Bypass VPN VLAN to external IP?
-
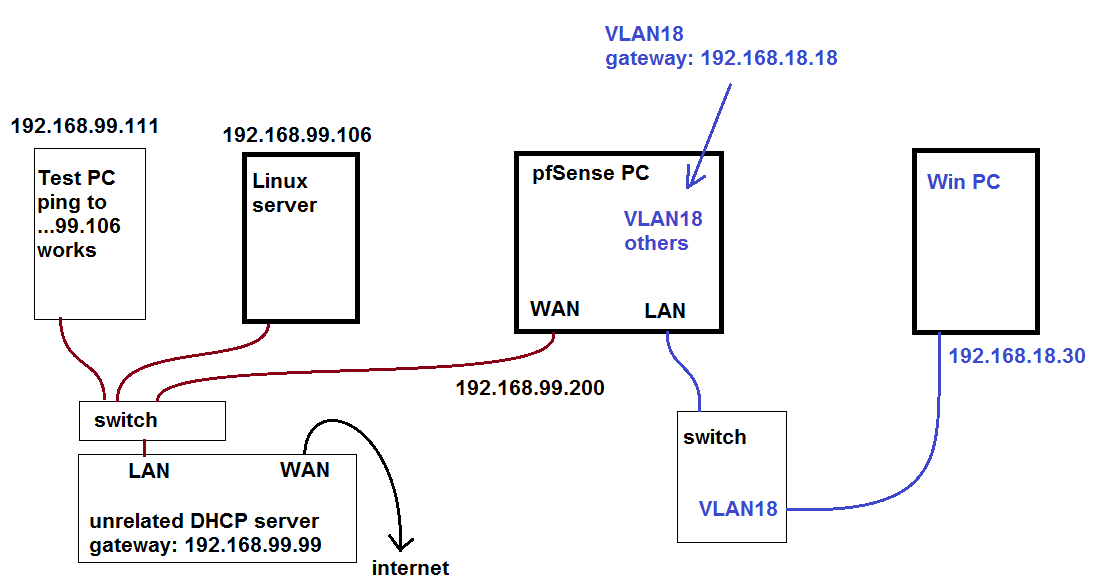
Hi. I'm trying to learn more about networking and how to use pfSense. My network is definitely getting convoluted but that's kind of on purpose to learn more things, so please forgive me for the confusing setup. The portion of interest is like this:
I have a Linux server at 192.168.99.106 and I have a pfSense PC on the same network at 192.168.99.200 (with that I'm describing the WAN port of the pfSense PC).
From the pfSense PC I have several VLANs with DHCP servers "coming out of" the LAN port. One of those VLANs (VLAN18) is set up to use OpenVPN and then I have a WinPC connected to that, at 192.168.18.30 (that PC is going through the VPN).What I'm trying to do is, keep using the VPN but for a couple of small things I want to bypass the VPN to get to the Linux server, and for starters all I'm trying to do is get ping to work. I used a test PC (192.168.99.111) to make sure I can ping the Linux PC (192.168.99.106) and that works.
I started with port forward and then realized, I think that is for connections coming into the WAN port and I'm trying to go the other way, so then I switched to outbound but there are just so many different combinations of options, not to mention firewall rules, after many hours of trying stuff and reading up on it, I decided I could really use help on this.
The network looks like this:
-
@SubSeven said in Bypass VPN VLAN to external IP?:
What I'm trying to do is, keep using the VPN but for a couple of small things I want to bypass the VPN to get to the Linux server
Just add a pass rule to the VLAN 18 interface to allow it.
I used a test PC (192.168.99.111) to make sure I can ping the Linux PC (192.168.99.106) and that works.
Remember that even the PC will allow ping from another device of its own subnet, it might block access from outside by its firewall. Most usual desktop operating systems behave like this.
You may have a policy routing rule to direct traffic to the VPN gateway on VLAN 18 interface, however a policy routing to the VPN gateway on the VPN interface is pretty useless.
Remember to put the pass rule for allowing traffic to internal destination above of the policy routing rule, so that it is probed first.
-
@viragomann Thanks for the tip about the ping, I did not know that. Now I've switched to a different test, there are 2 web interfaces on the Linux server, on port 80 and 8080. I figured I should be able to access those from "another place" as long as the other place can reach the server.
@viragomann said in Bypass VPN VLAN to external IP?:
Just add a pass rule to the VLAN 18 interface to allow it.
So would you say that I don't need to do anything with NAT though?
I didn't know for the gateway if I'm supposed to select default or the non-VPN gateway. I've tried both and it's not working yet. I also tried changing the order, that didn't help.
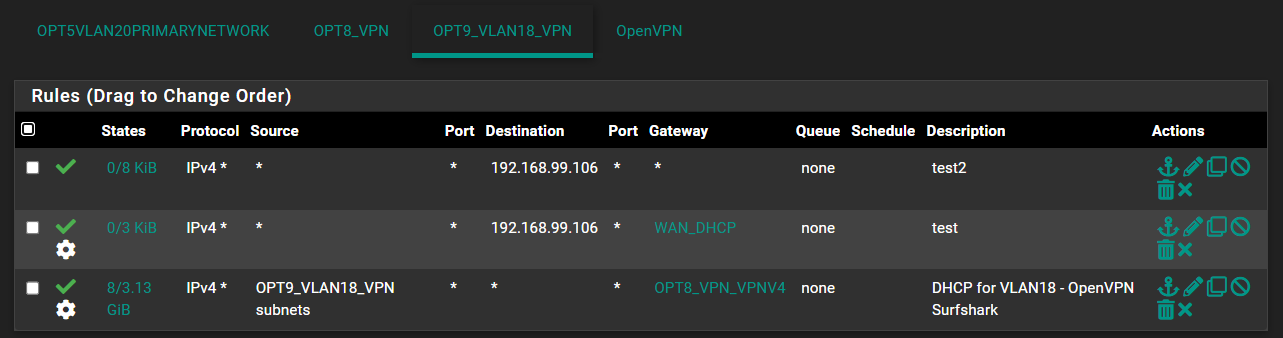
Then I also tried to do the same on the ovpnc1 interface (OPT8_VPN) and that didn't seem to help either.
