Crash report!!!!
-
@stephenw10 said in Crash report!!!!:
further so steps to reproduce would help a lot
Steps , what I did
Untick all offloads (Limiters were already) , than switch off back all offloads get first crash. After reboot changed some settings in Limiters as above in my post, get second crash. Next step remove Limiters and waiting now third crash. -
And just resaving the Limiters again did not reproduce the crash?
-
@stephenw10 Sorry, already removed Limiters and making state resetting's
-
@stephenw10 said in Crash report!!!!:
Hmm, backtrace is unusually long
It's a routing loop. The OpenVPN traffic is being routing into the OpenVPN tunnel. Sooner or later we run out of stack and crash.
It's a bug in if_ovpn that it doesn't discard this traffic, but it's also a configuration error. Once the bug is fixed the tunnel still won't work.
-
@kprovost said in Crash report!!!!:
but it's also a configuration error.
What do you mean, in my configuration error? Or OpenVPN have error itself?
-
@Antibiotic You've somehow configured your system so that the OpenVPN tunnelled traffic goes down the OpenVPN tunnel.
-
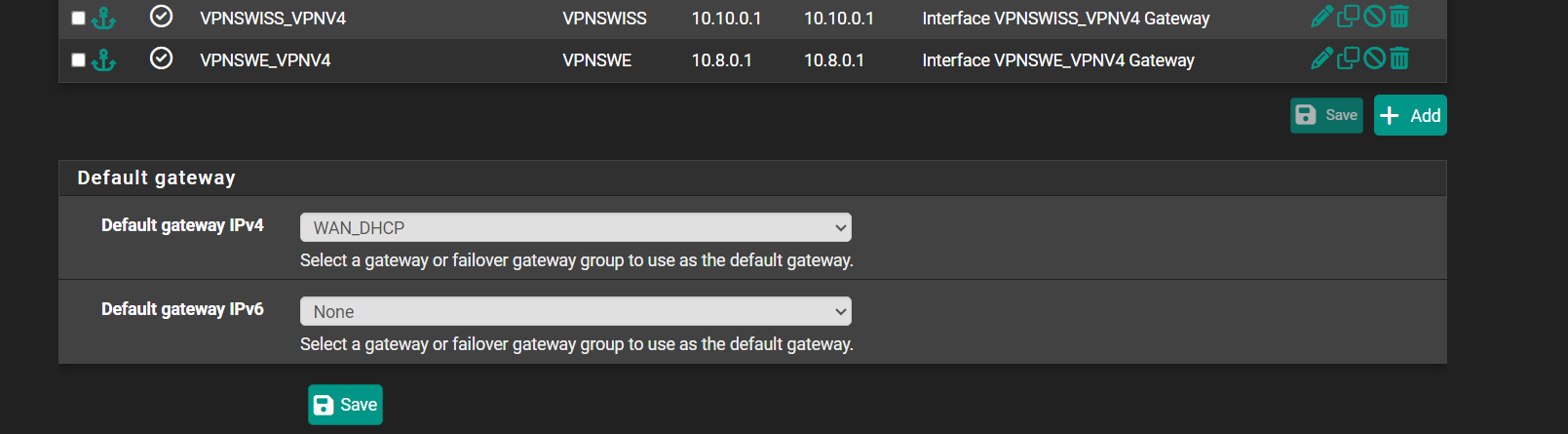
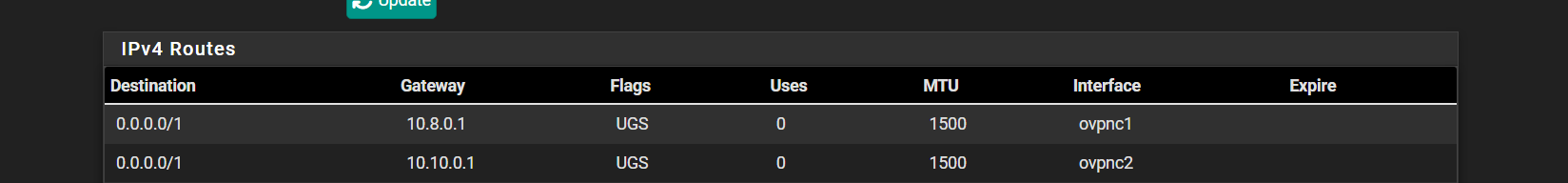
Check the routing table in Diag > Routes. Is your default route getting set to the OpenVPN gateway?
