Local DNS Records on different subnet
-
Does it actually not resolve or just not connect?
The screenshot above looks like a connection issue not a DNS problem.
If it does resolve what is it resolving to at the client?
-
@stephenw10 so I am on my pfsense subnet right now,
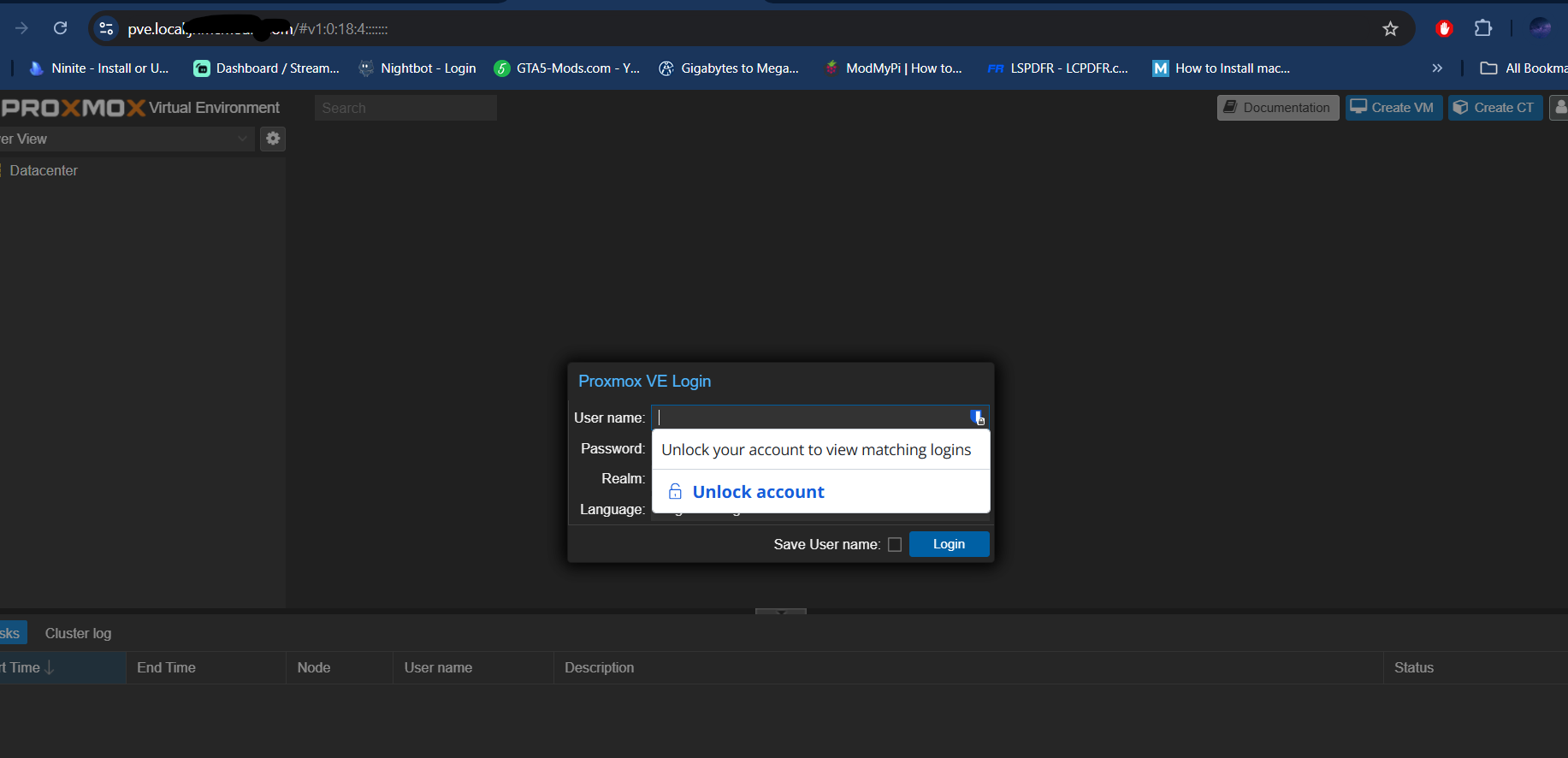
where as it doesn't do that if I'm on my isp router
-
@jhmc93 that browser error is not a dns not resolving, browser not resolving something would look like
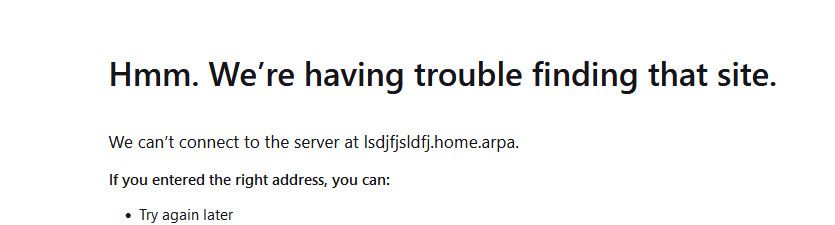
Your machine resolved that to something, is it the right thing - who knows from that picture - but it did resolve it.