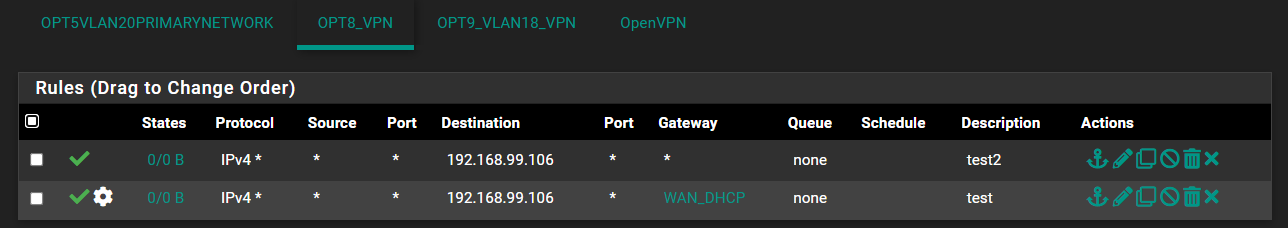
Just to confirm that I have the right idea, the following is true?
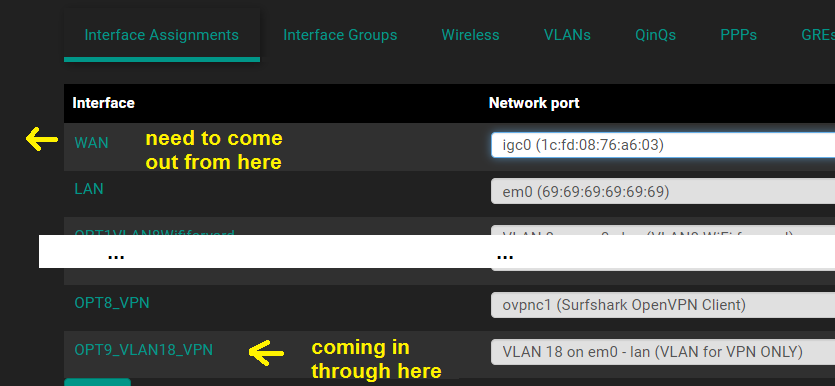
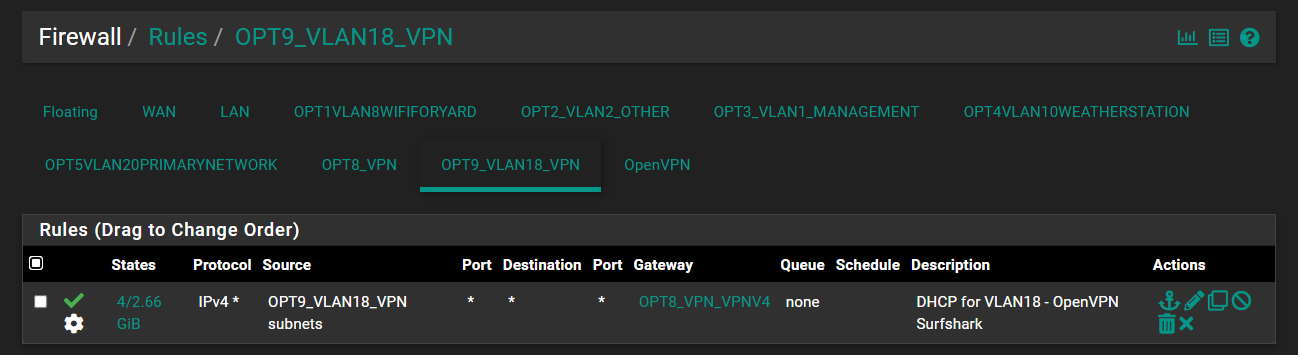
This is probably not relevant but I am a bit confused by having 2 different VPN thingies under firewall rules:
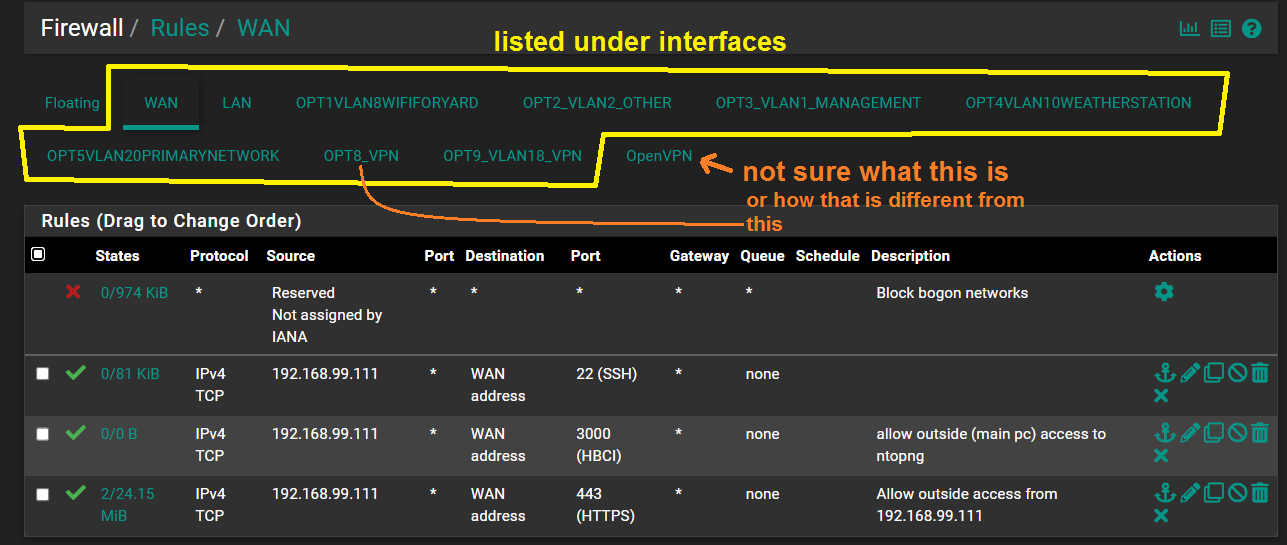
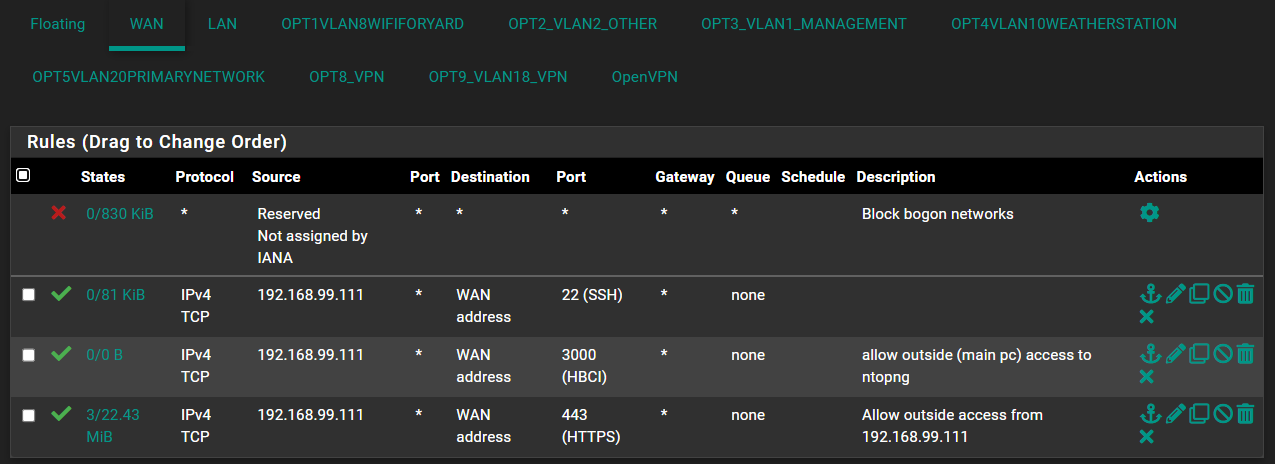
I feel like with the 4 rules I've added that traffic for the server (...99.106) is allowed to come in through the VLAN18 and uses the non-VPN gateway. Since it's still not working I will try to do a outbound NAT but here too I'm not really sure what I'm doing and I've read a bunch of documentation but I still don't completely understand.
I'm struggling with stuff that is probably super basic. For instance, outbound NAT, I'm confused what I select as the interface. The description reads:
The interface on which traffic is matched as it exits the firewall. In most cases this is "WAN" or another externally-connected interface.This is most confusing to me. I thought the interface is the place that the traffic is coming in from. Doesn't outbound mean it's going out through the WAN, like in my case I'm trying to go in at