ATT Internet AIr
-
Ok, so it's passing the LAN interface. That should be fine for anything that uses it. That one client is hard coded to use 8.8.8.8.
The root issue here though still seems to be that Unbound in pfSense is not using the WAN connection when WAN2 is down. I think you will need to test on site though.
Try setting up another failover group that has WAN as the tier1 gateway. Then try setting that as system default and retest. In that situation Unbound should already be using WAN when WAN2 is disconnected and should continue to work. It should also failover to WAN2.
-
@stephenw10
Back on site
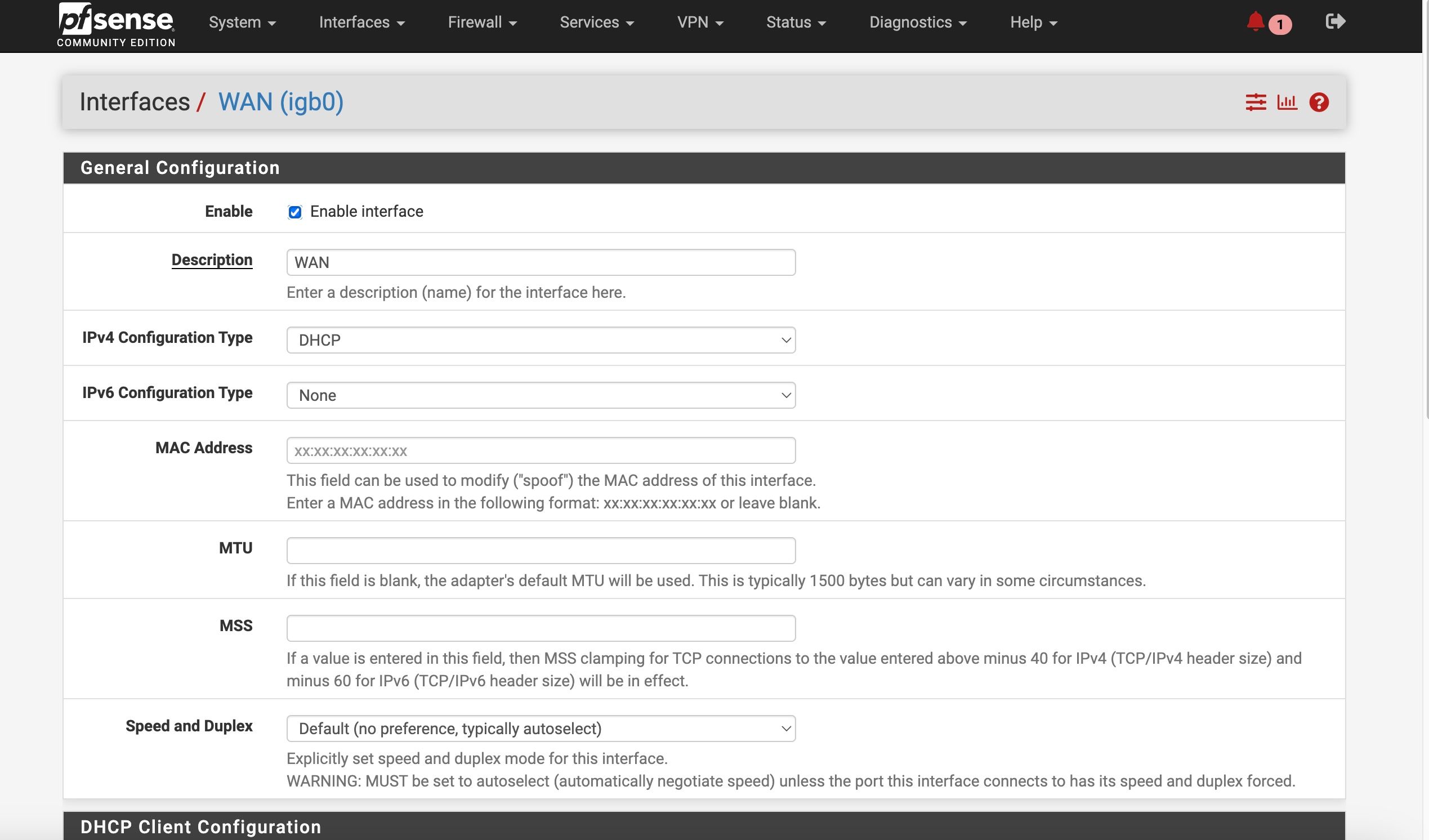
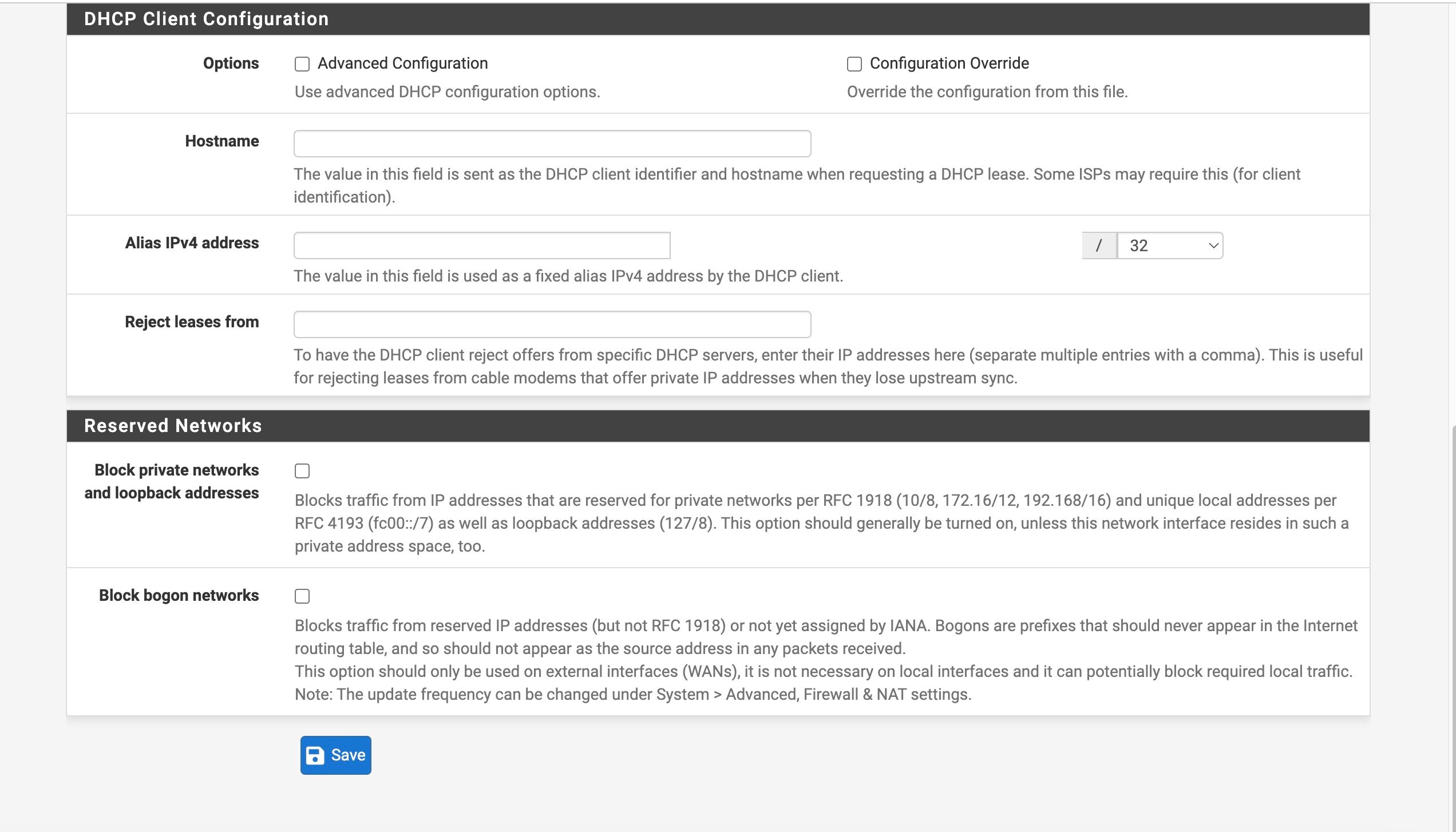
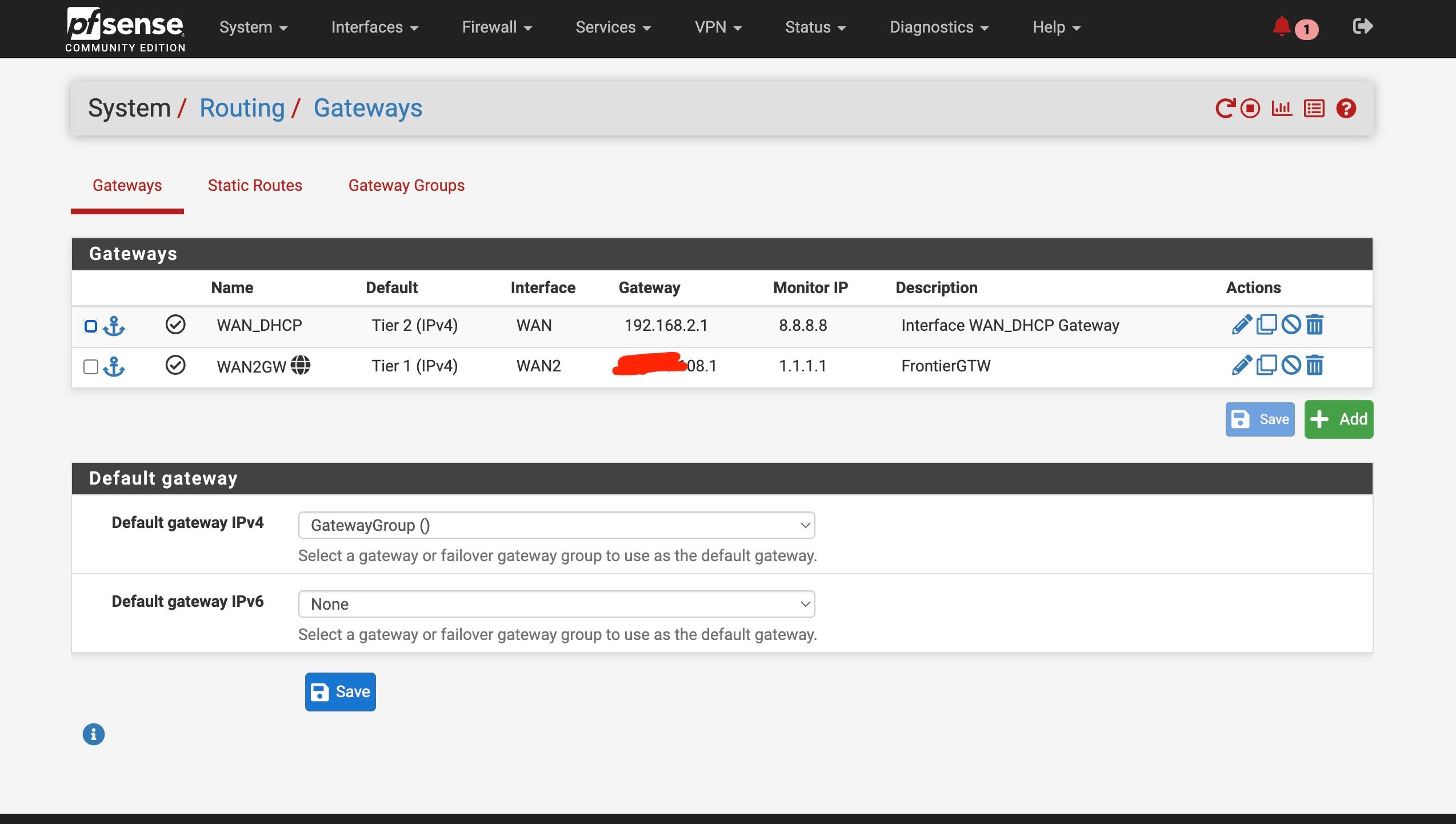
