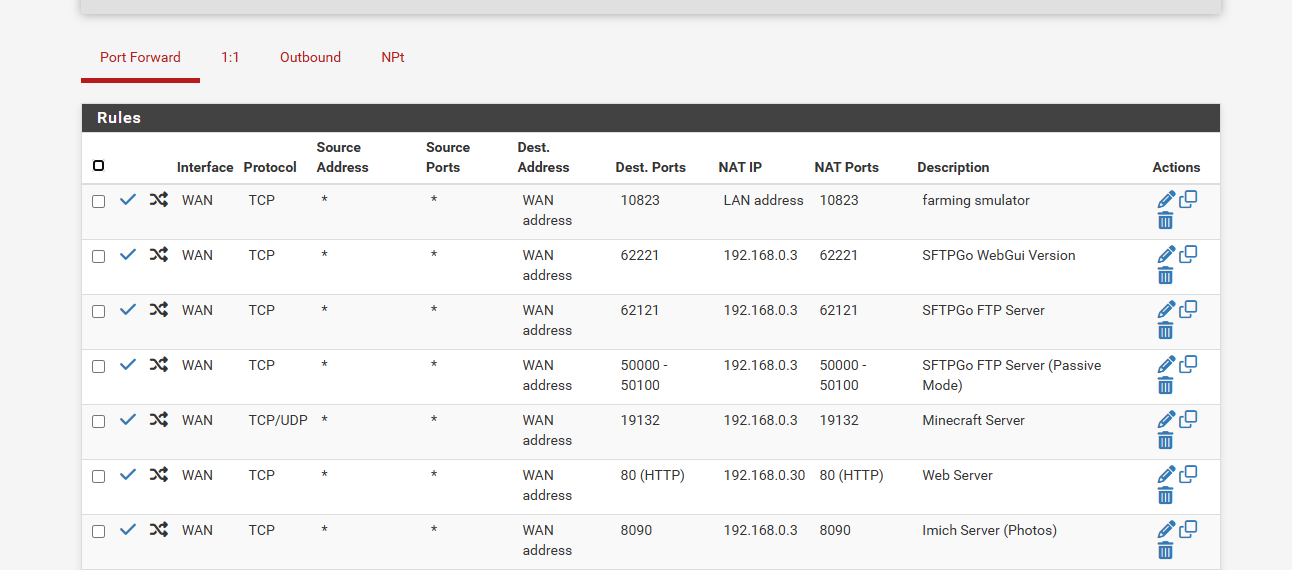
Port Forwarding stopped working after upgrading to 2.8.0
-
@stephenw10 i was able to figure out which pfblocker site was messing up home depot
its
cdn.cookielaw.org
it also screws up the cnn webpage too.. i had to find a video how you allow blocked lists. on pfblockerng.. so i got that solvedso my other issues still if the cira-cloud or cloudflare or isp shows up on your vpn side but you do not allow traffic of the vpn out the wan... does what you do on the vpn get tracked.. pia vpn customer support never bothered to email back.. as i still cant get these dns;s off the vpn side even when i tell pfsense to use 10.0.0.243
i use
103.86.99.100 in dns general for wan_ppoee to keep my internet connection alive.. if i dont it looses that dns and then nothing seems to work.. even if i dont have Enabled Forwarding of the DNS checked off in dns resolver -
@comet424 said in Port Forwarding stopped working after upgrading to 2.8.0:
i had to find a video how you allow blocked lists. on pfblockerng..
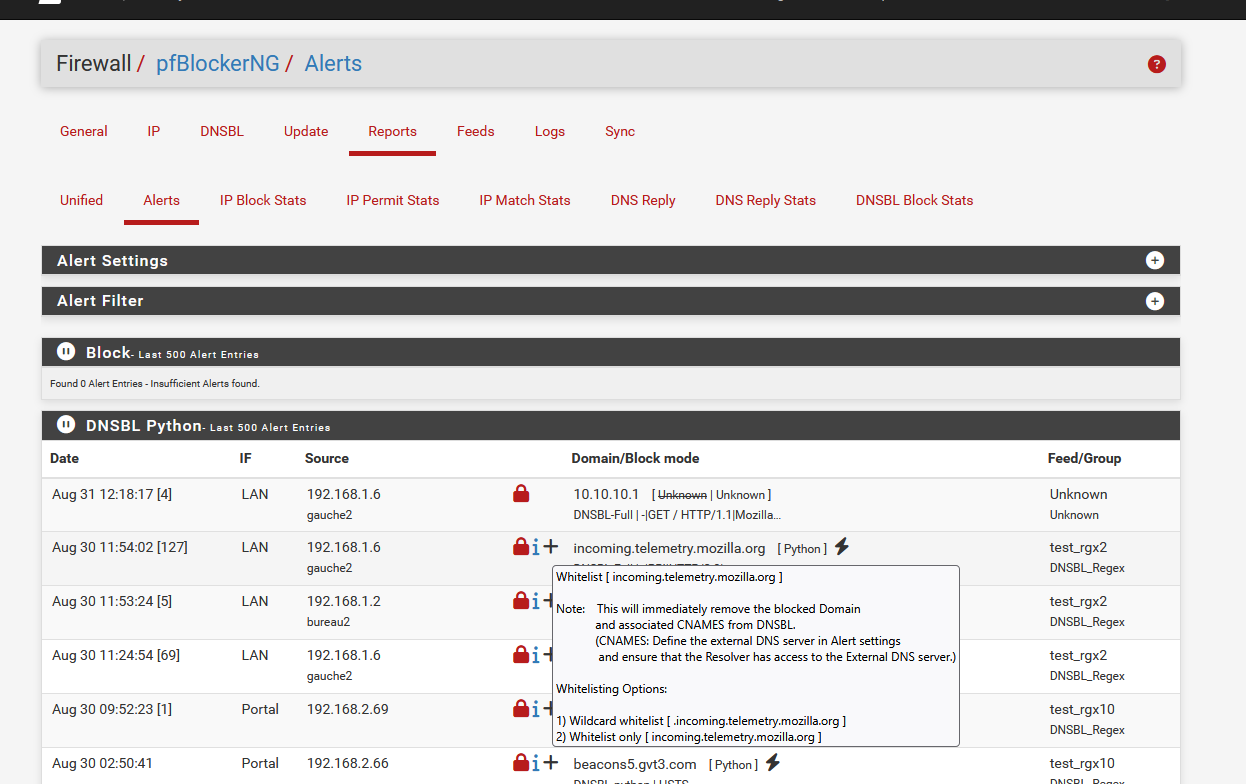
Hover your mouse over de black + (plus) and read the popup.