VLAN18 and then out from the WAN port. I don't know why it says for the outbound NAT that the interface is usually the WAN port. It's also slightly confusing to me "as it exits the firewall". I know that all the firewall rules apply to incoming traffic only. So I guess it looks like this: interface (VLAN18) -> firewall rule (matches with a pass) -> traffic now exits the firewall and enters the outbound NAT. Is that right?
The interface I selected is the VLAN18 and I think that is the right one. I have a little bit of confusion regarding the other 2 VPN interfaces. I think that OPT8_VPN is like a virtual WAN port that goes to the VPN and I don't know what OpenVPN is under rules but I imagine it's something similar. Neither of those have any rules defined and my understanding is that rules for those 2 apply to incoming connections from the VPN side, so no rules is correct for those.My understanding regarding the rules for LAN is that because I only use VLANs that the LAN is just the physical interface and I can ignore it completely and add all my rules to WAN and VLANs instead. The LAN interface only comes into play if there is untagged traffic coming in, which there isn't.
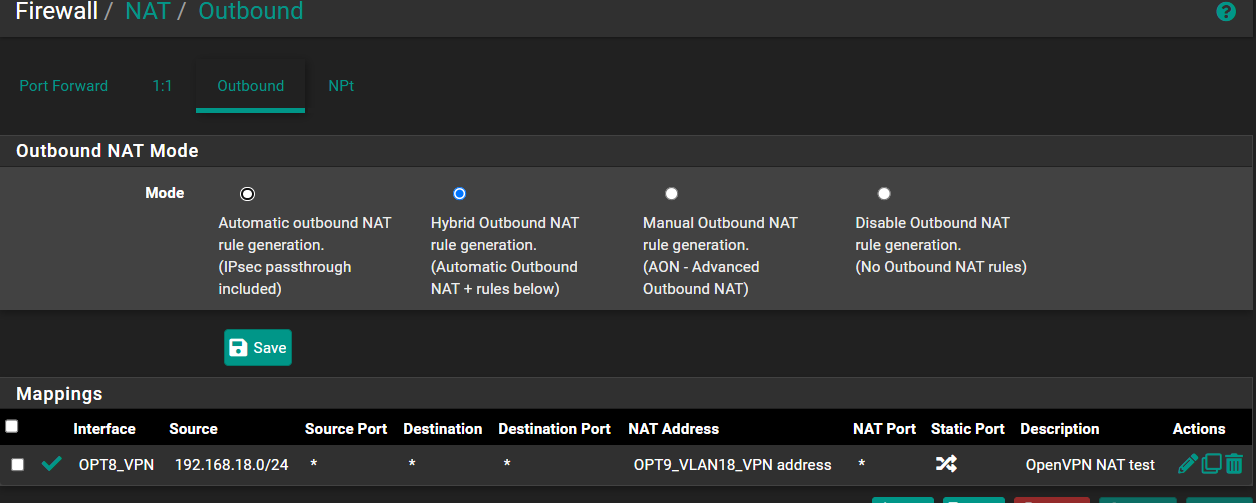