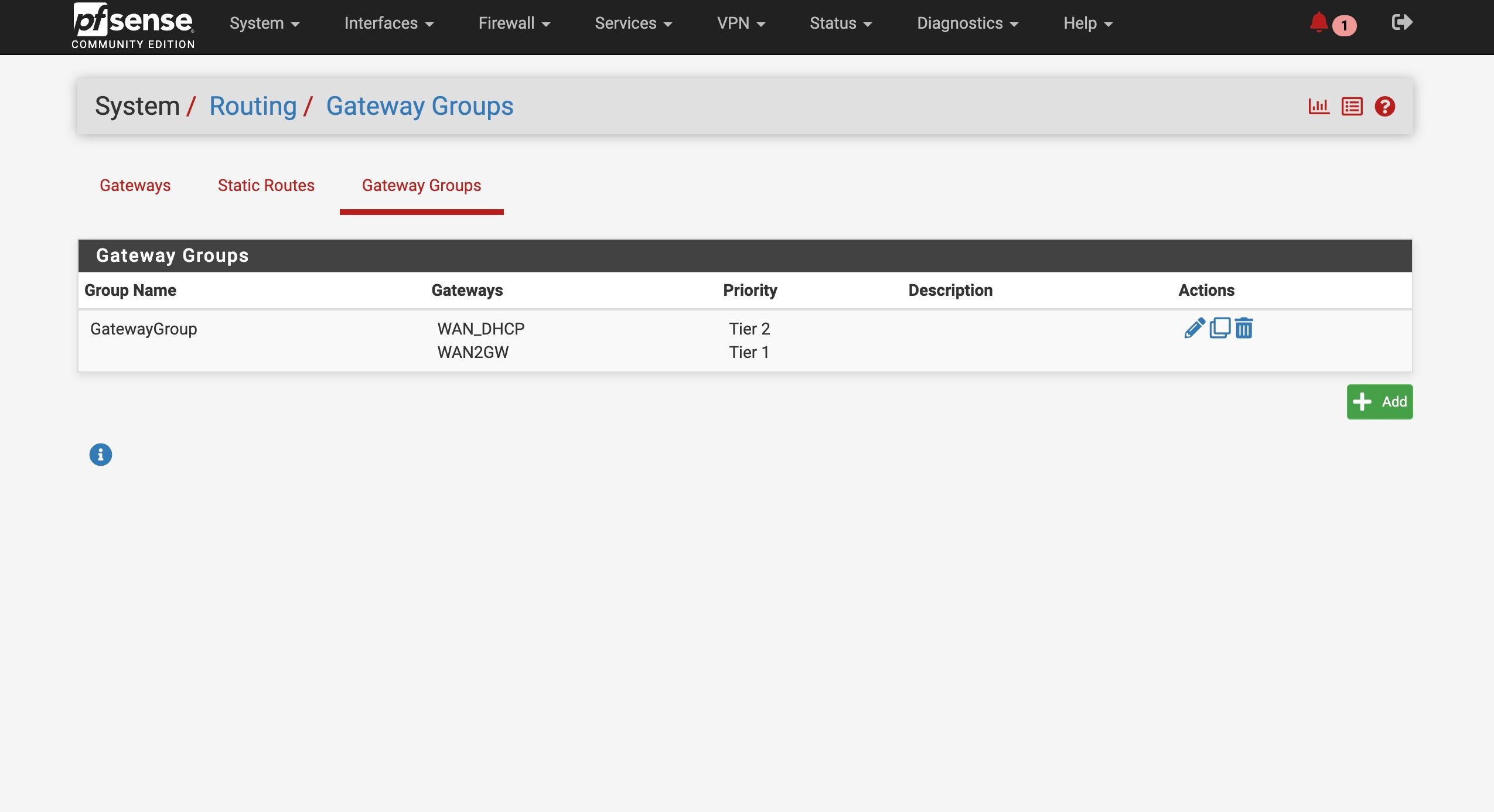
Set up the second test gateway group
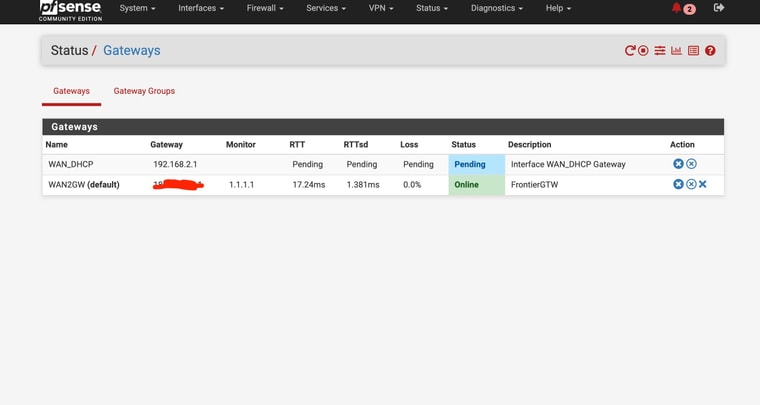
WAN as Tier 1 , WAN2 as tier 2When I set the test group as default, it switched to WAN ——- no internet/ DNS
Switched back to other gateway, internet/DNS returned without reboot
-
Hmm, were you able to see DNS traffic on WAN in the states?