Click on the + and follow the instructions to whitelist, my example in the image : incoming.telemetry.mozilla.orgBtw : no need to allow blocked lists.
If you want to allow a list, just remove that list. -
@Gertjan ah ok ya thats what i had done.. and it then i did the add to the whitelist..
thats what i ment i done.. my stupid dyslexia i dont always explain things right..but ya how i figured out in the end that website makes home depot usless to search anything...
you dont happen to know about if different dns's on the vpn side if its leaking or not if it doesnt go out the wan.. i havent found an answer yet
-
@comet424 said in Port Forwarding stopped working after upgrading to 2.8.0:
you dont happen to know about if different dns's on the vpn side if its leaking or not if it doesnt go out the wan.. i havent found an answer yet
I don't know if my DNS leaks ....
I use the pfSense resolver as a resolver ( duh ... ) so it forwards my TLD requests to a official 'one-and-only' Internet Root Server (there are 13 of them). From there, it contacts a TLD so it gets the addresses of the official domain name servers, as I like to ask nsx.facebook.com what the IP of www.facebook.com is.
) so it forwards my TLD requests to a official 'one-and-only' Internet Root Server (there are 13 of them). From there, it contacts a TLD so it gets the addresses of the official domain name servers, as I like to ask nsx.facebook.com what the IP of www.facebook.com is.
To make a long story short : why should I ask Paul for the phone number of Jack ? Isn't it preferable to ask jack directly ?
Resolving means you can get a possible bonus : DNSSEC, if available, will protect you.Down side : it's a couple of ms slower, but ones the answer is cached in the resolver, it will keep the asnwer ready for you until you lose power.
Also : request are send in the open : like, to a root server : "gime the address of a dot com server (= TLD) ?" and then the request to the TLD : "gime the NS of facebook.com ?" and then the request to one of these NSs : gime the IPv4 of www.facebook.com".
So true : some one knows now I visited facebook ....VPN : never used it / no need for it. All my traffic, except for the DNS, is already TLS encryped/protected. Afaik, there isn't much none TLS left these days.
So, nothing leaks for me ^^
-
f you have Unbound set to use the VPN for outbound connections hen you need to have at least one other DNS server configured in general setup and pfSense set to fall back to remote servers in order to resolve the VPN servers initially.
You should not see that server in a leak test from clients though unless they are not using either Unbound in pfSense or being passed the VPN DNS servers. Or not being routed over the VPN at all. -
@Gertjan ah ok i think i understand..
ya i use dns resolver i set mine to All/all for inbound and outbound.. and use a no wan egress and in the vpn options i set the dns server of the pia vpn and since i have a lancache server i got told to uncheck the dnssec but even if i check it... dnslesttest still points to cira-cloud or my isp etc.. so i never know if my vpn i paying for is secure or if it just going out the vpn and big deal my isp is dns resolve from dnsleattest as its going through the vpn first ..i tried to ask pia vpn customer support . but cuz i asked for help for pfsense they just ignore me tell me they not going to help me to ask the communities for answers .. so its like a vicious circle lol
i feel i not leaking but the dnsleak tests and dnsleak websites tell you you might be leaking so i always confused if i am or if i not
-
@stephenw10 so right now
i use inbound/outbound set to ALL
i have to set an ip address in the general setup.. as my internet still goes down from the isp.. but if i stop computers from doing anything it will bounce back to work again not like before it i loose it all.. but even with all all and if i dont put an ip address in general/setup i find when the modem say it stalls out it doesnt recover till i do a reboot of pfsense..and i use nordvpn ip address in the general/setup and i get cira-cloud as a dns leak test on vpn side
if i use 1.1.1.1 for wan_ppope
i then get cloudflare on vpn dns leak tests
-
and if i just set
outbound on dns resolver to the pia vpn... i set no forwarding.. and i dont have an ip in the general setup... i can get a pia vpn dns i guess but my internet stalls out and stops working and i loose dns resolving all i can do is ip pinging...so i havent found that sweet spot of i know 100% not leaking internet will always work for wan and vpn clients.
and even if my modem stalls it will bounce back without needing a reboot or so..
-
Ok so what are clients on the internal network that uses the VPN being passed to use for DNS?
Is all their traffic being routed over the VPN?
-
ya all the traffic i route through the vpn.. except like my Webserver.. some xboxs to try to stop double natting, gaming comp.. my iot devices and cameras that update through the wan but dont use vpn.. all my other devices tablets comps vms all go through the vpn.. except a few VMS that are on WAN but majority everything
so thats where i have Vpn_clients alias all those ips use VPN and ive done No_vpn_clients alias ips or i just did Lan subnet * * * * after the vpn clients..
and i have that bypass policy as i learned if i wanted to have split wan and vpn and over the network i needed to have thr routing bypass policy thats in front of everything
-
So are you passing specific DNS servers to those VPN clients or are they using the pfSense interface address?
Are you routing even DNS queries from those clients over the VPN or are they bypassing the rules and allowed to the local interface?
If all traffic, including DNS, is routed over the VPN then it cannot leak from some local resolver.