Make sure the system default gateway is set to the WAN gateway in Sys > Routing > Gateways.
-
-
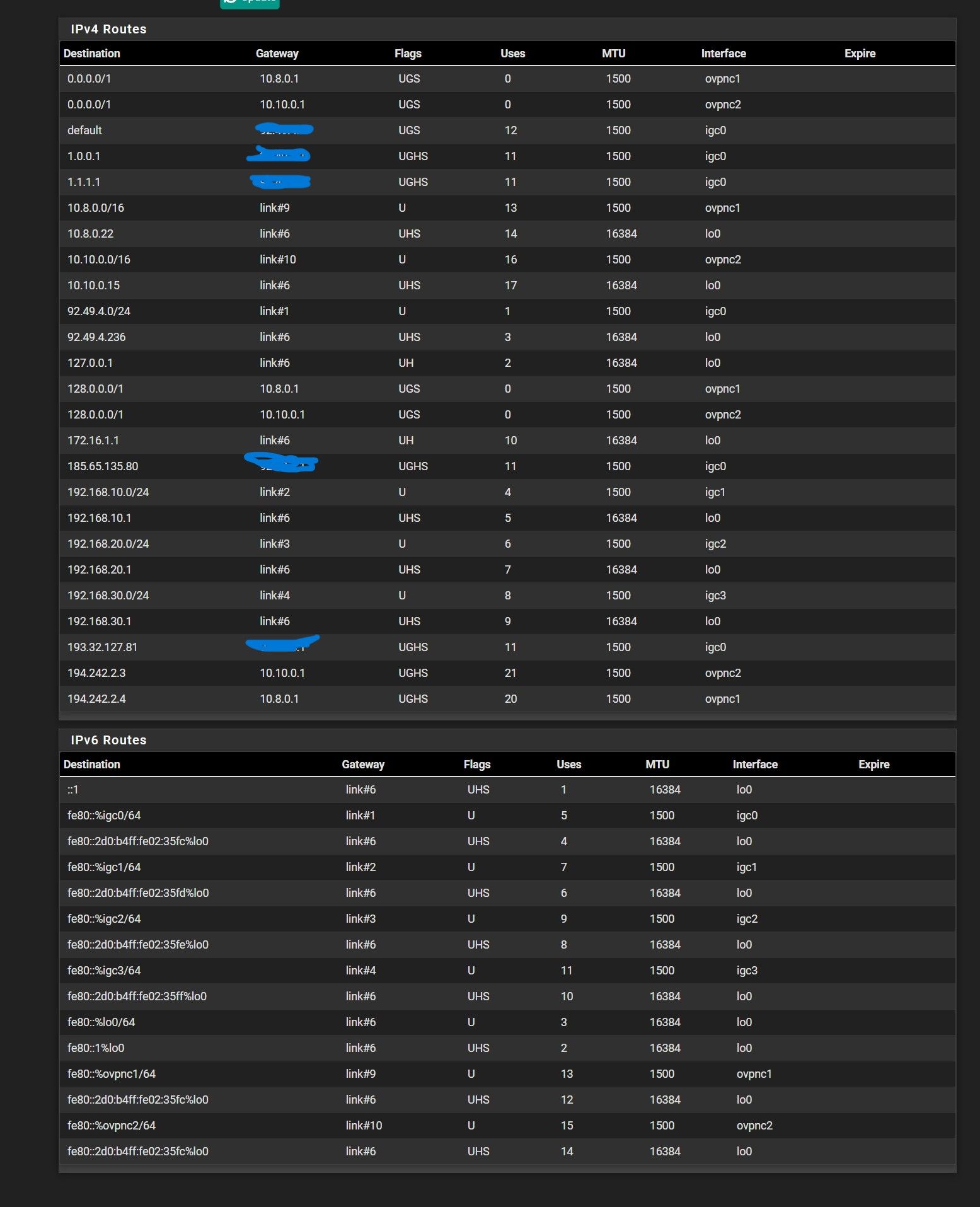
Hmm, seems like you don't have a default route there for some reason. Try resaving the system default gateway and then recheck the routing table.
