Need some routing assistance with pfSense, DMZ and WebSite
-
@stephenw10
Find below rules for WAN interface.
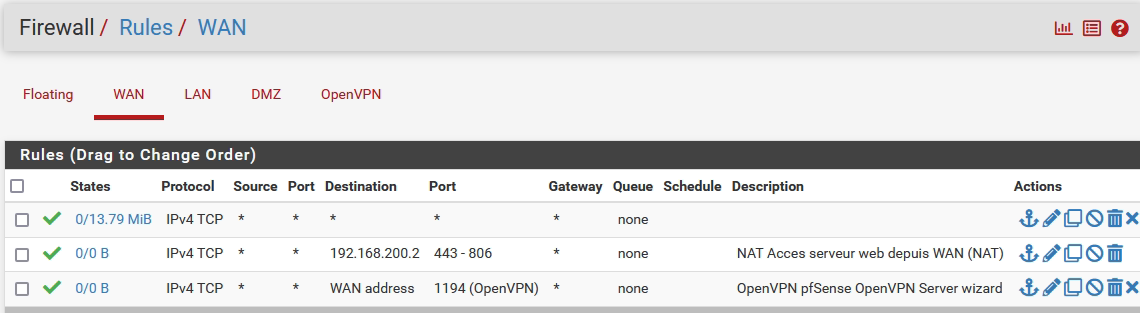
My web server is included inside DMZ network.
Thanks for helping.
Bet regards.
-
Ok, I assume you have the port forward rule too?
Check the state table when you're trying to connect. You should see states on WAN and DMZ if that traffic is arriving.
-
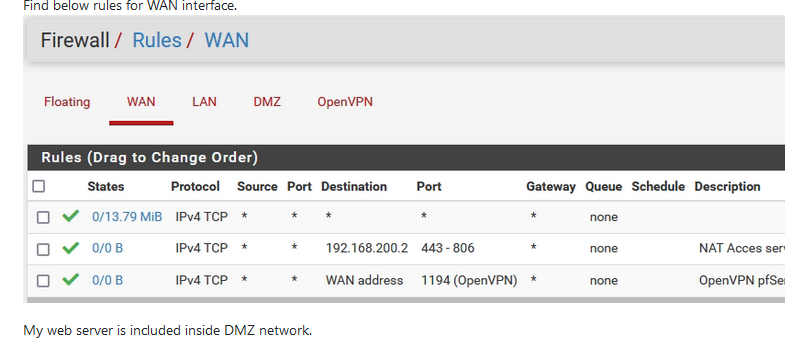
Get rid of your first rule.
- It's a very bad rule - no ... worse, as you've created your own nasty side effect :
- Traffic that would normally hit your second firewall rule, the one that open up TCP traffic with destination port 443 and 806 to you 'DMZ web server', is already 'captured' by the first rule ... that sends it 'no where'.
-
@Gertjan said in Need some routing assistance with pfSense, DMZ and WebSite:
Get rid of your first rule.
It's a very bad rule - no ... worse, as you've created your own nasty side effect :
Traffic that would normally hit your second firewall rule, the one that open up TCP traffic with destination port 443 and 806 to you 'DMZ web server', is already 'captured' by the first rule ... that sends it 'no where'.Even if I only the 2nd and 3rd rules is active, the problem is the same.
When I try to reach my website the error is ERR_CONNECTION_RESET.Best regards
-
Still my advise is to check the state table in Diag > States whilst trying to connect.
That will show you if the traffic even arrives at pfSense and if it does then if it's forwarded correctly.
-
@stephenw10 said in Need some routing assistance with pfSense, DMZ and WebSite:
Still my advise is to check the state table in Diag > States whilst trying to connect.
The traffic seems to arrive correctly. The web server has IP 192.168.200.2 (DMZ IP).
