Question Regarding Default Deny Rules
-
I am not seeing it this second but I will check back on it every once in a while to see if it shows up. I have my logging set to the last 750 lines so it rotates/overwrites pretty quickly.
-
So far I am not seeing it from Roku. I am seeing it from a couple of other devices, like a camera. Its getting the TCP:RA or TCP:PA flags and trying to hit a port 443 destination. This device(s) are not in the Alias because its not a Roku but if the same theory applies, I could add it to the alias.
-
Given what I have gathered from this thread, I do wish I could figure out the right flags or whatever needed to catch these packets so I could create a rule for all of them. I hate having a block rule for wide open protocols, etc.
So as of now, I have the block rule as you see from the screenshot. Its isolated to my Alias, but if there are other devices with similar traffic, would it be harmful to just make the rule apply to everything? I mean it would be at the bottom so theoretically it would only apply if the Allow Any/Any rule did not apply for some reason.
To be honest, it is a bit confusing how the default deny rule is not shown and then there are things like these 443 packets that don't get caught with a TCP filter. I am ok to create a rule to block/remove the logging but don't want to put in something that may end up blocking traffic that could impact something.
-
@djtech2k said in Question Regarding Default Deny Rules:
. I am ok to create a rule to block/remove the logging but don't want to put in something that may end up blocking traffic that could impact something.
putting any sort of rule that blocks below a any any rule isn't going to block anything that could get out anyway. If there is no state it isn't getting out anyway so the block is there to just not log noise/spam
-
Corrected: Now seeing it from Xbox, not “not” seeing it from Xbox.
Just for additional info, I am now seeing a ton of traffic like this for an Xbox. I guess it’s just been turned on or at least that I saw it. Lots of port 443 traffic with the TCPFA or TCP:PA flags getting blocked by the default rule.
-
@djtech2k said in Question Regarding Default Deny Rules:
Given what I have gathered from this thread, I do wish I could figure out the right flags or whatever needed to catch these packets so I could create a rule for all of them. I hate having a block rule for wide open protocols, etc.
Yes, you are only seeing blocked TCP traffic so you should be able to block-not-log only that. I would have expected the rule with 'any flags' you have previously to do that.
-
Yes, I was surprised that the filter with TCP any flags did not catch this stuff. Either way, I am not seeing ROKU logging this morning so I adjusted the rule to include LAN subnets with destination port 443. Since the Any/Any rule is above it, I am assuming any traffic that hits this block rule will be blocked anyway so this rule will at least suppress the logging. When I end up disabling the default deny logging, I can disable this rule, but for now this rule will help me get a better idea of what is being blocked and it anything needs tuned.
-
I am seeing quite a few WAN blocks on UDP for IP's that are coming back as Facebook. Seems kinda odd that Facebook would have traffic coming in from the WAN. Do you guys see this traffic too?
-
What port?
It's not unexpected though if some device on your LAN had opened a connection and never closed it. Eventually pfSense will kill the state and the remote server might send traffic that will be blocked.
-
Looks like the source port is a FB IP on port 443 and the destination is my pfsense WAN address (10.x) on port varying from 1604-36571. The 10.x IP comes from my ISP gateway device.
-
@djtech2k said in Question Regarding Default Deny Rules:
s my pfsense WAN address (10.x) on port varying from 1604-36571
so your pfsense is behind a nat device.. 10.x is not a public IP. And if its udp with 443 it would be quic
-
Yup, so similar to the other traffic you saw. It's a reply from the server back to some LAN side client after the firewall has closed the state. Nothing unusual or unexpected there.
-
@johnpoz said in Question Regarding Default Deny Rules:
@djtech2k said in Question Regarding Default Deny Rules:
s my pfsense WAN address (10.x) on port varying from 1604-36571
so your pfsense is behind a nat device.. 10.x is not a public IP. And if its udp with 443 it would be quic
Correct. My pfsense WAN is an RFC1918 IP coming from the ISP gateway.
-
Ok here is another traffic log related question. Since my tuning of the rules to block the logging of the stateless packets, I now see a lot more IPv6 log entries. They all seem to be the default block rule "Default deny rule IPv6 (1000000105)". I see a LOT of entries of some ipv6 addresses on my network trying to reach some ipv6 addresses on port 443 (others too) with TCP flag TCP:S.
I have exactly nothing configured for IPv6 on my network. I considered blocking it but I know some services are starting to depend on them. So I am not sure why this is happening but hat makes it worse than my situation with the stateless packets is that I do not know what devices they belong to. With IPv4 I would just check the ARP table and find the device. I feel like I am flying blind on this one.
-
@djtech2k well by default there should be a any any rule that allows IPv6.. But syn block means you don't have a rule to allow that traffic
Either allow it or block it - that is up to you. If you want to block and not log then setup a rule to block it and not log.
As to this?
but I know some services are starting to depend on them.
No name 1 please - there are no major services that I am aware of that require IPv6 that.. Are you trying to access some site hosted by someone that doesn't have IPv4.. Been waiting for 1 example of this for years..