-
@stephenw10
im not 100% sure?? not sure what you all mean sorryso all LAN use 192.168.0.1 as the dns and gateways for VPN and WAN clients
on the other Vlans they just use default so 192.168.10.1 for camera network thats the dns for that
192.168.20.1 dns for the IOT network and so onfor the lancache.. server it is 192.168.0.32 where all the host over rides goto .. and the uplink is 103.86.96.100 dns i just used it as thats what i had.. from nordvpn
now under the VPN PIA as dhcp options i use
persist-key persist-tun remote-cert-tls server reneg-sec 0 auth-retry interact dhcp-option DNS 10.0.0.243the 10.0.0.243 is the dns for PIA vpn.. now i seen some use semi colon on the end and some dont.. but neither made a difference..
and for my 2nd pia vpn i use 10.0.0.242 as the dns as i tried using the same 10.0.0.243 but found no differenceas for bypassing the rules i dont think they do????
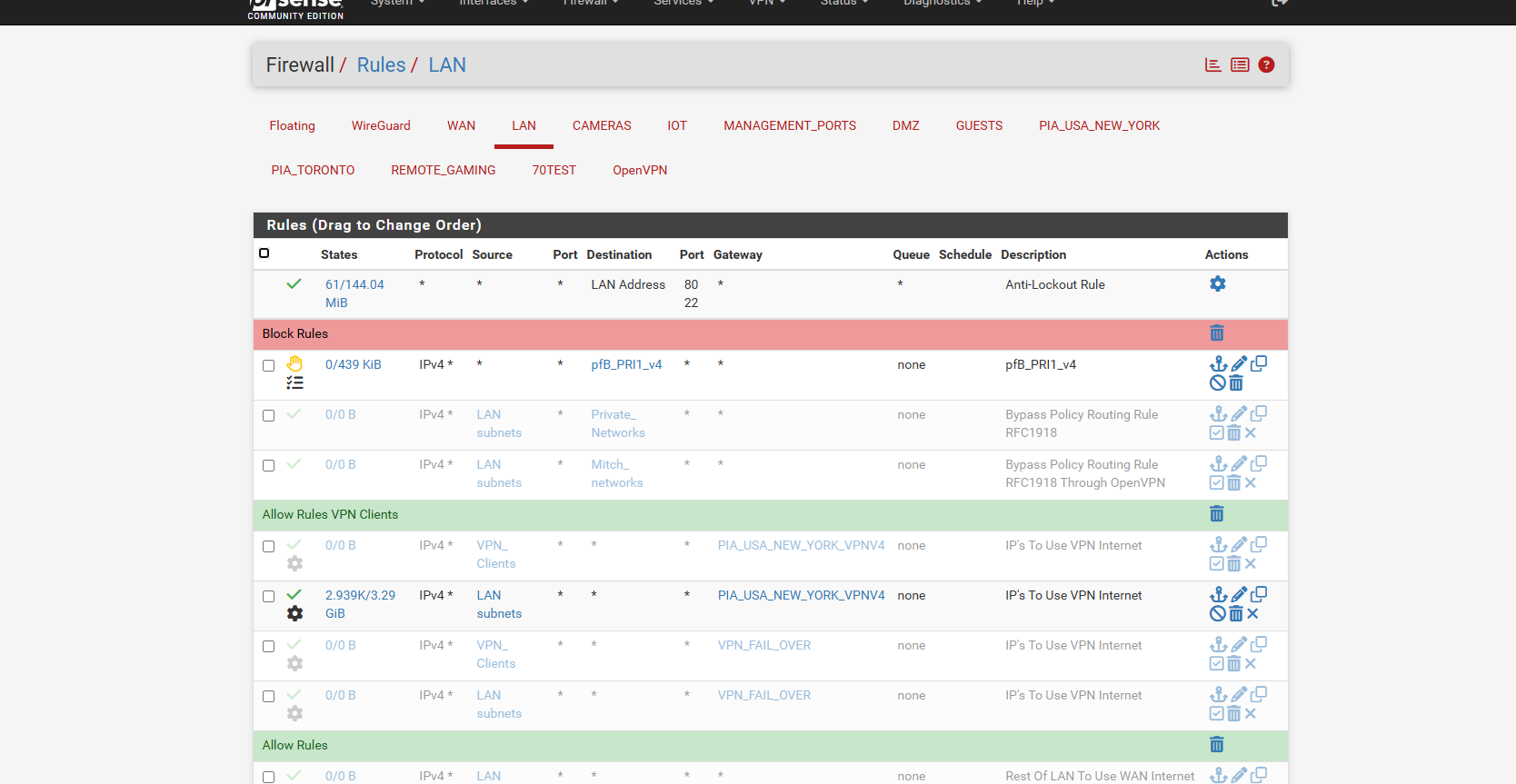
first line is pfblocker
2nd line is the routing bypass policy
3rd line is the vpn clients out the vpn gateway
4th line is the wan clients out the wan gatewayi also watched another video where in the NAT rules for the VPN he didnt use the PIA interface.. but used the WAN interface NAT part.. i not sure if that makes a difference or not
if u need more screen shots i can post them if u need to see more..
-
Ok so all clients are using pfSense for DNS. Both VPN and non-VPN clients. So that means to avoid a 'DNS leak' reported on vpn clients that Unbound must send all queries over the VPN. Either by resolving using the VPN interfaces only or by forwarding to the PIA DNS servers only.
That does mean that if the VPN is down no clients will be able to resolve. Both vpn and non-vpn clients.
I'm not sure why you have added the DNS servers to the VPN client config. Those should be passed to you by the server. But Unbound won't use them there either way. It can only forward to servers configured in general setup.
A better setup here would be to put vpn clients on a separate interface. That way you can easily pass them different DNS servers to use etc.