Anyway, back to the outbound NAT, I select VLAN18 as the interface and I put the linux server (192.168.99.106) as the destination (I believe this is important so that all other traffic continues to go through the VPN). Under translation for address I put WAN interface. I believe this means the traffic going to the Linux server will end up looking like it's coming from 192.168.99.200. I don't think that even matters, my understanding is that it would be fine if the traffic looks like it's coming from 192.168.18.30 (the Win PC) which is why I'm not even sure that I need outbound NAT. So now it looks like this:
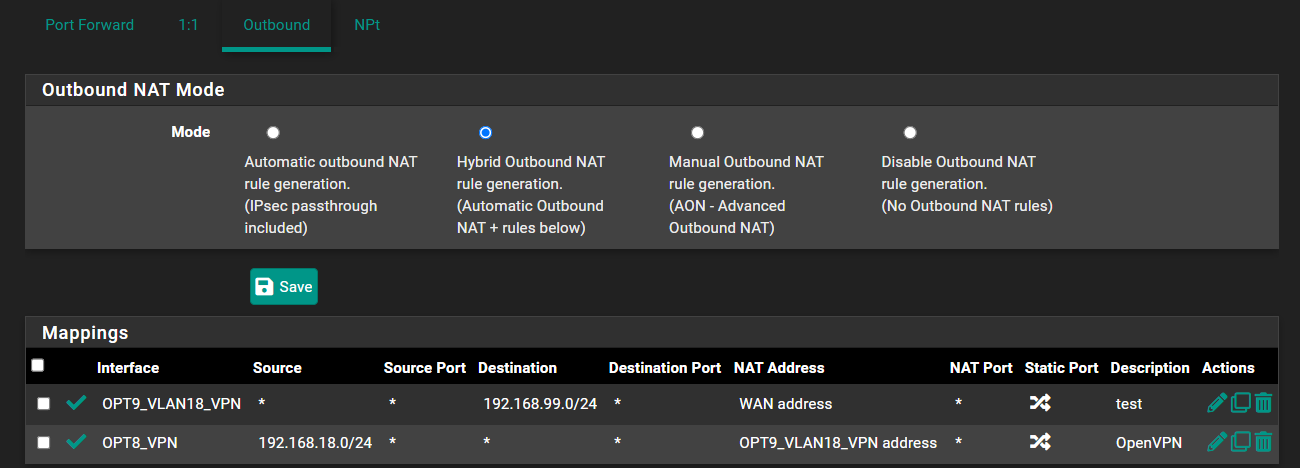
I also tried specifying the ports:
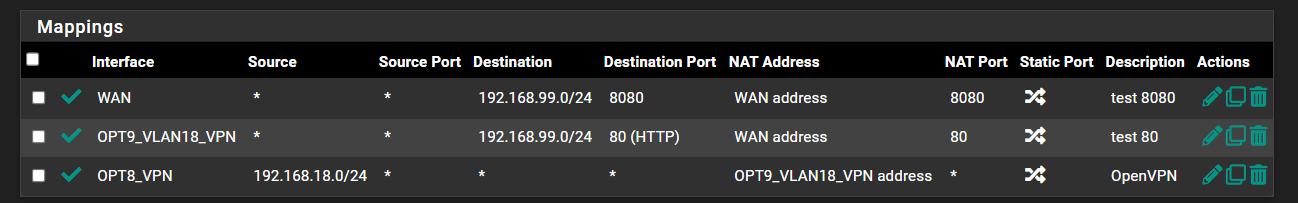
It still doesn't work and as you can tell from all of my noob questions I'm basically completely lost and at the same time aware that what I'm trying to achieve is probably a very simple task.
-
Because the destination is in the WAN subnet directly you should not set a gateway on that pass rule. That traffic has to go directly to the target not via the WAN gateway device.
Steve
-
@SubSeven said in Bypass VPN VLAN to external IP?:
So would you say that I don't need to do anything with NAT though?
Presumed, you have a gateway stated in the WAN interface settings and with outbound NAT in hybrid mode, pfSense nats traffic leaving the WAN to the WAN address automatically. So no further settings needed.
Automatically created outbound NAT rules are listed below the manual rules.
-
@stephenw10 Ok, thanks. I took out the firewall rule that had called for the WAN gateway, so it just looks like this now but still doesn't work:
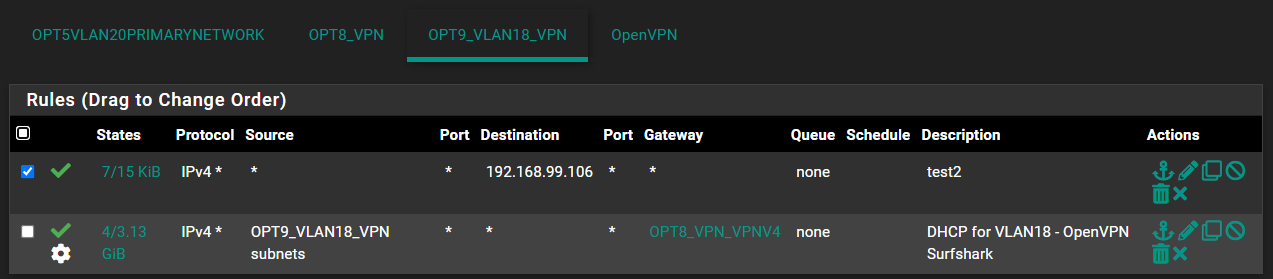
@viragomann I kind of thought that, I took out the outbound NAT entry again. So now it looks like this but still doesn't work and I assume the portion in the yellow square is what you were referring to:
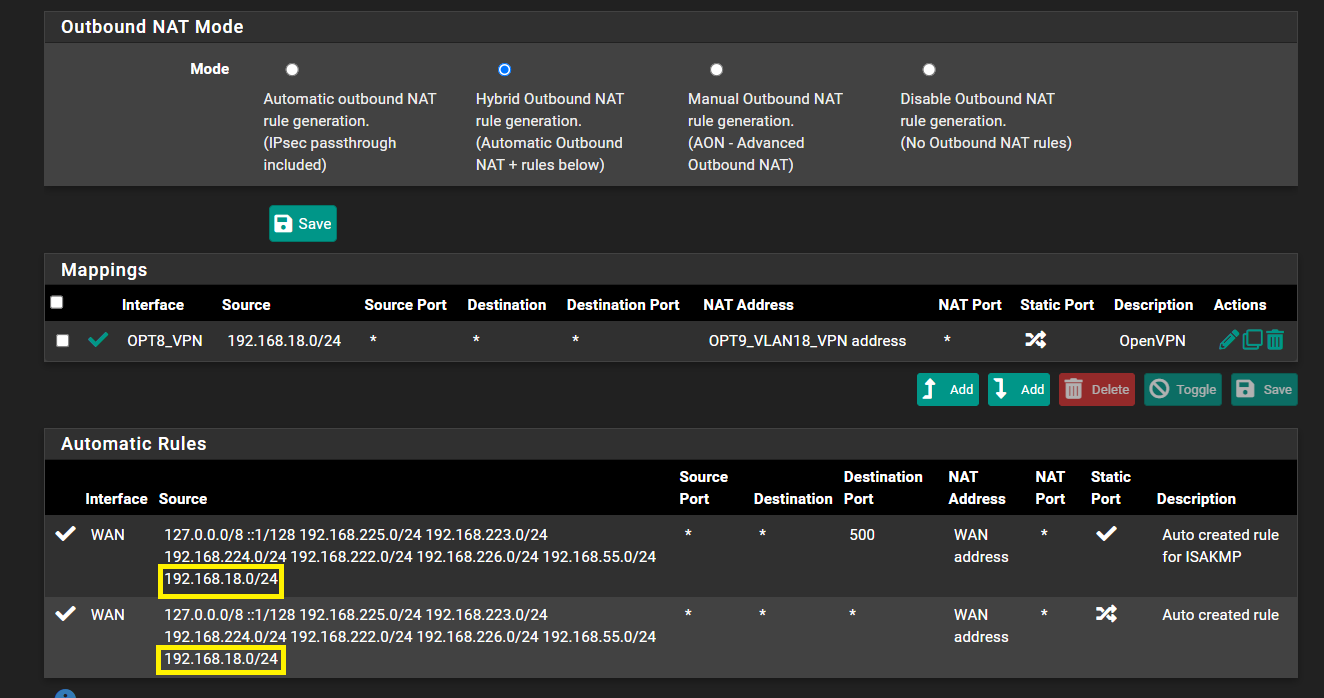
-
Check the state table in Diag > States while you're pinging.
-
Btw. I don't know if this means anything but under diagnostics/routes, I don't see 192.168.99.106 listed and I also don't see it under diagnostics/states or diagnostics/states summary.
I played around in diagnostics and found this port test and it succeeded, so at least that part works.
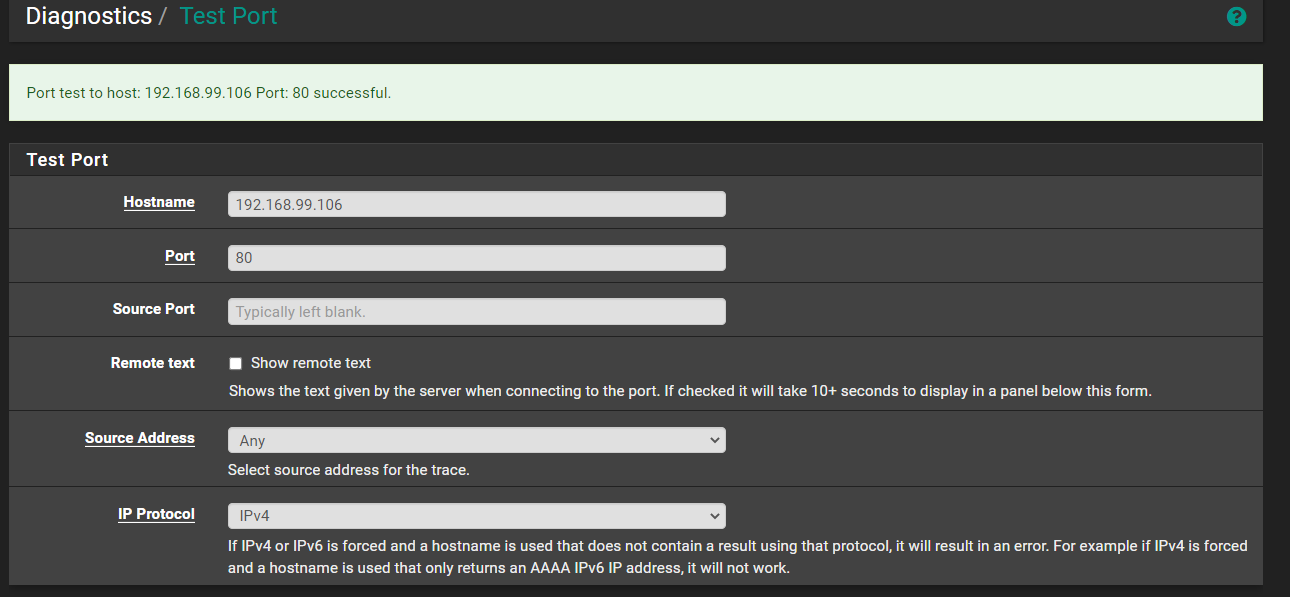
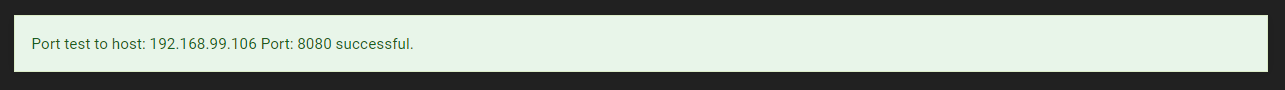
The ping also worked.
