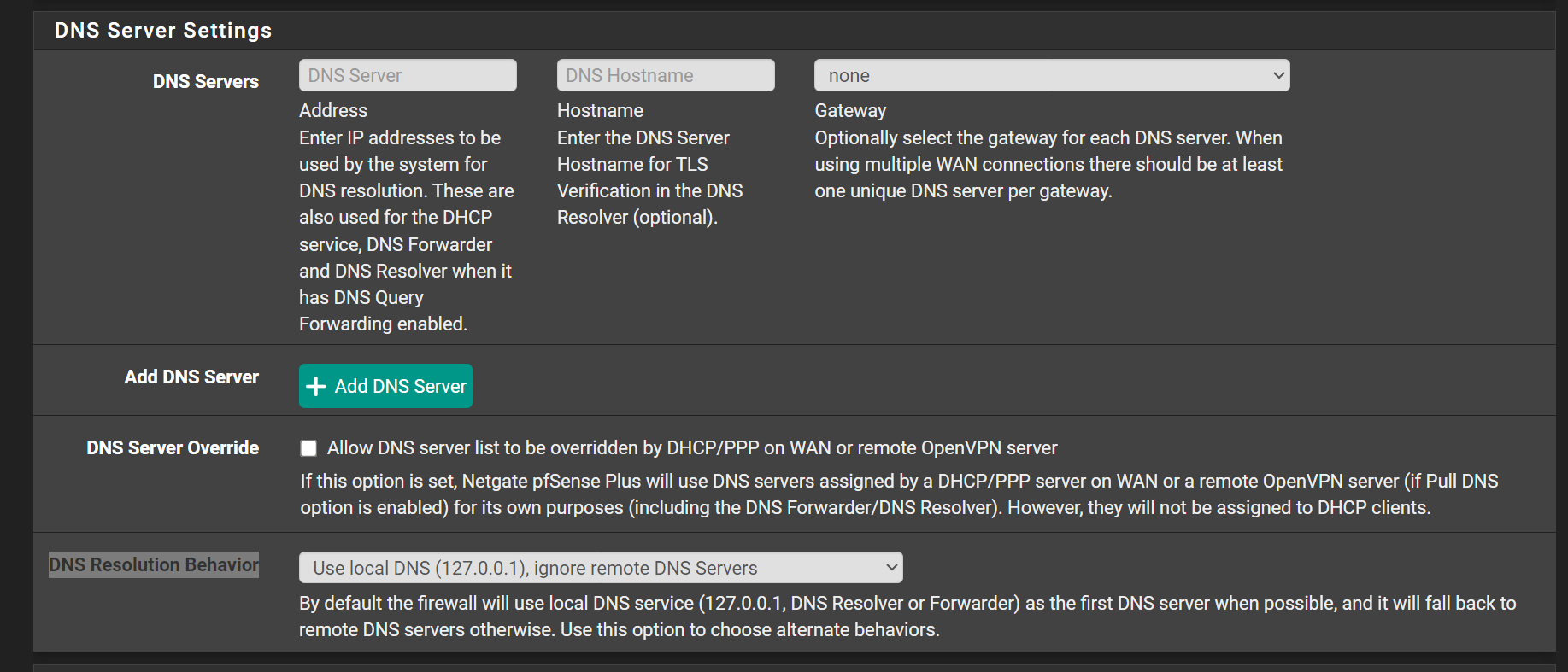
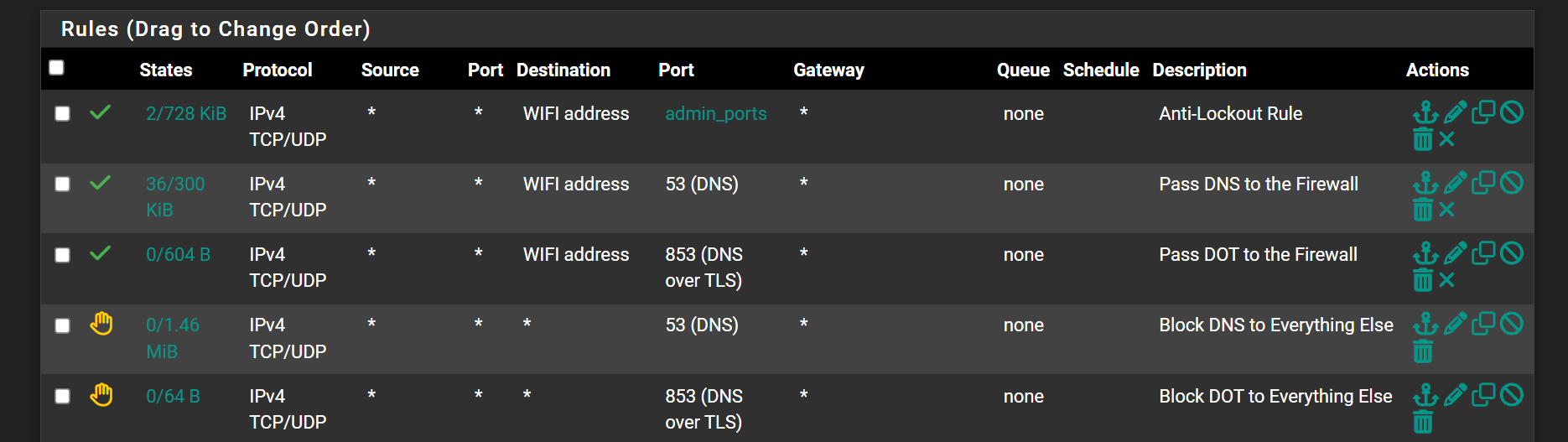
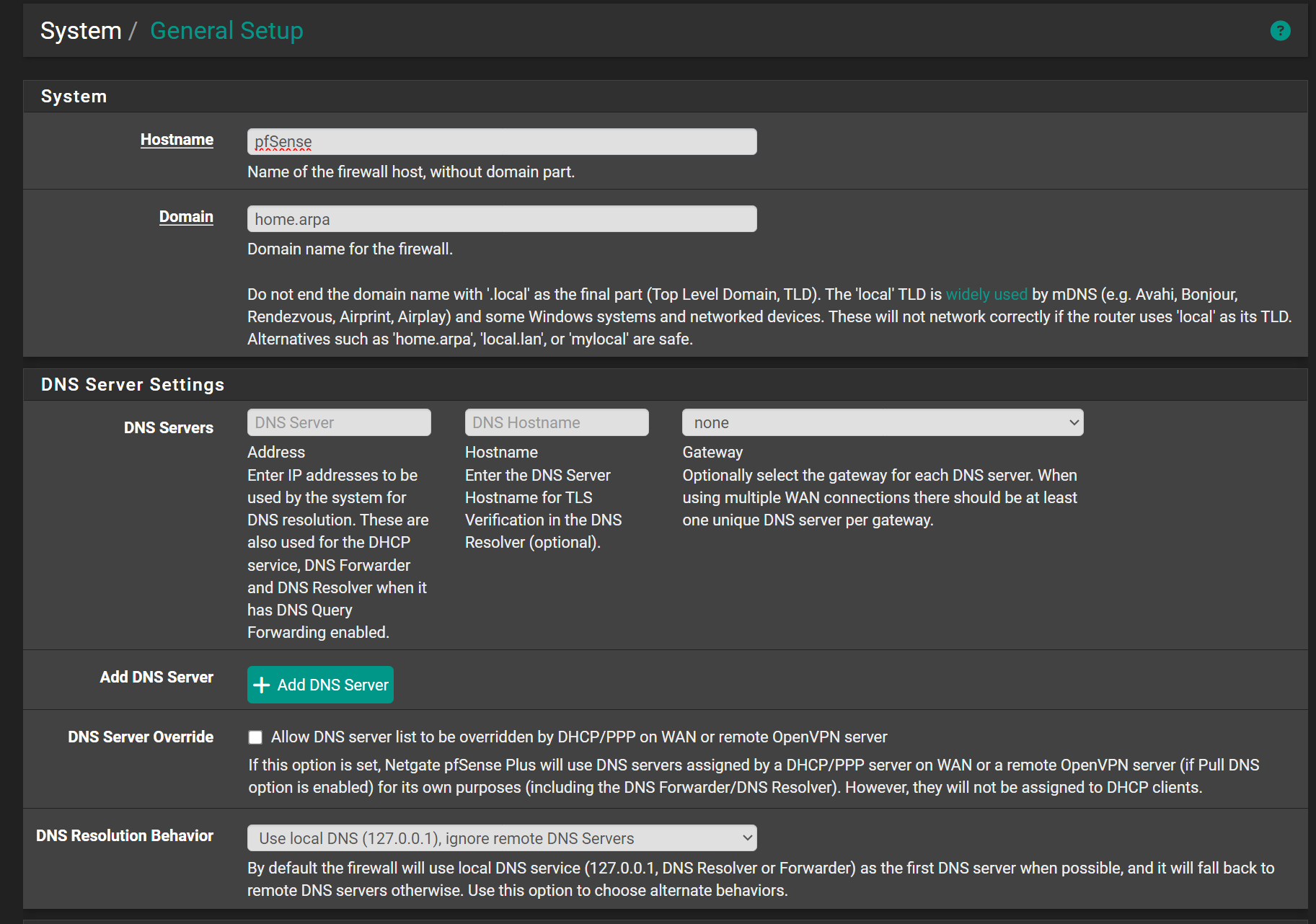