-
@stephenw10
hi ok
so the reason i do the dhcp options part wht the dns is thats the PIA VPN instructions they tell you to type it in there.. and then you choose 1 of the 3 dns servers they offerand then i have the Forwarding unchecked
so that sucks you cant do both without leakage
so for the better setup
so you mean do
LAN IPS would not use VPN
VLAN 5 IPS would use the WANlike how i have it right now IoT Cameras DMZ Vlan use WAN so its not a split Internet on the same interface
so would i change anything special?
and the reason i left a dns ip address in general setup.. even when i dont check Forwarding in the dns resolver with the dhcp options ip address. is even with that my internet goes down and it doesnt bounce back till i reboot or its given time..
so when i have the current setup with the dns leaking on the vpn side... is it actually leaking?? or is it just falsly reported.. do you happen to know? as i learning on the go and when you try to google you cant find info... so like is the actual cloudflare or isp seeing what your doing out the vpn side?
and do i need that bypass routing policy then as i read i needed that when you do split internet like wan and vpn
and over multi interfaces -
Yes, like that. Use a separate VLAN for clints you want to use the VPN.
Pass clients on the subnet the VPN DNS servers to use dircetly.
Route all traffic from those clients over the VPN and block traffic not routed.
That will prevent leaks and should also no longer drop the VPNs etc. But it will mean VPN clients can;t use the lancache or any other local resource.
-
@stephenw10 ah ok... and well that sucks
so there really isnt any good ways to get both worlds and use a lancache..if i put the lancache server as one of the vpn clients.. can then the WAN clients use the lancache?
and how come dns leaks when i split vpn and wan on the same ips like the lawerance systems videos dont even say when you follow his instructions that dns leaks .. and i still dont know why the one video shows using WAN interface of NAT for the PIA VPN
guess stuff just isnt as simple... i guess i wouldnt have the problem if my internet was fast and you just run it all out the vpn lol
but ya ill try to transisiton my VPN or WAN clients to a seperate Vlan then.. do i still need that routing bypass policy?
-
so i toggled teh routing policy off for now
i set that LAN only uses VPNi find my desktop pc still getting ISP dns but if i run a firefox Docker i will get it to goto teksavy
i left the dns resolver to all/all for inbount and outbound.. and unchecked dnseq and unchecked the forwarding.. and removed the ip address's in the general setup
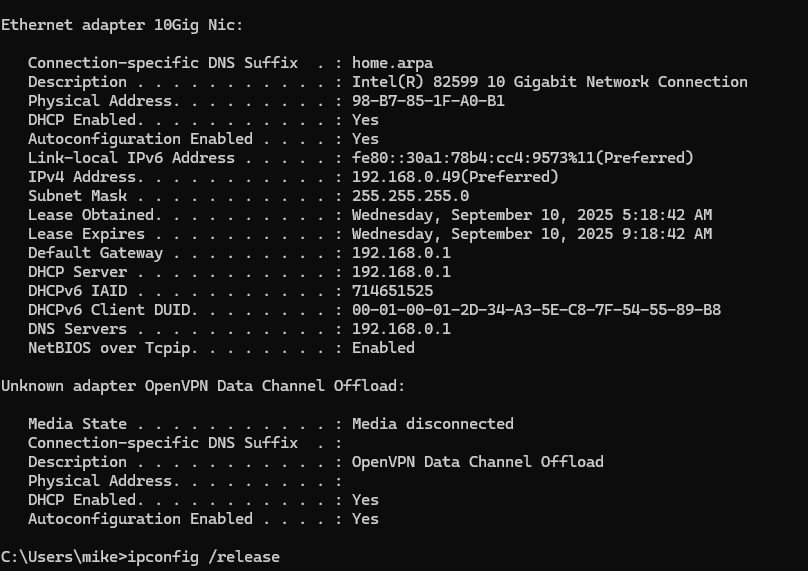
i did run
ipconfig /release
ipconfig /flushdns
ipconfig /renewbut it still retains isp as a dns
i made sure in the dhcp settings that gateway and dns are 192.168.0.1but still pointing wrong dns is there other spots it saves dns
i not getting good tests at this rate -
can you do VPN on LAN and WAN on the VLAN
or do you need to start things
LAN = WAN
Vlan = VPNas i seem to having dns issues if i leave it as VPN = LAN and WAN= VLAN5
as i get isp dns on my gaming desktop when behing the VPN etcgoing to play around but also trying to understand more
-
@comet424 said in Port Forwarding stopped working after upgrading to 2.8.0:
i find my desktop pc still getting ISP dns but if i run a firefox Docker i will get it to goto teksav
....
ipconfig /release
ipconfig /flushdns
ipconfig /renewYour PC uses DHCP, right ? By default, it does.
Double check that you didn't set a DNS (statically) yourself on this PC.If DHCP : The DNS the PC got was given by the DHCP server - which is (should be !) pfSense.
Check that :
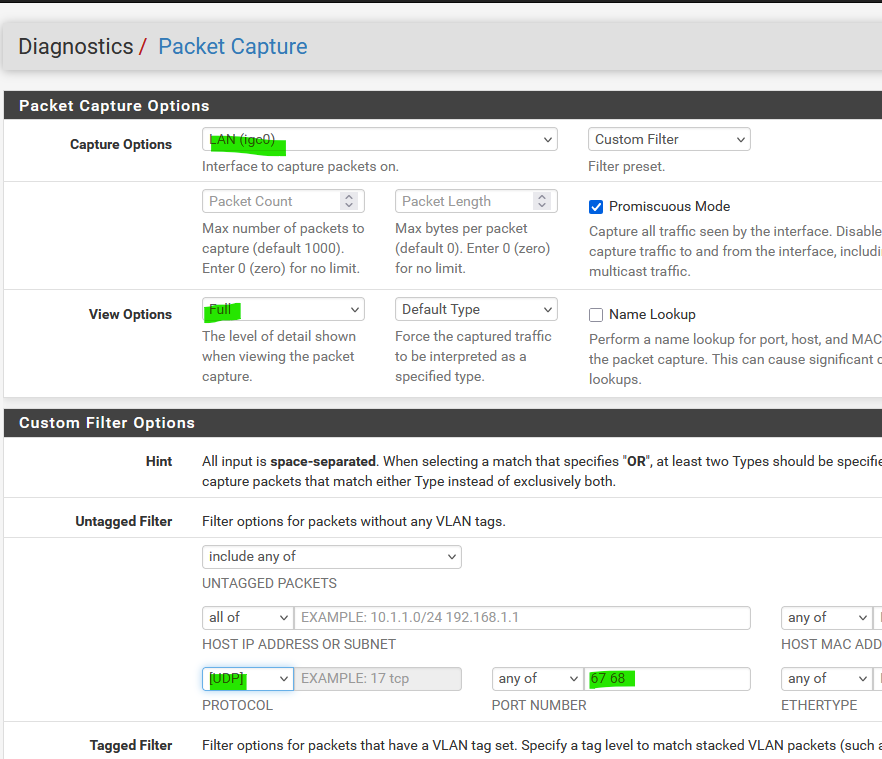
-> Use another PC to access the pfSense GUI !.
