Potential DNS Rebind attack detected on my local network
-
@comet424 said in Potential DNS Rebind attack detected on my local network:
@stephenw10
this is the result of the dig @192.168.0.1 tardis.home.arpa.Sorry that last . was outside the quote! Muscle memory forced me to type it.

The command should be:
dig @192.168.0.1 tardis.home.arpa -
@stephenw10 that wouldn't matter, and dig does it by default anyway unlike nslookup
-
Given the presence of Nord and PIA do you have Unbound in forwarding mode to other upstream servers over the VPN?
None of that should matter though, Unbound should still respond with hostoverrides in place.
-
@stephenw10
@johnpoz
so for custom options in dns resolver i haveserver: local-zone: "windowsupdate.com" redirect local-data: "windowsupdate.com 86400 IN A 192.168.0.32" server: local-zone: "microsoft.com.edgesuite.net" redirect local-data: "microsoft.com.edgesuite.net 86400 IN A 192.168.0.32" server: local-zone: "update.microsoft.com" redirect local-data: "update.microsoft.com 86400 IN A 192.168.0.32" server: local-zone: "do.dsp.mp.microsoft.com" redirect local-data: "do.dsp.mp.microsoft.com 86400 IN A 192.168.0.32" server: local-zone: "dl.delivery.mp.microsoft.com" redirect local-data: "dl.delivery.mp.microsoft.com 86400 IN A 192.168.0.32" server: local-zone: "cdn.blizzard.com" redirect local-data: "cdn.blizzard.com 86400 IN A 192.168.0.32" server: private-domain: "home.arpa" server:include: /var/unbound/pfb_dnsbl.*confmy host over ride is
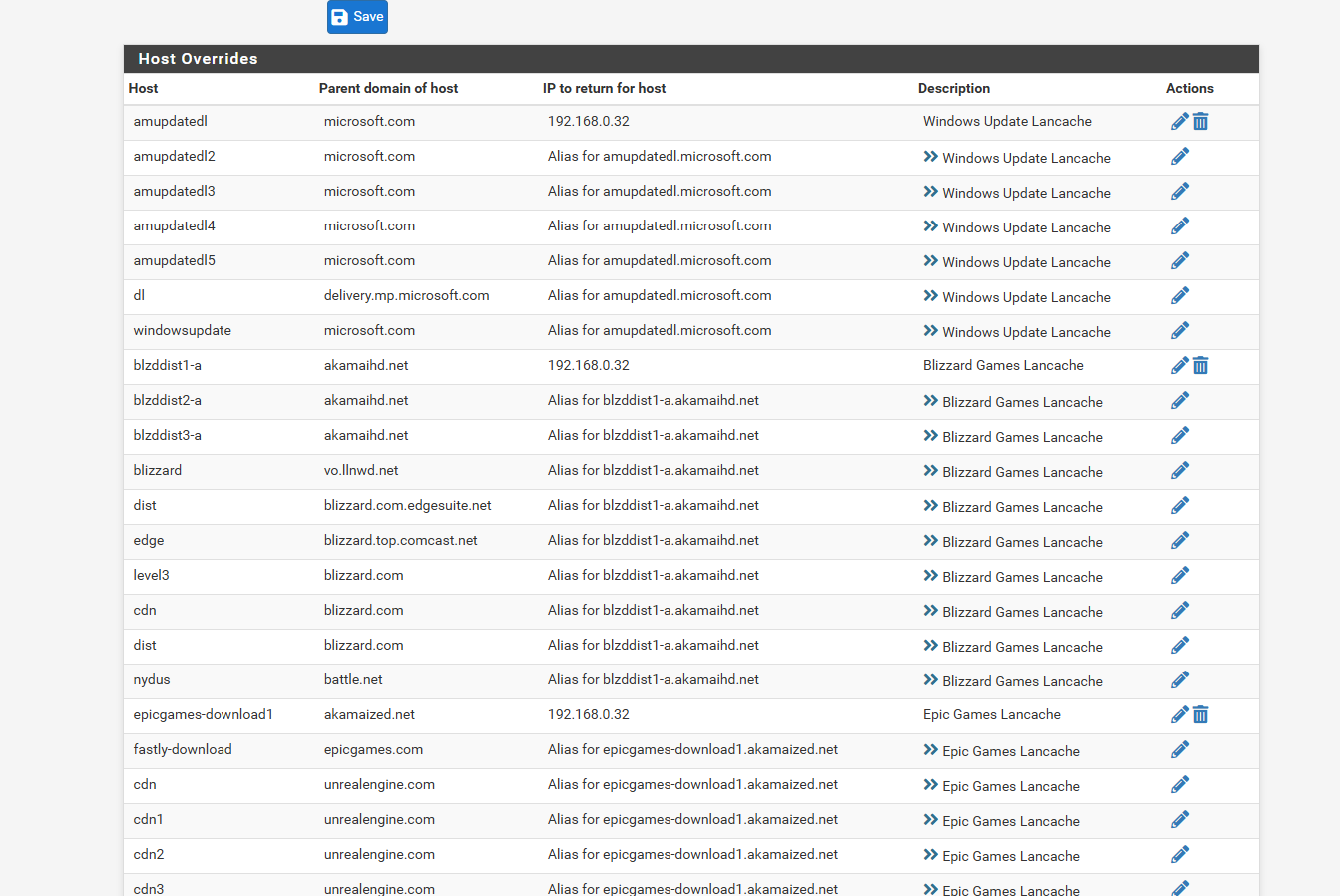
the
dig @192.168.0.1 tardis.home.arpa command without the extra .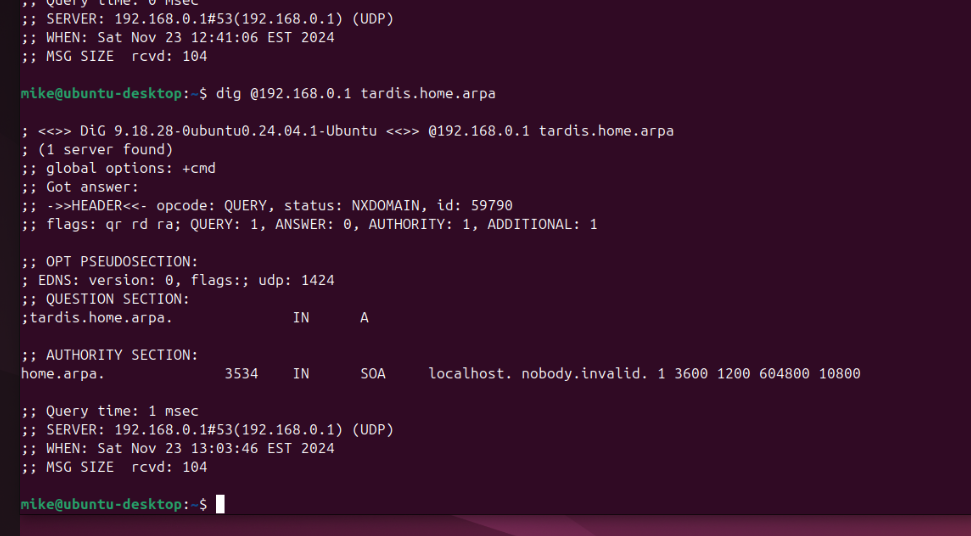
dns resolver i set to all all so i can then do the bypass routing policy on Lan
i disabled NordVPN and switched over to PIA they do different things... like no proper video for PIA but one had NAT just 192.168.0.0 and another used the pia for 1::128 and those other generated in NAT table so i dubbed them like i read in a PIA setup tutorial.. its like there is different ways to set up there vpn..
i dont use the DNS forwarder... as it wasnt part of the setup of PIA or norvpn in the past.. and i think i read or watched you cvan have dns resolver and forwarder same time?
only other VPN i use is Site to Site to my sisters Pfsense so i can access her network like it was here.. and i have to re add remote access...
