Bypass VPN VLAN to external IP?
-
@stephenw10 Ok, I did that and something did show up:
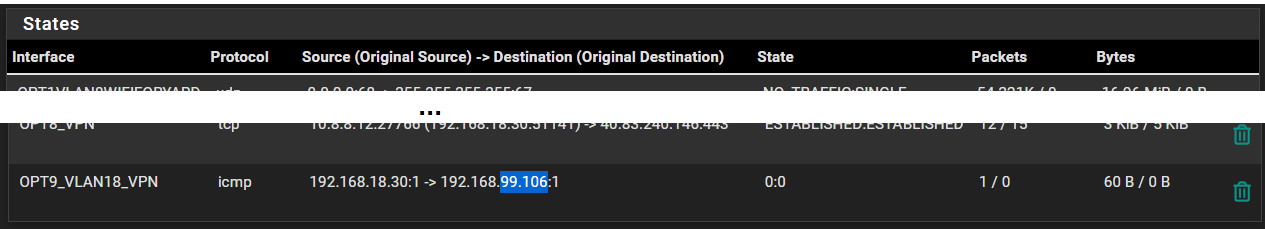
-
@stephenw10 I don't know if this helps, but below is the same thing with ping happening, and trying to access web interface on port 80 and on port 8080:
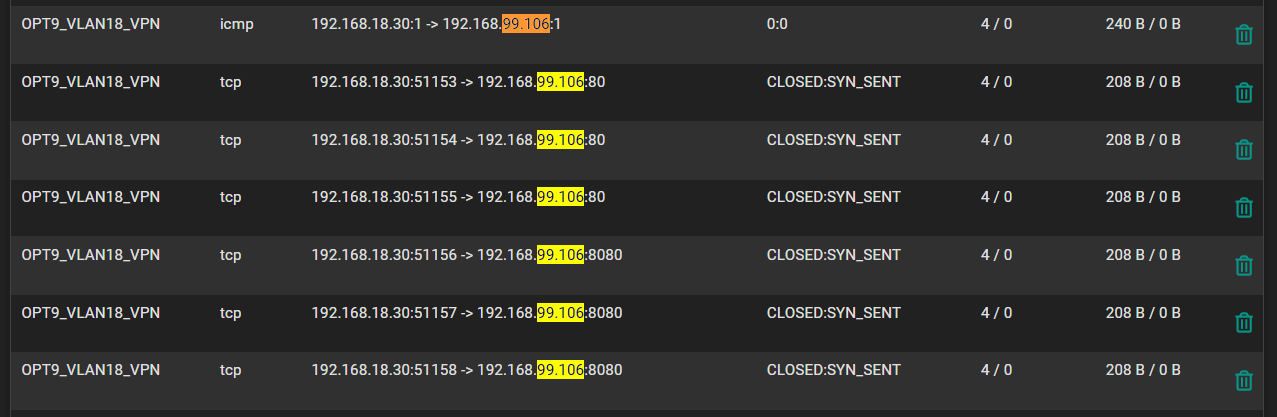
I also tried turning off the firewall on the server:
sudo ufw disable
Firewall stopped and disabled on system startup -
Ok so that is the incoming state. There should be an outgoing state on WAN too.