-
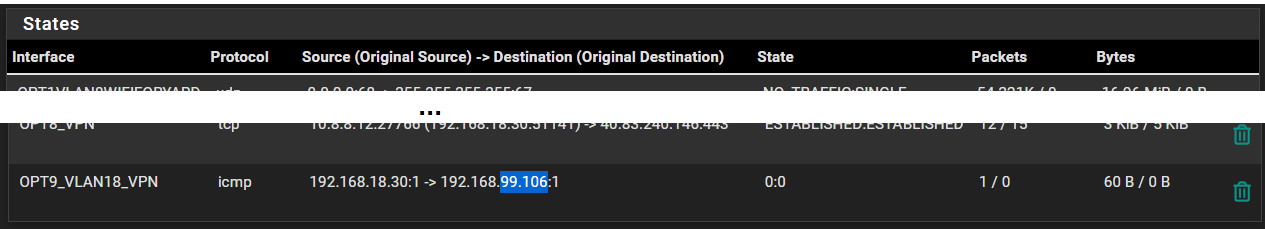
@stephenw10 Ok, I did that and something did show up:
-
@stephenw10 I don't know if this helps, but below is the same thing with ping happening, and trying to access web interface on port 80 and on port 8080:
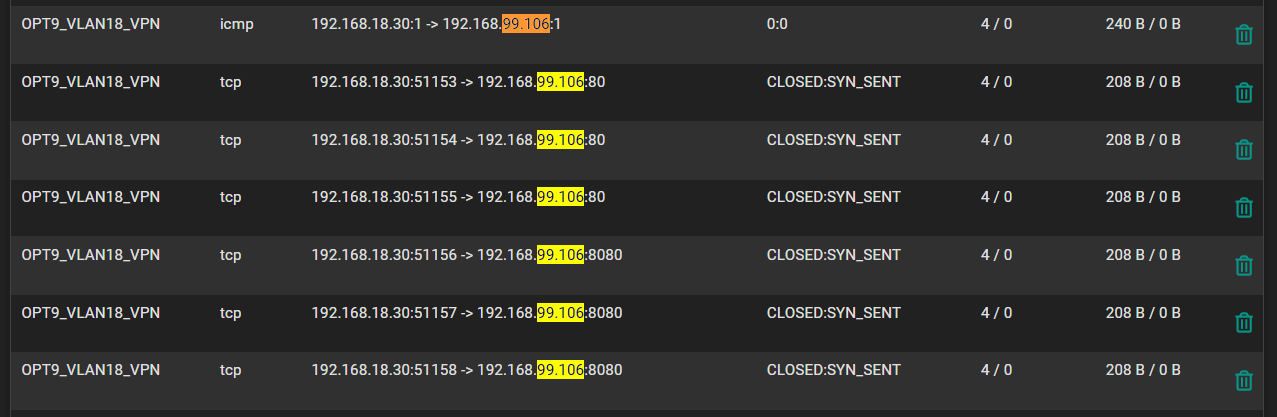
I also tried turning off the firewall on the server:
sudo ufw disable
Firewall stopped and disabled on system startup -
Ok so that is the incoming state. There should be an outgoing state on WAN too.
If it's not going out of the WAN there may be firewall rules preventing it. Or there may be no route.
You said you don't see a route but the WAN should be in that subnet. What do you see in the routing table?
-
@stephenw10 I really appreciate you helping me btw.
For the WAN rules there are these:
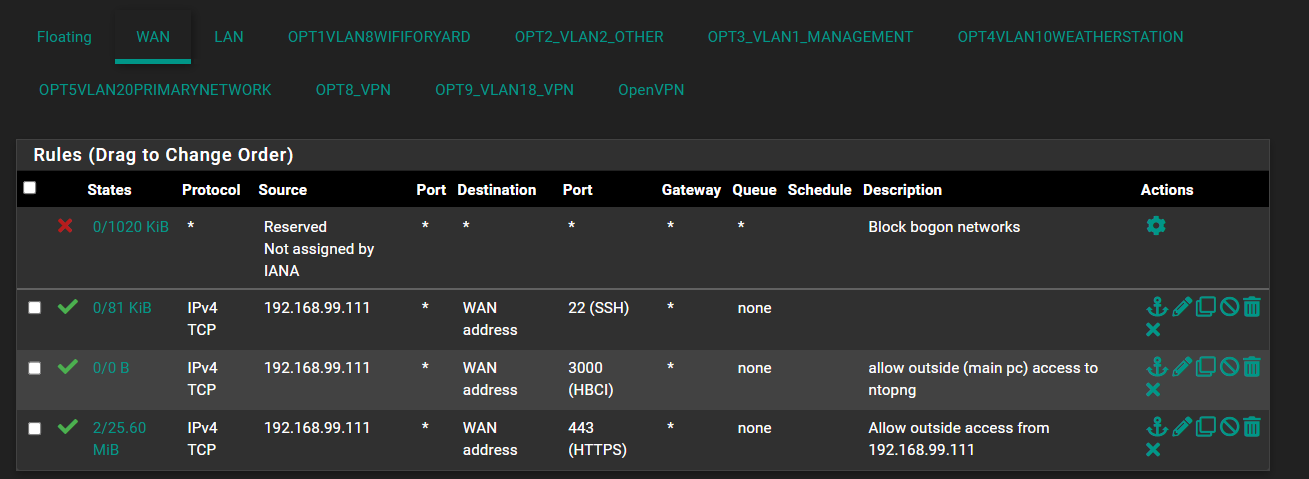