-
-
Ok you should be good.
Do you see the OpenVPN server IPs there as static routes?
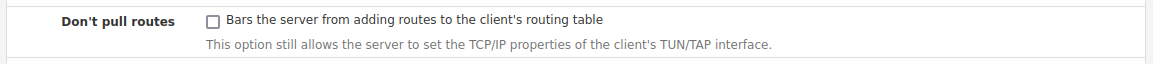
Those /1 routes you see there are being pushed to you by the VPN providers. I would disable those clients from accepting routes like that. You don't need that if you;re policy routing traffic across them.
-
@stephenw10 said in Crash report!!!!:
I would disable those clients from accepting routes like that
What do you mean, what better to disable?
-
In the OpenVPN client tunnel settings:
-
@stephenw10 Did , restart OpenVPN and resaving system defaultr gateway. Is it good now?
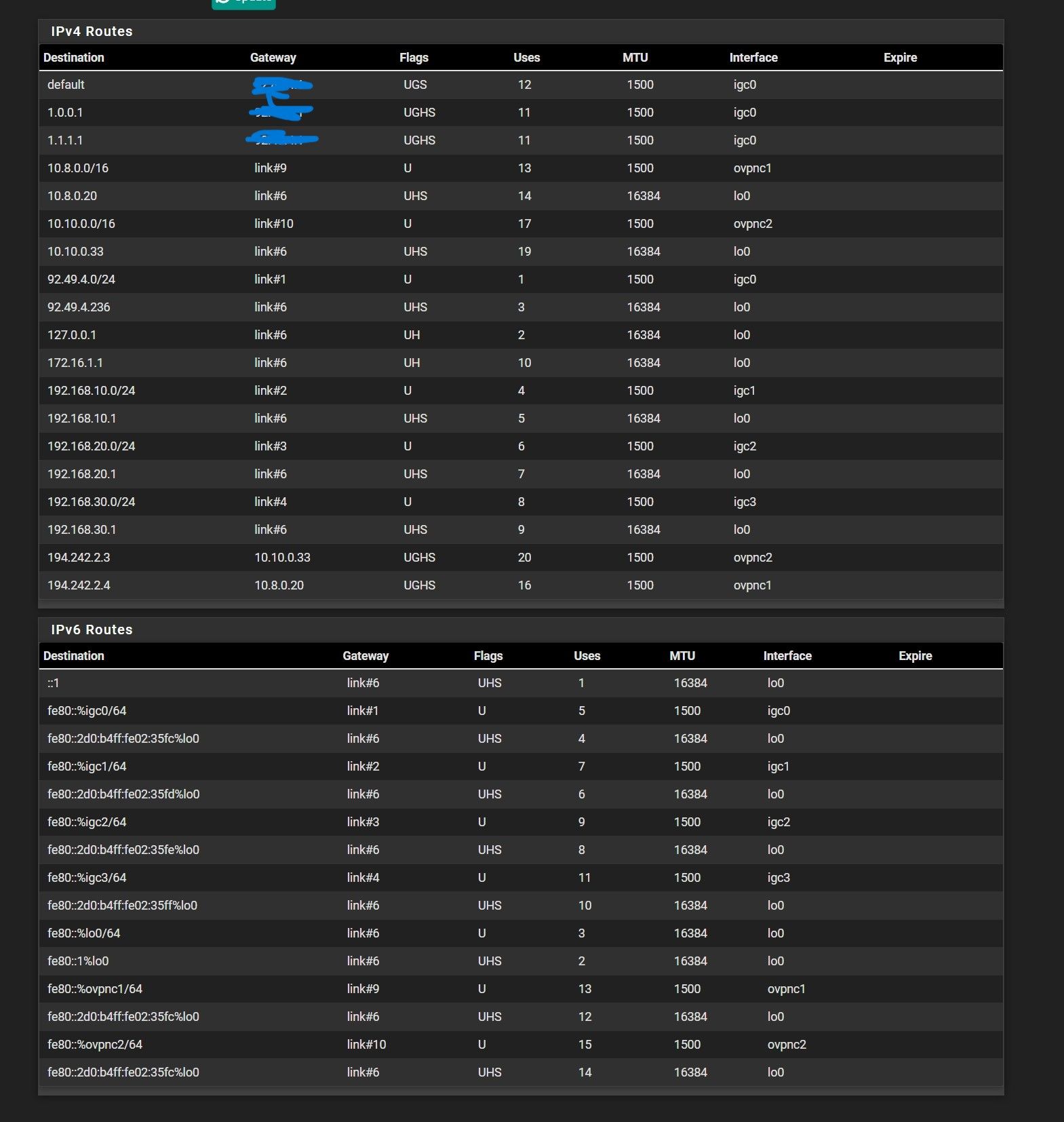
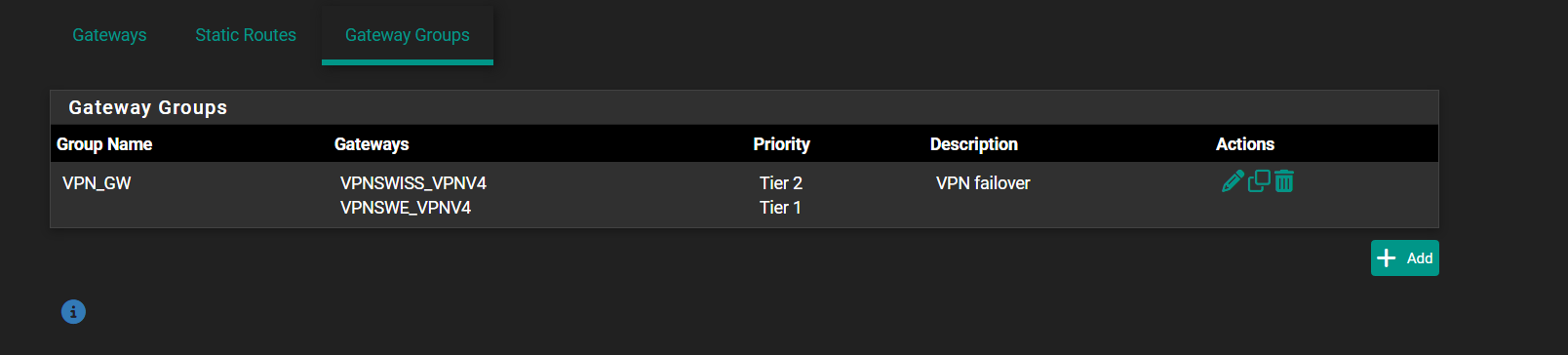
And second question , is it normally that I create 2 routes for one local address for VPN failover?Is it will work normally?
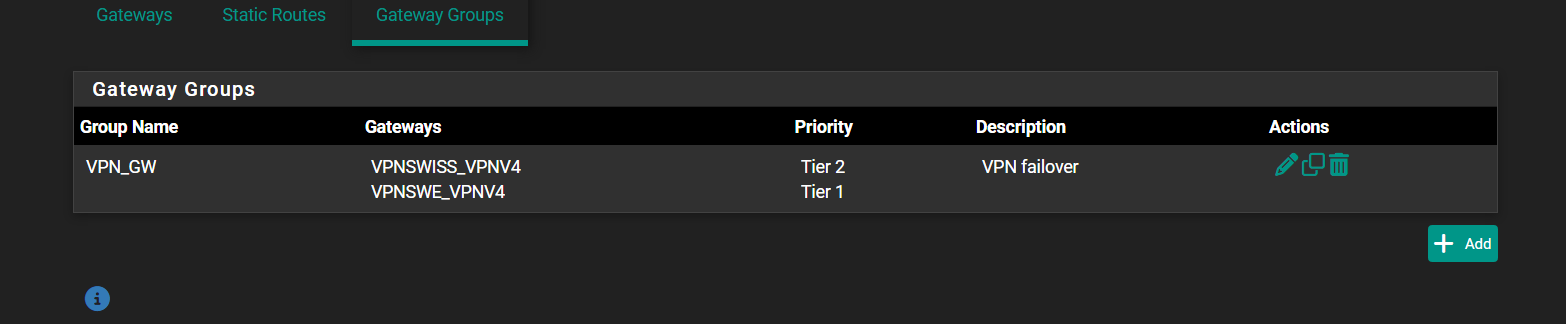
Local 192.168.20.0/24
-
That looks fine that should work.