Starts to look like the WAN connection just blocks or intercepts DNS for some reason.
You can try to test that directly from the pfSense command line with something like:
dig @8.8.8.8 netgate.com -b 192.168.2.2 -
@stephenw10
No joy directly from command line!If I knew for sure another failover device/method would for sure work I would consider returning the Internet Air devices - lol
Now it's just irritating that this is so difficult (esp with expert help like you)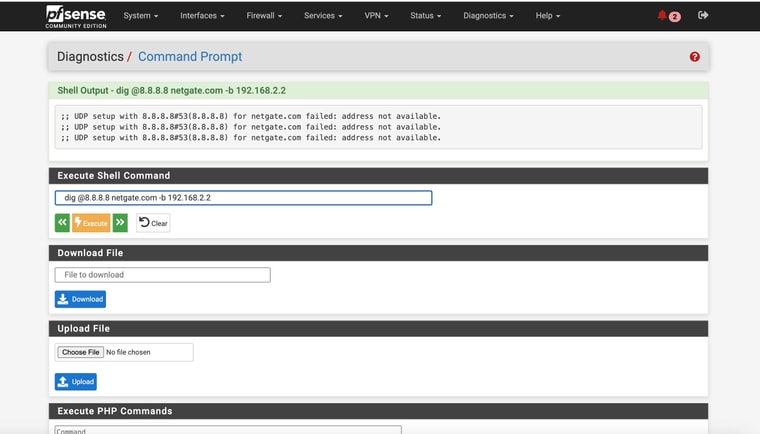
-
Did the WAN IP change from 192.168.2.2? By binding to that address the query is forced to use the WAN.
-
@stephenw10
OMG, sorry
I'll have to get back on-site this afternoon - looks like the WAN device went offline or something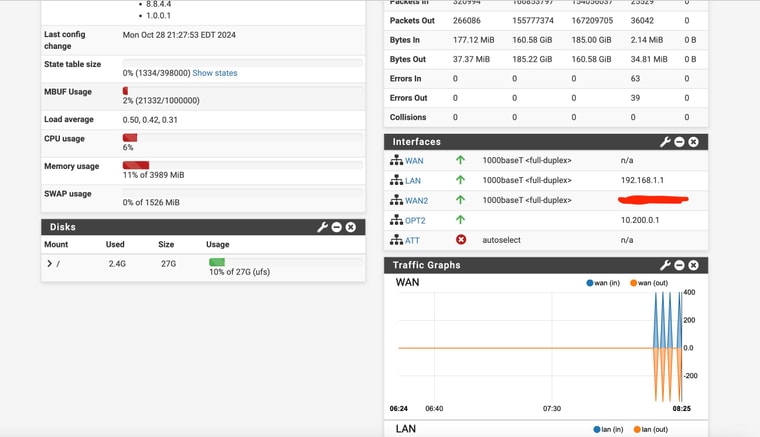
-
Ah, that would do it.

