High Avail secondary node IPs - How to find it
-
So 192.168.35.6 is the WAN CARP VIP for the HA pair? You shouldn't have to do anything at the CLI. When the VIP fails over the secondary should try to connect.
What is logged on the other side?
-
@stephenw10
So for clarityThe NATs are like this
192.168.35.6 <> x.x.188.125 - CARP VIP
192.168.35.5 <> x.x.188.124 - Secondary WAN pfsense
192.168.35.4 <> x.x.188.123 - Primary WAN pfsenseSo when I failover to backup what i see on my firewall is UDP/500 traffic coming from the Secondary WAN interface (not the CARP) which i found odd. I see that happening for a few times and then after awhile i see the CARP VIP finally reach out and establish a VPN
-
@stephenw10
I think i figured out the problem.
The firewall is behind a NAT box
When i initiate a P1 connection its trying to talk out on port 500.Obviously, this breaks IKE all together as after the translation, IKE drops packets.
NAT-T is set to Force. Yet its still trying to go out on port 500.
Any ideas as to why its doing that?I have also restarted the IPsec daemon process but same results.
edit
Confirmed. This is for sure happening. On the Cisco i see the translations, Its trying on port 500 even though NAT-T is set to Force
udp 103.127.188.124:20402 192.168.35.5:20402 x.x.92.128:500 x.x.92.128:500
-
Ok...what a marathon day with IPsec.
I think i figured out the problem and now failover happens faster.
There was an Outbound NAT policy that said
Interface: WAN
Source: Any
Destination: Any
Nat Address: 'CARP WAN Address'That seemed incorrect because my assumption is that any source address would include the firewall source address as well.
So i changed the source to 'LAN subnets' and things are looking much better.Failover is quicker but i do find that in some cases i have to hop onto thee new Master firewall and initiate P1/P2 (it doesn't initiate right away sometimes).
-
@michmoor said in High Avail secondary node IPs - How to find it:
There was an Outbound NAT policy that said
Interface: WAN
Source: Any
Destination: Any
Nat Address: 'CARP WAN Address'That seemed incorrect because my assumption is that any source address would include the firewall source address as well.
That's correct. Outbound traffic from the firewall itself must not be natted to the CARP VIP.
If you have multiple local subnets and want to use any for the source you can override the default outbound NAT rule by additional ones for the firewall itself at the top of the rule set:
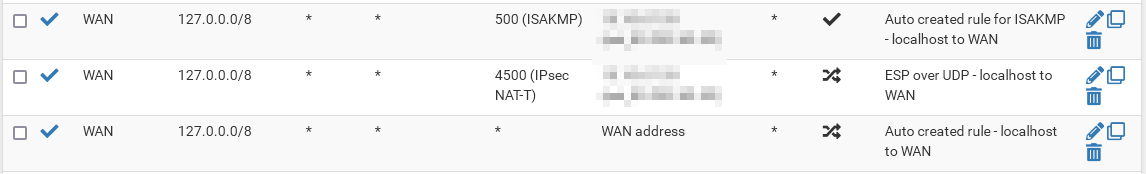
Also remember, that connections to port 500 must keep the port static.
-
Yup, that^.
Outbound NAT rules should almost never use source 'any'. Always define the subnets you actually need translation from to avoid over matching. IPSec is most commonly broken by that but other things can be.