If your using firefox go to about:networking#dns it will show you what you resolved something too
-
not showing anything
-
@johnpoz
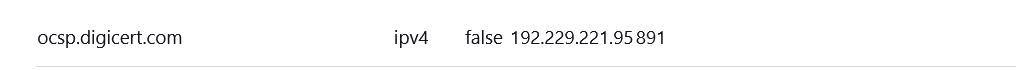
guessin this is it can't be sure though -
On the client just try to resolve it at the command line so you can see what it resolves to.
If it resolves to something in the 10.84.x.x subnet (pfSense LAN) then you will need a route to it via pfSense.
If you just put all your clients on a subnet behind pfSense this would work without issue.
-
@stephenw10 by client do u mean my machine I work on, the traefik machine or the pihole server??
-
I mean a desktop/laptop in the 192.168.8.X subnet (pfSense WAN side).
-
@jhmc93 how would you think that is it - that name ocsp.digicert.com is not the fqdn you were trying to go to.. Come on Man!!
The fqdn in your proxmox shows pve.local.something - does that look anything even remotely close? That is the oscp check for a digicert cert..
https://en.wikipedia.org/wiki/Online_Certificate_Status_Protocol
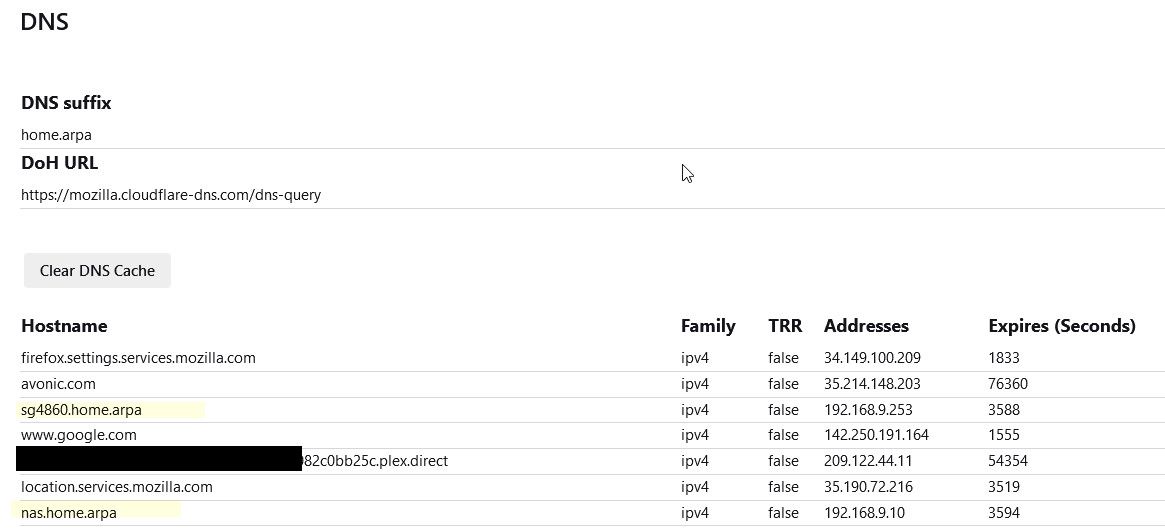
I thought it was pretty obvious - I highlighted 2 names that are local on my network, nas and sg4860.home.arpa - that resolve to local rfc1918 IPs
-
@johnpoz
 I'm thick sorry
I'm thick sorry -
@jhmc93 that doesn't show any iP it was resolved too - unless you cut it out columns are different order?