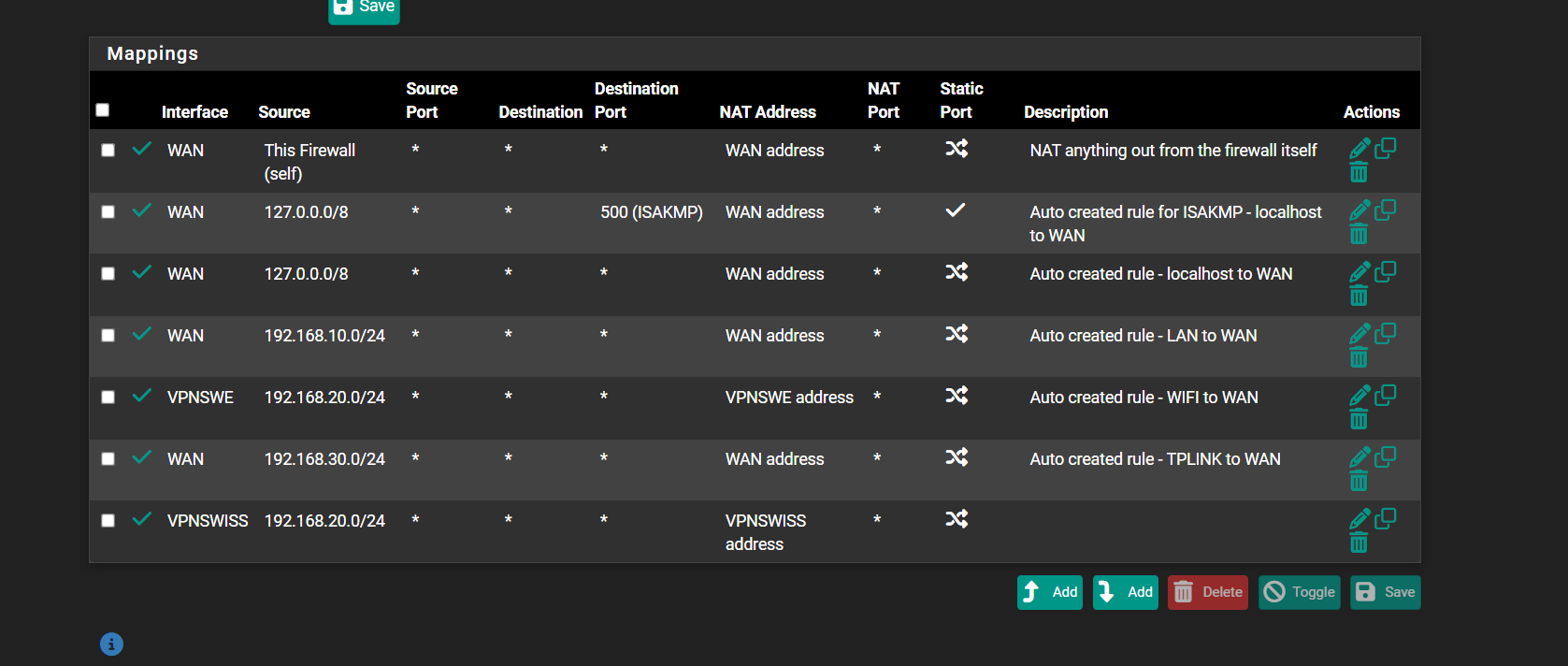
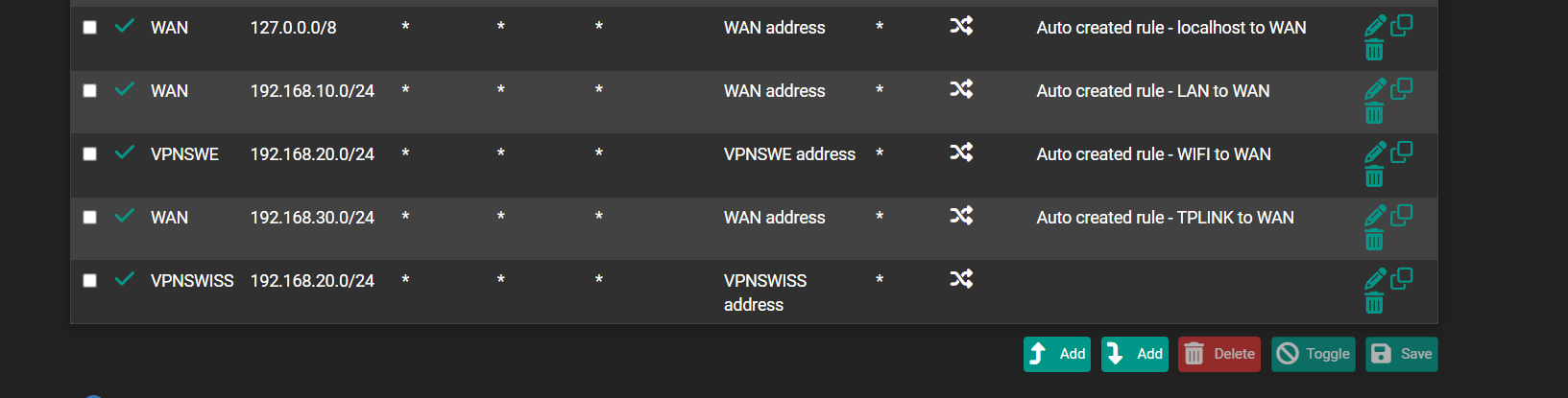
Do you mean two outbound NAT rules for the same source subnet?
Then, yes, you need outbound NAT on both VPN interfaces. -
@stephenw10 said in Crash report!!!!:
Do you mean two outbound NAT rules for the same source subnet?
Yes , in case of one VPN down to use second VPN. So, is this normal practice, settings in NAT are, OK ?for the same source subnet
-