-
@stephenw10
So on my firewall, i have the following SNAT rules. Do i need to create one for NAT-T as shown in your picture @viragomann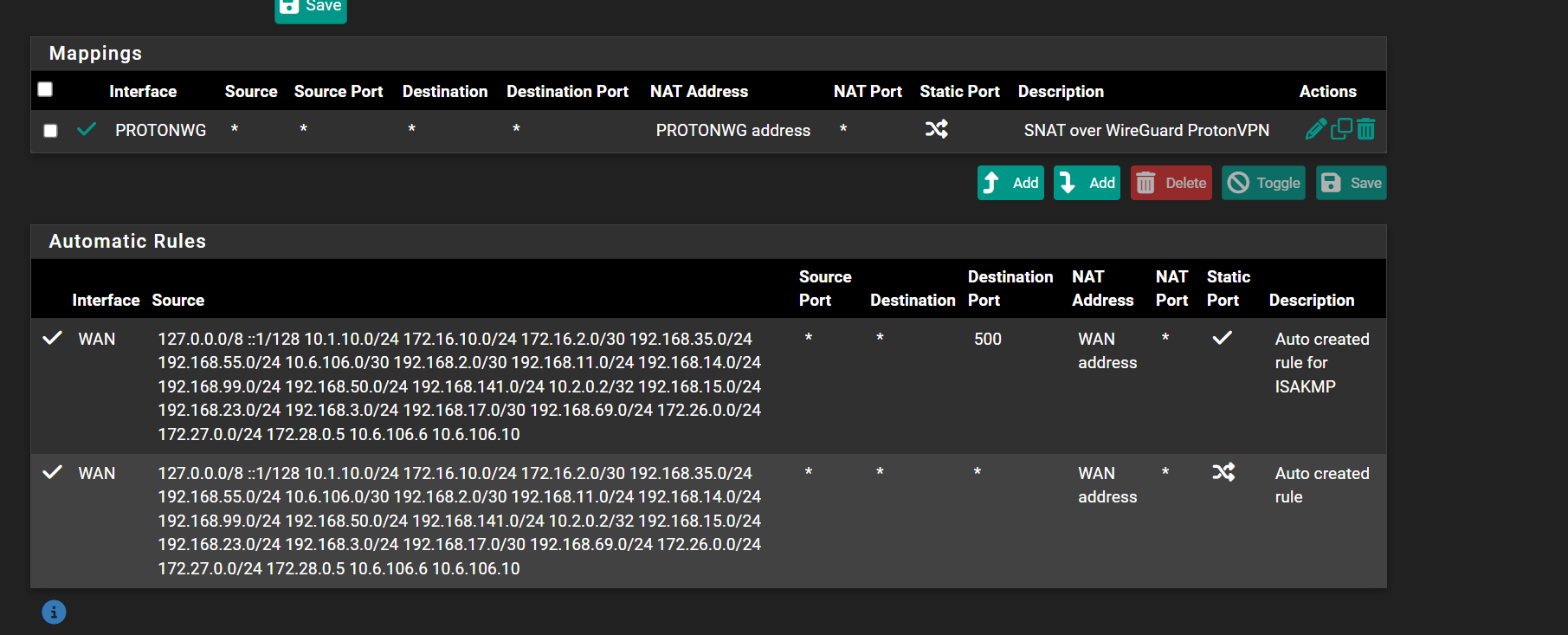
-
@michmoor
No, if you don't have a manual rule natting to any other IP than WAN address (e.g. CARP), you don't need a specific rule for IPSec NAT-T.
However, I assumed, we were talking about a CARP setup. -
But I would set a source for that manual rule over the VPN so it can never over-match traffic that shouldn't be NAT'd.
-
@viragomann Sorry i sent a screen shot of my own pfsense not in HA mode but i wanted to ensure i didn't need to do any SNAT rules here
-
@stephenw10
So you mean for source address use the WAN interface? -
Nope the source should be the subnet (or subnets) that need to be translated to the VPN address. So whatever internet subnet(s) you;re routing over the VPN.
-
@michmoor said in High Avail secondary node IPs - How to find it:
@viragomann Sorry i sent a screen shot of my own pfsense not in HA mode but i wanted to ensure i didn't need to do any SNAT rules here
In a CARP set up you might have an outbound NAT rule in place, natting the source address to the CARP VIP. Maybe your outbound NAT is also in manual mode, not hybrid.
In this case you need an additional rule for pfSense itself as shown in my screenshot above. But it would be sufficient to have the last one of these if you don't need ISAKMP (NAT-T doesn't use it, as far as I know).
And the NAT-T rule in my screen is due to using a specific outbound IP.@stephenw10 said in High Avail secondary node IPs - How to find it:
Nope the source should be the subnet (or subnets) that need to be translated to the VPN address.
Hint: you can also state an alias here by selecting "Network" and entering the network alias with a /32 mask.
-
I appreciate you folk working with me on this thread. I think i ironed out all the issues and/or misunderstandings i was having here.
Appreciate yall !