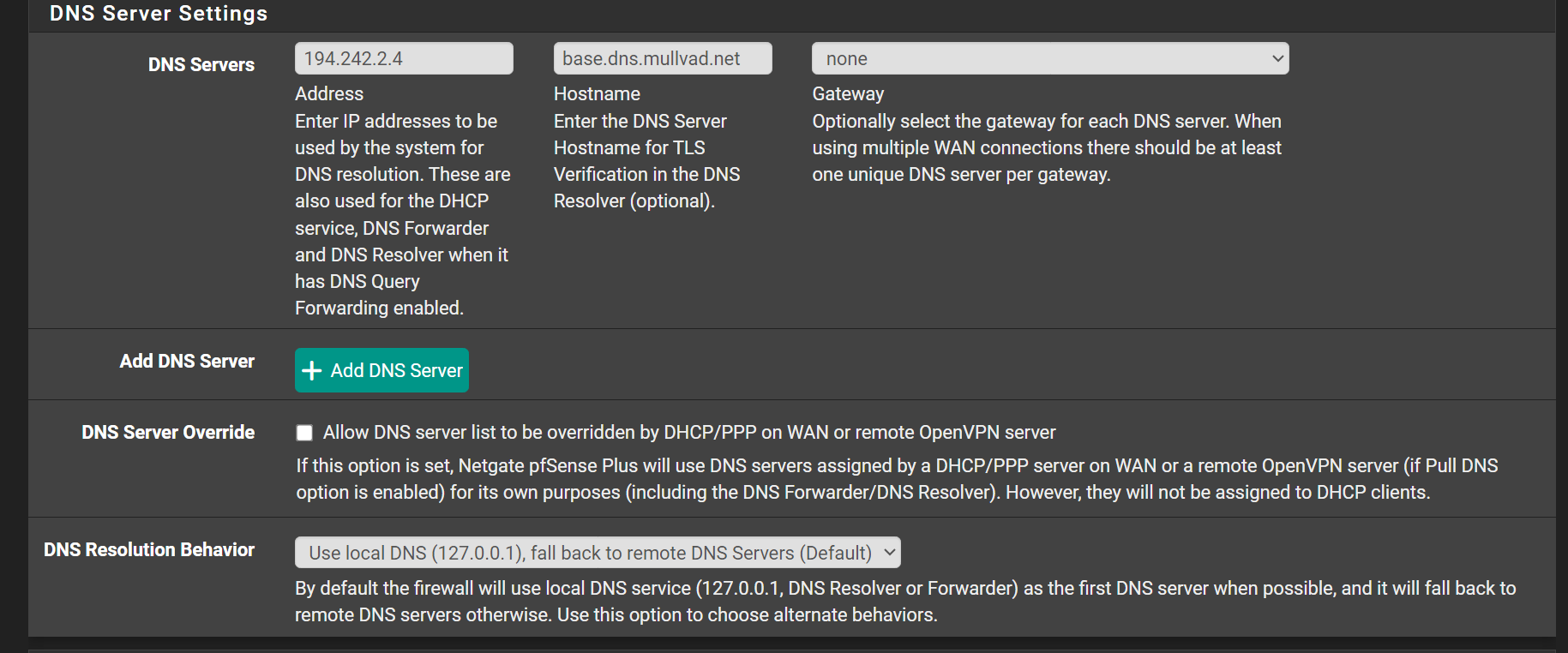
If you are using a vpn you have to use the vpn gateways and not the WAN in forwarding so local DNS server will go out the VPN Gateways not the WAN and there will be no DNS leak.