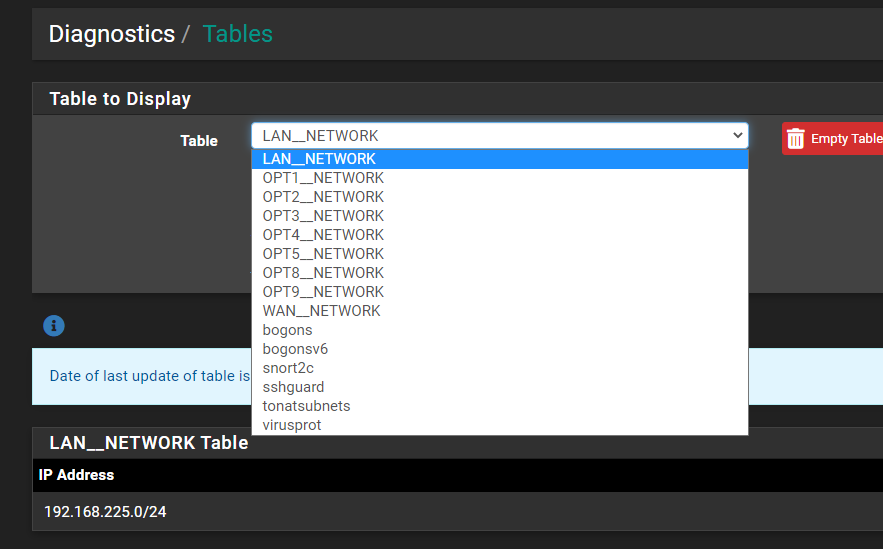
All the tables seem to be pretty empty, unless I'm looking at the wrong thing:
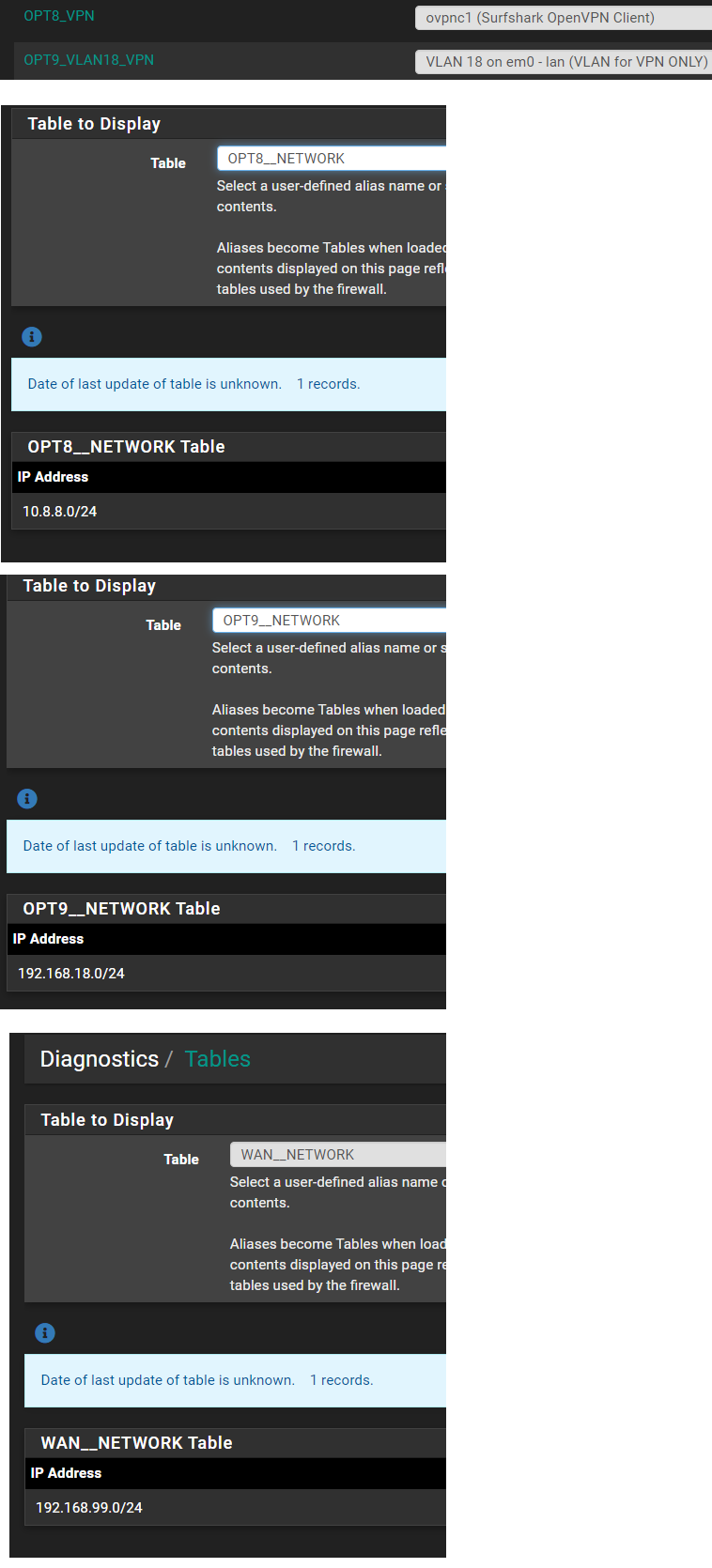
-
Diag > Routes is where the routing table is.
The rules that might block that would be outgoing so on the floating tab. Unlikely there are any.
If you have an IPSec VPNs defined that might be grabbing the traffic.
-
@stephenw10 my bad!
The floating rules are empty yes.
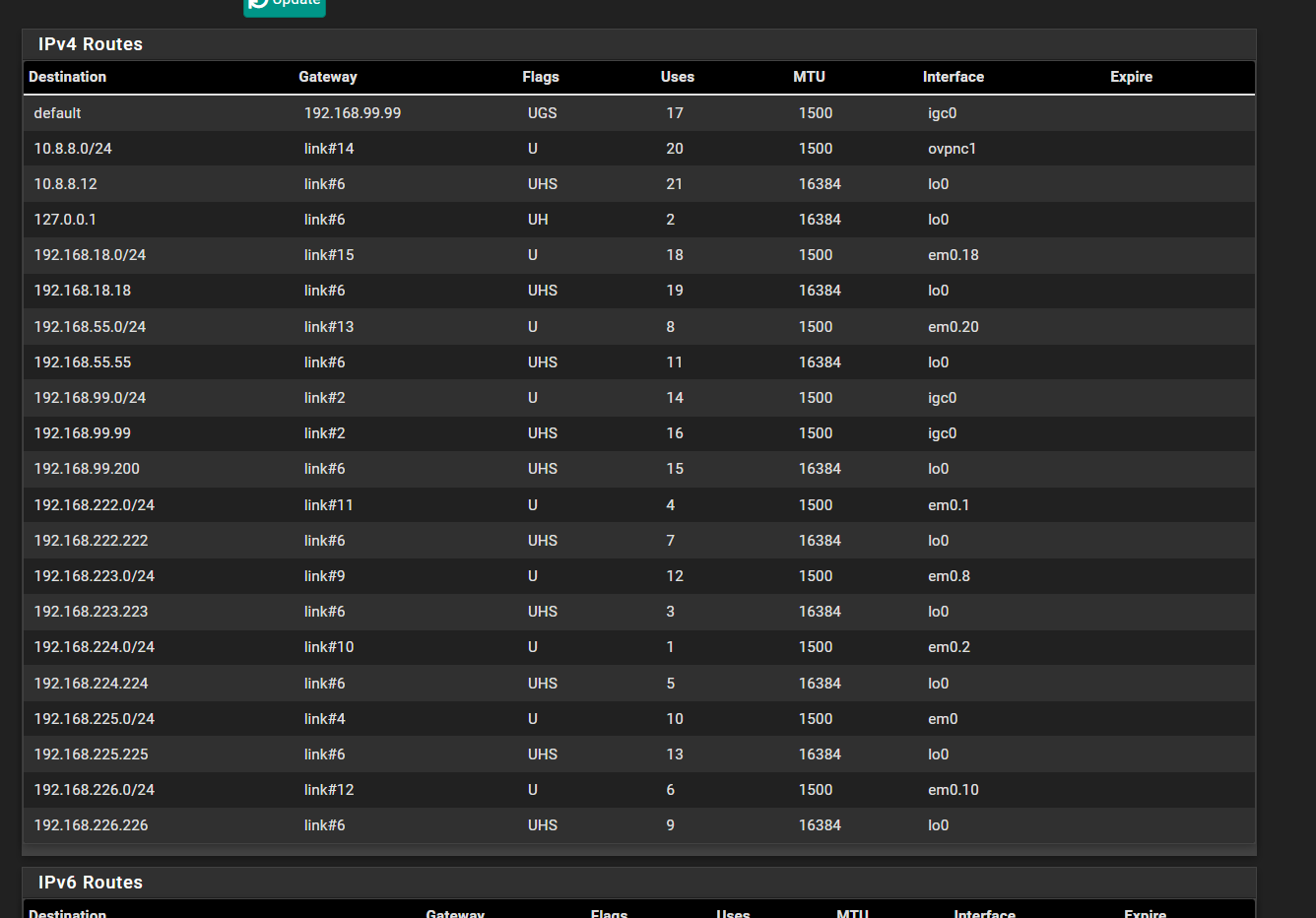
This is what is under routes for IPv4 and 192.168.99.106 is not on the list:
-
@stephenw10 I don't know if this helps but here are all the rules:
-
Hmm, well it correctly shows the 192.168.99.0/24 subnet on the igc0 interface directly so it should send that traffic to it.
Something must be blocking it. I'd check IPSec tunnels.