If it's not going out of the WAN there may be firewall rules preventing it. Or there may be no route.
You said you don't see a route but the WAN should be in that subnet. What do you see in the routing table?
-
@stephenw10 I really appreciate you helping me btw.
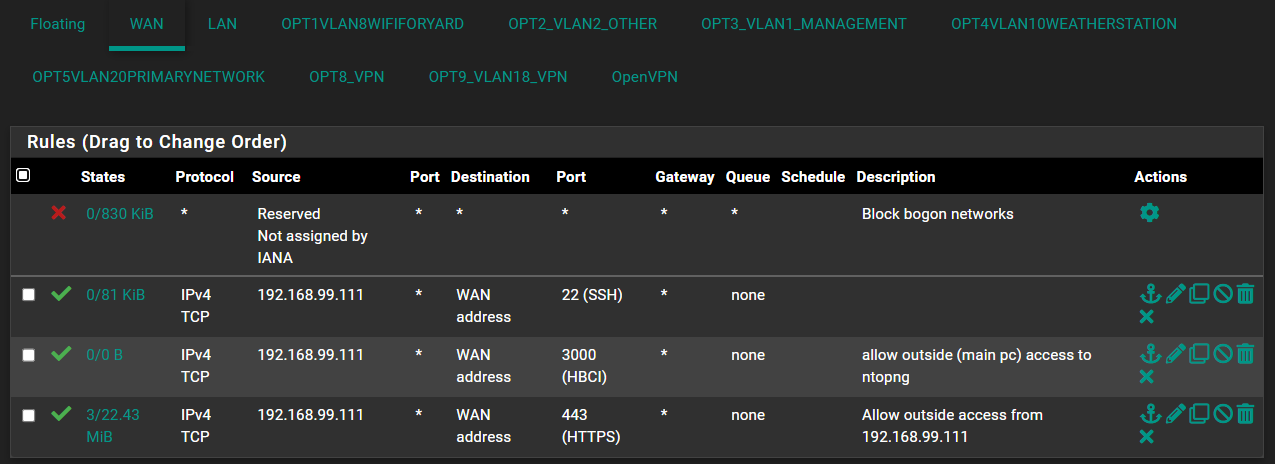
For the WAN rules there are these:
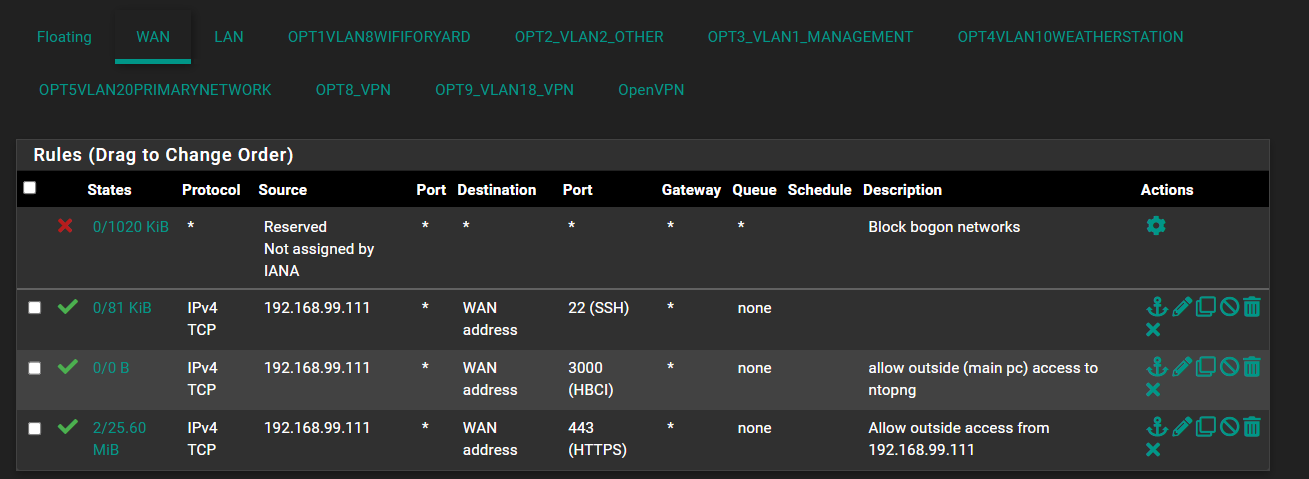
All the tables seem to be pretty empty, unless I'm looking at the wrong thing:
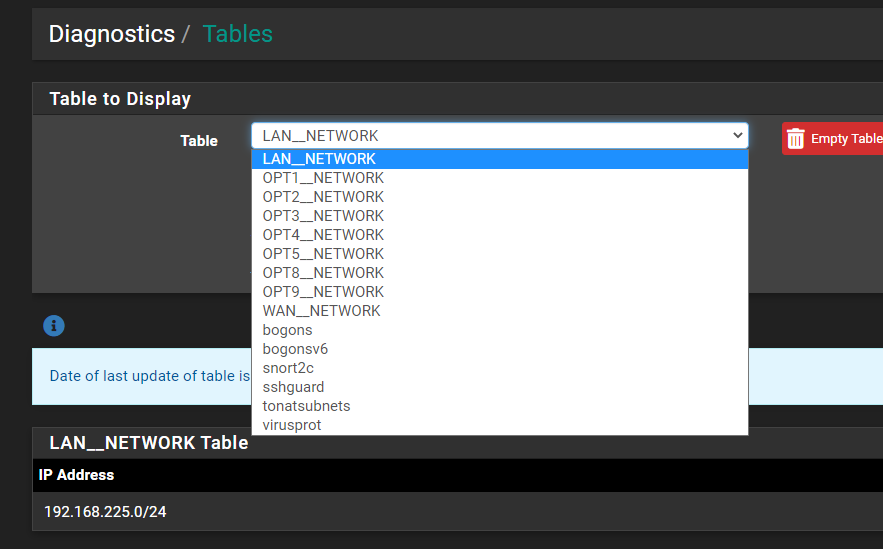
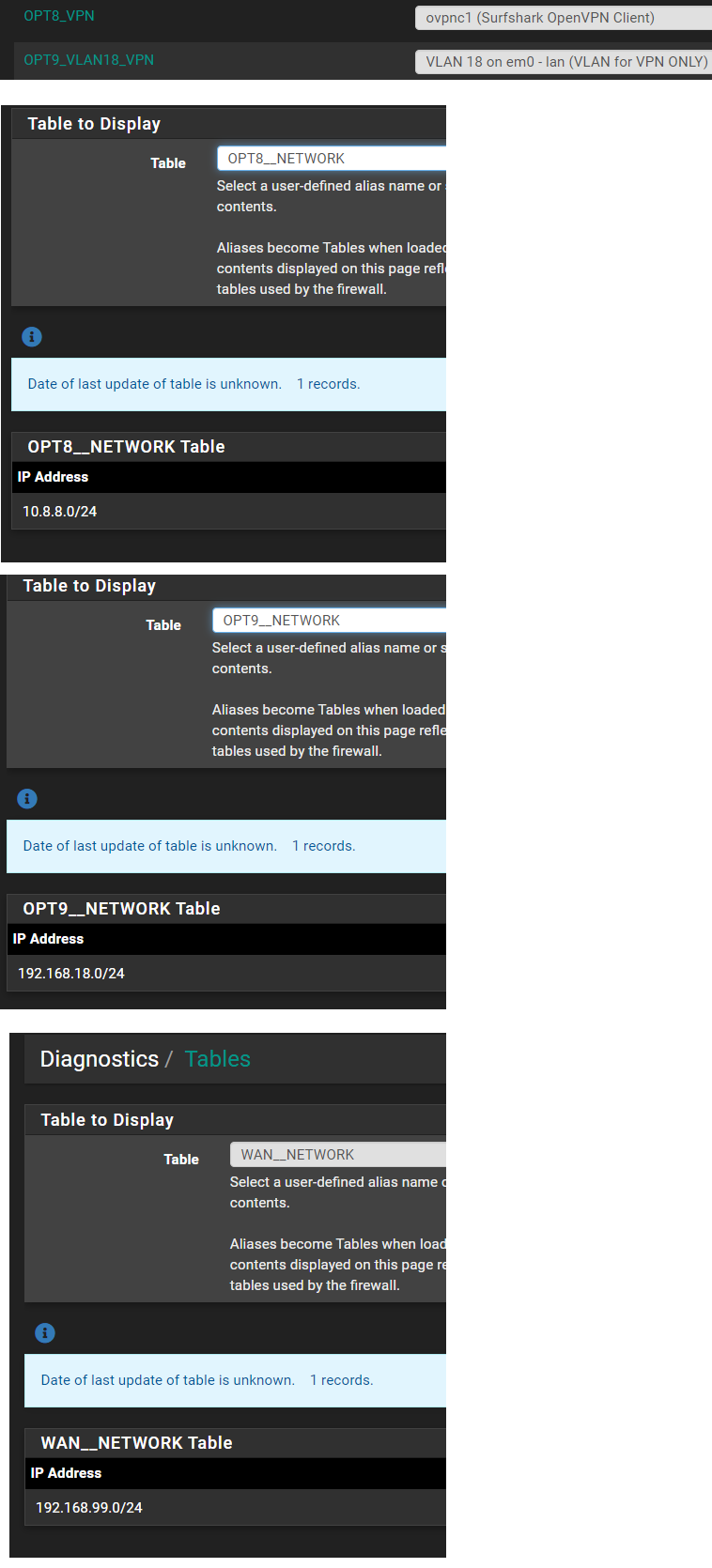
-
Diag > Routes is where the routing table is.