and hit Start.
Now, on the PC :ipconfig /release
ipconfig /renewand get back to pfSense.
You should seee the DHCP request from the PC, and the pfSEnse DHCP answer - with the gateway, DNS, etc etc.
What DNS was given by pfSense , By default it is the LAN I of pfSEnse.
If it isn't, that could be explained because you've selected :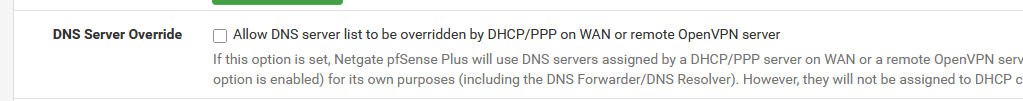
Or you've set (DHCP > LAN server) :
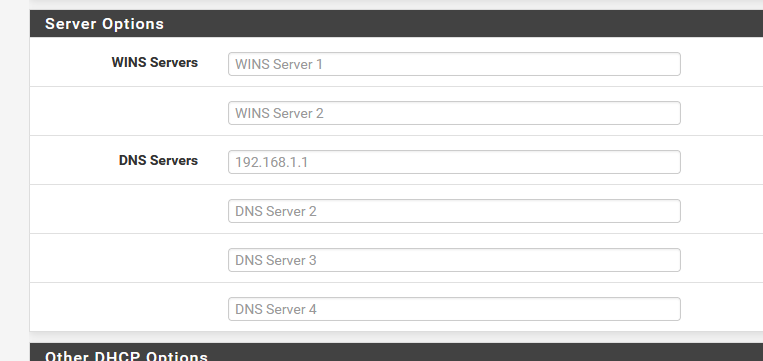
to something else ?
-
@Gertjan
ok so i tried that.. i also had googled about pia and pfsense and tried to go several google searches in.. as what i find is like the lawerance systems and couple others they dont touch that dns resolver.. they did what i did ips on the same lan so novpn and vpn clients and do the no wan egress.. but none of them ever talk about dns leakage,, but i find it leaks.. and i not 100% is it ok for the dns to leak on the vpn side if no traffic goes out the wanso here is the tests and i commented a bit too
