Pfsense crashed - stuck on reboot
-
I’ll do my best to respond on my phone but pfsense appears stuck. This is a SG6100
-
I pulled the power to reset it. After coming back online the interface assignments are wrong. WAN was igc3 but now ix3. Seems to be an old config. I went in through the console to list all my backups and to my shock all 30 files are from today and seems to be the system adding interfaces , setting syslog…just random changes
Performing another reboot through cli and my vlans and even my LAN interface is gone… -
@michmoor
Im back online.
Super weird. Almost all my interfaces were gone, LAN/Wifi etc. The only ones that were available was my WAN and Wireguard Remote Access.
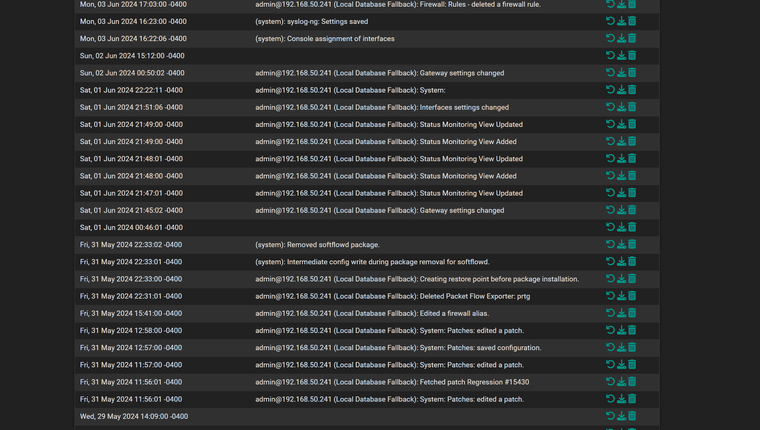
I hopped into VPN and was able to hit my pfsense. I go straight into my backup configurations and all 30 backups like it states in the GUI are all from today and from system.These are the interfaces that are showing up. Note that LAN is missing, igc2.14 and igc.23 is missing which are the main wlans.
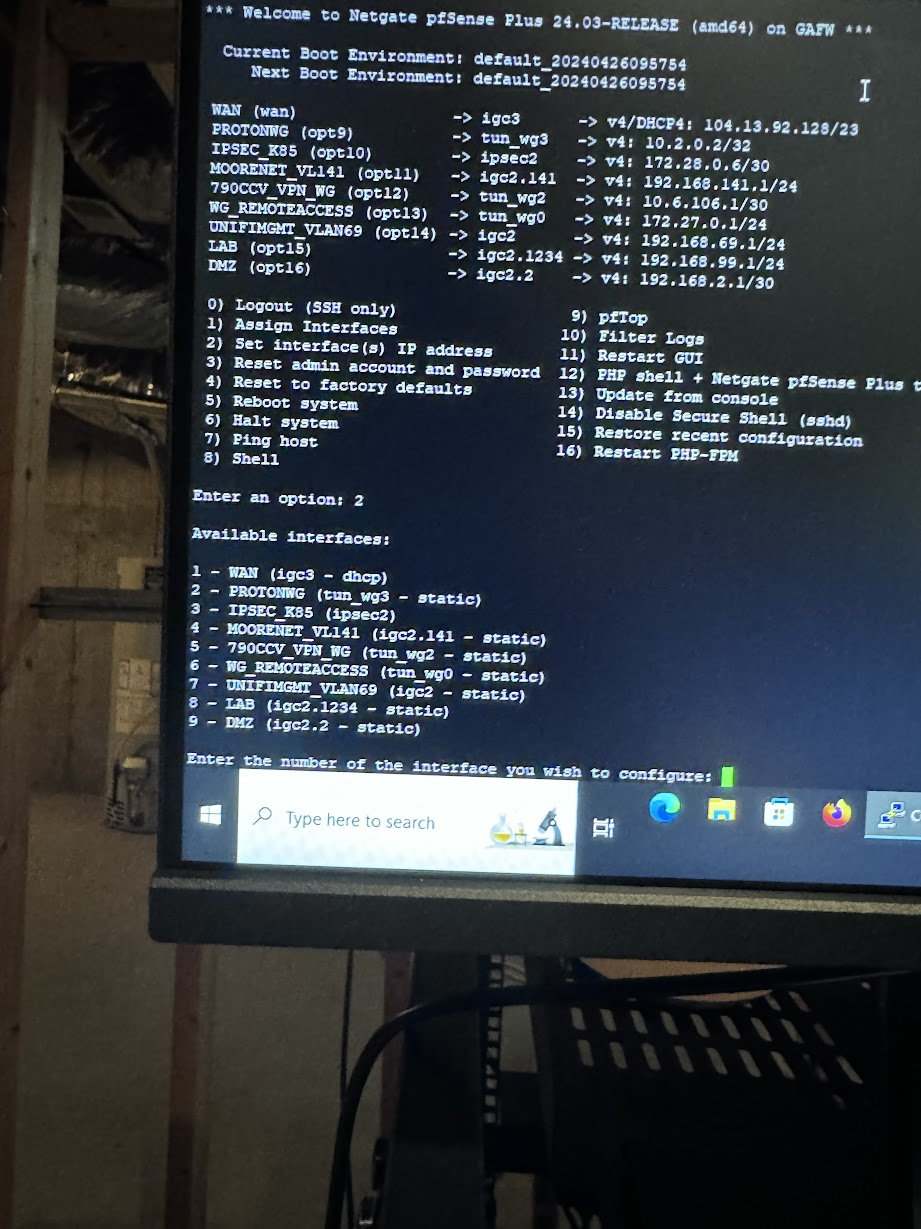
Boot env
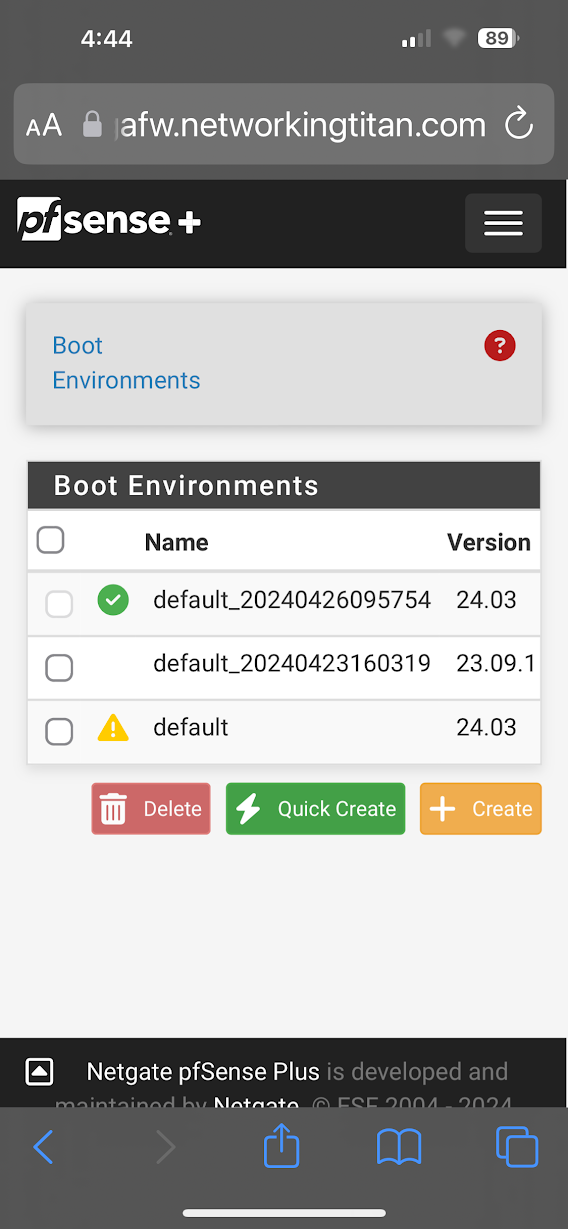
The default seems to be broken for some reason but the one being booted is corrupted i feel as its not loading the most recent config.
I went into BE and cloned the default that is in a warning state ..i think... rebooted. Firewall comes up with the latest configuration.