Here is my advice if you do not understand how to work with ipv6 - disable it at your clients.. Don't hand them a public IPv6 address in the first place.. Are where they going actually public IPv6, or are they just link local addresses? Or ULA?
-
@johnpoz said in Question Regarding Default Deny Rules:
@djtech2k well by default there should be a any any rule that allows IPv6.. But syn block means you don't have a rule to allow that traffic
Either allow it or block it - that is up to you. If you want to block and not log then setup a rule to block it and not log.
As to this?
but I know some services are starting to depend on them.
No name 1 please - there are no major services that I am aware of that require IPv6 that.. Are you trying to access some site hosted by someone that doesn't have IPv4.. Been waiting for 1 example of this for years..
Here is my advice if you do not understand how to work with ipv6 - disable it at your clients.. Don't hand them a public IPv6 address in the first place.. Are where they going actually public IPv6, or are they just link local addresses? Or ULA?
Well I don't have an ipv6 DHCP server running so they are either built-in static or coming from somewhere else. As for services that use them well I have seem some used in VPN and also from my ISP. Now I do not know the significance or if it could be disabled somehow but I have seen them assigned. I guess my biggest issue is finding the device it belongs to. Obviously I hate ipv6 and don't work with it so IDK of a reliable way to link IP to device. As for where the ipv6 log entry is going, I grabbed a few and ran an IPInfo on them and they were amazon.com. So I am assuming the device(s) would be Amazon Echo devices, but that's just the example on this. I don't want to have to grab every ipv6 address and do a check on every one and then try to guess what device on my network is using it.
-
@djtech2k dhcpv6 is not required for IPv6 - prob using slaac
Out of the box pfsense would not setup IPv6 it would get on its wan on its lan.. Do you have IPv6 enable on your wan? Did you enable track interface for a prefix delegation?
If you do not even understand the basic concepts of how IPv6 even gets an address, then yeah I wouldn't have it enabled.
You can track an IPv6 to a device with NDP, it's really the same as arp - but for IPv6.. Here I enabled IPv6 on my machine to show you. I normally have it disabled
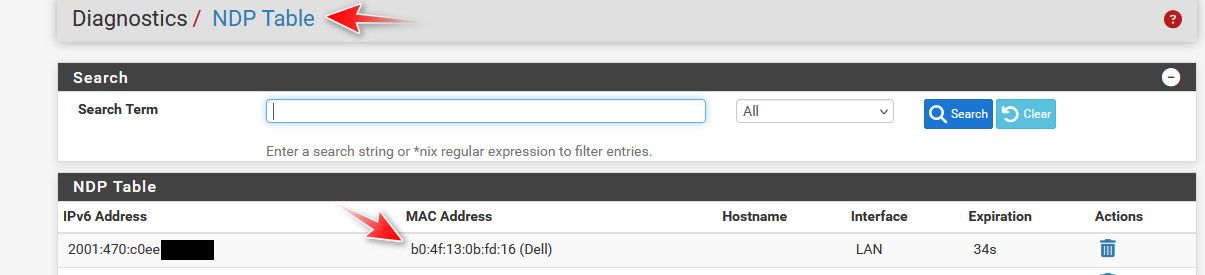
here are some other IPv6 my machine is using now that I turned it on

that fe80 is just a link local address.. Ipv6 clients normally use multiple IPv6 address - that address in my 2nd post with 2001:470 is different than the one I posted in the first pic.
Our resident ipv6 fan boy will prob chime in here soon about how IPv6 is required (its not) most of the planet still doesn't even have it deployed to be honest - my ISP doesn't provide it for example. Here is my advice to any protocol you do not understand how it works or for sure how to manage it - disable it plan and simple.. This is security 101.. If you don't understand how something works, or how to control it - how can it be secure.. And to quiet our fanboy since I think he searches for any mention of IPv6 - yes it is the future, yes it will get rid of that nasty thing called nat..
Hey if I get him to disable it - will I have slowed the snail roll of ipv6 deployment by another fraction of a nanosecond? ;)
edit: back to disabled on my client - because I have less than zero use for IPv6.. Even though I have been using it for almost 15 some years.. It still serves zero purpose on my network.. I turn it on to answer peoples questions.. My phone uses it when its out and about, etc. But locally it has no use to me, so like any security conscious person should do with protocols they are not actively using - they should be disabled.
I have been doing this for 30+ plus years and have worked for a few different companies, and for quite some time worked for a major MSP - not one client of ours was using IPv6.. Not one - we had no use for it anywhere in our own networks in some very large networks.. I actively looked for projects to work on that were using IPv6 - not one could I find... I did at a previous company get them a /32 from arin and got that all setup for them - and they working on a project to use IPv6 for mass car iot sort of deployment thing.. But no local IT resources anywhere in the global company were actually using IPv6, etc.. You can turn it off - and unless your playing some p2p game or something that is leveraging it.. You won't even notice its not there..