-
@stephenw10
Got back on site and restarted the WAN
It is back up and going on 192.168.2.2
If I do the test gateway group , I am still losing DNS/Internet with WAN as Tier 1 and primary internetBut I did get differnt result with the command line
see below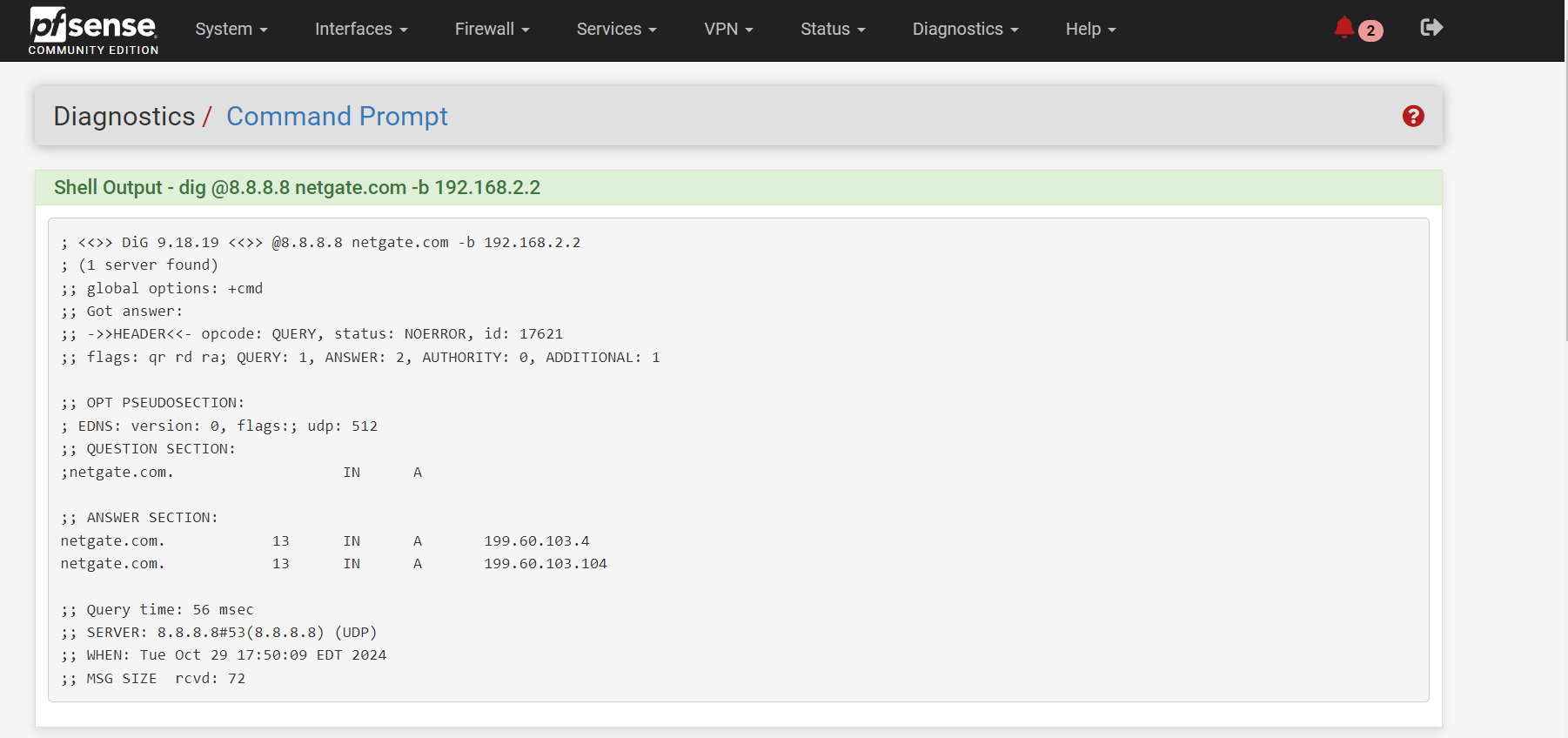
-
Hmm, well that looks OK. Try setting Unbound (DNS Resolver) to forwarding mode so it uses the configured remote DNS server directly. You should also disable DNSSec whilst testing that.
-
Just wanted to chime in here and mention that I have been using pfSense with AT&T Internet Air in failover configuration for about a year now without issues (primary WAN is fiber). During that time I have not observed any evidence that DNS might be intercepted somehow on the Internet Air side - DNS is working fine for the failover gateway group I've got setup with Unbound in resolver mode. So I think in this case it's still a misconfiguration somewhere in the pfSense settings.
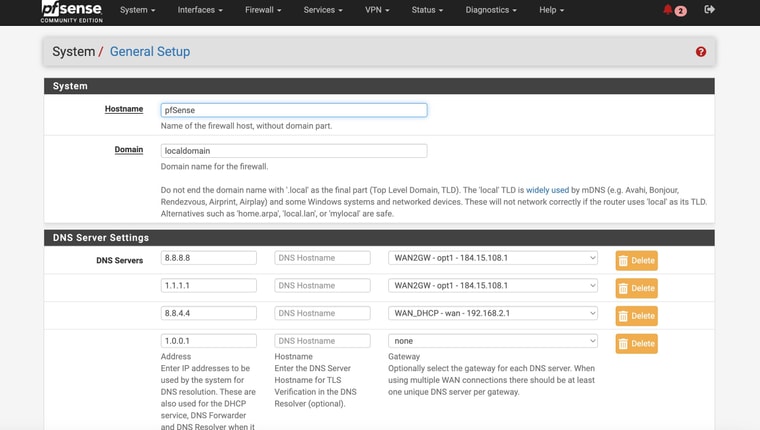
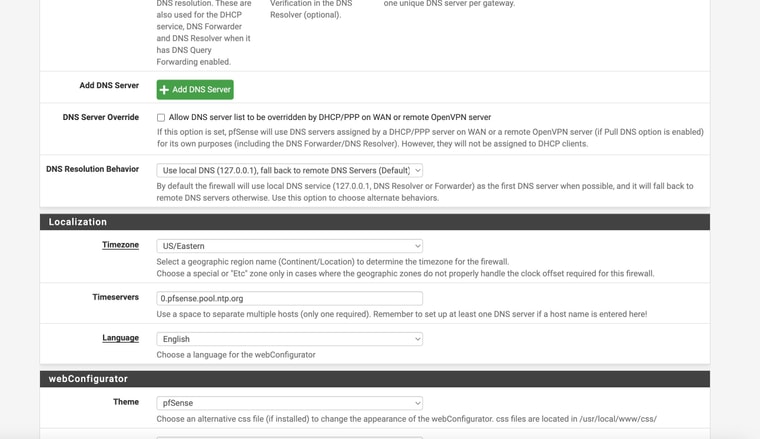
What do you have set for
DNS Server OverrideandDNS Resolution Behaviorunder General Setup?Also, this section in the pfsense docs will be good to review if you're switching over from resolver to forwarder and using multiple wan connections:
https://docs.netgate.com/pfsense/en/latest/multiwan/interfaces-and-dns.html#dns-configuration
Hope this helps.