Also in general setup usually you enter the DNS servers provided by Mullvad. I also select the gateways they will go out. Also in general settings use the default DNS Resolution Behavior. -
@The-Party-of-Hell-No Sorry I do not use forwarding
-
-
-
@Antibiotic
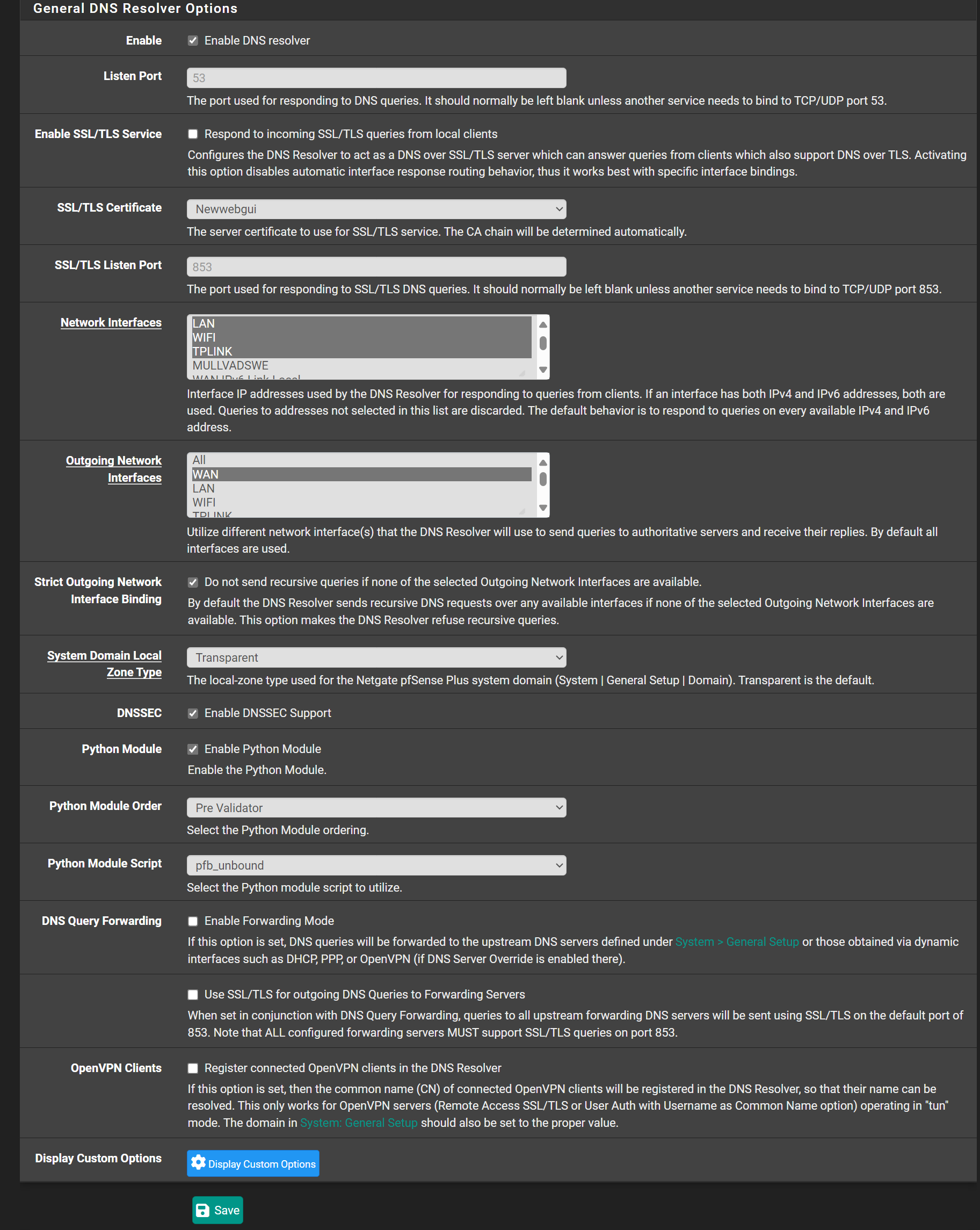
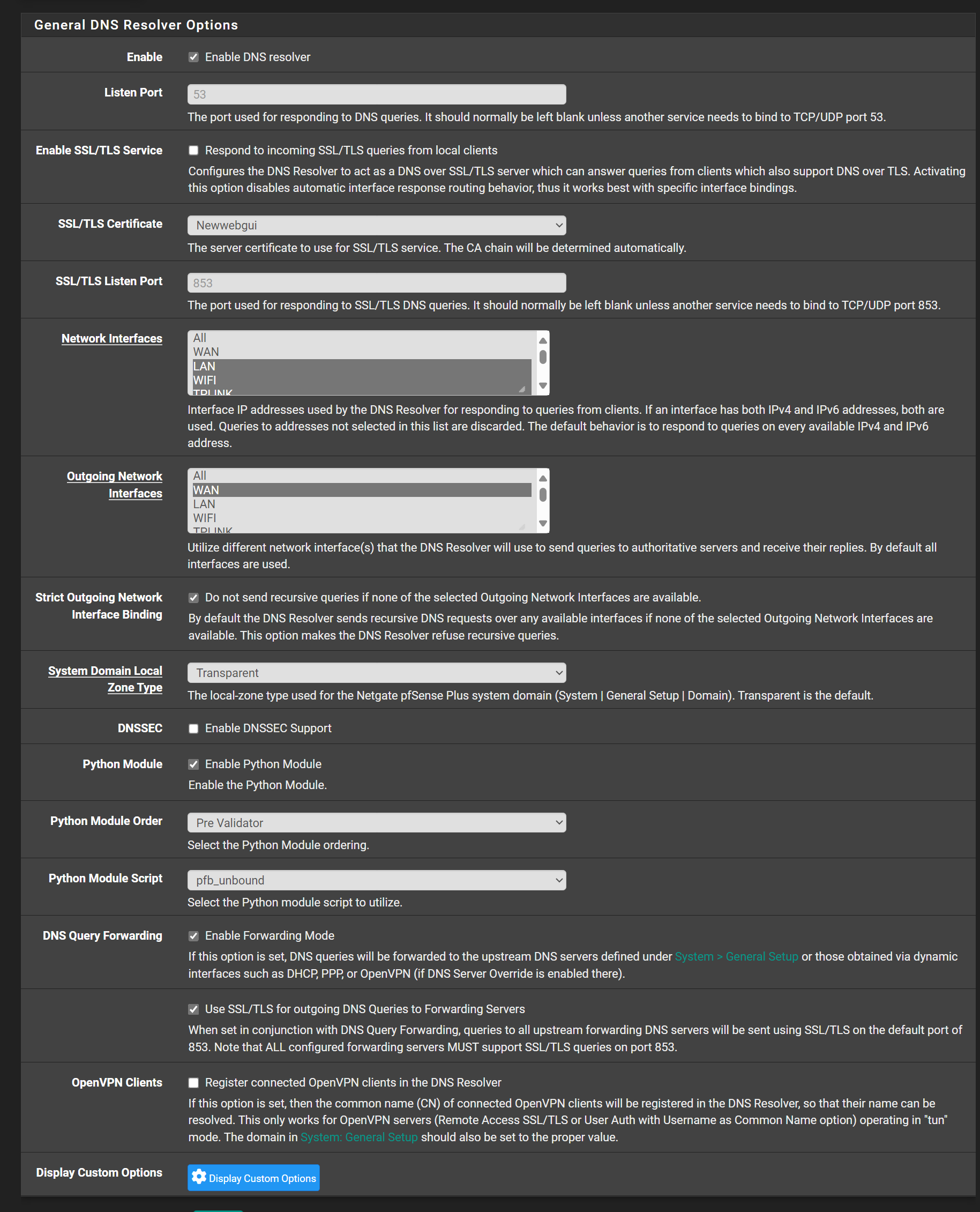
In my use of vpn services they all require forwarding, be turned on - as in turning on forwarding in the DNS resolver - there is a checkbox. In the outgoing interfaces, if you are running a vpn like Mullvad you should only highlight the vpn gateways and the local dns server. if the WAN is checked this will cause the dns leakage because your isp will see your dns requests. you want the dns requests to go out through the encrypted VPN tunnel. -
@Antibiotic
Without stating a DNS server in the general setup, you cannot enable DNS forwarding.Anyway, I saw a thread here, where an ISP blocked the DNS root servers.
Also the ISP can redirect DNS request to any server he wants, as long as you do not DNS over TLS upstream requests.
You can try this, however.Search for DoT servers and enter some into the general settings with their host names.