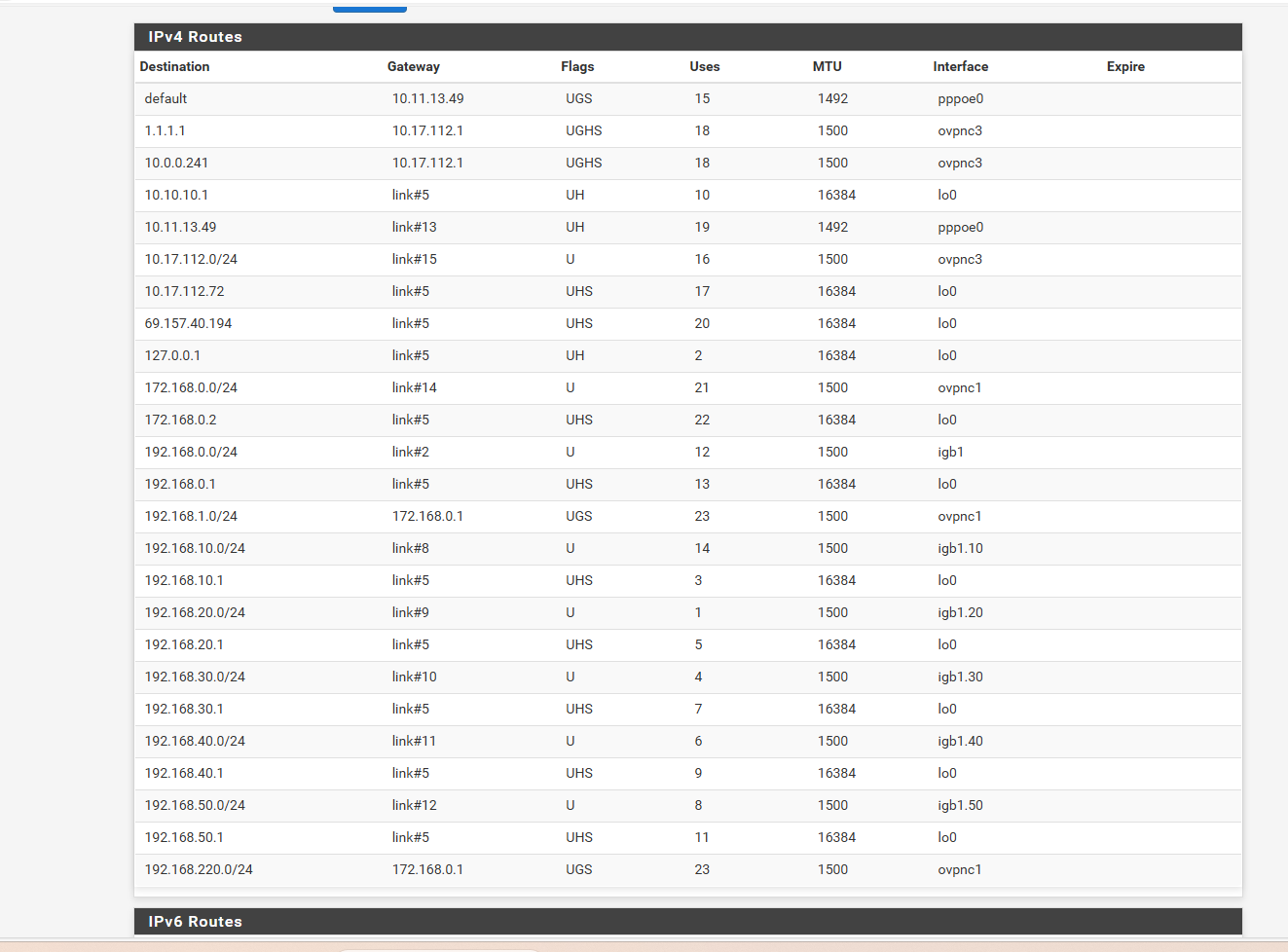
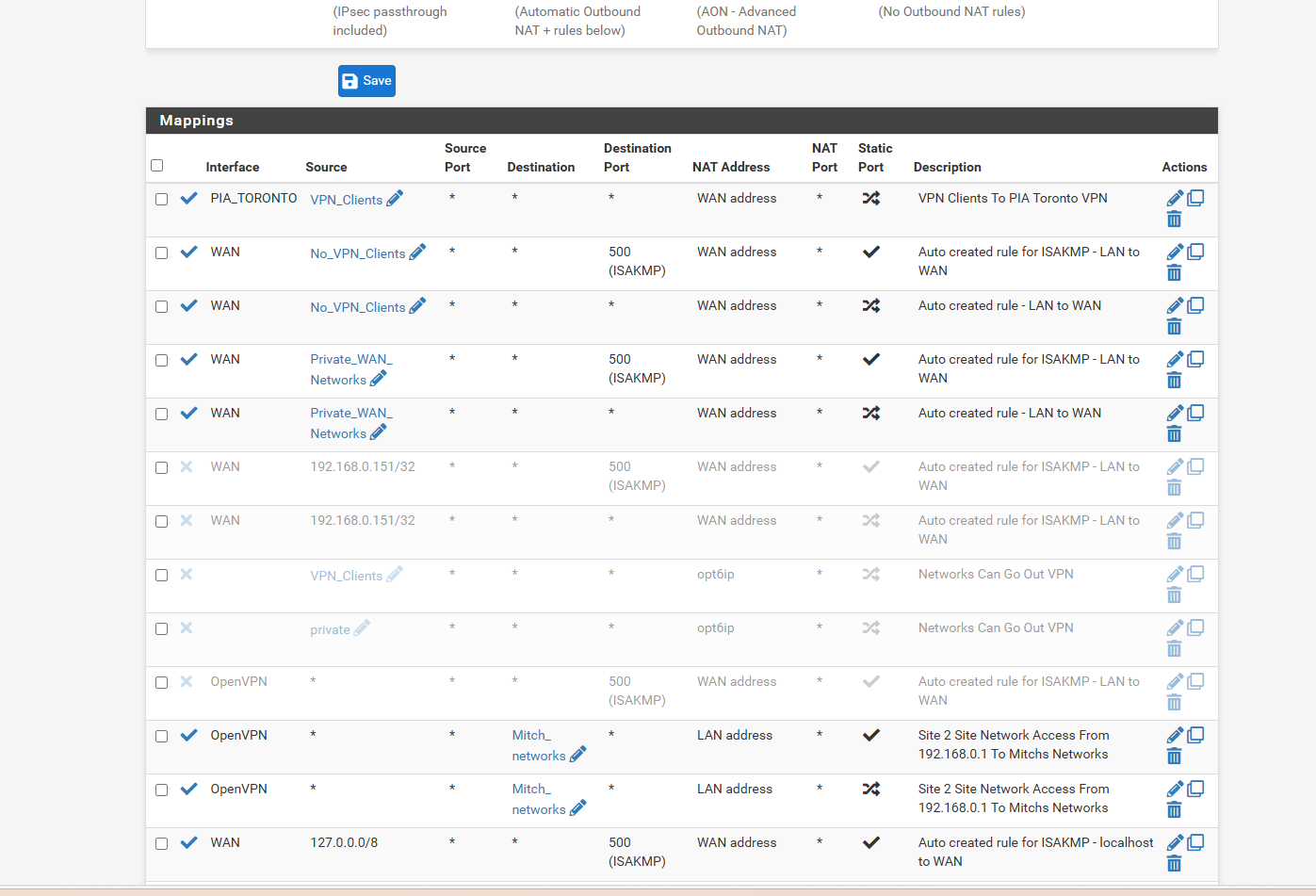
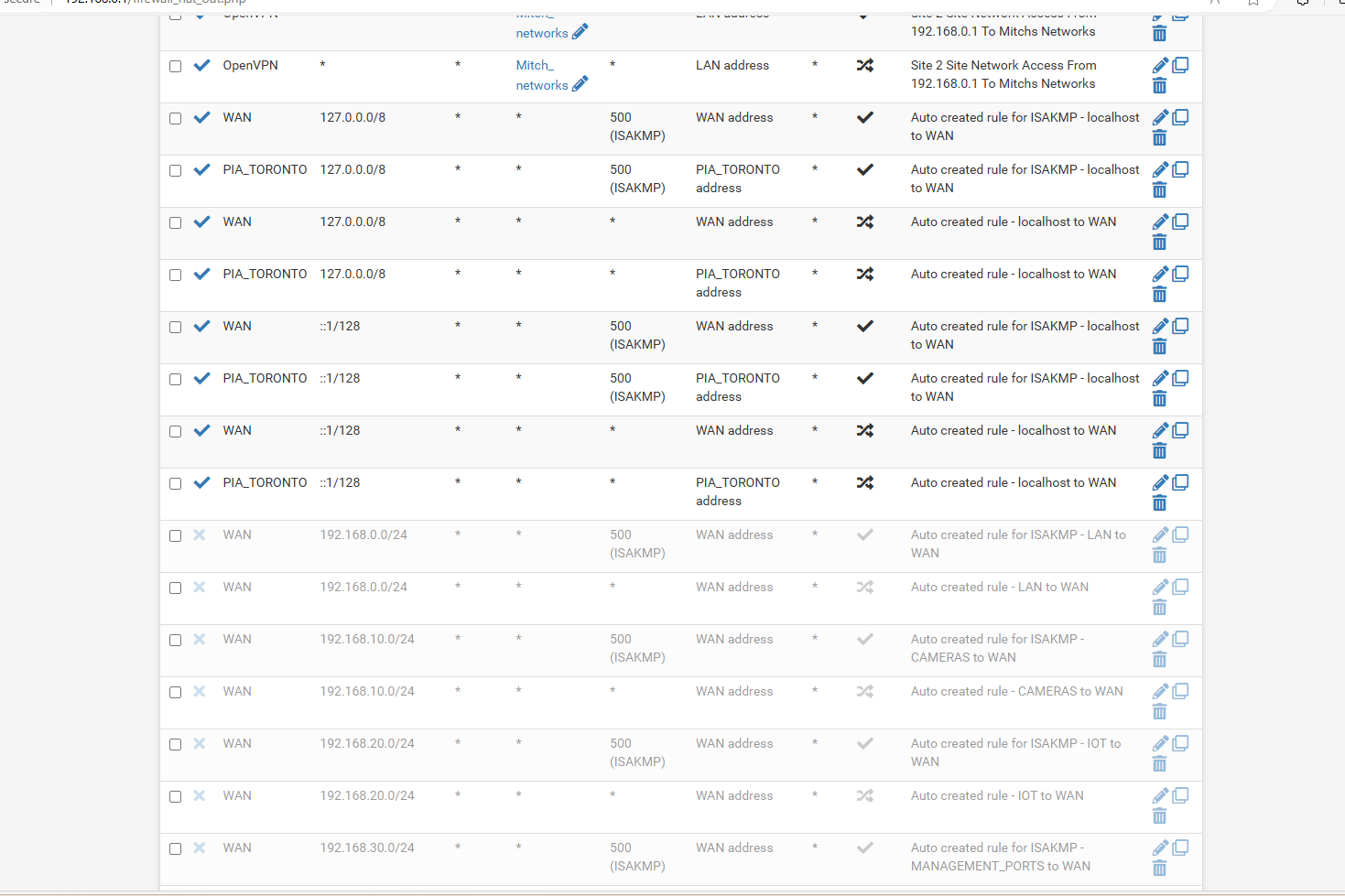
and this is my LAN rules
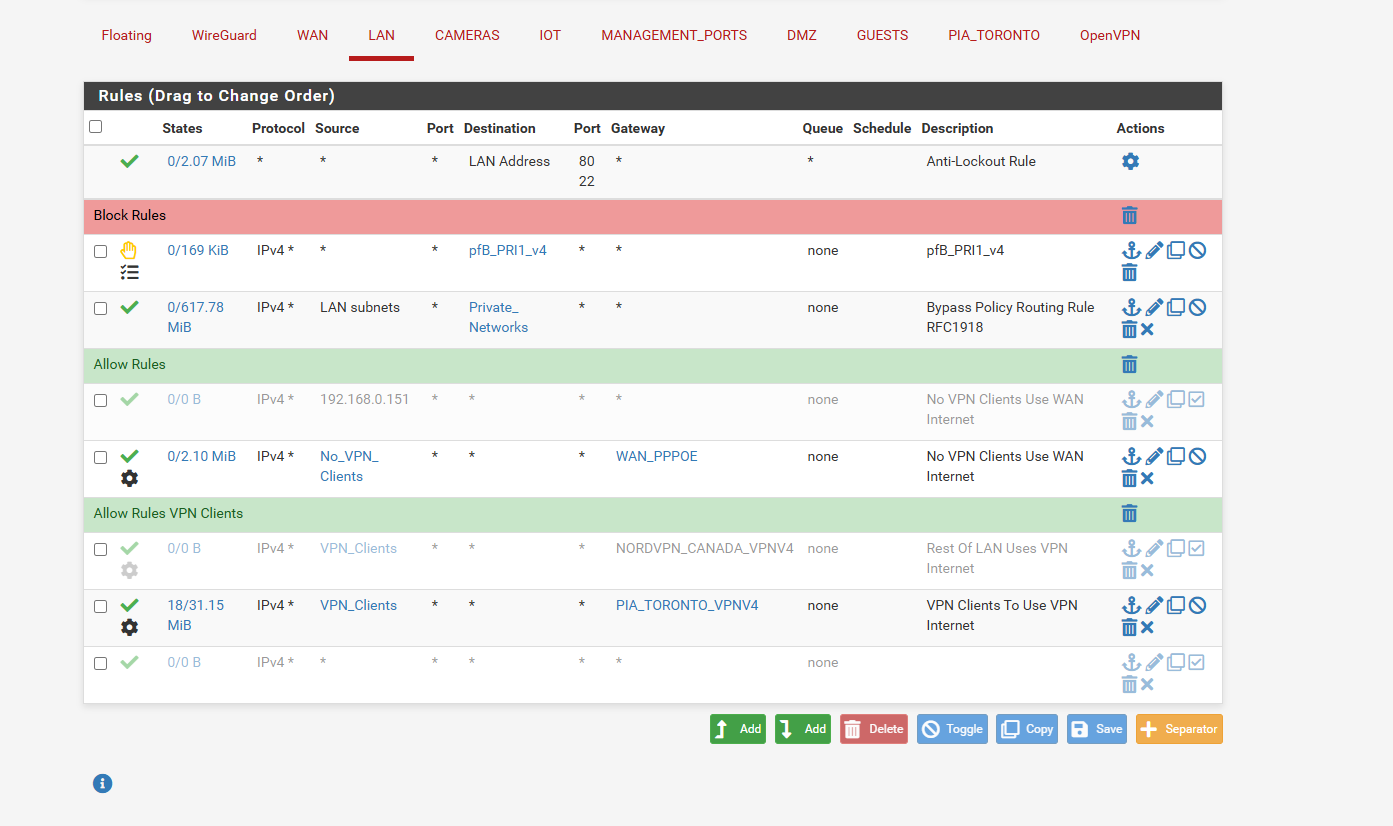
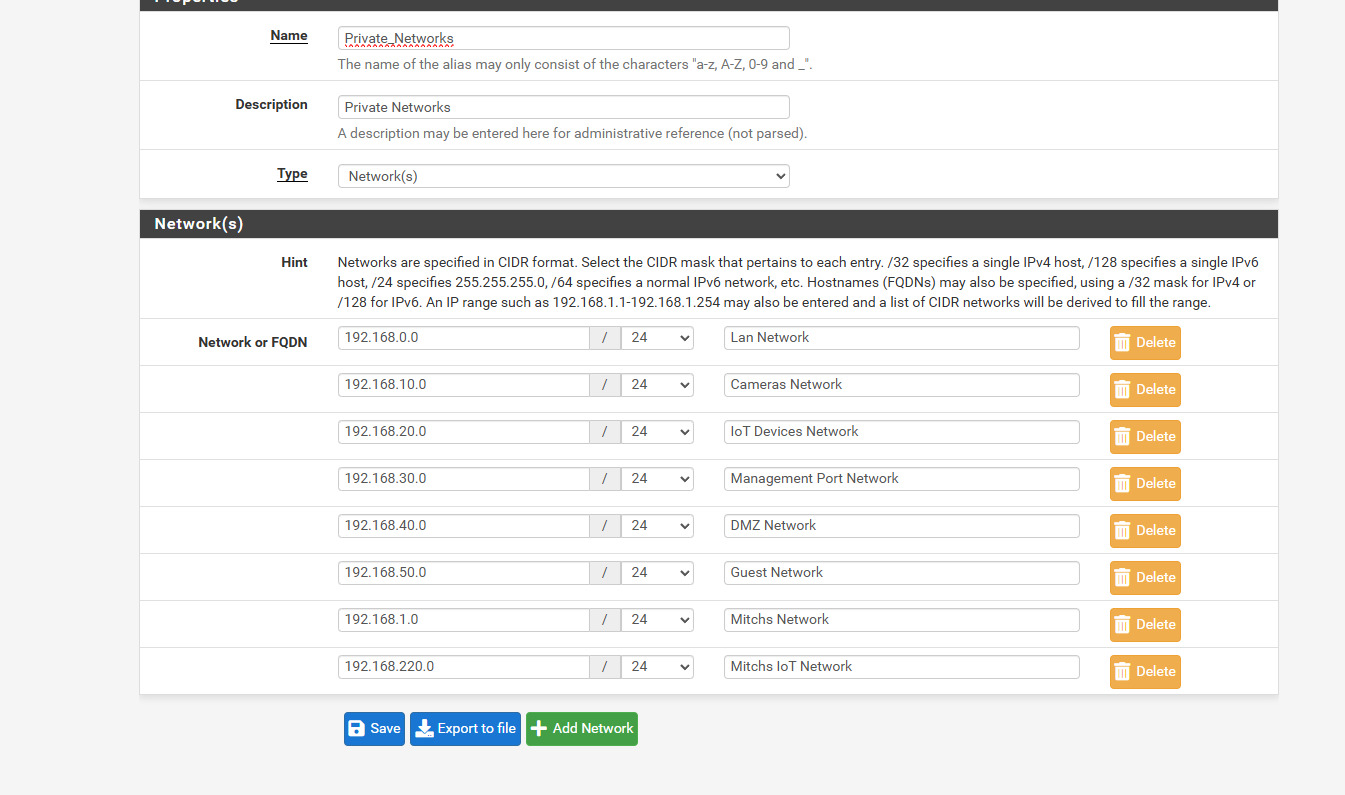
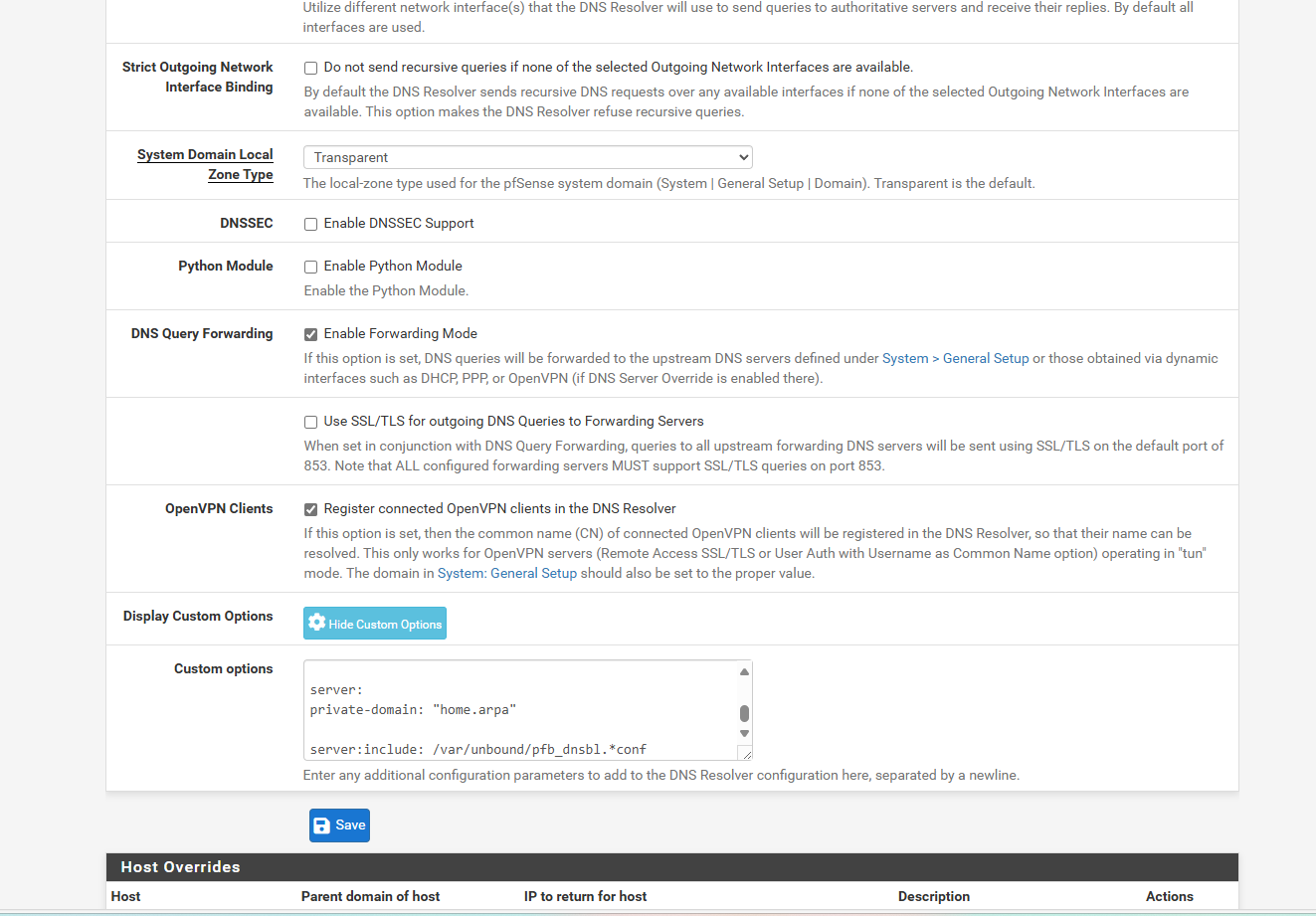
any other screen shots you need.. -
@comet424 said in Potential DNS Rebind attack detected on my local network:
server:
private-domain: "home.arpa"that is not needed, like I said that tells unbound hey if I forward home.arpa to some other NS or get an answer from some other ns and the answer is rfc1918 its ok.. But in no scenario that I can think of should that soa be returned for anything in home.arpa domain - unless you created the local record for it.