-
@stephenw10 @tman222
Ok so I'm not completely sure which setting fixed things BUT by setting DNS Resolver to forwarding and disabling DNSSec - the WAN (ATT Internet Ait ) Internet worked when enabling the Test Gateway group1@tman222
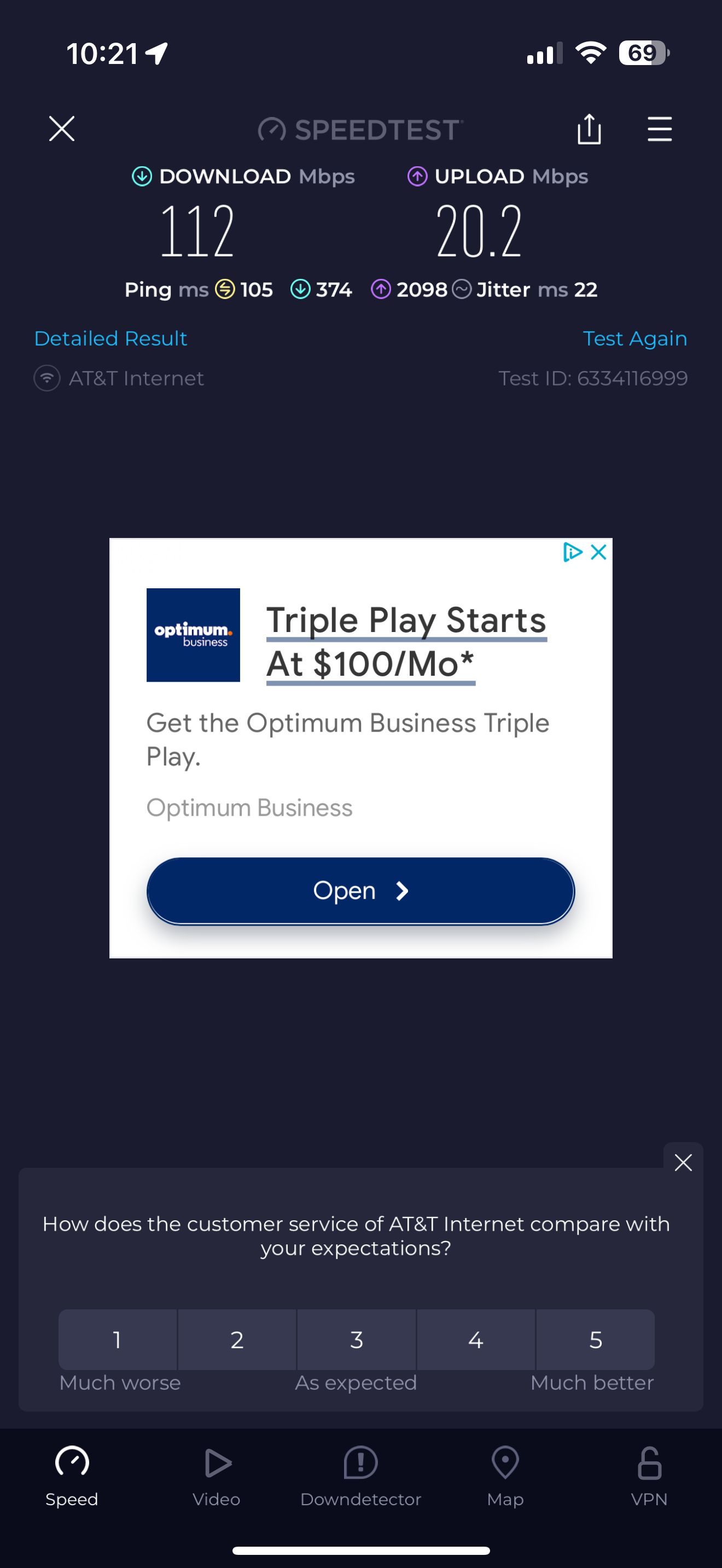
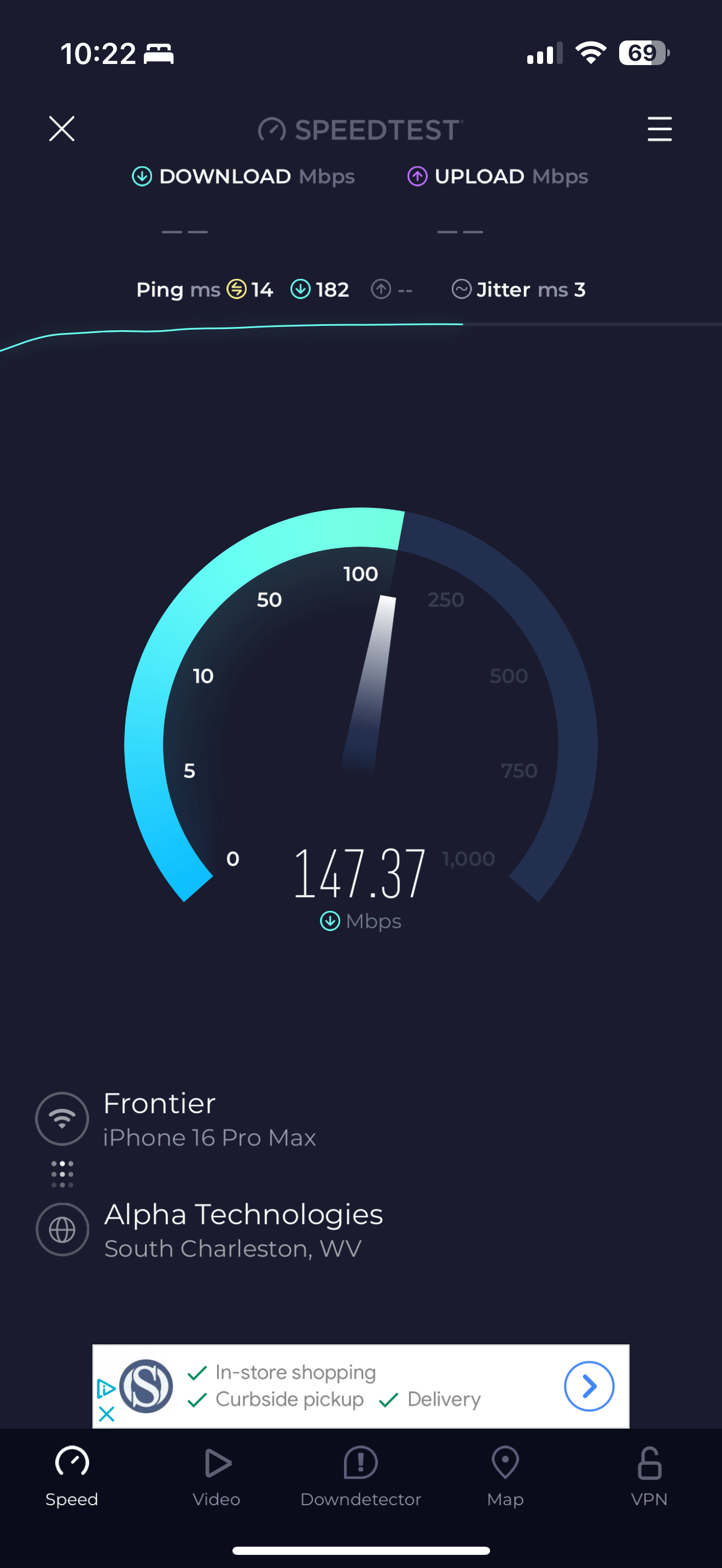
I attached screnshots of my settings - how does that compare to yours? Do you have the Internet Air setup on a seperate "local" subnet like I do? Shame it doesn't have a full "bridge mode". Also I could not seemingly get DMZ to work in that with it enabled my pfsense