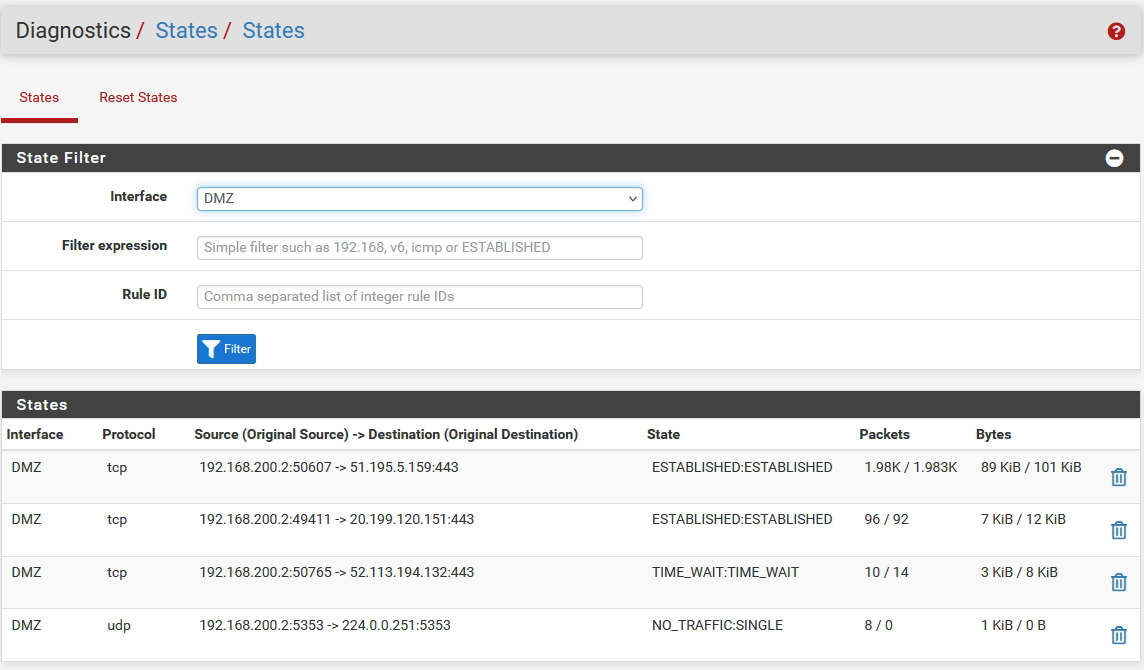
As the pfsense is connected to my ISP router, all traffic from 443 are redirected to port 443 on PfSense IP. Is it good ?
Many thanks in advance.
-
OK that's all outbound traffic from the server in the DMZ.
Set interfaces to
Allthere.Add
192.168.200.2to the Filter field and then check for states whilst you're trying to connect externally.You should see states on WAN and DMZ for that incoming traffic.
-
@stephenw10 Find below traffic.
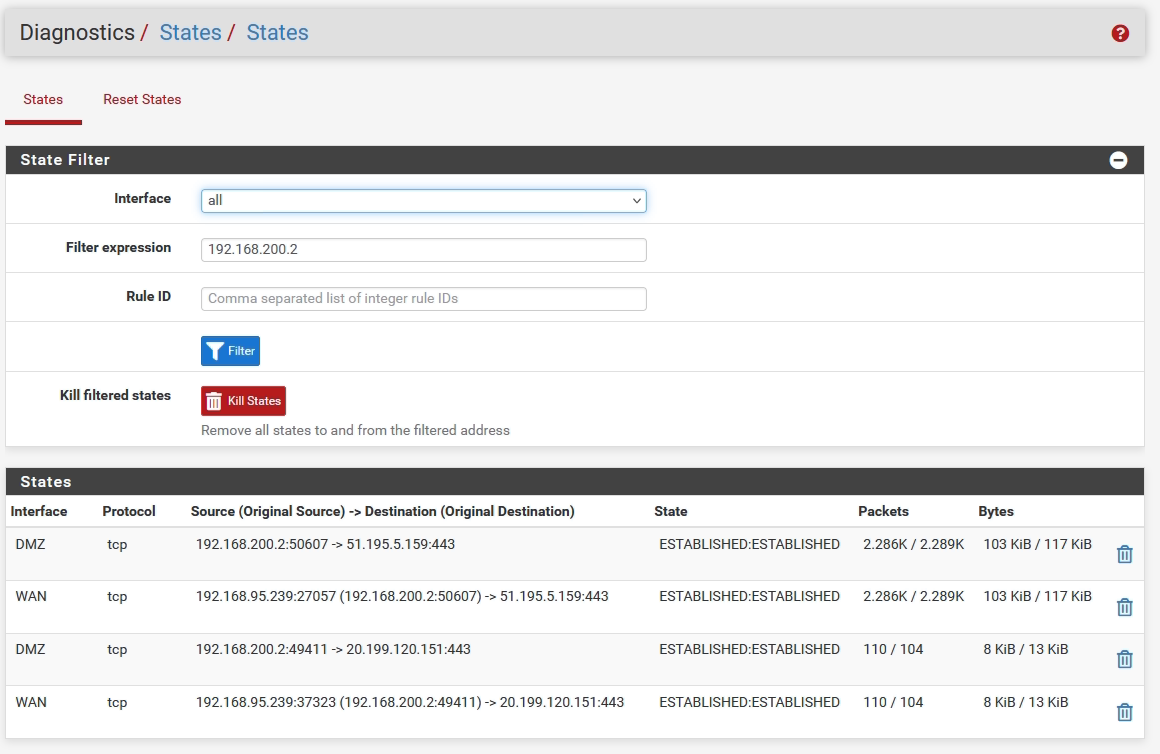
Is it possible to have the same view with dateTime ?
I don't know if it's important but my web site use php technology.
Best regards
-
Ok that shows NAT works outbound but those are still all outbound states.
Were you testing from some external device at the time? If so it looks like incoming traffic is not being passed to pfSense.
-
@stephenw10 Find below traffic.

Is it possible to have the same view with dateTime ?
I don't know if it's important but my web site use php technology.
Best regards
-
Ok, try this: Filter by the external IP address you are testing from instead. You should see that traffic open states inbound.
-
@ILO_EWS this tells me your behind a double nat
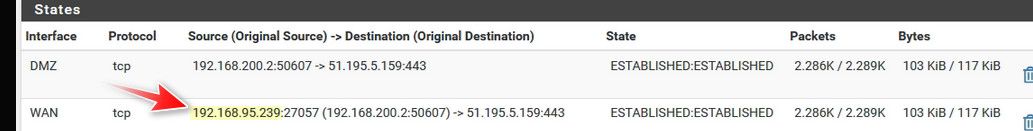
Your lan traffic going out the wan was natted to a 192.168.95.239 address, your wan IP.. So if you want to forward something from out on the internet to something behind pfsense you would first have to forward on whats in front of pfsense to pfsense wan IP.
From your own statement, your clearly behind a double nat
Internet <--> Router 192.168.95.0/24 <--> pfSense <--> LAN 192.168.77.0/24
On that router that is connected to the internet, you need to forward whatever traffic you want to get to something behind pfsense to pfsense wan, from your state table that would be the 192.168.95.239 IP.
Then on pfsense you forward to what is behind pfsense. But until you forward on your router - pfsense isn't ever going to see anything to forward.
-
@ILO_EWS said in Need some routing assistance with pfSense, DMZ and WebSite:
As the pfsense is connected to my ISP router, all traffic from 443 are redirected to port 443 on PfSense IP.
As long as that's true it should work.
-
@stephenw10 if that was true then he would see that traffic hit his pfsense wan, be it he had any ports working or not via sniff.
-
@johnpoz
So in this case, do you think that the problem is on the configuration of my ISP routeur ?
Best regards -
@ILO_EWS go to like can you see me . org and send some traffic to 443 while you're doing a packet capture on pfsense for your wan IP and port 443 do you see anything with destination of pfsense IP to 443..
if pfsense doesn't see inbound to its 443 then no it can not forward anything.. Also that any any rule isn't right.. When you create your port forward it should auto create your wan firewall rule to allow 443 to your host your forwarding to IP.