The rules that might block that would be outgoing so on the floating tab. Unlikely there are any.
If you have an IPSec VPNs defined that might be grabbing the traffic.
-
@stephenw10 my bad!
The floating rules are empty yes.
This is what is under routes for IPv4 and 192.168.99.106 is not on the list:
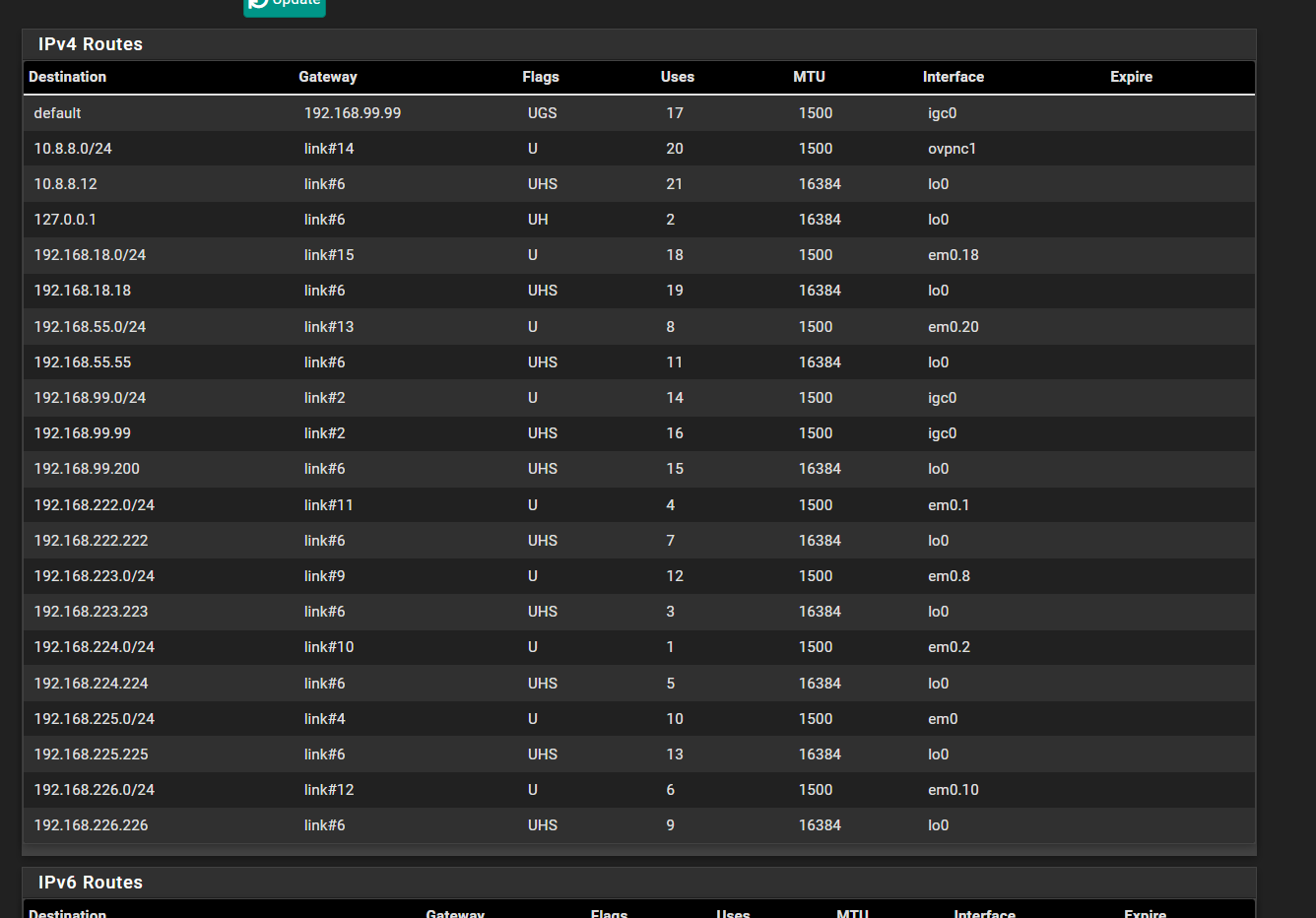
-
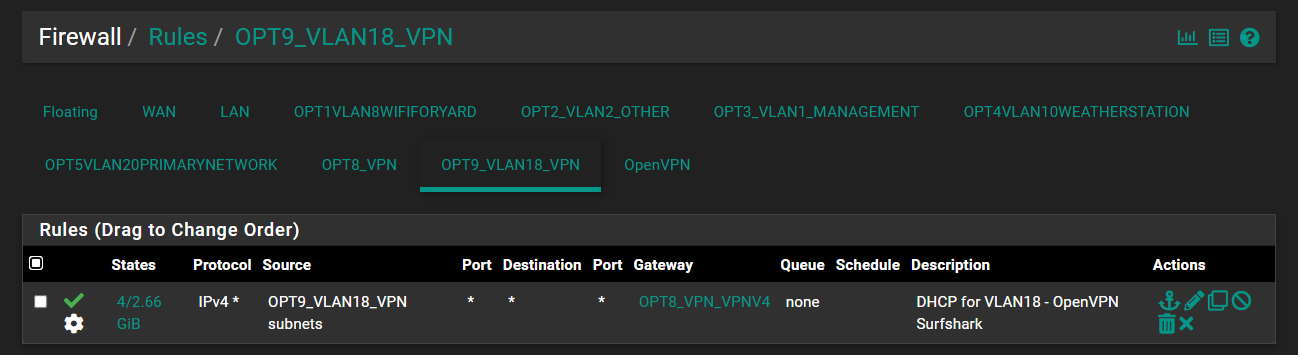