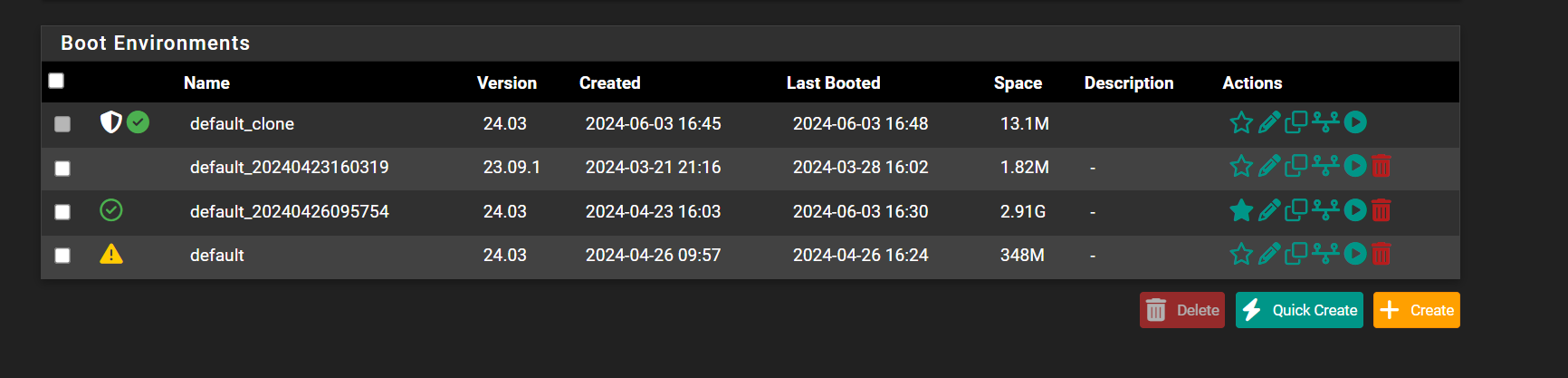
-
@stephenw10 i need your help. Why do i get the weird issues with no cause? lol
-
Hmm, that is odd. What is shown as the 'Configuration Change' for each of those backup files? It sounds like it may have been stuck in a loop creating configs, at boot possibly?
Are those missing interfaces available to assign?
Can you restore a config remotely? Do you have other backups? ACB configured?
-
@stephenw10
My config history is all from today.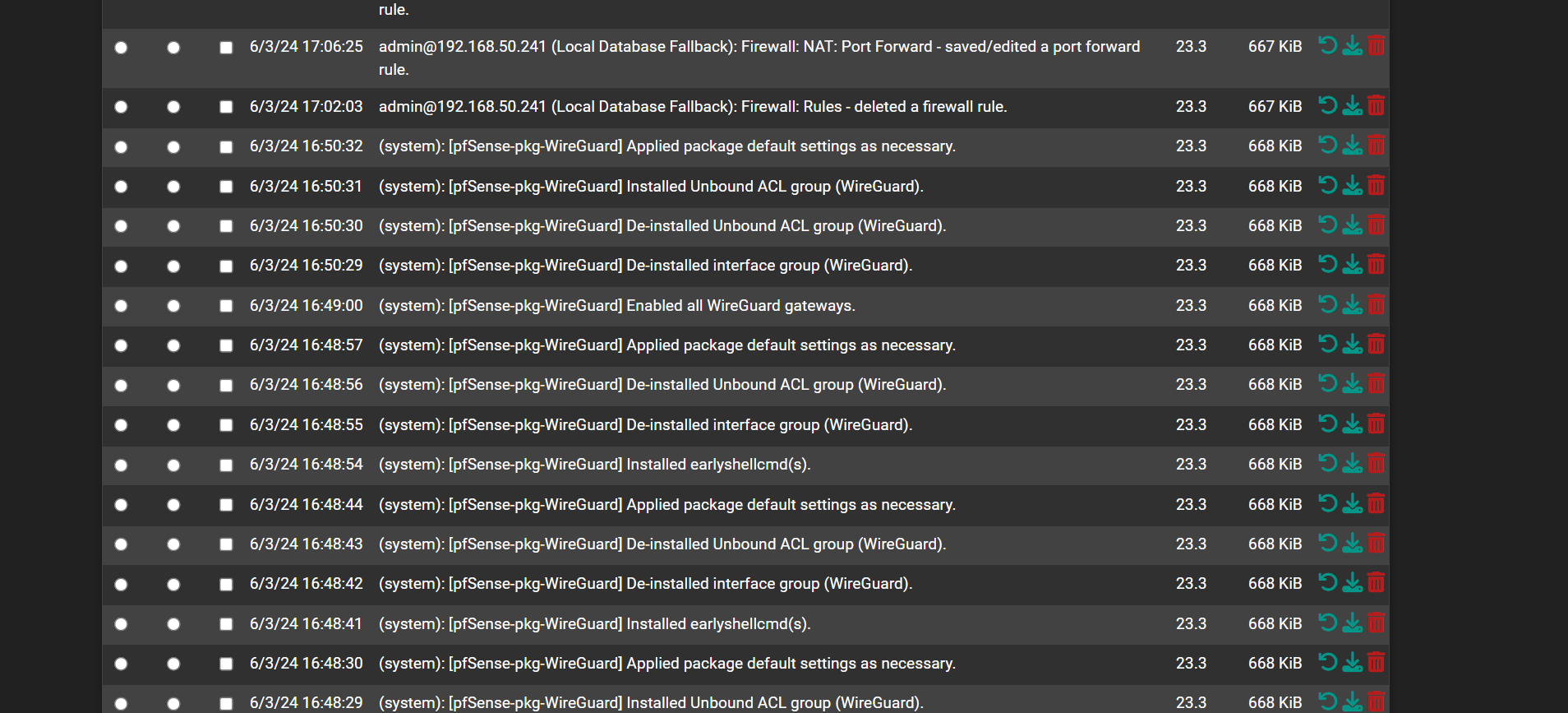
My remote VPN network was still assigned so i got in through there. I cloned my default BE. Rebooted the firewall. All my config came back.
-
ACB does have better back ups available thank goodness.
-
Yeah ACB excludes those package config writes to prevent it spamming the backups.