-
@johnpoz said in Need some routing assistance with pfSense, DMZ and WebSite:
go to like can you see me . org and send some traffic to 443 while you're doing a packet capture on pfsense for your wan IP and port 443 do you see anything with destination of pfsense IP to 443..
if pfsense doesn't see inbound to its 443 then no it can not forward anything.. Also that any any rule isn't right.. When you create your port forward it should auto create your wan firewall rule to allow 443 to your host your forwarding to IP.
When I launch a test on this website, this error appear
Error: I could not see your service on 82.66.xxx.xxx on port (443)
Reason: Connection timed outBest regards
-
@ILO_EWS but that doesn't tell you if even got to pfsense.. You need to do a packet capture to see if it even got to pfsense, or yeah no duh its not going to work and yeah it would time out.
edit: example... I don't have anything listening on 666, no forwards, etc.. but if I send traffic pfsense still sees it.. And yeah since no answer it would time out
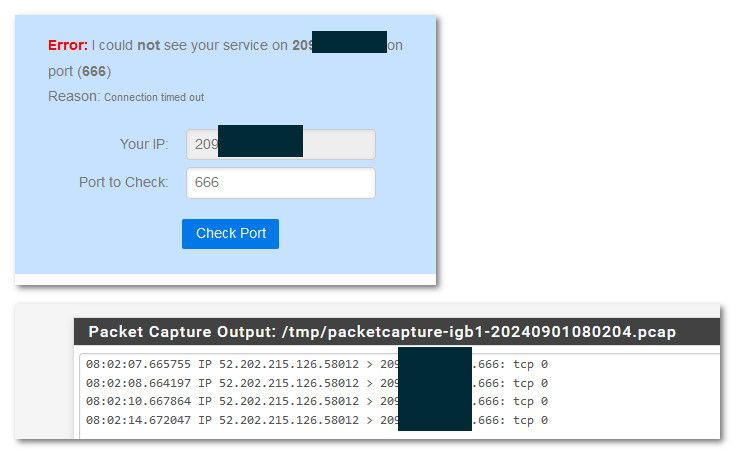
edit: what does your router in front of pfsense show for its wan, for all we know its a cgnat IP and no forwards are ever going to work.
-
Yup, the result is not important. The test is that the traffic arrives at the pfSense WAN. So in the pcap as suggested or openning states in the state table.
-
@ILO_EWS
and @stephenw10 :
Something did come on :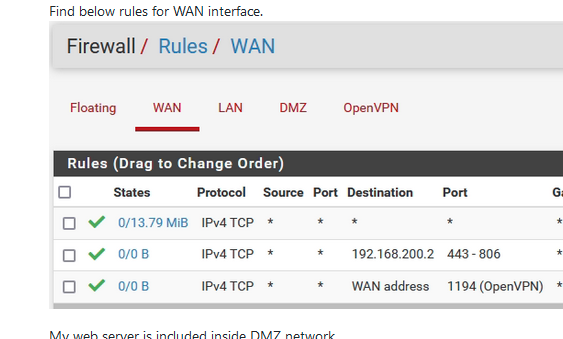
The first rule - that should have been removed by now - clearly shows TCP traffic was entering = coming from the Internet.
With that first rule removed, the second and third now have chance to work.so I presumed : no cgnat horrors.
When testing, the counters "0/0 B" should not stay at 0/0. 0/0 means nothing arrivd at the WAN interface that matches the rule.
For fast NAT, or whatever, testing, no need to packet capture, or look at the state table : look at your firewall rues, and see if they get used/applied.Also, ISP router, the one in front of pfSEnse, can have DMZ look alike options.
Don't use them.
Handle incoming incoming connection the old classic way :
You have to NAT a port (for your web server who lives at the network called DMZ) on pfSense.
You have to do the same thing on the ISP router : NAT that port to the pfSense WAN IP.