Or your forwarding to some other NS that has that soa setup or returns that soa for its local records... Unbound sure and the hell does not do that out of that box.
; <<>> DiG 9.16.50 <<>> @192.168.9.253 home.arpa SOA ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 31045 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;home.arpa. IN SOA ;; Query time: 0 msec ;; SERVER: 192.168.9.253#53(192.168.9.253) ;; WHEN: Sat Nov 23 12:36:13 Central Standard Time 2024 ;; MSG SIZE rcvd: 38You can see there is no SOA record for home.arpa That tells me unbound is asking something else for home.arpa - or your client isn't actually asking unbound. Or you have a local-data record setup your not showing. You don't have bind package running do you on pfsense?
And if you did ask the public internet for home.arpa or any normal NS on the public internet for something in home.arpa it should return that prisioner soa, because home.arpa has been set aside for private local use only.
Also that you would ever get back a rebind tells me unbound did not return what it had in its local records.. But asked/forwarded to someone else.. A rebind is when unbound asks some other NS and the answer is rfc1918.. That is by definition a rebind.
-
@johnpoz ok ill remove that server private domain then
as for NS thats Name Server right...
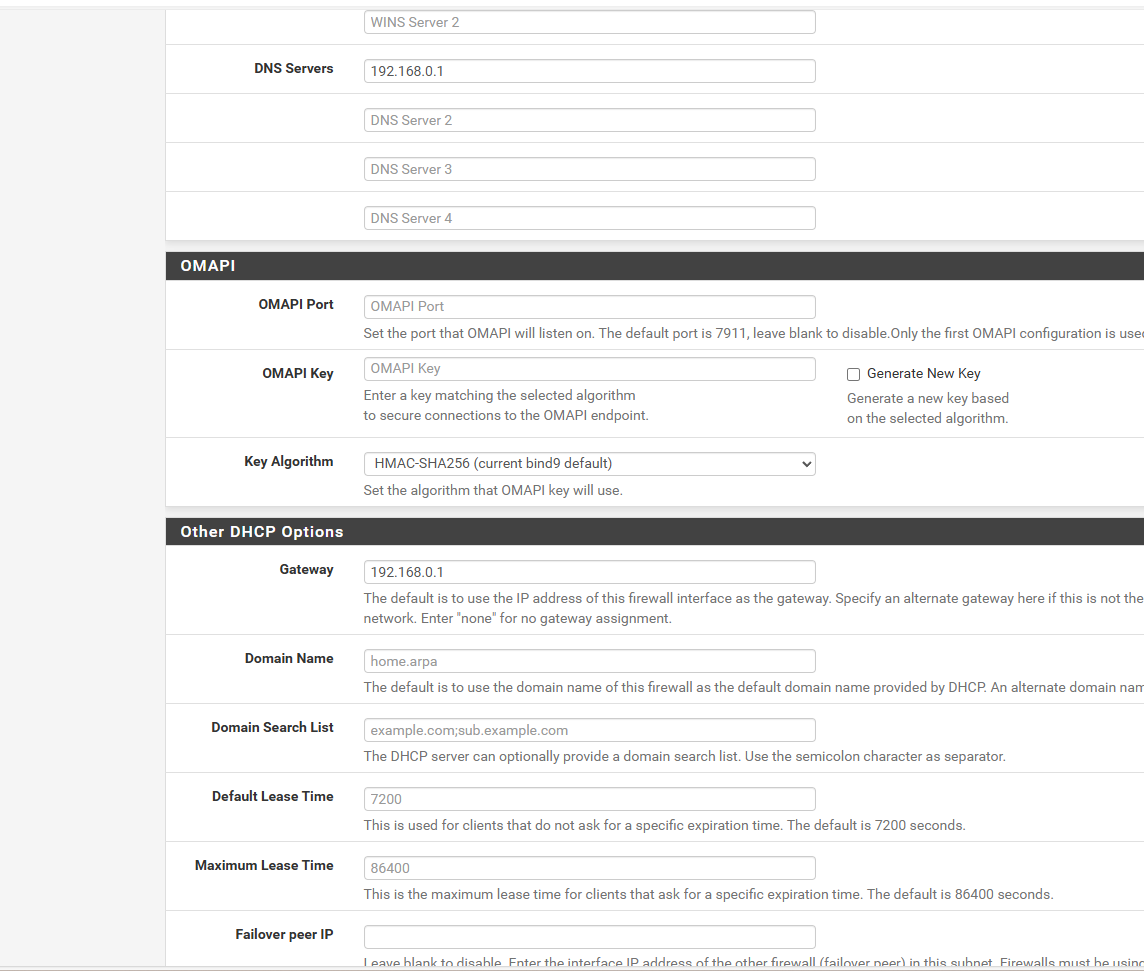
and only dns is pfsense minus 192.168.0.32 but thats the lancache for Windows updates and some games.. as my internet is only like 2 megabit and pay 100 bucks a month for internet thats not always stable.. but thats the only DNS stuff i setupnow the only local data setup i setup i guess is under the dhcp server i set static IPs like tardis.. but i set the Tardis hostname and ip of 192.168.0.3 and the DNS 192.168.0.1 and gateway of 192.168.0.1 so i dont do anything fancy
do you need a full display of NAT table.. or my PIA vpn right now i disabled the Nordvpn interface so i was able to shut off the openvpn client...
but ill remove the private domain and do a reboot of pfsense so its fresh.. i sometimes find pfsense works better after a reboot
-
and i thought i was good everything was find after i changed the general to the home.arpa
and i was able to ping again from Windows and unraid so i thought i was good
but then noticed i couldnt do it from ubuntu or raspberry pi
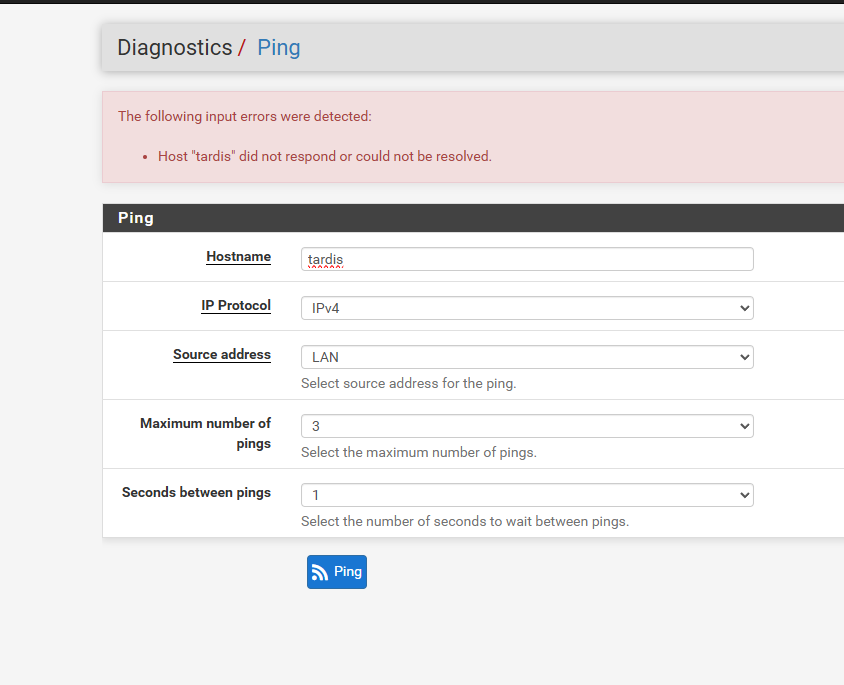
also i cant ping "tardis" from pfsense ping doesnt allow me there but i was sure i used to be able to
-
You are forwarding requests to whatever DNS servers you have set in System > General Setup via whatever gateways are set there.
