Plex through surfshark wireguard pfsense vpn
-
Did you follow a guide for adding the surshark VPN? Did it have you remove the auto outbound NAT rule to prevent 'leaks'?
-
You don't need to obscure that 10.x.x.x private IP address. I assume that's the Plex server?
-
@stephenw10 that's the plex server, I followed this guide here,
https://www.ivpn.net/setup/router/pfsense-wireguard/
there's also another guide, trying to find it.Found it. Forget what I said above it was definitely this guide I used:
PFsense how to surfshark and wireguard.zip -
Yup so that's exactly what it has you do:
https://www.ivpn.net/setup/router/pfsense-wireguard/#firewallYou'll need to add an outbound NAT rule for the Plex server IP to the WAN address on the WAN. Otherwise it not be translated and cannot connect out.
-
Like:

Assuming 10.0.5.2 is the Plex IP. I would probably add an alias for it and then use that everywhere so you can change it in one pace if you need to.
-
@stephenw10 can you guide me on what I need to do then? Please as I’m new to pfsense. And all I seem to be doing is messing it up. The ip I’m using is a temporary machine so when I get the pfsense to bypass the vpn for Plex I can put it on my main thanks again
-
Your WAN IP doesn't matter. The NAT rule only has to reference the source as the Plex server IP.
So add a rule like I showed above.
What outbound NAT rules do you have currently?
You could just switch Outbound NAT back to Auto or Hybrid and the rules will match the traffic from the Plex server.
As I said in those VPN guides they have you remove the auto outbound NAT rues to prevent traffic from internal subnet leaving via the WAN directly. Here you need that to happen.
-
-
OK so you need to add rule on WAN for the Plex server IP as I showed above.
As an aside you should add a source for the Tailscale rule you have there. Having outbound rules with 'any' source can easily over-match traffic that should not be NAT'd like traffic from the firewall itself.
-
@stephenw10 said in Plex through surfshark wireguard pfsense vpn:
Having outbound rules with 'any' source can easily over-match traffic that should not be NAT'd like traffic from the firewall itself.
Like traffic from the WAN-address will be NATed to the WAN-address? I see, one can not invert that.
-
Yup, exactly. We have seen that break VPN tunnels from the firewall itself because it also randomises the source port.
-
@stephenw10 Thanks. I guess I have to write a Feature request.
-
@stephenw10
So I don’t need to do anything with my NAT outbound rules?
I Tried creating a nat rule for Plex IP but it just defaults to 192.168.0.0 -
You need a add a rule like I showed in my example where the source is set to the Plex server IP address.
You could set the source to the full LAN subnet but I'm assuming you don't want any other LAN side hosts to be able to use the WAN directly.
-
@stephenw10 I did what you said but when I add my Plex server ip address for eg. (192.168.0.90) and I save it, it changes back to 192.168.0.0
-
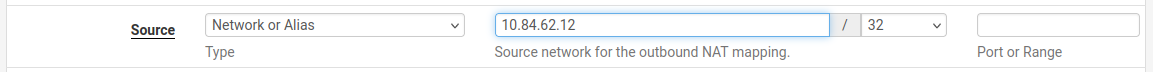
I assume your Plex server is actually 10.84.62.X?
What are you setting that keeps switching back to 0.0?
You should be setting the source like so:
-
@stephenw10 is there a way I can send a small vid on here to show you?
-
You can upload it here: https://nc.netgate.com/nextcloud/s/iRCYoGnH6KsMrXR
-
@stephenw10
Uploaded the video -
You have to set the subnet to /32 for a single host like in my screenshot above.