@stephenw10 I don't know if this helps but here are all the rules:
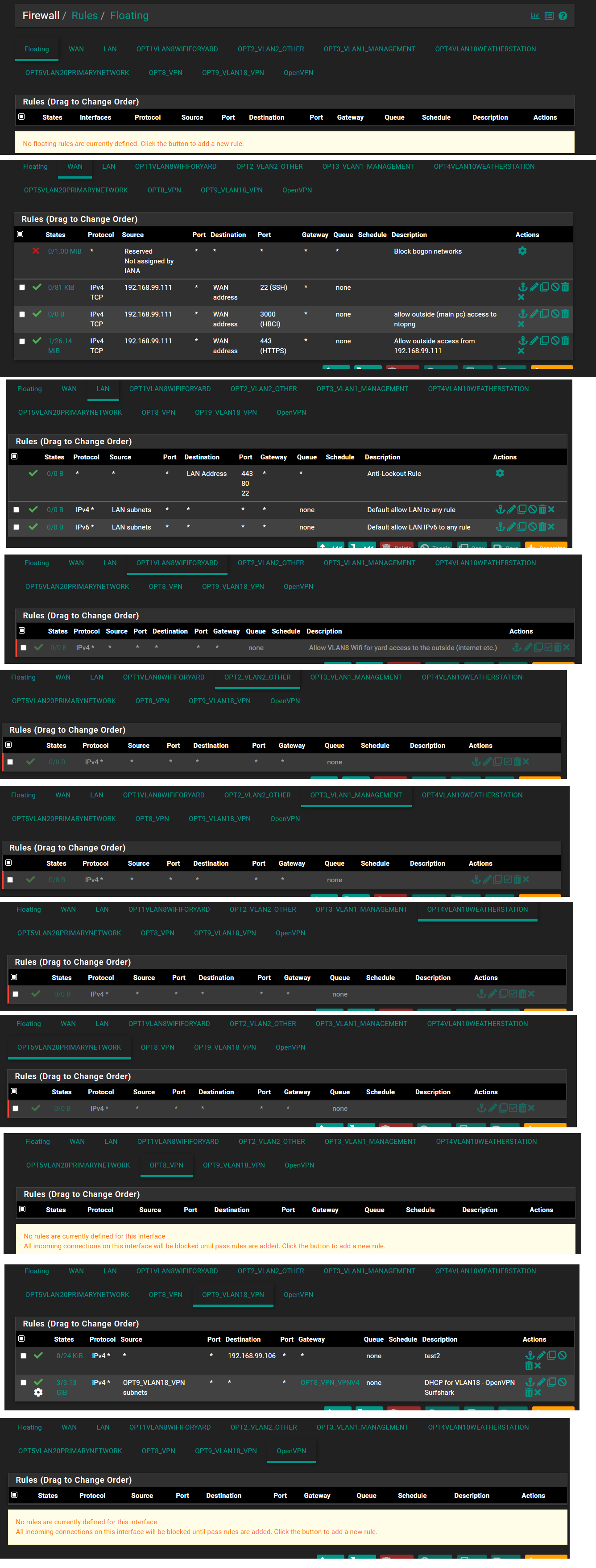
-
Hmm, well it correctly shows the 192.168.99.0/24 subnet on the igc0 interface directly so it should send that traffic to it.
Something must be blocking it. I'd check IPSec tunnels.
-
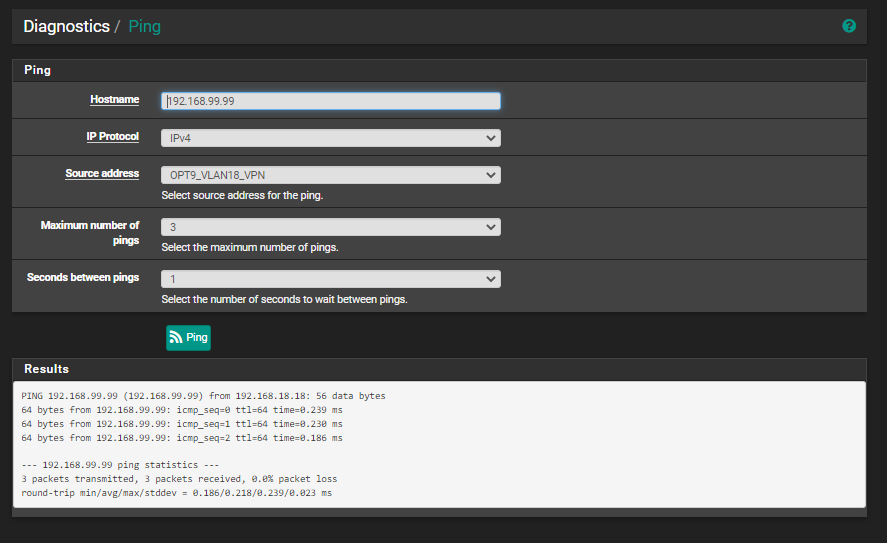
Try pinging it from the firewall but setting the source to the OPT9 address then check the states.
