Unbound/DNS resolver with IPv6 unreliable finally solved
-
allow_ or allow_snoop, thats one thing.
But what does is mean :access-control: ::1 allow_snoop
access-control: ::1/128 allowas ::1 and ::1/128 are the same for me.
So, allow_snoop gets set on ::1 and then overridden by 'allow' ?Here you can see how the access_lists.conf file gets created :
/etc/inc/unbound.incFirst, "127.0.0.1/32 allow_snoop" gets thrown in and then "::1 allow_snoop".
You and I don't chose the 'allowed_snoop' from the GUI here, it's hard coded.Then, all your local known interfaces, and this includes
127.0.0.0/8 allow
and
::1/128 allowand as said : these are the same for me.
Note that the 'allow' here is the one I set up here :
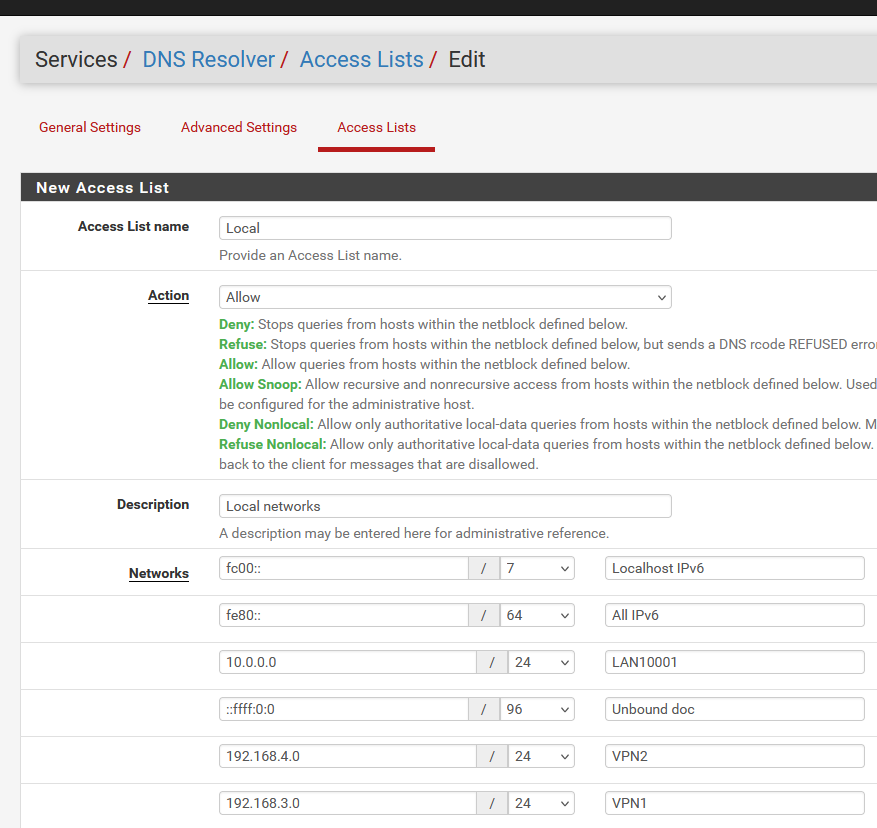
I wonder what happens if I delete these two lines :

-
It is possible to configure manually the "Allow_snoop", by choosing "Allow_snoop" under "Action" in the web gui of unbound under "Access Lists". The sequence of rules shown in the lower part of that web page are the same as the sequence of the rules in the access_lists.conf file. I'm currently testing to see if putting the snoop rule first or last has any influence on the end result, but so far I can't say that it seems to have any effect.
What I see is that after doing a change in the configuration the resolver will work for some minutes more, then be unresponsive for some minutes and then come back. I wonder if it is pfBlockers large DNSBL lists which need to be loaded before unbound can take care of resolving again?
After this down period of some minutes it again seems to be stable no matter if the snoop is first or last. The only thing I'm not able to reproduce is to make the rule in access_lists.conf 100% similar to the auto created rule:Auto created it looks like this:
access-control: ::1 allow_snoop
but when I manually create it I can't make it in any other way than this (mask needs to be selected, and if you do not select it will be auto created):
access-control: ::1/128 allow_snoop
I guess that should be the same, if it isn't a bug which makes trouble for the auto rule?
-
@strandte said in Unbound/DNS resolver with IPv6 unreliable finally solved:
It is possible to configure manually the "Allow_snoop", by choosing "Allow_snoop" u
Noop.