interface still shows the local IP address - it doesn't pass through the public IPThe screeshots show the active test gateway. The command line results AND the succesful "speedtest" (shich was never accesible before) with the test gateway and then the regular gateway. AND my general setup settings page for @tman222 question
How should I permanenetly set things ? Any explanation or thoughts on what is happening?
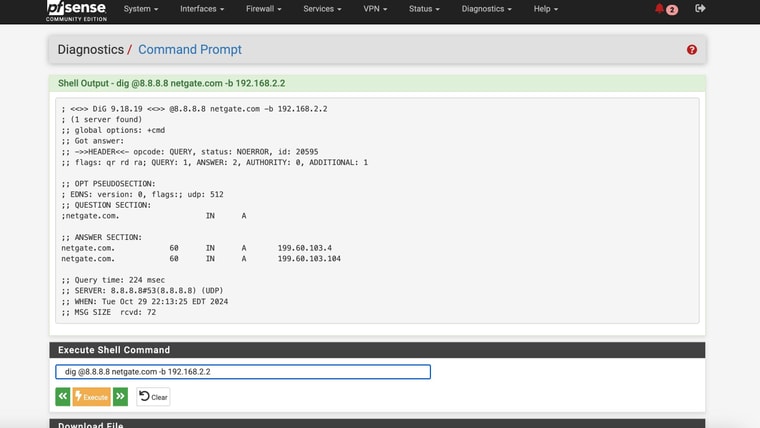
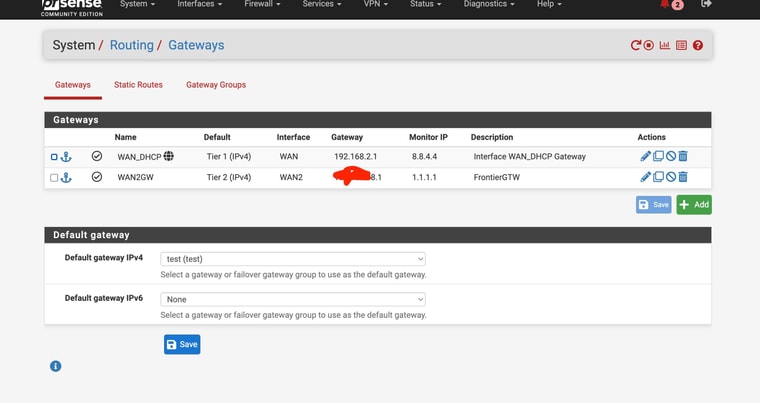
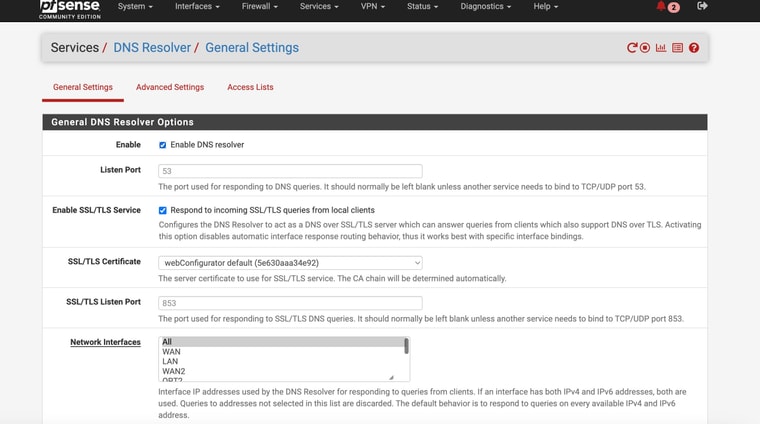
-
-
-
@ahole4sure - glad you got things up and running.