The host names are essential to get sure, that you're connected to the correct server (verifying the SSL cert).In the DNS resolver you have to enable the query forwarding + SSL and disable DNSSEC.
-
@The-Party-of-Hell-No If set outgoing interface to lpcal and mullvad in dns resolver internet not working at all
-
@Antibiotic said in DNS and ISP provider:
trying to understand how they are doing this, if me do not use them DNS
because they most likely are intercepting.. Its not difficult, there is a guide on how to do it on pfsense.. Do you not think isp could do such a simple thing.
Quick test just do the dig test to 1.2.3.4, if you get an answer your dns is being intercepting
[23.09.1-RELEASE][admin@sg4860.home.arpa]/root: dig @1.2.3.4 www.cnn.com ;; communications error to 1.2.3.4#53: timed out ;; communications error to 1.2.3.4#53: timed out ;; communications error to 1.2.3.4#53: timed out ; <<>> DiG 9.18.16 <<>> @1.2.3.4 www.cnn.com ; (1 server found) ;; global options: +cmd ;; no servers could be reached [23.09.1-RELEASE][admin@sg4860.home.arpa]/root:If you get a response your being intercepted, there multiple other ways to check, maybe they only intercept specific dns? etc.. but if you get an answer to that query its a smoking gun that upstream of where you doing the query from interception of dns is happening.
-