-
@stephenw10 Those look empty. I'm going to restart pfSense to see if that does anything and I'll also restart the Win PC and the Linux server.
-
@stephenw10 I powered all 3 down, started pfSense back up, then Linux server, and then the Win 10 PC but the good old "restart your computer" trick didn't help :)
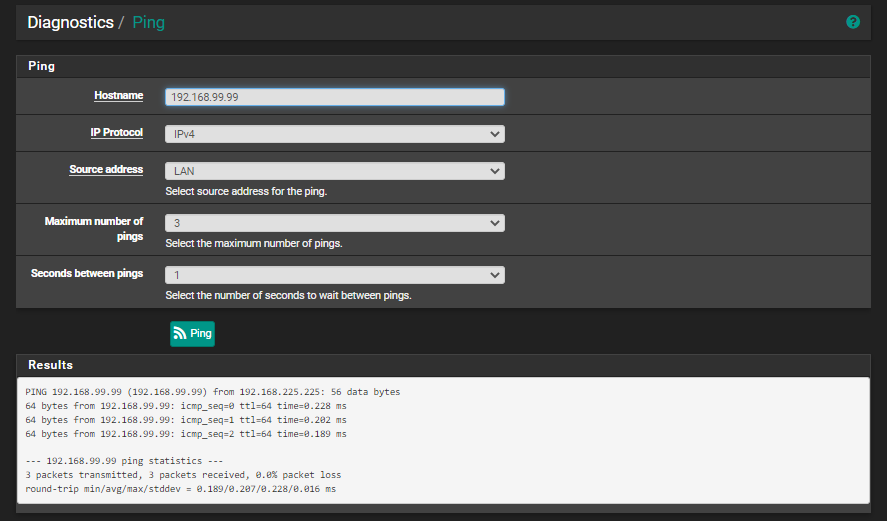
I tried the ping and that seems to work:
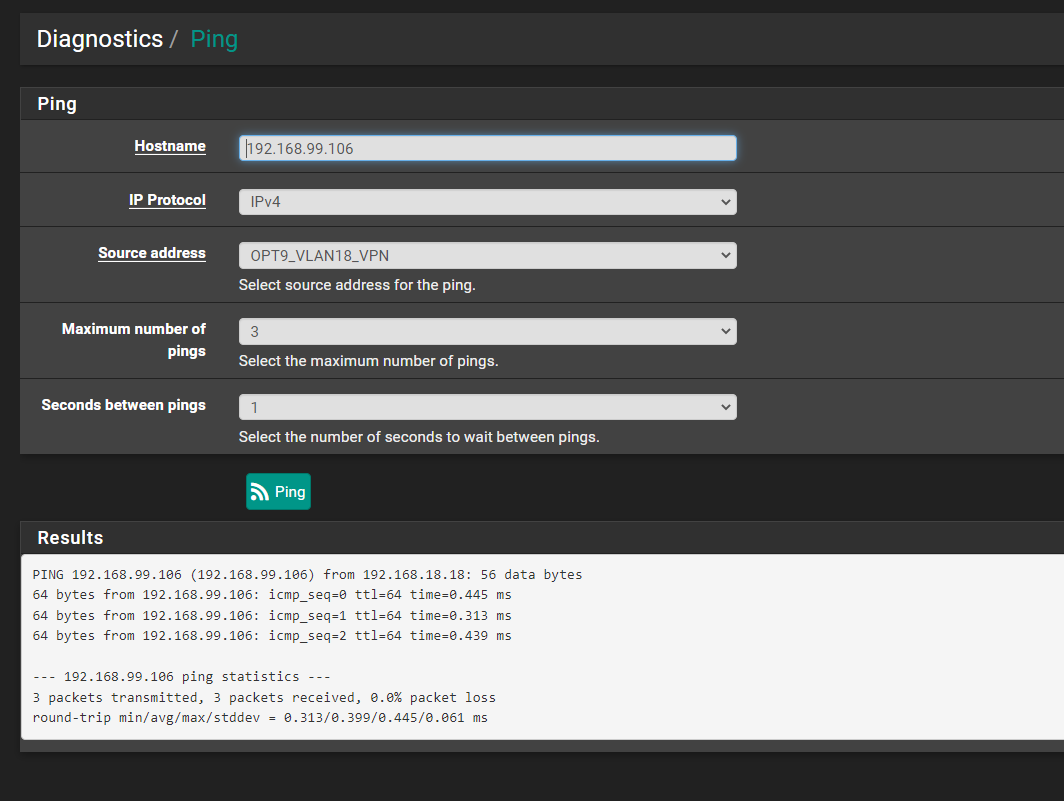
At the same time I was doing that I checked the states again and saw an entry for ...99.106:
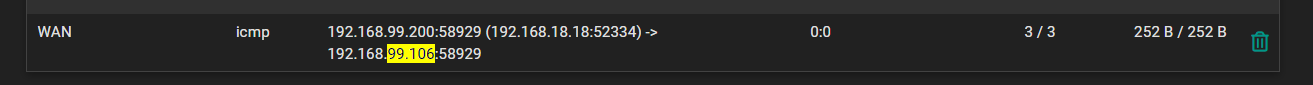
-
Ok, so that is translating as expected.