I selected some random "Refuse Nonlocal" :

this creates :
access-control: 127.0.0.1/32 allow_snoop access-control: ::1 allow_snoop access-control: 127.0.0.0/8 allow access-control: 192.168.1.0/24 allow access-control: 192.168.2.0/24 allow access-control: 192.168.3.0/24 allow access-control: 192.168.100.0/24 allow access-control: 2a01:dead:beef:a6e2::/64 allow access-control: ::1/128 allow #Local access-control: fc00::/7 refuse_non_local access-control: fe80::/64 refuse_non_local access-control: 10.0.0.0/24 refuse_non_local access-control: ::ffff:0:0/96 refuse_non_local access-control: 192.168.4.0/24 refuse_non_local access-control: 192.168.3.0/24 refuse_non_local access-control: 2a01:dead:beef:a6e2::/64 refuse_non_localso everything before
#Local
didn't change. -
Are you sure you have disabled the auto rules?
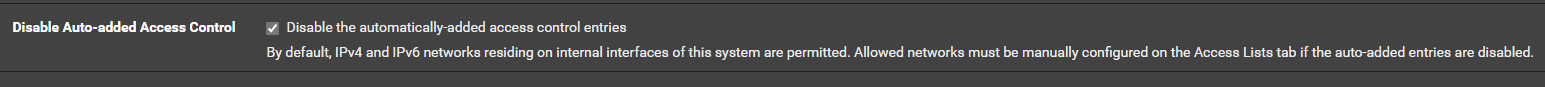
The access_lists.conf does not look like that in my case with auto rules disabled. -
When I check this :
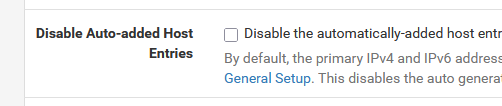
( which I don't have checked right now )
I have to create my own access list .... so more chances to f##k up.
I'm a "leave it to default" guy
-
@Gertjan said in Unbound/DNS resolver with IPv6 unreliable finally solved:
I wonder what happens if I delete these two lines :
a9c12224-4af3-4fde-8015-2265b6b91de5-image.png
I would delete
::1/128 allow, and add the/128CIDR notation to the::1 allow_snoopentry manually—and leave127.0.0.1/32 allow_snoopas is.But I agree that neither may be necessary as my auto-generated
/var/unbound/access_lists.confcontains only the ACLs I've defined via the webGUI. No loopback addresses are present. -
This post is deleted! -
@tinfoilmatt said in Unbound/DNS resolver with IPv6 unreliable finally solved:
127.0.0.1/128
Isn't that a 'syntax error' ?
127.0.0.1/32 is as far as it goes. -
I tried to add the:
access-control: ::1/128 allow_snoop
to my manual access list over the weekend. The result was that both the primary and the secondary firewall had a unresponcive unbond service on sunday. Today I have removed the access rule above. We will see how this goes.
Does anybody know what this rule is for?
-
Yes, 127.0.0.1/128 is wrong, and 127.0.0.1/32 is correct, but I see that the auto rule allow 127.0.0.0/8. Is that necessary? In case it is which other IP addresses in the 127.0.0.0/8 are in use?
-
@strandte said in Unbound/DNS resolver with IPv6 unreliable finally solved:
but I see that the auto rule allow 127.0.0.0/8. Is that necessary? In case it is which other IP addresses in the 127.0.0.0/8 are in use?
127.0.0/8 is a bit large, true.
Execute for example
sockstat -4 | grep '127'to see who is using 127.a.b.c
-
I can't see any othe address in the 127.0.0.0/8 used other than 127.0.0.1, so I would assume it would be ok to change out 127.0.0.0/8 with 127.0.0.1/32.
-
Sure.
Will it make any difference ?
Not sure. -
@strandte said in Unbound/DNS resolver with IPv6 unreliable finally solved:
After I setup monitoring I found out that the DNS resolver on the pfSense boxes often stopped for a while and then automatically started to respond to queries again, and that the problem seemed to be more pronounced for resolving via the IPv6 addresses of the pfSense boxes. Often the unbound stopped responding to queries done via the IPv6 address, but still responded to queries done via the IPv4 address. After a while both became unresponsive. When this was the case restarting the service made it respond to queries again, but I think it might also would have started again at some time if I had not done anything. When the service had stopped this would not be the case of cause.
I honestly don't think that the unbound control settings are related to this issue. Unless access control for unbound simply prevents its endless restarts and refreshes, which, in turn, solves one problem but clearly causes a thousand others. In fact, unbound was rock-stable for me on 24.11 and earlier. But it "broke" on the 23.05 beta because pfSense suddenly decided that now, every time it receives configuration packets (RA info) from the ISP, it needs to refresh and update all related settings, including unbound, even if no changes are detected in those settings received. When I started digging into this issue, I was surprised to see just how many requests there were to stop and restart the service — sometimes ending with it stopping and not starting again. Ideally, with proper Python module integration, everything should be much more stable, but sometimes it is not.
-
@Gertjan said in Unbound/DNS resolver with IPv6 unreliable finally solved:
Isn't that a 'syntax error' ?
Yes, typo. Post edited. Thanks for pointing out.