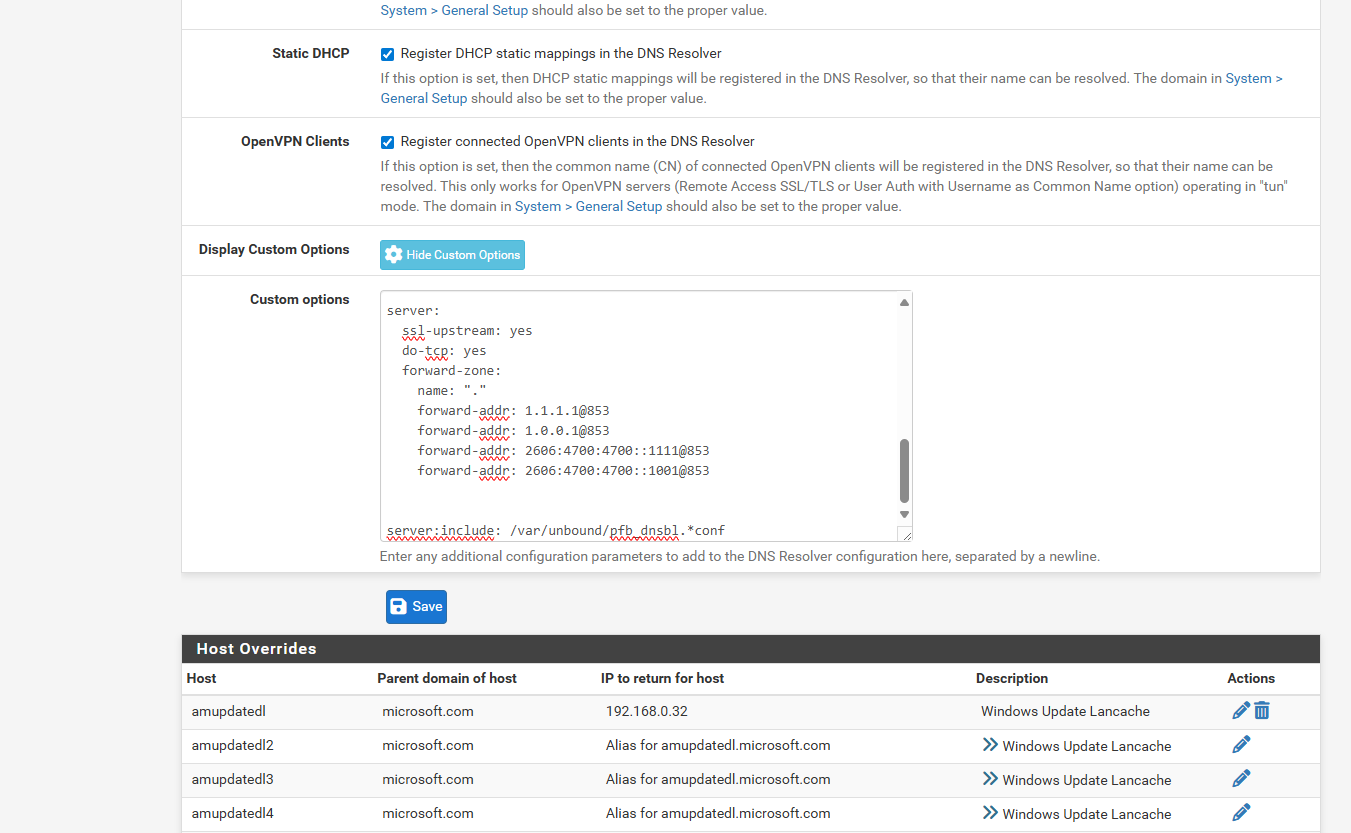
i also followed a couple other articles where they tell you to add custom options code in the dns resolver.. since i have it set All Inbound just 2 PIA VPns as outbound
i in the dhcp settings for the desktop pc i had left the dns and gateway blank.. this time i entered in 192.168.0.1 but it didnt help i still got a dhcp for 192.168.0.1packet capture
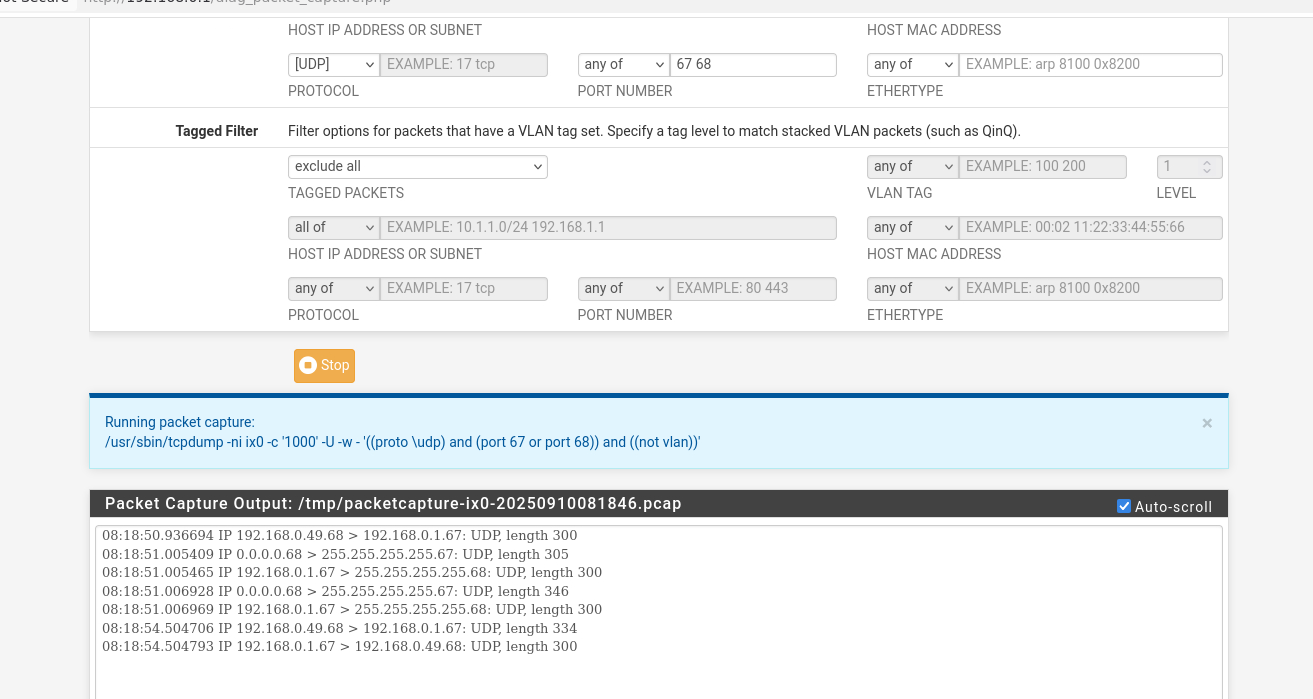
windows dhcp ipconfig /all
rules I set everything on the LAN to just go out the one VPN and not the 2 vpns or the WAN for now
DNS Resolver.. Inbound All, Outbound to the 2 PIA VPNS. and i followed couple sites they add the server: forwarding for custom options.. i guessing this is for the when the vpn goes down wan cant be resolved anymore and it fails to reconnect..