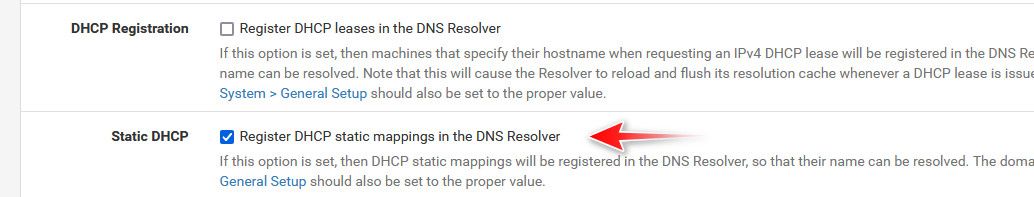
But more importantly you don't appear to have any DHCP registration options in the Resolver. So either you are running 24.03 with Kea or pfSense is not the DHCP server on your network?
-
@stephenw10
pfsense is the dhcp server for all my vlans and lan
the general tab
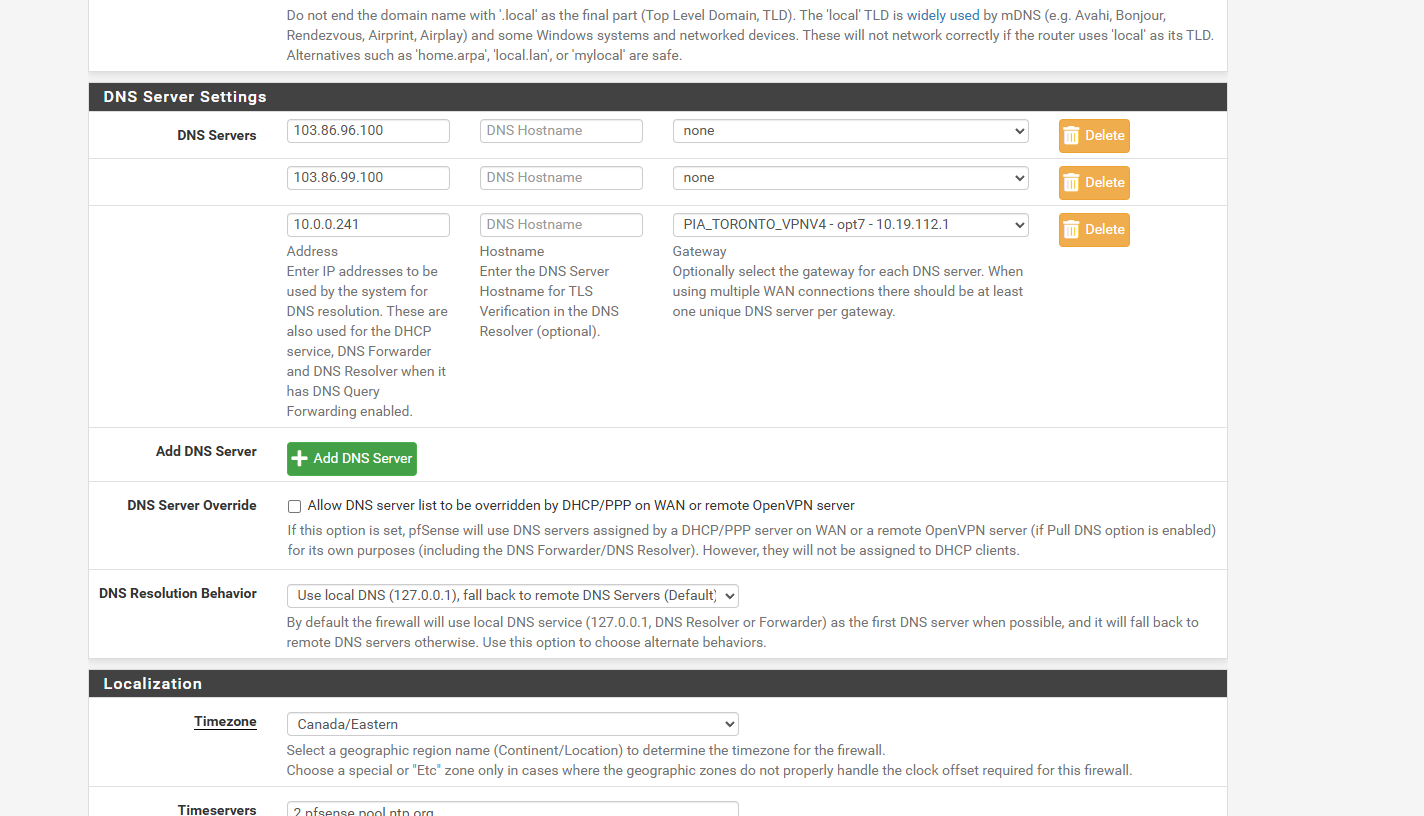
i have it set for kea
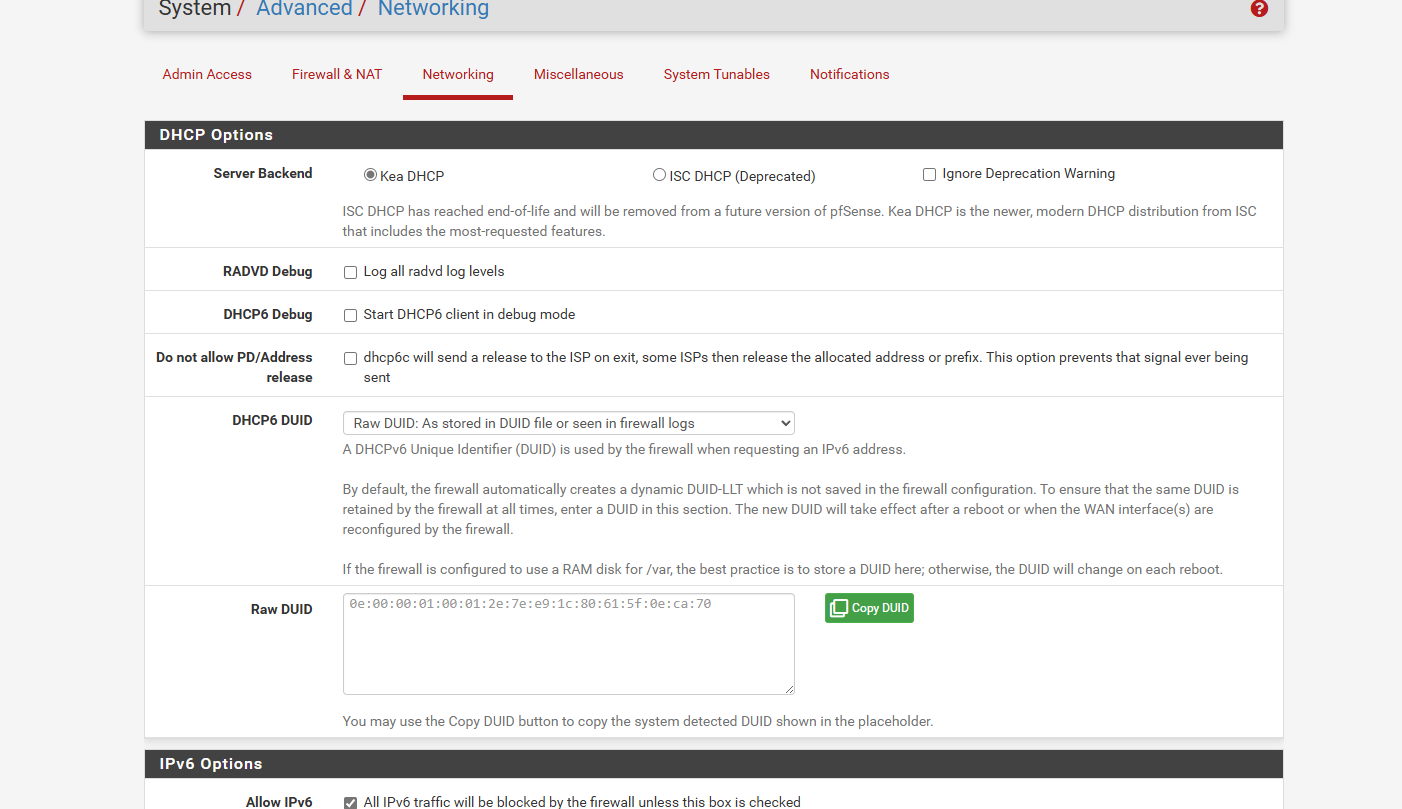
i do not know what 24.03 is if thats pfsense version no i not running that version must be new
i only have 2.7.2
i looked under dns resolver under the 3 tabs didnt find a registration option -
Ah Ok. In that case DHCP registration in the DNS server was not available in Kea at that point. If you switch back to ISC you can enable that and can then resolve other clients by hostname.