Yes, those settings look correcy. You need to have OBN on both VPN connections. The OBN rules do not route or pass traffic, they only translate it.
-
@stephenw10 said in Crash report!!!!:
You need to have OBN on both VPN connections. The OBN rules do not route or pass traffic, they only translate it.
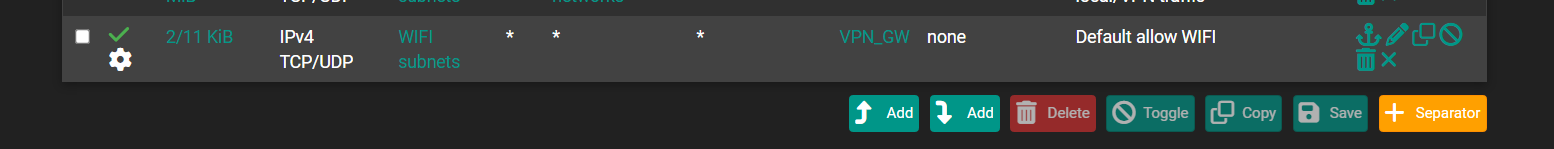
Oh . what it mean OBN. Can you please to show example??
-
OutBound Nat.
What you have there is correct.
-
@stephenw10 So, do not need any additional rules. All is fine with my settings now?