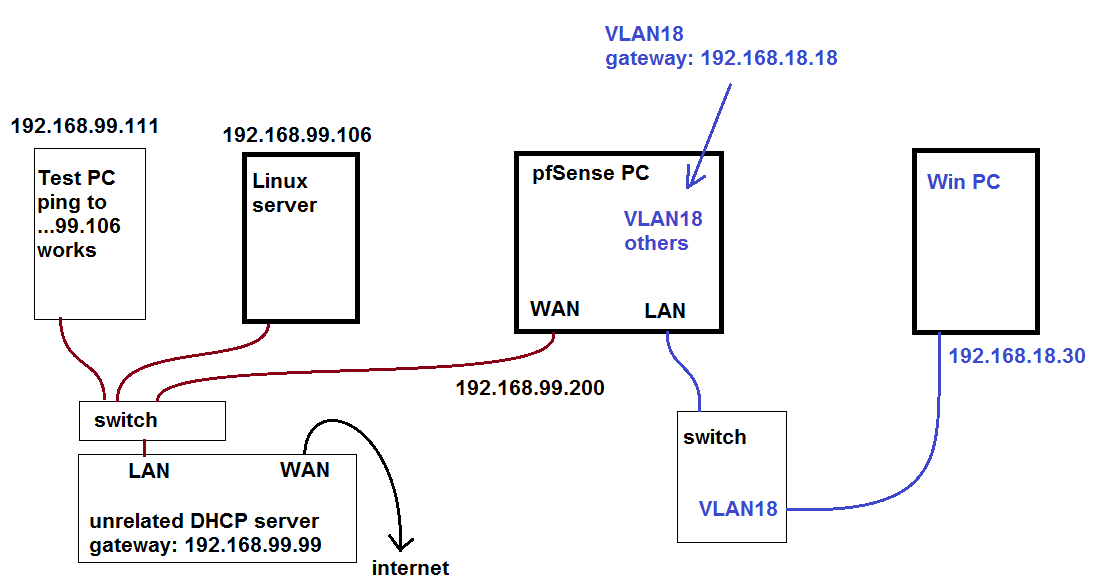
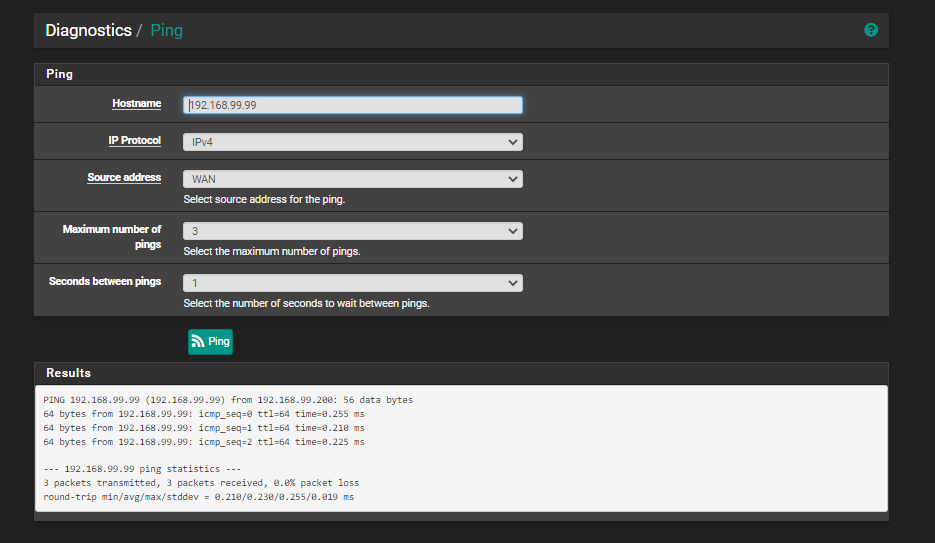
One thing I see is that pfSense has two IP addresses in that subnet, 192.168.99.99 and 192.168.99.200. Which of those is the WAN address?
-
@stephenw10 192.168.99.99 is the gateway of the parent router, it is part of my old / original network which I want to eventually get rid of. That one is running OpnSense.
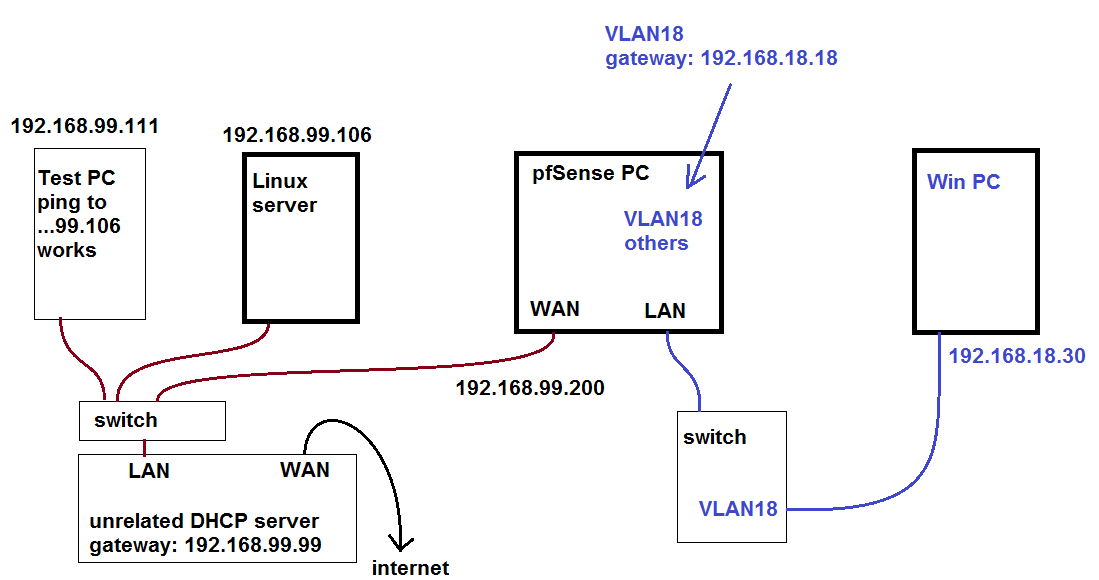
I access it from what I labeled as test PC (...99.111):
To get to the pfSense PC we've been talking about, I would go to 192.168.99.200 so that tells me that is the WAN IP.