-
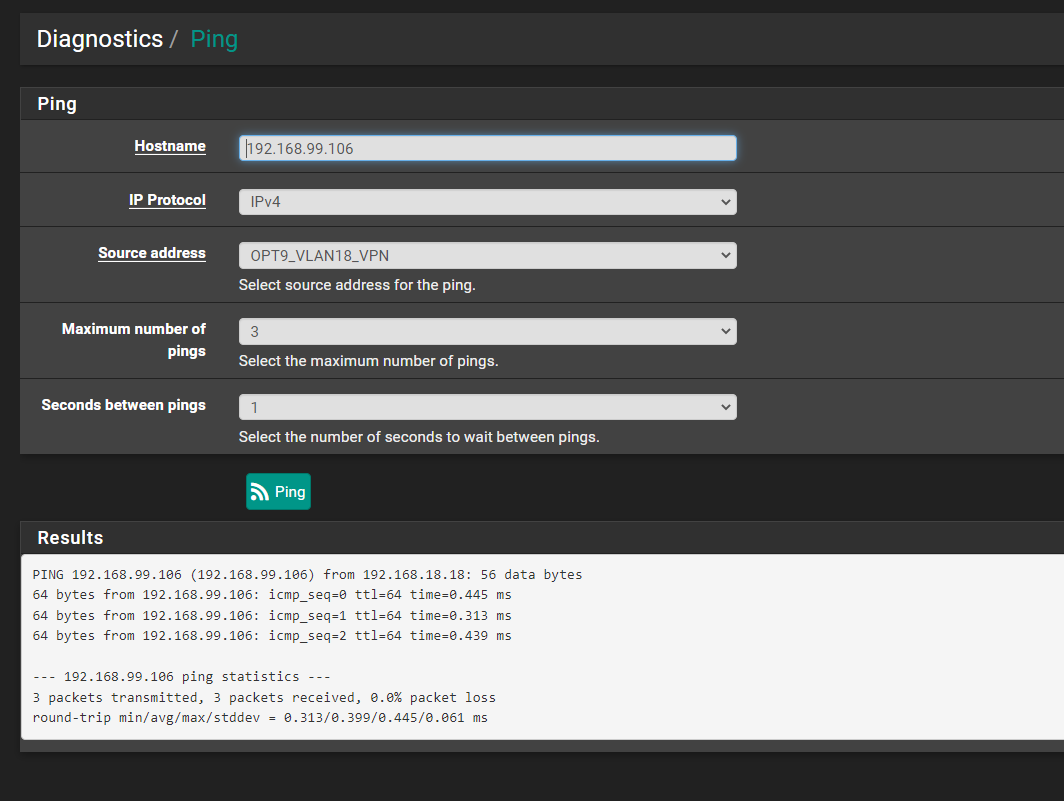
Try pinging it from the firewall but setting the source to the OPT9 address then check the states.
-
@stephenw10 Those look empty. I'm going to restart pfSense to see if that does anything and I'll also restart the Win PC and the Linux server.
-
@stephenw10 I powered all 3 down, started pfSense back up, then Linux server, and then the Win 10 PC but the good old "restart your computer" trick didn't help :)
I tried the ping and that seems to work:
At the same time I was doing that I checked the states again and saw an entry for ...99.106:
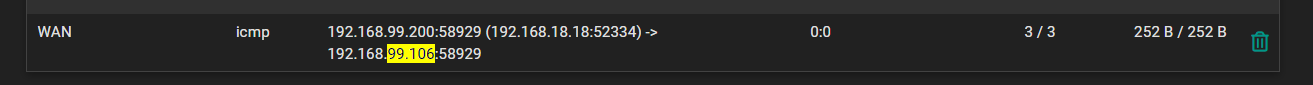
-
Ok, so that is translating as expected.
One thing I see is that pfSense has two IP addresses in that subnet, 192.168.99.99 and 192.168.99.200. Which of those is the WAN address?