not sure why it would even show that?? If it didn't resolve to something, and you would get a different error if had no ip to talk to, like I posted above.
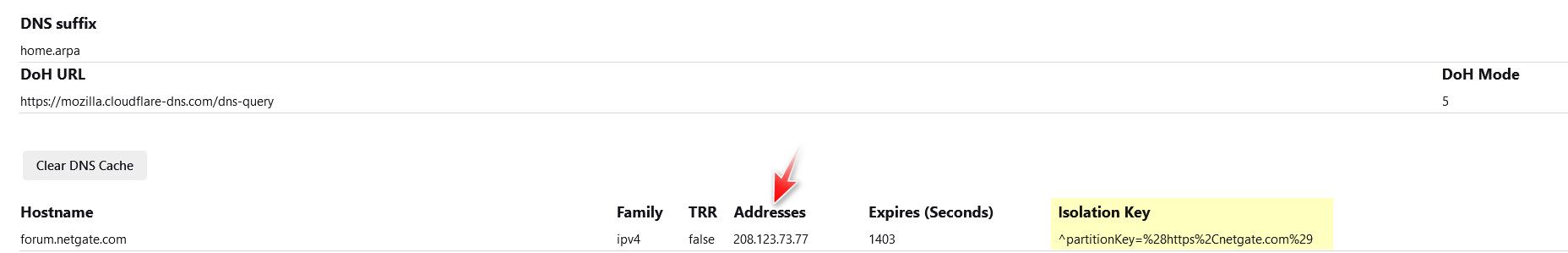
Can we see the top of that output, see where it shows suffix and doh and trr mode.
Also that seems like a really odd isolation key for going to some local domain.. jhncmedia.com
-
-
@jhmc93 so your search suffix is a public domain? Yeah your most likely going to have weird stuff happen.
because you look, for something like pve.local.whatever its going to end up looking for pve.local.whatever.cable.otherthing.net
-
@johnpoz even though pihole is set as my dns on pfsense and on the laptop on my isp side so don't know what is going on
-
@stephenw10
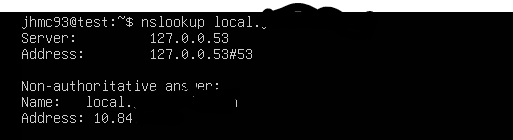 your answer
your answer -
Ok great so it does resolve to the internal IP in the pfSense LAN subnet as expected.
This it is almost certainly failing because the client has no route to reach that subnet. It would not have one by default. It would have to have been added as a static route via the pfSense WAN. And pfSense would need rules on WAN to pass it.
-
@stephenw10 how would I go about that? without exposing it to public internet because I wanna keep it in my ISP subnet and Pfsense Subnet
-
Well really what you should do is move all clients to a subnet behind pfSense to avoid this issue. It's almost certainly going to cause other problems having clients in the pfSense WAN subnet.
But I understand you might have physical restrictions for example preventing that.
So you need a firewall rule on the pfSense WAN to allow traffic from the wan subnet to whatever the target IP is on the LAN.
And you need to add a static route to the pfSense LAN subnet via the pfSense WAN IP on the client directly.
That doesn't expose anything to the public internet.
-
@stephenw10 so do I create that rule in the lan or wan firewall rule or is it a nat rule
-
It's a firewall rule on the WAN interface. The client is trying to open connections from the WAN subnet to servers in LAN.
