Question Regarding Default Deny Rules
-
I have about half of my Roku's wireless and the other half are connected via ethernet. I am going to continue to check the logs every so often to see what pops up and maybe I will grab another packet capture.
I realize this traffic is probably benign and turning off the default logging is the easiest way to avoid it. Like I said, I am more using this as an opportunity to investigate something that I may want/need to do for another purpose down the road.
-
@djtech2k sure makes sense - keep in mind that if your ever running into something weird that not sure what is going on - turn default logging back on is always just a click away ;)
-
Hmm, I would have expected that block to match before the default block though. It's definitely on the correct interface?
-
@stephenw10 said in Question Regarding Default Deny Rules:
Hmm, I would have expected that block to match before the default block though. It's definitely on the correct interface?
Yes, everything is on the LAN interface. All other physical interfaces are disabled there are only 2 vif's, which are for the vpn server and vpn client.
-
Hmm, must be something not matching. The source traffic is definitely in the alias?
What exactly do the rules look like now?
-
@stephenw10 said in Question Regarding Default Deny Rules:
Hmm, must be something not matching. The source traffic is definitely in the alias?
What exactly do the rules look like now?
I have checked the alias members a few times when looking at a specific packet and its always been in a member.
Here are the current rules:
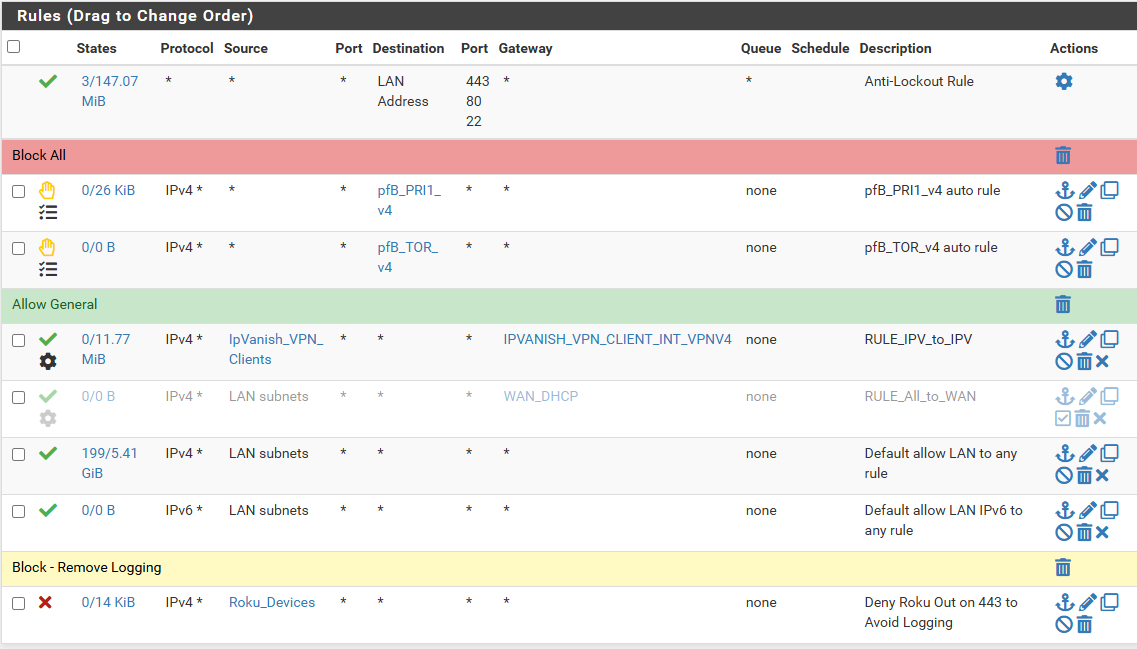
-
And it's still logging TCP flagged packets from devices inside that alias hitting the default deny rule?
If you reload the ruleset in Status > Filter Reload does it show any errors?