My settings are similar except that I'm using Unbound in resolver mode so I have no additional DNS Servers defined under General Setup > DNS Server Settings.
Which gateway did you end up getting from AT&T for the Internet Air service? The one I received does allow for IP passthrough so I can get a public IP on the pfSense side.
Hope this helps.
-
Mmm, interesting. Yeah it should work is resolving mode behind a failover gateway group as @tman222 shows. Curious that it's failing for you.
You should not have a gateway set against 8.8.8.8 so it's available for use on either WAN. Especially since you have at least one device hard coded to use that directly.
-
@stephenw10
I guess I’m confused a little
Maybe even with terminologyI have DNS Resolver enabled. I never disabled it. I just enabled “forwarding mode” in the DNS Resolver settings.
And another thing I don’t understand is that in the General Setup page I have WAN2 supposedly hardcoded to use 8.8.8.8, and WAN to use 8.8.4.4
But based on the command line results 192.168.2.2 used 8.8.8.8 to resolve the addressSo I’m confused as to what is happening
AND how I should have things setup?? -
@tman222
Yeah I am a bit confused because I have DNS Reolver enabled - but under those settings I have check to use DNS Forwarding mode -- so I guess I don't understand what that means??Attached is the model Internet Air that I am using.
In the settings I do have an option to set DMZ to a particular address and to "allow IP passthrough" but it doesn't seem to be actually doing the passthrough??
Do you have actual settings like a "bridge mode" - could you possibly send a screenshot of your Internet Air settings page where you are able to accomplish "passthrough"?
-
Unbound in it's default config acts as a DNS resolver. That means it queries the DNS root servers directly. If you run a DNS leak test whilst using that it will show your WAN IP address.
When you set it in forwarding mode (or use the separate DNS forwardibg service, dnsmasq) queries from LAN clients are forwarded to external DNS servers. Either those configured in general setup or passed by your ISP via DHCP. There they may be forwarded again If you run a DNS leak test when running that it will show the public IP of the final server that resoles queries.
Both modes should work behind failover WANs.
-
@stephenw10
I guess I'm still confused since "forwarding" is still a sub-section under the main page of DNS Resolver and is a sub-setting under enabling DNS Resolver
From the explanantion as I understand it - it's like the setting page allows you to enable unbound or DNS Resolver and then bypass it (or disable it) all on the same page ??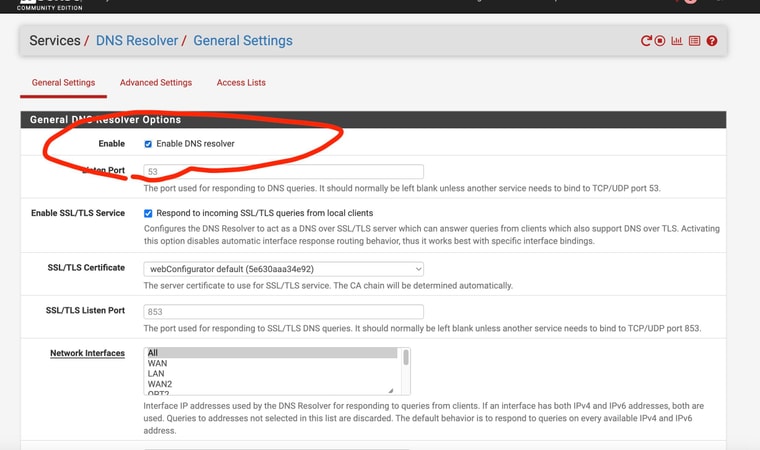
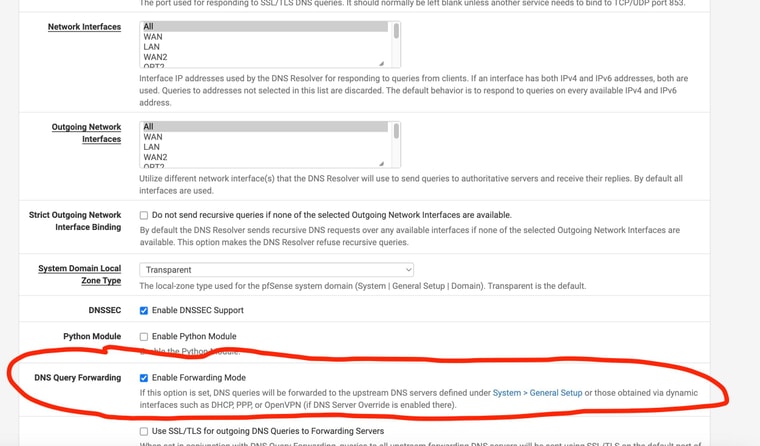
-
There are two DNS services that can be enabled in pSense.
The 'DNS Resolver' is Unbound and that resolves directly but can be set to forward also.
The 'DNS Forwarder' is dnsmasq. It's what pfSense used by default in much older versions and is included for compatibility. It can only run as forwarder.