-
@stephenw10
Question for you.
Do you recall those pfSense random lock ups i would have. I moved from an IX interface to a IGC ?
I would see increase CPU core load with [kernel{if_io_tqq_X} as the top usage item.I saw it today with this incident.
Maybe something, Maybe nothing but i noticed i have a limiter applied to certain rules on my WAN interface.
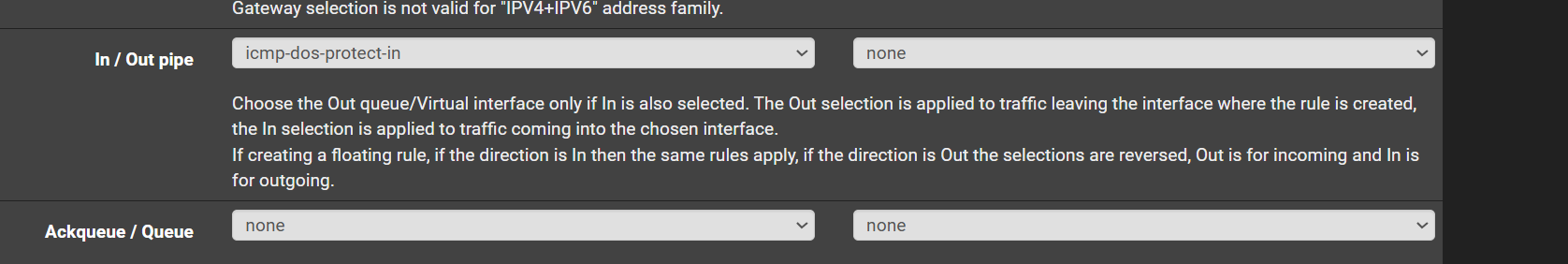
I was experimenting to see if i could police ICMP traffic. Never the less, could something like this impact performance? Could this cause issues with the NIC queue where it locks up the whole system?
-
No it shouldn't lock up the system entirely. You might end up blocking all ICMP traffic depending on how the limiter is configured. That could potentially block gateway monitoring etc.