-
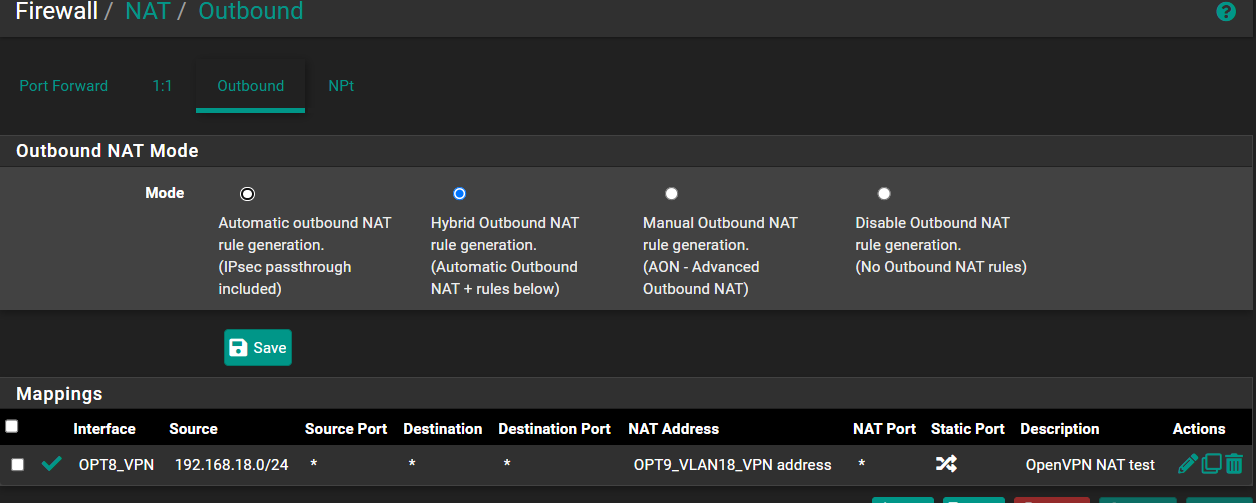
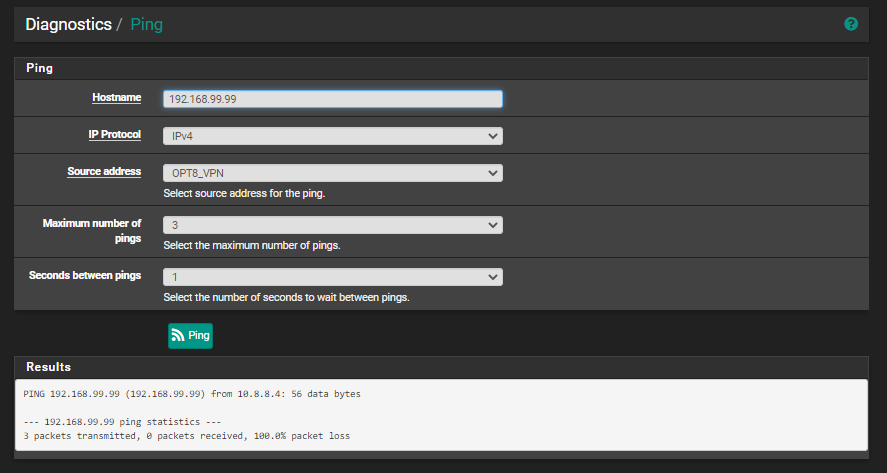
@stephenw10 I also wanted to share the details of the outbound NAT that is used for the VPN in case there is something in there.
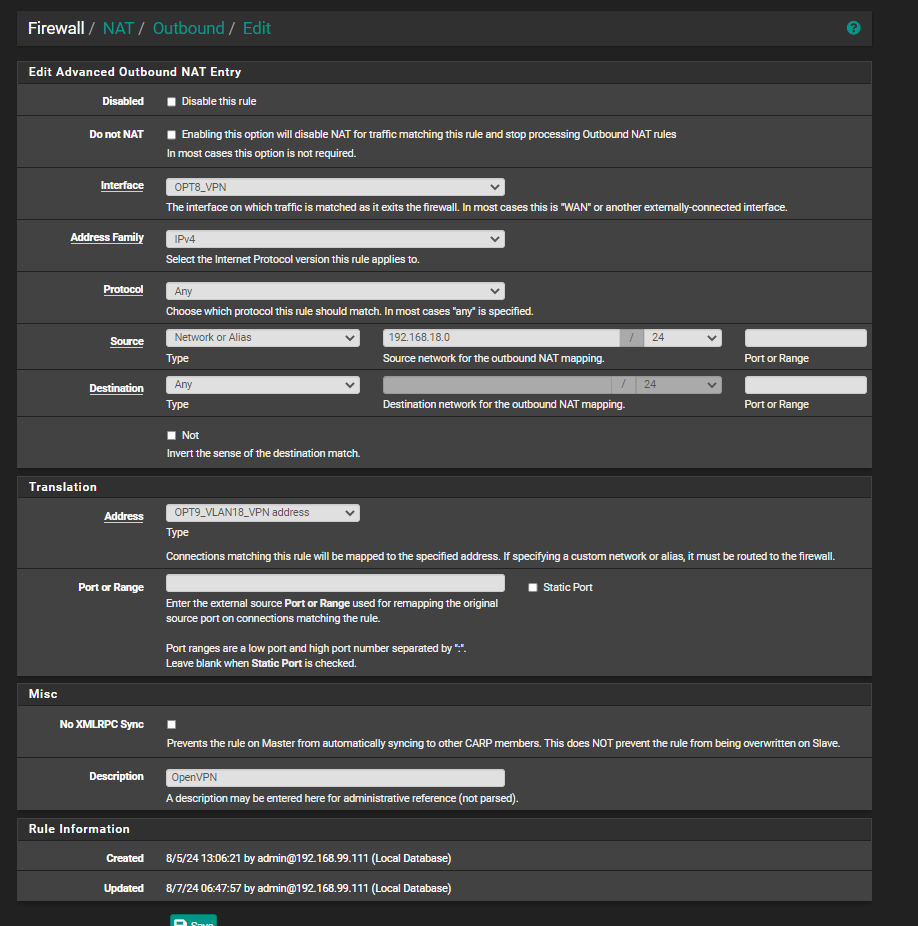
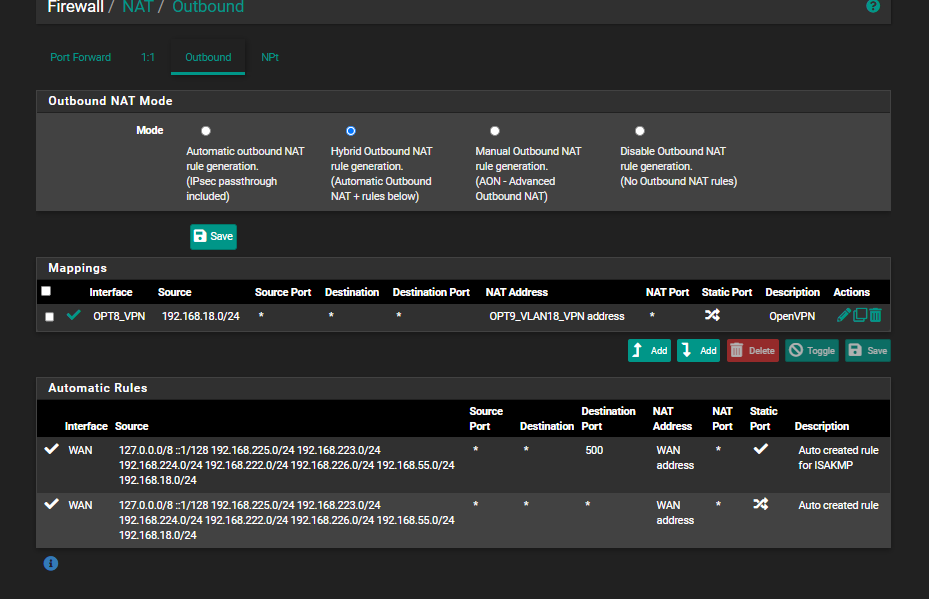
-
-
Ah I see. Yes that all looks OK. That outbound NAT rule is not in play here since traffic isn't leaving via the VPN.
It feels like the incoming rule on OPT9 is preventing it open the WAN state somehow. If you disable the policy routing rule and just pass traffic there without a gateway does it work?
-
I "grayed that out", I'm pretty sure that's what you mean.
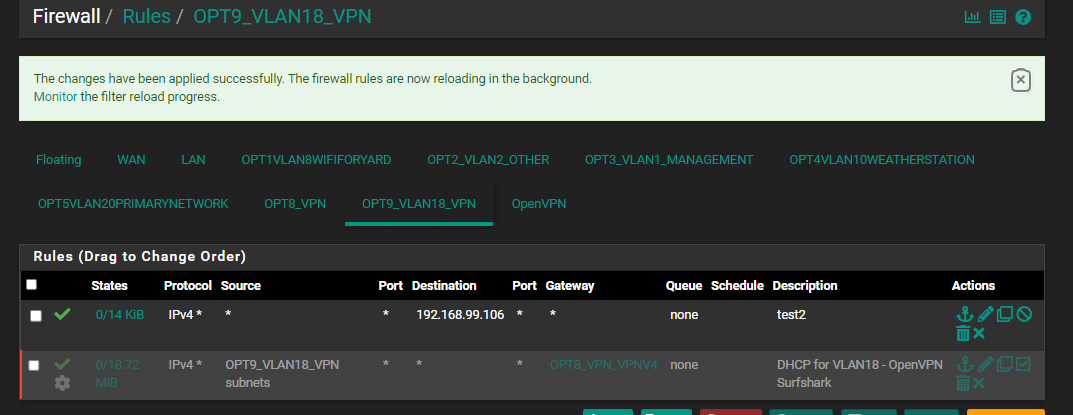
I was still having no luck and I tried something else which is another PC, coming in from VLAN20 and I put in the following rule:
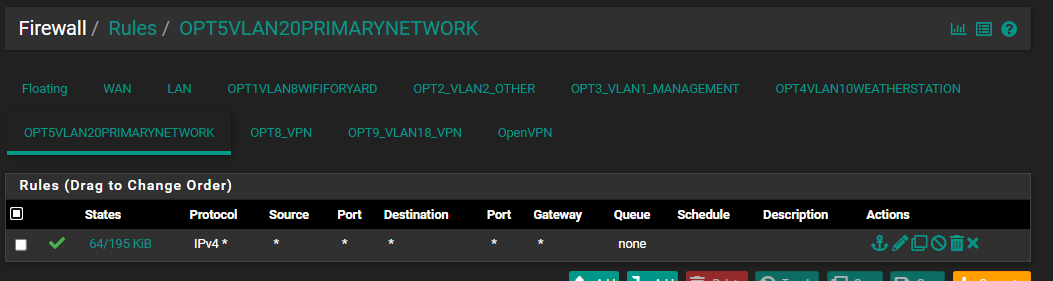
However I'm not able to access the internet, or ...99.99, or 99.106 and VLAN20 should have nothing to do with the VPN. Granted I should have tried this much sooner. I must have something else going on and I just feel awful for taking up your time. I still think it's related to pfSense and not something external like switches or parent router. I'm just going to keep trying stuff and if nothing works I will in the end reinstall pfSense from scratch, if it comes to that but there are lots of things I will try before that. Once I get it to work, I will let you know about it.
If there is anything you would like me to try by all means I'd be happy to but I don't want to take up anymore of your time and let me just say that I appreciate all your help so much! -
Same symptoms? No outbound state at all?
-
This post is deleted!