VPN -> LAN (OK) | LAN -> VPN (OFF) need both working
-
If the LAN host is pinging something in the 50.50.50.X subnet and it is using pfSense as it's default gateway that traffic will arrive at the LAN interface. So it will either be blocked or passed and open a state.
Try running a packet capture on the LAN filtered by the target IP (50.50.50.X) and then running the ping from the LAN host. If those pings don't arrive at the LAN then there is some routing issue on the LAN host.
-
CONFIG FOR LOGS:
LOGS:
10:50:20.318469 IP 192.168.140.3.445 > 50.50.50.2.54499: tcp 132 10:50:20.318544 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 750 10:50:20.318586 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 750 10:50:20.318657 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 750 10:50:20.318717 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 749 10:50:20.318793 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 766 10:50:20.320465 IP 50.50.50.2.50010 > 192.168.140.90.50001: UDP, length 72 10:50:20.323776 IP 192.168.140.90.50001 > 50.50.50.2.50010: UDP, length 51 10:50:20.324112 IP 50.50.50.2.52351 > 192.168.140.3.445: tcp 1 10:50:20.324316 IP 192.168.140.3.445 > 50.50.50.2.52351: tcp 0 10:50:20.341619 IP 50.50.50.2.50010 > 192.168.140.90.50001: UDP, length 73 10:50:20.343805 IP 192.168.140.90.50001 > 50.50.50.2.50010: UDP, length 48 10:50:20.347624 IP 50.50.50.2.54499 > 192.168.140.3.445: tcp 92 10:50:20.347697 IP 50.50.50.2.50010 > 192.168.140.90.50001: UDP, length 80 10:50:20.347853 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 767 10:50:20.347928 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 767 10:50:20.347929 IP 192.168.140.3.445 > 50.50.50.2.54499: tcp 128 10:50:20.354125 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1120 10:50:20.355054 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1120 10:50:20.356012 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1120 10:50:20.356996 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1120 10:50:20.357897 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1120 10:50:20.358843 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1120 10:50:20.359862 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1120 10:50:20.360770 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1120 10:50:20.361752 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1120 10:50:20.362722 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1120 10:50:20.363615 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1120 10:50:20.363803 IP 192.168.140.90.50001 > 50.50.50.2.50010: UDP, length 48 10:50:20.364059 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 104 10:50:20.364600 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1118 10:50:20.365594 IP 50.50.50.2.50020 > 192.168.140.90.50025: UDP, length 1134 10:50:20.366410 IP 50.50.50.2.50020 > 192.168.140.90.50025: UDP, length 1134 10:50:20.366494 IP 50.50.50.2.50010 > 192.168.140.90.50001: UDP, length 71 10:50:20.374943 IP 50.50.50.2.54499 > 192.168.140.3.445: tcp 136 10:50:20.375246 IP 192.168.140.3.445 > 50.50.50.2.54499: tcp 156 10:50:20.380252 IP 50.50.50.2.50010 > 192.168.140.90.50001: UDP, length 75 10:50:20.380740 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 742 10:50:20.380810 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 742 10:50:20.380871 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 742 10:50:20.380941 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 742 10:50:20.381000 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 742 10:50:20.381071 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 742 10:50:20.381131 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 742 10:50:20.381201 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 742 10:50:20.381260 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 742 10:50:20.381336 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 736 10:50:20.381399 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 758 10:50:20.383143 IP 192.168.140.90.50001 > 50.50.50.2.50010: UDP, length 51 10:50:20.398530 IP 50.50.50.2.53657 > 192.168.140.3.53: UDP, length 50 10:50:20.400254 IP 50.50.50.2.50010 > 192.168.140.90.50001: UDP, length 61 10:50:20.402203 IP 50.50.50.2.50020 > 192.168.140.90.50025: UDP, length 80 10:50:20.402585 IP 50.50.50.2.54499 > 192.168.140.3.445: tcp 108 10:50:20.402791 IP 192.168.140.3.445 > 50.50.50.2.54499: tcp 100 10:50:20.403809 IP 192.168.140.90.50001 > 50.50.50.2.50010: UDP, length 48 10:50:20.415028 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 743 10:50:20.415104 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 743 10:50:20.419528 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1162 10:50:20.420497 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1162 10:50:20.421476 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1162 10:50:20.422432 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1162 10:50:20.423124 IP 192.168.140.90.50001 > 50.50.50.2.50010: UDP, length 48 10:50:20.423410 