-
@stephenw10 so i flipped back to the ISC and enabled the dns registration... nothing happened so i rebooted everything pfsense switchs computers..
i still only can ping tardis from windows or unraidubuntu, raspberry pi,. and pfsense cant ping hostnames
and since ithe ISC is being depreciated the features in KEA will it get the ISC features when it gets released? like the hostname resolving you mentioned
-
Yes it's in the upcoming 24.11 Plus release.
But pfSense itself should certainly be able to resolve them if they appear in the DHCP leases table.
-
@stephenw10 maybe by morning it fix itself will see if not its werid as i can "ping pfsense" from ubuntu and it does it ok but i cant ping tardis and pfsense i cant ping either tardis or any local hostnames
is that a rule order issue or conflicting nat and not sure what 1:1 nat is really
-
How does the ping fail? What error is shown?
-
@stephenw10 so i left it and it didnt fix itself
so for pfsense i get
The following input errors were detected: Host "tardis" did not respond or could not be resolved.for ubuntu i get
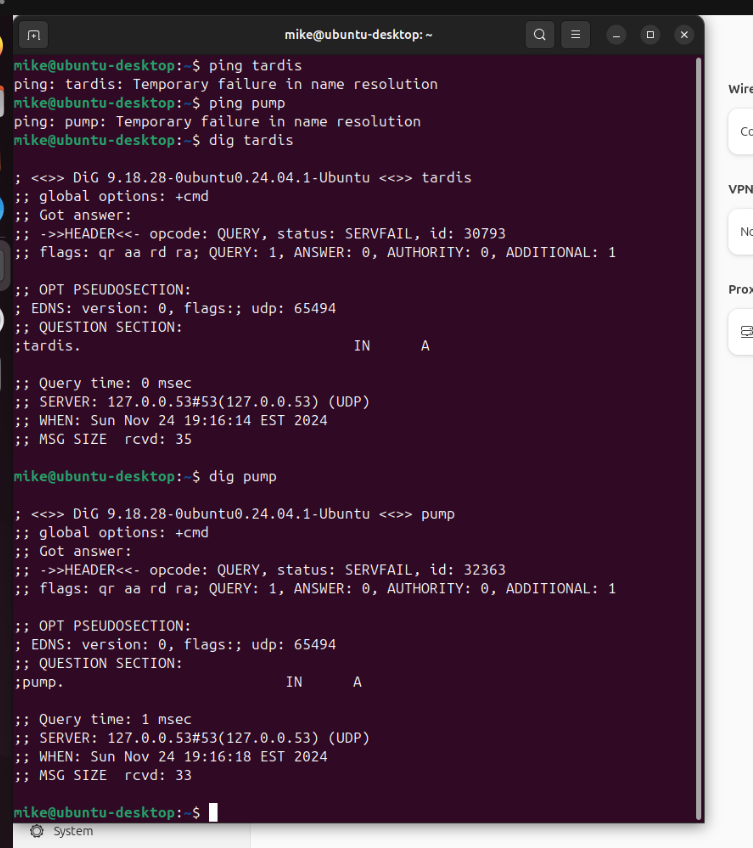
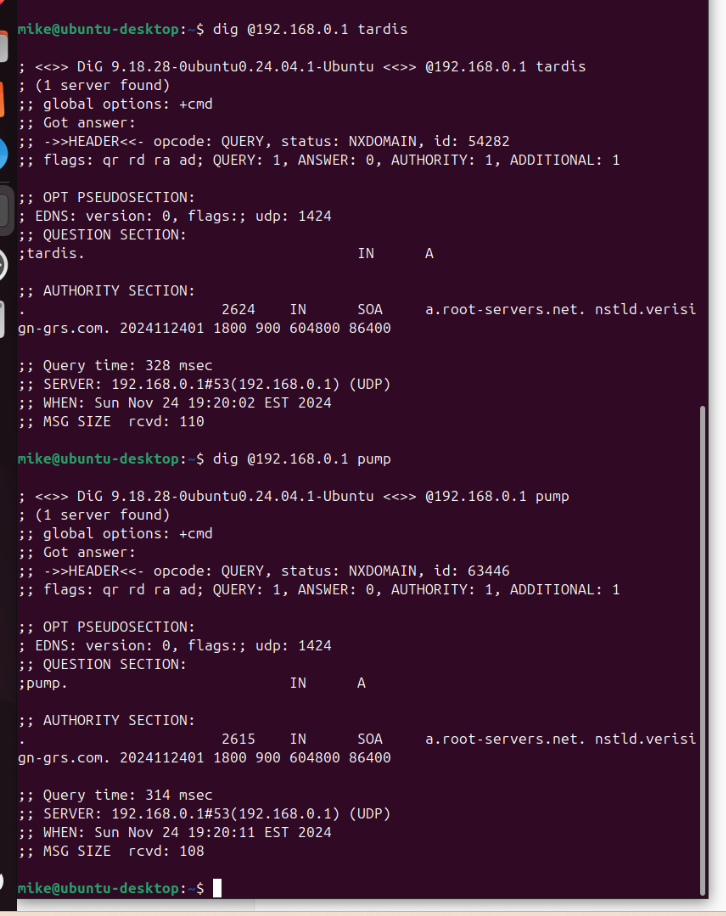

and windows and unraid i can still ping host name finei checked the dns registration box
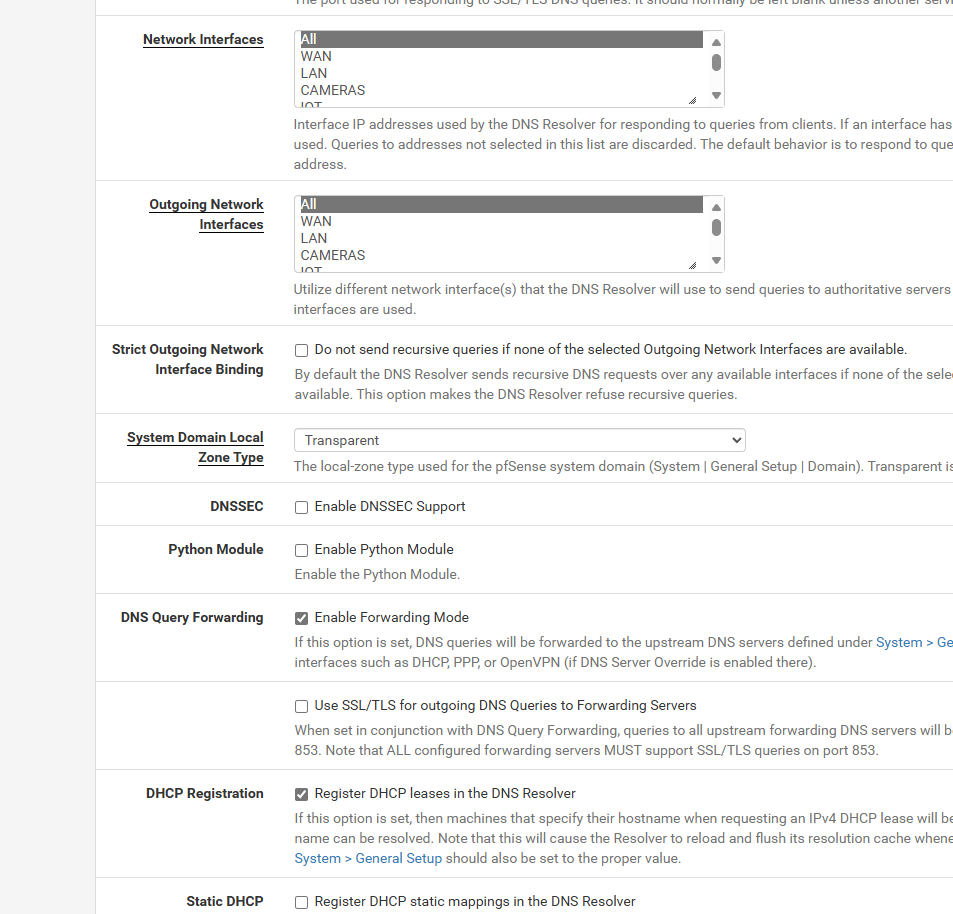
-
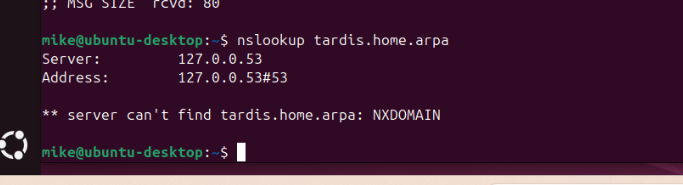
nslookup doesnt find anything in windows
but ping does
and no dig in windows command prompt
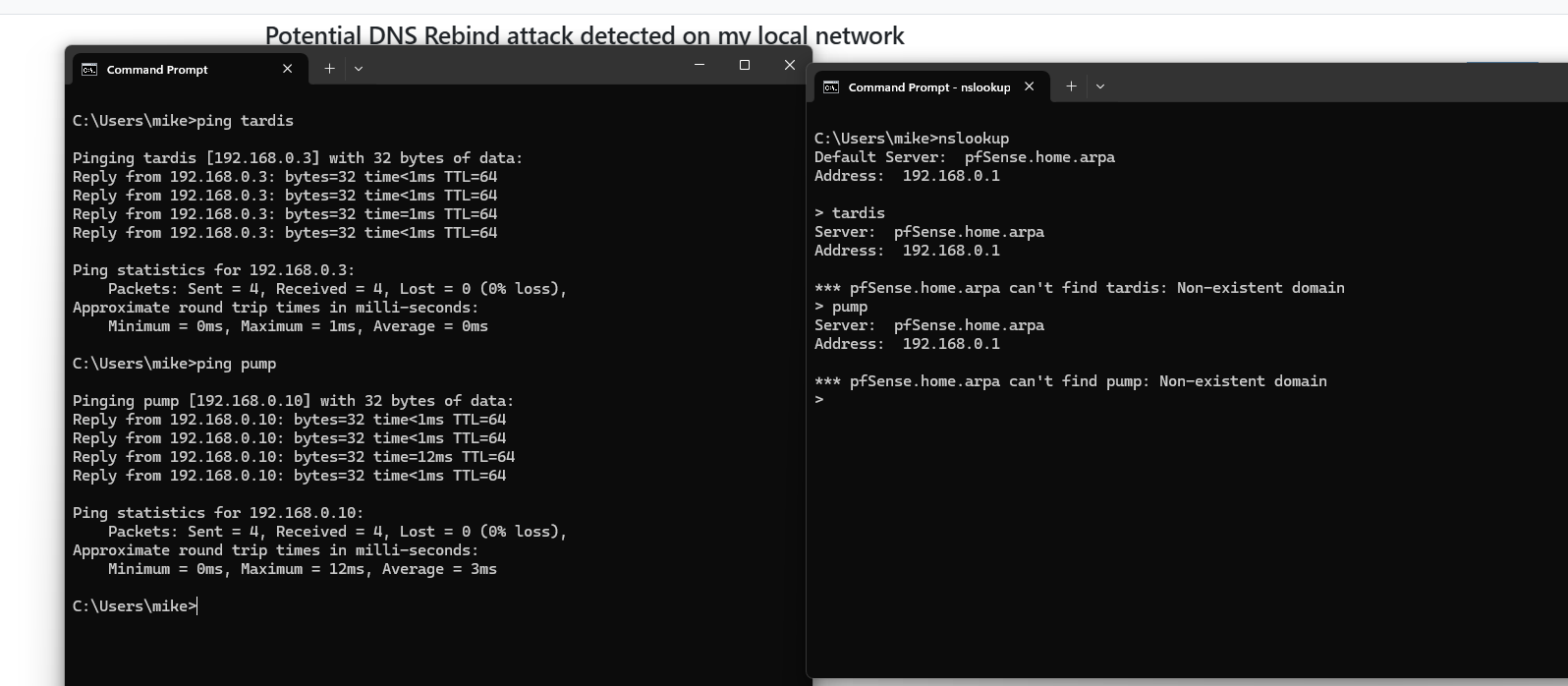
-
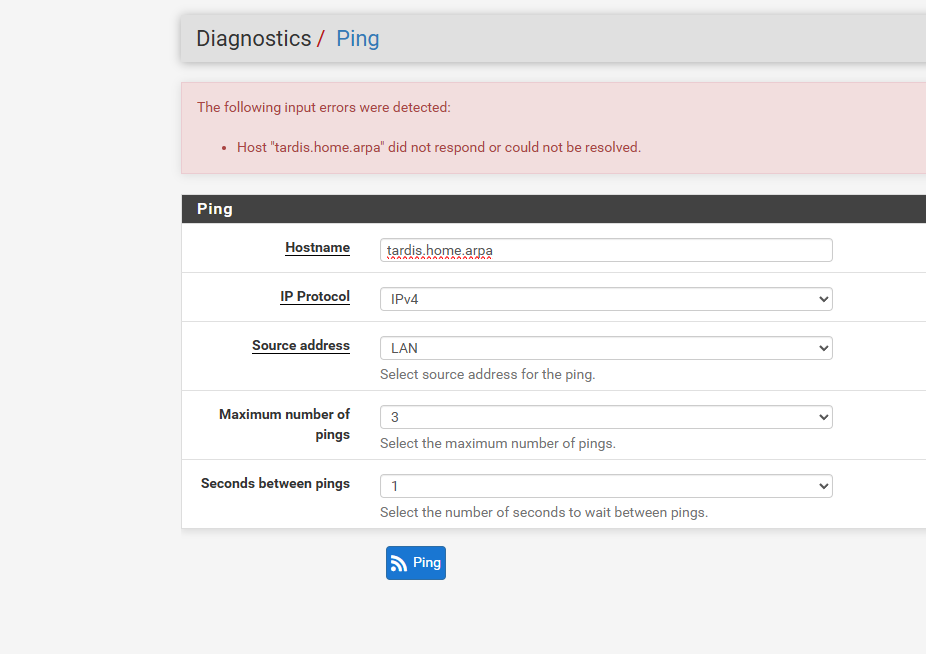
Ok. I expect though that host or nslookup works if you use the fqdn?:
tardis.home.arpaAnd ping Ubuntu?
It looks like you have a mismatch in the domain you're assigning or passing to clients somewhere. Windows appends it from something. Linux doesn't. or uses the wrong domain.
-
@stephenw10 yeah you would expect tardis. to fail with dig.. that is asking for just tardis and not fully qualified, that should always fail.
if your going to use nslookup and let the search suffix work you should set debug so you can see what it actually asks for.
Your ping there on windows that comes back without it fully qualified is most likely using something else to resolve mdns, llmns, wds - there are multiple methods of just resolving locally without dns. If it actually used dns to resolve that than the ping should show tardis.home.arpa, etc..
ash-4.4# nmblookup i9-win 192.168.10.9 i9-win<00> 192.168.9.100 i9-win<00> 172.29.64.1 i9-win<00> ash-4.4# -
so not sure how to use the debug for for nslookup well properly the way you guys want me to type it in
as for domain name. i only have it set under general.so its weird i always thought that as long as i could ping a hostname in windows that the dns was working but it used mdns llmns wds or so on.. always learn something new everyday no wonder i had probems 25 years ago witn WinGate trying to share internet was a program to share internet and dns server...
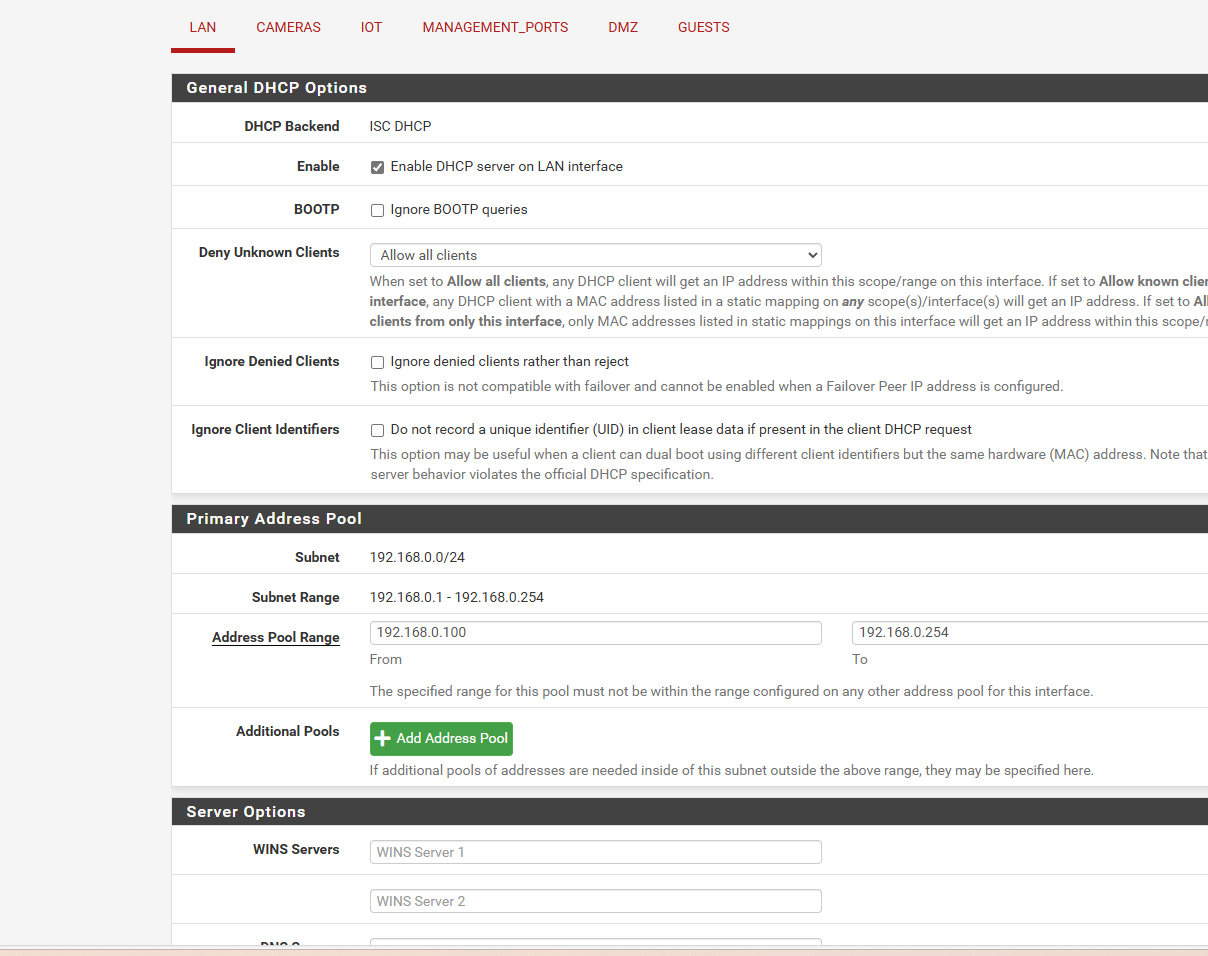
so i did a bunch of tests and screen shots of my static ip the dhcp of lan general... do you see anything i got set wrong that that dns resolver isnt working right.. does NAT have anything to do with it?