-
I am not seeing it this second but I will check back on it every once in a while to see if it shows up. I have my logging set to the last 750 lines so it rotates/overwrites pretty quickly.
-
So far I am not seeing it from Roku. I am seeing it from a couple of other devices, like a camera. Its getting the TCP:RA or TCP:PA flags and trying to hit a port 443 destination. This device(s) are not in the Alias because its not a Roku but if the same theory applies, I could add it to the alias.
-
Given what I have gathered from this thread, I do wish I could figure out the right flags or whatever needed to catch these packets so I could create a rule for all of them. I hate having a block rule for wide open protocols, etc.
So as of now, I have the block rule as you see from the screenshot. Its isolated to my Alias, but if there are other devices with similar traffic, would it be harmful to just make the rule apply to everything? I mean it would be at the bottom so theoretically it would only apply if the Allow Any/Any rule did not apply for some reason.
To be honest, it is a bit confusing how the default deny rule is not shown and then there are things like these 443 packets that don't get caught with a TCP filter. I am ok to create a rule to block/remove the logging but don't want to put in something that may end up blocking traffic that could impact something.
-
@djtech2k said in Question Regarding Default Deny Rules:
. I am ok to create a rule to block/remove the logging but don't want to put in something that may end up blocking traffic that could impact something.
putting any sort of rule that blocks below a any any rule isn't going to block anything that could get out anyway. If there is no state it isn't getting out anyway so the block is there to just not log noise/spam
-
Corrected: Now seeing it from Xbox, not “not” seeing it from Xbox.
Just for additional info, I am now seeing a ton of traffic like this for an Xbox. I guess it’s just been turned on or at least that I saw it. Lots of port 443 traffic with the TCPFA or TCP:PA flags getting blocked by the default rule.
-
@djtech2k said in Question Regarding Default Deny Rules:
Given what I have gathered from this thread, I do wish I could figure out the right flags or whatever needed to catch these packets so I could create a rule for all of them. I hate having a block rule for wide open protocols, etc.
Yes, you are only seeing blocked TCP traffic so you should be able to block-not-log only that. I would have expected the rule with 'any flags' you have previously to do that.
-
Yes, I was surprised that the filter with TCP any flags did not catch this stuff. Either way, I am not seeing ROKU logging this morning so I adjusted the rule to include LAN subnets with destination port 443. Since the Any/Any rule is above it, I am assuming any traffic that hits this block rule will be blocked anyway so this rule will at least suppress the logging. When I end up disabling the default deny logging, I can disable this rule, but for now this rule will help me get a better idea of what is being blocked and it anything needs tuned.
-
I am seeing quite a few WAN blocks on UDP for IP's that are coming back as Facebook. Seems kinda odd that Facebook would have traffic coming in from the WAN. Do you guys see this traffic too?
-
What port?
It's not unexpected though if some device on your LAN had opened a connection and never closed it. Eventually pfSense will kill the state and the remote server might send traffic that will be blocked.
-
Looks like the source port is a FB IP on port 443 and the destination is my pfsense WAN address (10.x) on port varying from 1604-36571. The 10.x IP comes from my ISP gateway device.
-
@djtech2k said in Question Regarding Default Deny Rules:
s my pfsense WAN address (10.x) on port varying from 1604-36571
so your pfsense is behind a nat device.. 10.x is not a public IP. And if its udp with 443 it would be quic
-
Yup, so similar to the other traffic you saw. It's a reply from the server back to some LAN side client after the firewall has closed the state. Nothing unusual or unexpected there.
-
@johnpoz said in Question Regarding Default Deny Rules:
@djtech2k said in Question Regarding Default Deny Rules:
s my pfsense WAN address (10.x) on port varying from 1604-36571
so your pfsense is behind a nat device.. 10.x is not a public IP. And if its udp with 443 it would be quic
Correct. My pfsense WAN is an RFC1918 IP coming from the ISP gateway.