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1162 10:50:20.424435 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1162 10:50:20.425411 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1162 10:50:20.426391 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1162 10:50:20.427365 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1162 10:50:20.428353 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1162 10:50:20.429330 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1162 10:50:20.429831 IP 50.50.50.2.54499 > 192.168.140.3.445: tcp 276 10:50:20.430068 IP 192.168.140.3.445 > 50.50.50.2.54499: tcp 84 10:50:20.430548 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1162 10:50:20.431225 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1162 10:50:20.432285 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1162 10:50:20.433288 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1162 10:50:20.434268 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1158 10:50:20.434278 IP 50.50.50.2.50010 > 192.168.140.90.50001: UDP, length 76 10:50:20.440307 IP 50.50.50.2.50010 > 192.168.140.90.50001: UDP, length 64 10:50:20.443141 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 771 10:50:20.443173 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 763 10:50:20.443244 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 763 10:50:20.443306 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 763 10:50:20.443379 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 763 10:50:20.443439 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 763 10:50:20.443512 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 763 10:50:20.443571 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 763 10:50:20.443644 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 763 10:50:20.443710 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 757 10:50:20.443781 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 779 10:50:20.443785 IP 192.168.140.90.50001 > 50.50.50.2.50010: UDP, length 51 10:50:20.457078 IP 50.50.50.2.54499 > 192.168.140.3.445: tcp 117 10:50:20.457394 IP 192.168.140.3.445 > 50.50.50.2.54499: tcp 200 10:50:20.460799 IP 50.50.50.2.50010 > 192.168.140.90.50001: UDP, length 60 10:50:20.463234 IP 192.168.140.90.50001 > 50.50.50.2.50010: UDP, length 48 10:50:20.477045 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 788 10:50:20.477115 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 788 10:50:20.480347 IP 50.50.50.2.50010 > 192.168.140.90.50001: UDP, length 62 10:50:20.483227 IP 192.168.140.90.50001 > 50.50.50.2.50010: UDP, length 48 10:50:20.484522 IP 50.50.50.2.54499 > 192.168.140.3.445: tcp 260 10:50:20.484758 IP 192.168.140.3.445 > 50.50.50.2.54499: tcp 84 10:50:20.488096 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1058 10:50:20.489003 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1058 10:50:20.489890 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1058 10:50:20.490847 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1058 10:50:20.491749 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1058 10:50:20.492651 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1058 10:50:20.493522 IP 50.50.50.2.50054 > 192.168.140.90.50049: UDP, length 1058 10:50:20.500071 IP 50.50.50.2.50010 > 192.168.140.90.50001: UDP, length 62 10:50:20.503213 IP 192.168.140.90.50001 > 50.50.50.2.50010: UDP, length 51 10:50:20.504777 IP 192.168.140.90.50049 > 50.50.50.2.50054: UDP, length 188 10:50:20.507329 IP 50.50.50.2.50635 > 192.168.140.3.53: UDP, length 32 10:50:20.511759 IP 50.50.50.2.54499 > 192.168.140.3.445: tcp 117 10:50:20.511931 IP 192.168.140.3.445 > 50.50.50.2.54499: tcp 132 10:50:20.518403 IP 50.50.50.2.50020 > 192.168.140.90.50025: UDP, length 1132 10:50:20.519377 IP 50.50.50.2.50020 > 192.168.140.90.50025: UDP, length 1132 10:50:20.520360 IP 50.50.50.2.50020 > 192.168.140.90.50025: UDP, length 1132 10:50:20.521351 IP 50.50.50.2.50020 > 192.168.140.90.50025: UDP, length 1132 10:50:20.521359 IP 50.50.50.2.50010 > 192.168.140.90.50001: UDP, length 58 10:50:20.523636 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 1003 10:50:20.523722 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 1003 10:50:20.523808 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 1003 10:50:20.523894 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 1003 10:50:20.523980 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 1003 10:50:20.524066 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 1003 10:50:20.524151 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 1003 10:50:20.524237 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 1003 10:50:20.524322 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 1003 10:50:20.524407 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 997 10:50:20.524502 IP 192.168.140.90.50025 > 50.50.50.2.50020: UDP, length 1019 10:50:20.524504 IP 192.168.140.90.50001 > 50.50.50.2.50010: UDP, length 48 -
OK so no ICMP packets at all there. But those were all inside 0.2 seconds so maybe it wasn't running long enough?