When someone like amazon or facebook or any other major player on the internet says - hey you have to have IPv6 to connect to us - that is when IPv6 has arrived.. Until that day arrives, I will for sure be retired if not dead, it is a very slow transition and we will be in a dual stack mode for many many many years to come - no matter how much our local fanboy thinks different ;) So if you do not understand it, don't know how to manage it - then yes disable it.
But if you want to learn about it - then yes I would say go for it.. But its a bit more involved than just a longer IP address ;)
-
They are probably link local addresses that are based on the device MAC address. If so you should be able to find the source devices from that.
However if you're not using IPv6 at all you can just not log it. Or ignore it.
-
So when you say disable ipv6, are you still talking about the client level? That would be a chore to touch all devices and I really don’t know how to disable it on lots of things like the Roku and Amazon echo for example.
You asked about the ipv6 track setting and the answer is yes. That was the default value and I left it. Are you suggesting disabling it at the pfsense level, and if so, what is the best setting/option to do that?
I’ve seen my ISP address be ipv6 when I checked it online. It comes back ipv4 most of the time and ipv6 sometimes. Not saying this is related to my LAN IPv6 conversation but just something I remembered.
-
@djtech2k if you do not hand out IPv6 from pfsense - no client can use IPv6 be it how much they might want too.
Yes if possible disable it that client - you prob can't do it so much that they don't have it in the stack.. But in windows its pretty simple to turn it off, and prevent the extra noise the windows will be sending out if it has a IPv6 link local even..
Here is my window 10 client..
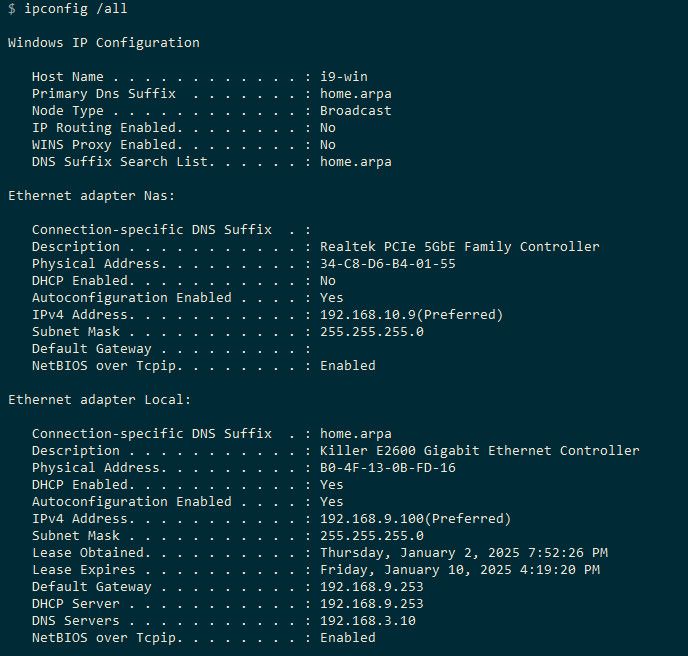
See any IPv6 ;) click on, click off is how easy it is in window 10..
Here is linux box
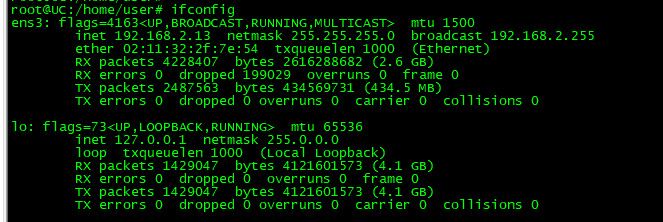
See any ipv6 link local address - nope.. Its still there in the stack on both systems, its not not enabled for any of the interfaces.
With pfsense - it would be more complicated to get rid of the link-local, but there is not GUA or ULA address etc.. here is one of my interfaces I don't even run IPv6 on
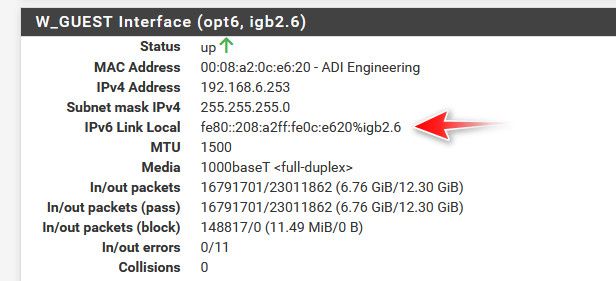
I do have it available on my network - and I can turn it on at will if want to play/test something, etc. But like I mentioned I have been playing with it for going on 15 years for sure.. And I would encourage you to do that as well - BUT!! if you are not ready to dive into it, and you don't understand it it - then from just from a security point of view I would not suggest you enable it if you don't not understand how to control it.. And if you do want to play/learn about it - enable it on a test network and play and learn vs turning it on for all devices in your network.
If you do want to play and learn - I would suggest you go over the IPv6 certification on Hurricane electric - going through the certification will get you familiar with the basics, and hey you can get a free tshirt ;)
https://ipv6.he.net/certification/
One of the users here just posted up that they got their tshirt ;)