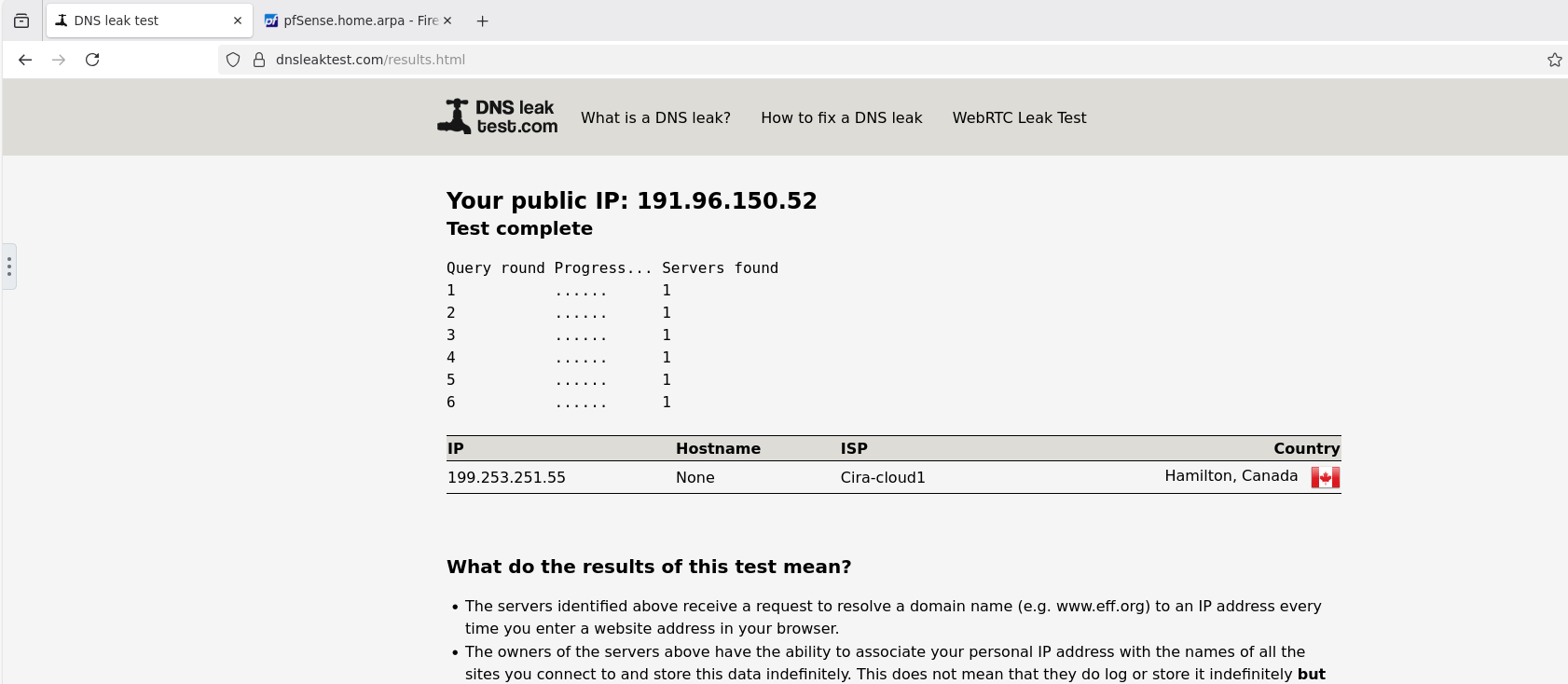
Fire Fox Docker Browser #1
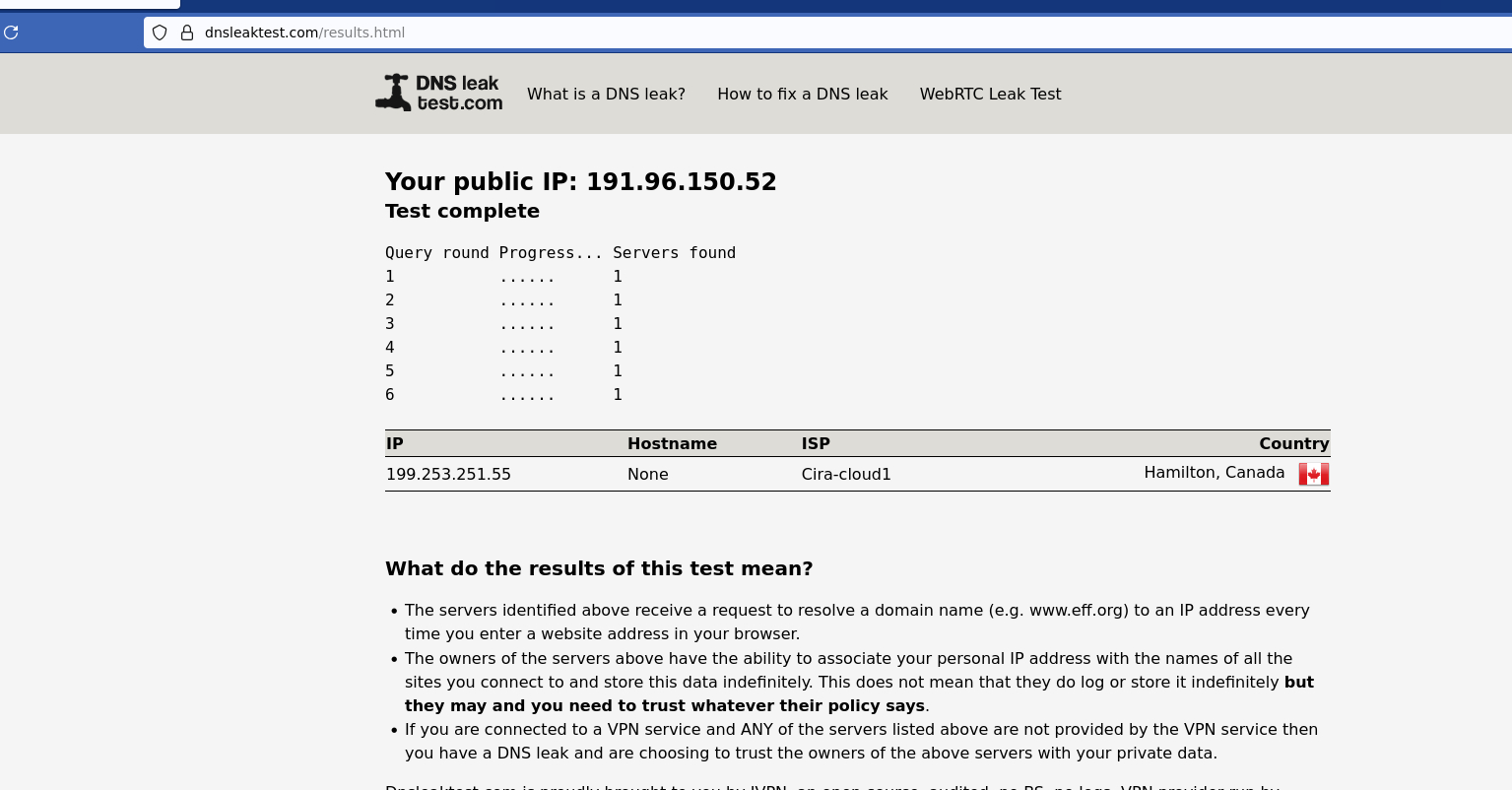
Fire Fox Docker Browser #2
Windows Desktop IE Browswer
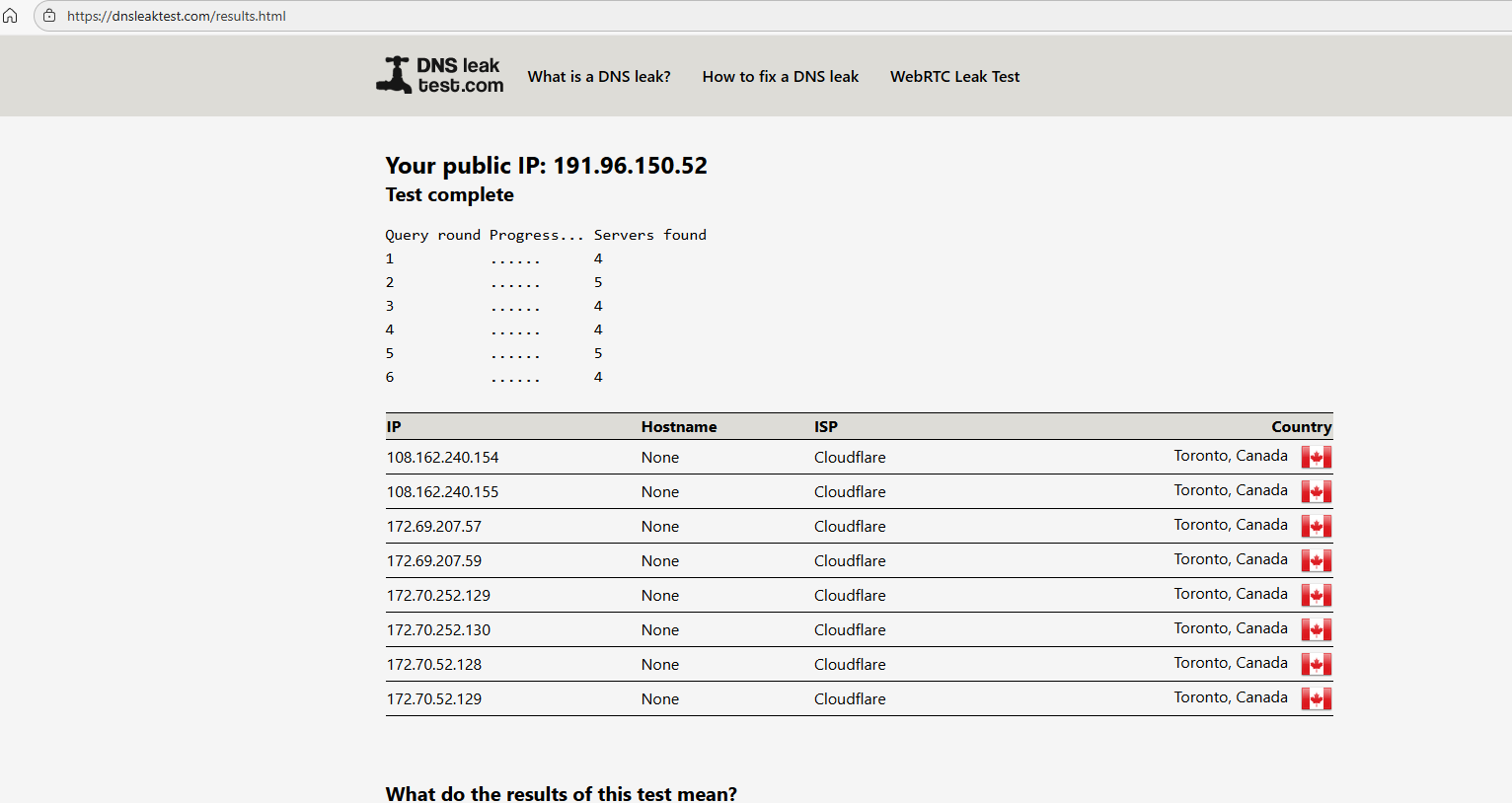
yet all are behind the same firewall.. this is probably why i cant seem to figure out why am i truly leaking or what not but seems the windows desktop says i am
here is the github dnsleaktest you download and run on windows or linux here is the same desktop
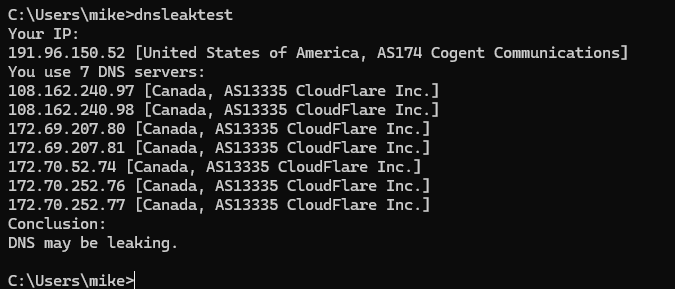
so i been confused for months and thats probably why this question form i posted has gone on forever cuz i truly never figured whats going on or how to make wan lan ips and vpn lan ips seperated and secure.. and the videos and articles never address this..
and i confused why my desktop pc is always pulling dns even when it should be pulling vpn
and when you run the dnsleak.com website for PIA leak test.. on the 2 Firefox docker.. they tell you its leaking.. so its not even working like they supposed to be.. cuz it throws a whole bunch of ips of the cloudflare
so dnsleak.com sees the cloudflare ips the dnsleaktest.com doesnt see that but sees the cira one but should be i guess teksavy
so ive never figured out this rolling headache lol