What IP address on LAN were you pinging from?
What we can see there though is that OpenVPN clients are able to connect to hosts on the LAN and they are able to reply. And importantly that there is no NAT. The OpenVPN tunnel IPs appear directly on the LAN.
-
@stephenw10 This test I showed you is from the packet capture of PFSENSE itself for the IP that my clientOPENVPN is getting 50.50.50.2
-
So you didn't try to ping from LAN host?
Repeat the capture but try to ping from a host on the LAN.
Pings from pfSense itself never go through the LAN interface to reach the VPN so would not appear in the pcap.
-
@stephenw10 It's in Portuguese, but it causes 100% packet loss
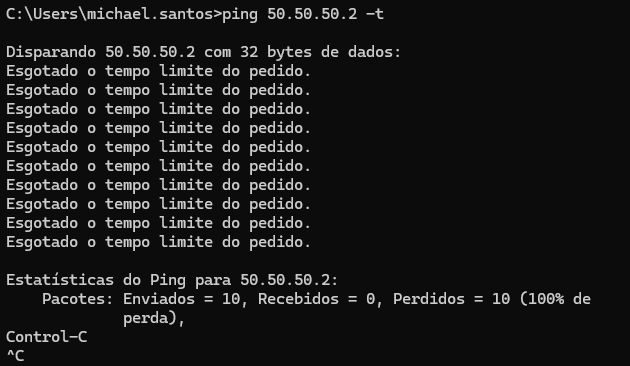
-
Ok and what does the packet capture show on LAN whilst that is running?
What IP address in the LAN are you pinging from?
What is 50.50.50.2 there? Another client device?
By the way 50.50.50.0/24 is a public subnet belonging to Frontier Communications. You should really use a private subnet for the tunnel.
Steve
-
@stephenw10 But packet capture where? in pfsense? You told me to use ping elsewhere, I don't understand
50.50.50.2 is another client device that
50.50.50.0/24 But the tunnel already uses a private subnet, doesn't it? -
You are saying that you need to be able to connect to OpenVPN clients from hosts in the LAN subnet and it is not working.
We are trying to find out why it's failing.
So to test that we are trying send ping traffic from a host in the LAN to a VPN client and then looking to see where it goes.
The first place it should hit is the pfSense LAN interface.
So the test is to start a packet capture on the pfSense LAN interface. Then run the ping and make sure it arrives there.
If it doesn't arrive then the issue is on the LAN host.
-
50.50.50.0/24 is a public subnet that should not be used here. BUT that is not the cause of the problem. It only means you could not connect to that subnet if you ever had to which is very unlikely.
