Local DNS Records on different subnet
-
@stephenw10 Windows 11
-
OK so at the Windows command prompt do something like:
ROUTE -P ADD 192.168.11.0 MASK 255.255.255.0 192.168.0.100Where 192.168.11.0/24 is the pfSense LAN subnet and 192.168.0.100 is the pfSense WAN address. I don't think you ever said what the WAN address is so replace that. Earlier in the thread it looked like the pfSense LAN was using 10.84.0.0 so if it is then replace that.
If you then run
ROUTE PRINTin the laptop you should see that route in the table so it then knows how to reach the pfSense LAN. -
@stephenw10 so will that allow me to access my dns records pointing to traefik on my lan side, on my isp lan?
-
@jhmc93 said in Local DNS Records on different subnet:
dns records pointing to traefik on my lan side
DNS 'points' to A or AAAA addresses, TXT fleds, MX (mail server host names), CNAM (= other DNS fileds)
but not to traefik ? = traffic !? -
@Gertjan I have pi hole set up on my isp lan with an A record pointing to my traefik reverse proxy machine on my pfsense LAN
-
Yes that would allow your laptop to reach the DNS server behind pfSense.
Though I still advise against this entirely because it will cause problems down the line.

-
@stephenw10 what kind of problems?
-
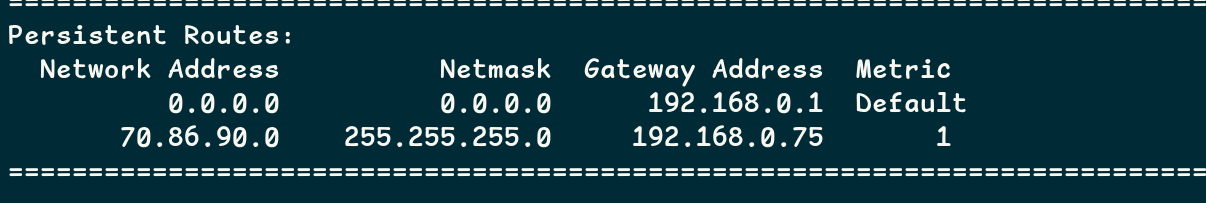
@stephenw10 so I tried it on a test machine, so IP is different, but what have I done wrong??
-
Because it relies on the client being configured to reach it then any changes on the client may break it. And in this circumstance that would mean the client loses DNS. If Windows is updated for example.
Or if you add some other client you have to remember to add the static route.
I imagine I could think of at least 10 ways this could bite you.
 I have seen many customers with similar setups where things mostly worked until they didn't.
I have seen many customers with similar setups where things mostly worked until they didn't.But for that one device it should work for now.
-
@stephenw10 look up, it hasn't worked unfortunately
-
Ok so 192.168.0.75 is the pfSense WAN IP address?
And 70.86.90.0/24 is the pfSense LAN subnet? A public /24 subnet?
That seems unlikely and you previously showed it as 192.168.11.0/24.
-
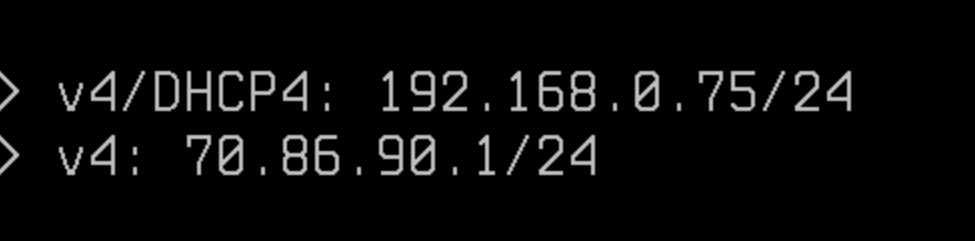
@stephenw10 so this is a test machine, not the actual machine that has the ip above, 70.86.90.0/24 is the test machine, 192.168.0.75 is the wan ip address as shown below
-
Then yes, that should work as long as firewall rules exist to pass it. And, of course, the target host in the LAN must allow it.
Start a continuous ping from the laptop then check the states on that test firewall to see if it's passing. Or the firewall logs to see if it's being blocked.
-
@stephenw10 ye it didn't work 4 me
-
@jhmc93 wa rulle should i have on firewall
-
A rule on WAN to pass traffic from your laptop to the internal host. Or to the full LAN side subnet.
I assume it shows blocked traffic in the log then?
-
@stephenw10 so how would i set the rule
WAN siide?
source?
destination lan subnet? -
On the WAN interface.
Source: The laptop IP address or the full WAN subnet
Destination: The LAN side host or the full LAN subnet
Protocol: icmp to allow pings or all to allow any traffic type.
-
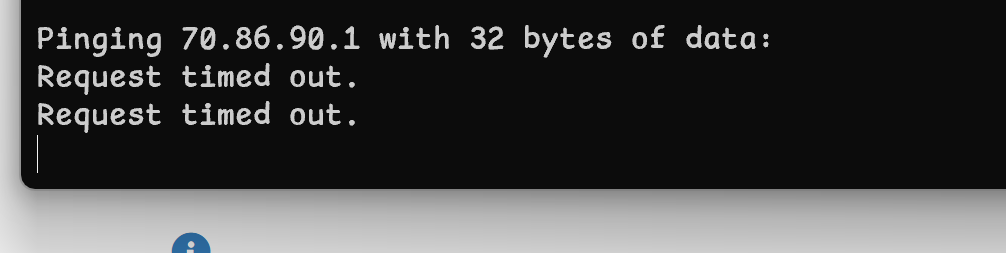
@stephenw10 So this is the outcome:
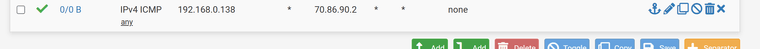
The rule I have set:
-
You are pinging 70.86.90.1 but your rule is passing traffic for destination 70.86.90.2. So it's not matching.
I assume you are seeing those pings blocked in the firewall logs?