is there another place to look for domain name or page that the resolver isnt working.. i figured the extra PIA NATs i added duplicated of the WAN as i dunno i did a clean install last time i had issues and seems i got issues again lol its just just 1 check box or 1 rule that causes the dns not to work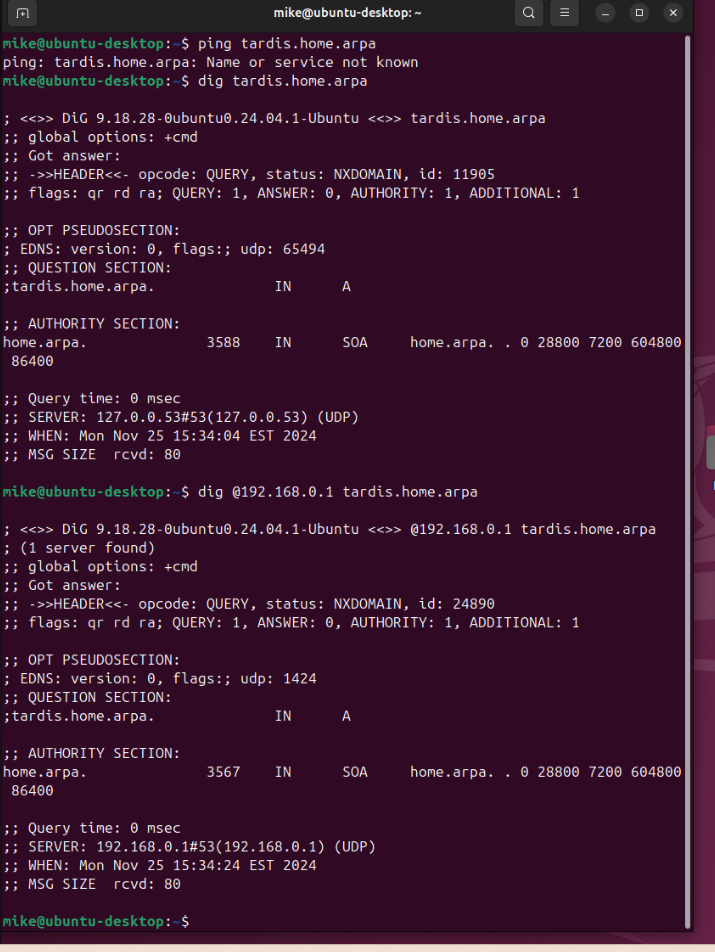




-
@comet424 I am not sure what is going on but what does yours show when you go to the dns lookup under diagnostics?
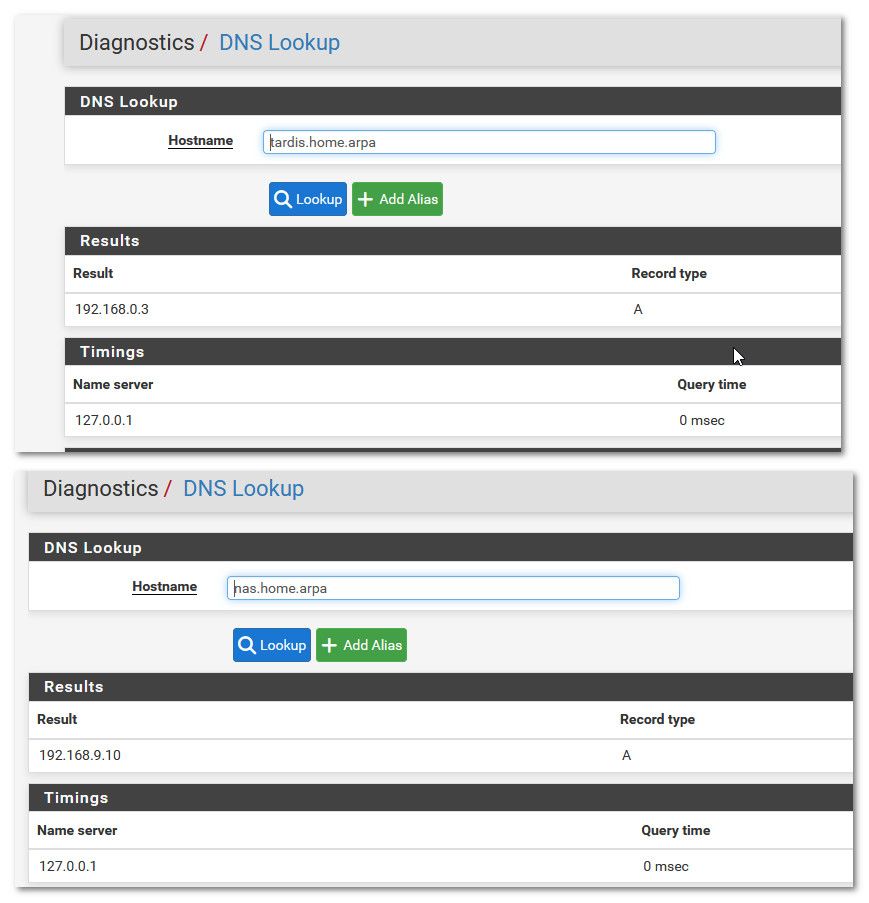
what about dig right on pfsense?
[24.03-RELEASE][admin@sg4860.home.arpa]/root: dig nas.home.arpa ; <<>> DiG 9.18.20 <<>> nas.home.arpa ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 41317 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;nas.home.arpa. IN A ;; ANSWER SECTION: nas.home.arpa. 3600 IN A 192.168.9.10 ;; Query time: 0 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) (UDP) ;; WHEN: Mon Nov 25 15:33:39 CST 2024 ;; MSG SIZE rcvd: 58 [24.03-RELEASE][admin@sg4860.home.arpa]/root:What seems really odd to me is that SOA.. you shouldn't be getting that.
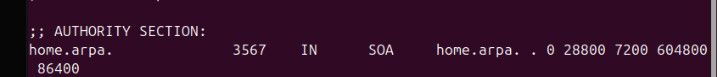
unbound is not an authoritative NS, it really shouldn't hand out SOAs for domain you have records for.. And have no idea where that is coming from.. If your stuff was being forward to any sort of public dns.. Then you should get back that
SOA prisoner.iana.org.
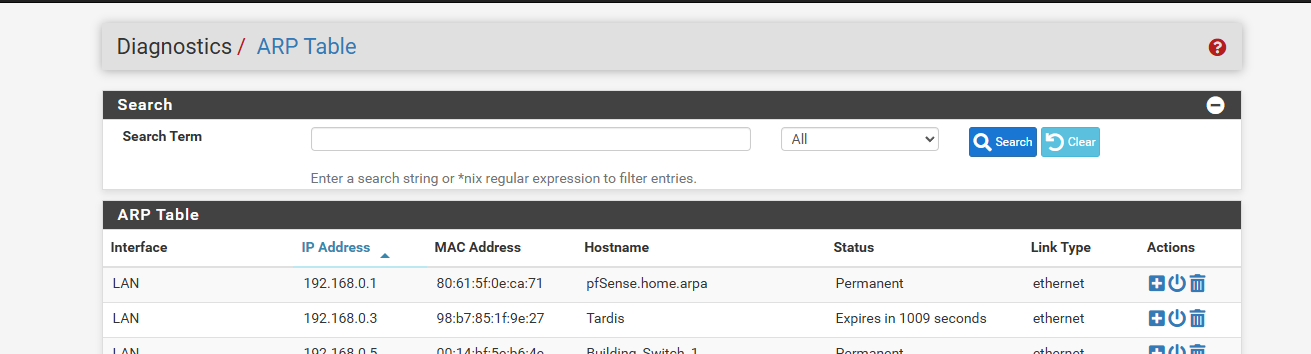
if you setup a reservation for this tardis IP via its mac, then on unbound register reservations/static
does pfsense.home.arpa resolve via dns diagnostic?
You can look in your unbound config.
[24.03-RELEASE][admin@sg4860.home.arpa]/var/unbound: cat host_entries.conf local-zone: "home.arpa." static local-data-ptr: "127.0.0.1 localhost.home.arpa" local-data: "localhost. A 127.0.0.1" local-data: "localhost.home.arpa. A 127.0.0.1" local-data-ptr: "::1 localhost.home.arpa" local-data: "localhost. AAAA ::1" local-data: "localhost.home.arpa. AAAA ::1" local-data-ptr: "192.168.9.253 sg4860.home.arpa" local-data: "sg4860.home.arpa. A 192.168.9.253" local-data-ptr: "192.168.9.10 nas.home.arpa" local-data: "nas.home.arpa. A 192.168.9.10" local-data-ptr: "192.168.9.100 i9-win.home.arpa" local-data: "i9-win.home.arpa. A 192.168.9.100" local-data-ptr: "192.168.2.5 FlexHD.home.arpa" local-data: "FlexHD.home.arpa. A 192.168.2.5" local-data-ptr: "192.168.2.13 UC.home.arpa" local-data: "UC.home.arpa. A 192.168.2.13" local-data-ptr: "192.168.2.198 Johns-13.home.arpa" local-data: "Johns-13.home.arpa. A 192.168.2.198"Can you post up your /var/unbound/unbound.conf file? If your registering dhcp, and you have a client renew its lease you should see it listed in dhcpleases_entries.conf