-
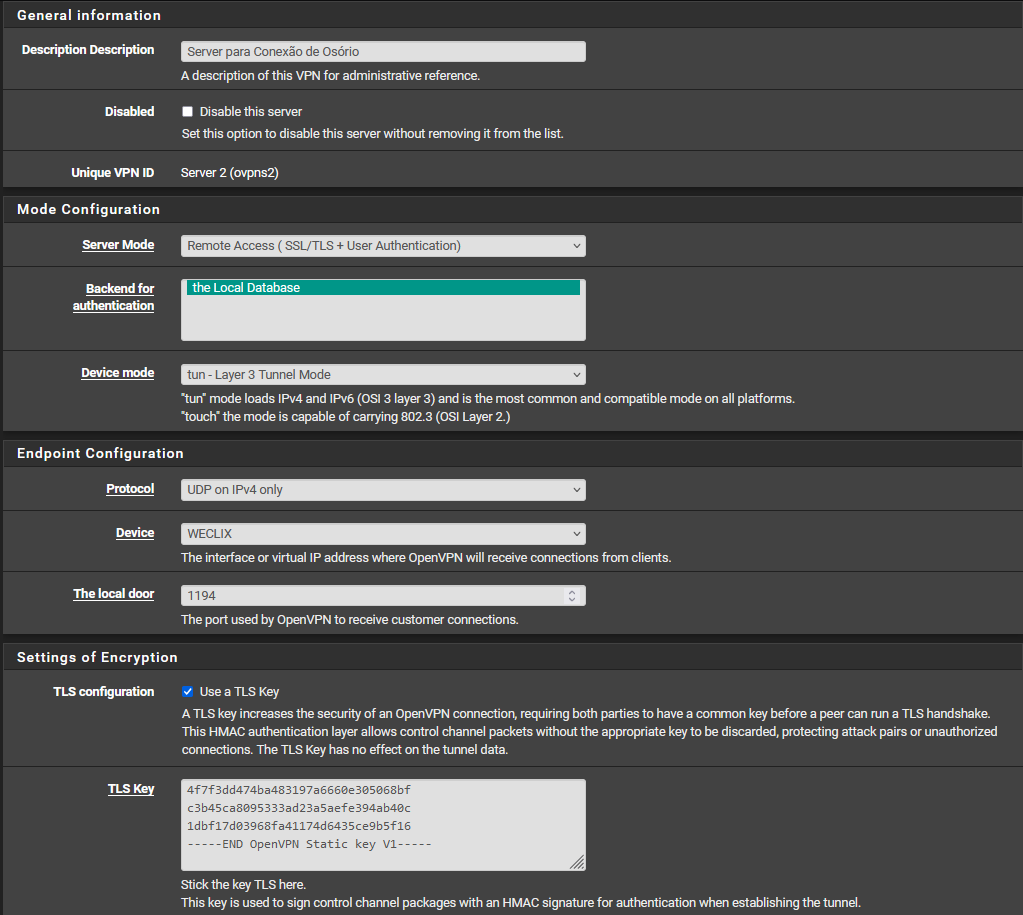
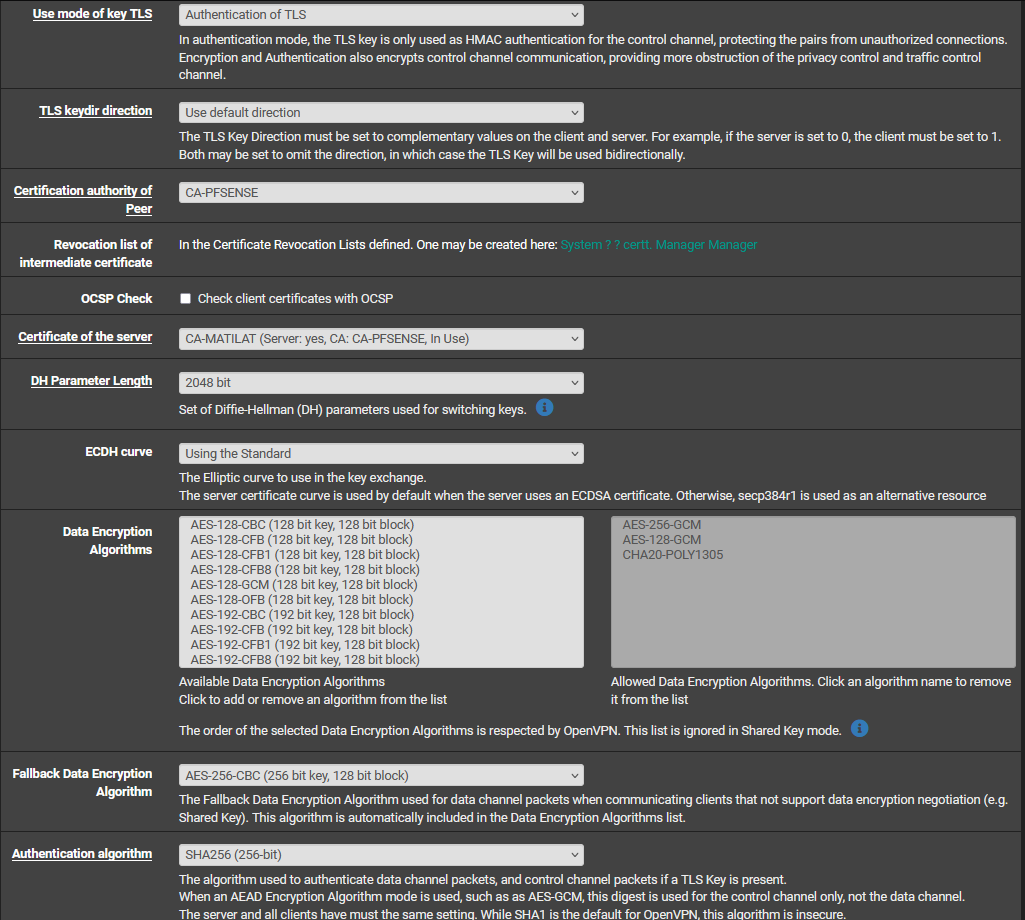
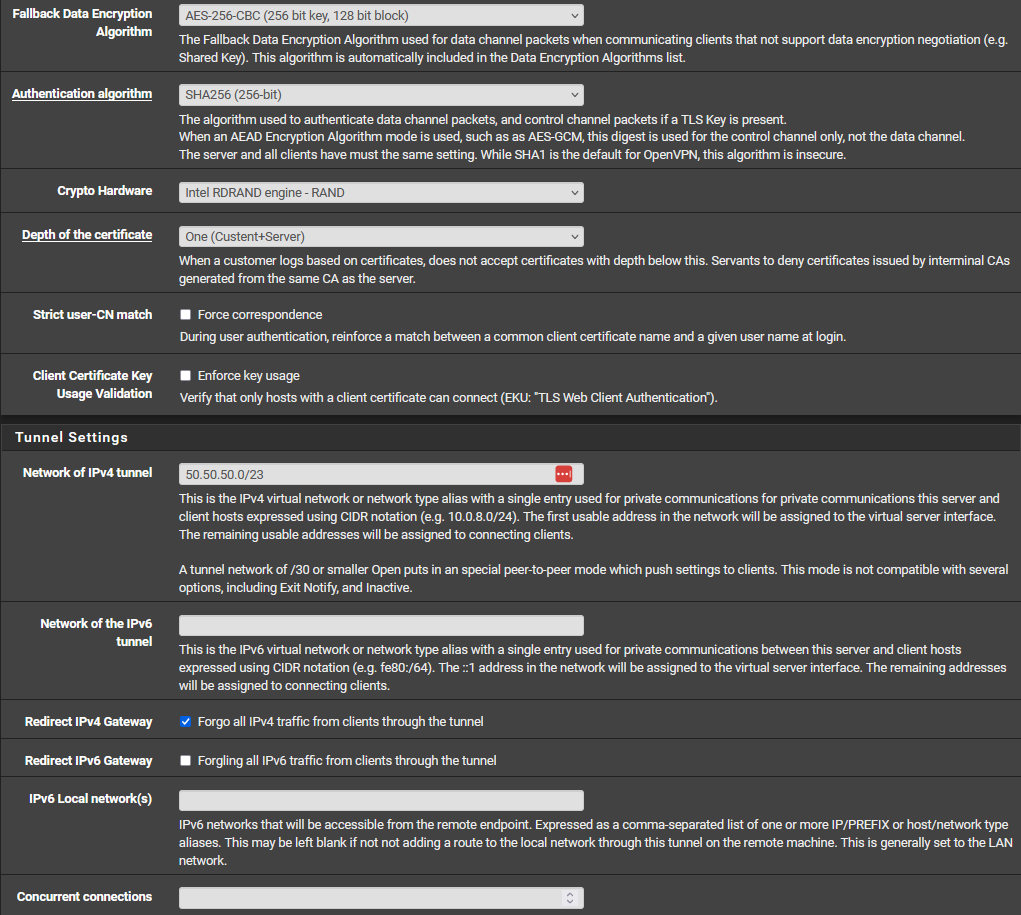
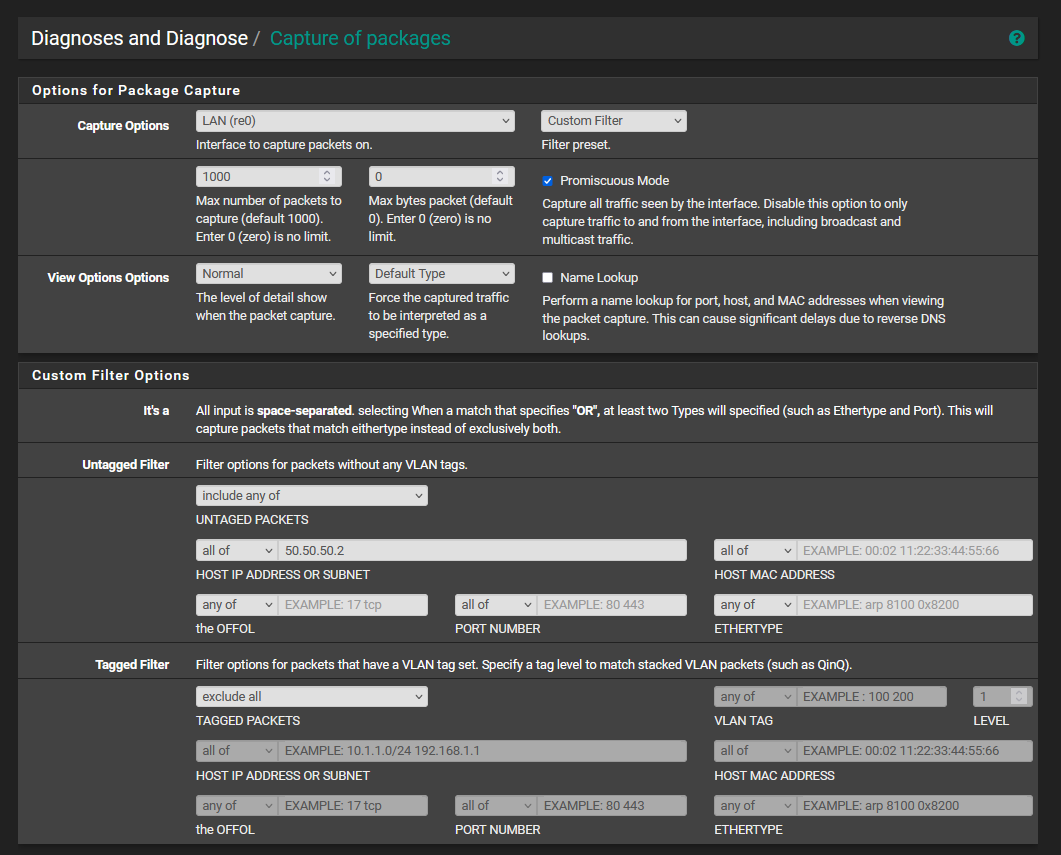
@stephenw10 I pinged directly from my machine to an OPENVPN client and captured the packets from my PFSENSE LAN interface, with these settings:
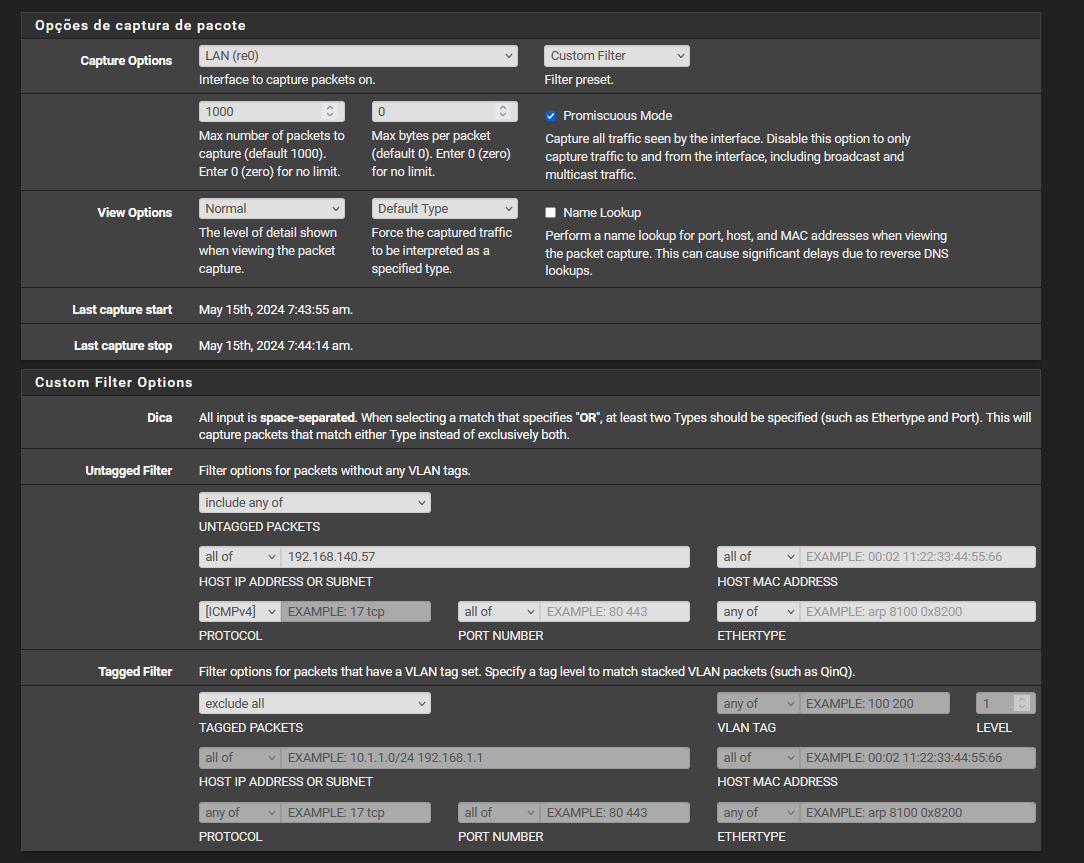
Try ping 50.50.50.2:
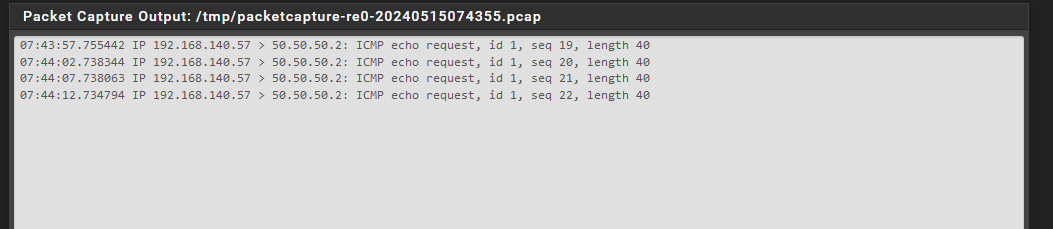
-
Ok great. So the ping packets are arriving in the correct place. The client is not responding so either it can't respond (it's blocking them) or it never sees the pings.
Next try running the packet capture on the openvpn interface to make sure the pings are leaving the correct way.
You can also check the state table while that ping is running so make sure pfSense is open states on the correct interfaces.
Can I assume that if you ping the other way, from 50.50.50.2 to 192.168.140.57, it works?
-
If I am capturing ICMP packets from my OpenVPN Server interface, the same log that I sent you appears.
Yes, if I try to ping ip 50.50.50.2 to 192.168.140.57 it works normally
-
Ok if you see the pings leaving the OpenVPN interface the packets are almost certainly being blocked at the VPN client. A local software firewall on 50.50.50.2.
-
@stephenw10 But what could this be blocking? my rules allow everything
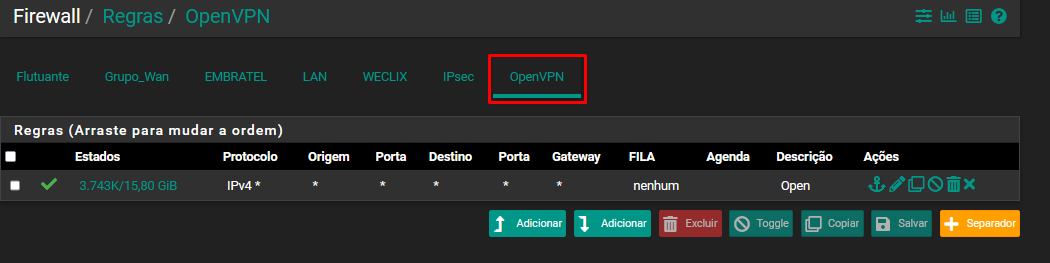
-
Its almost certainly blocked on the client device directly. So like Windows firewall, if it's a Windows device.