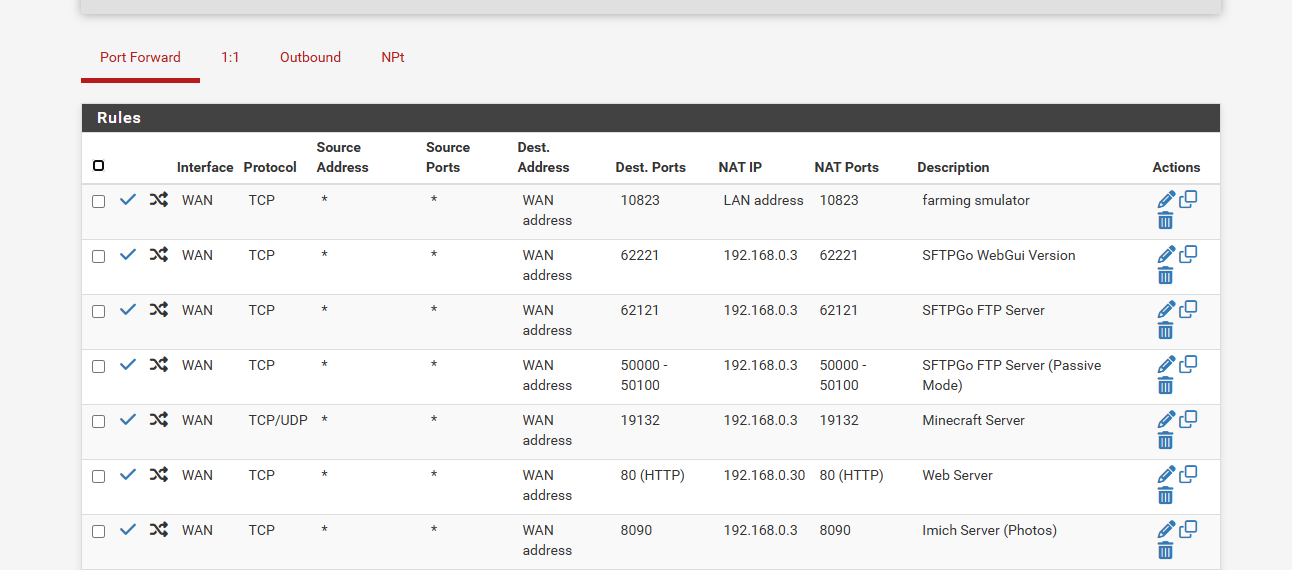
Port Forwarding stopped working after upgrading to 2.8.0
-
oh and seems now my firefox dockers now pull cloudflare behind the vpn
i guessing its because of that custom options... after i did a server reboot.. the firefoxs are now getting like 20 cloudflare and not just vpnthis is my current dns resolver
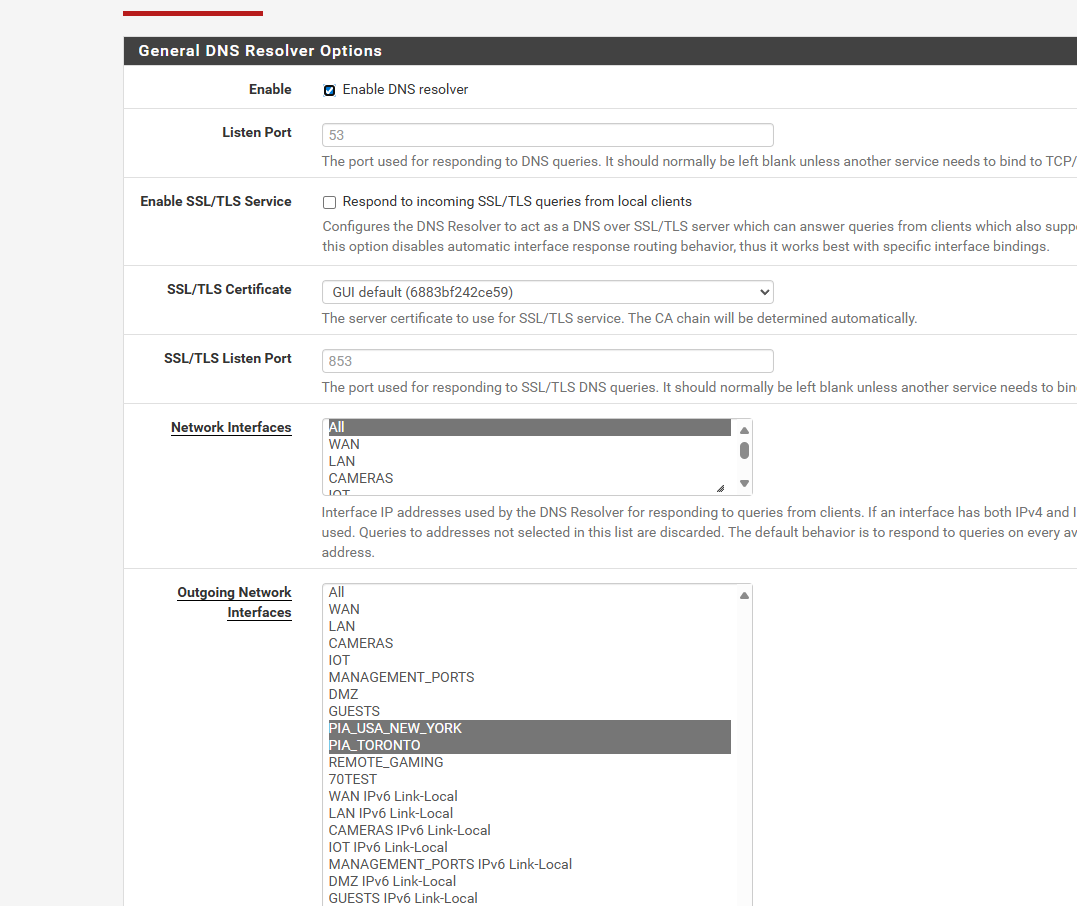
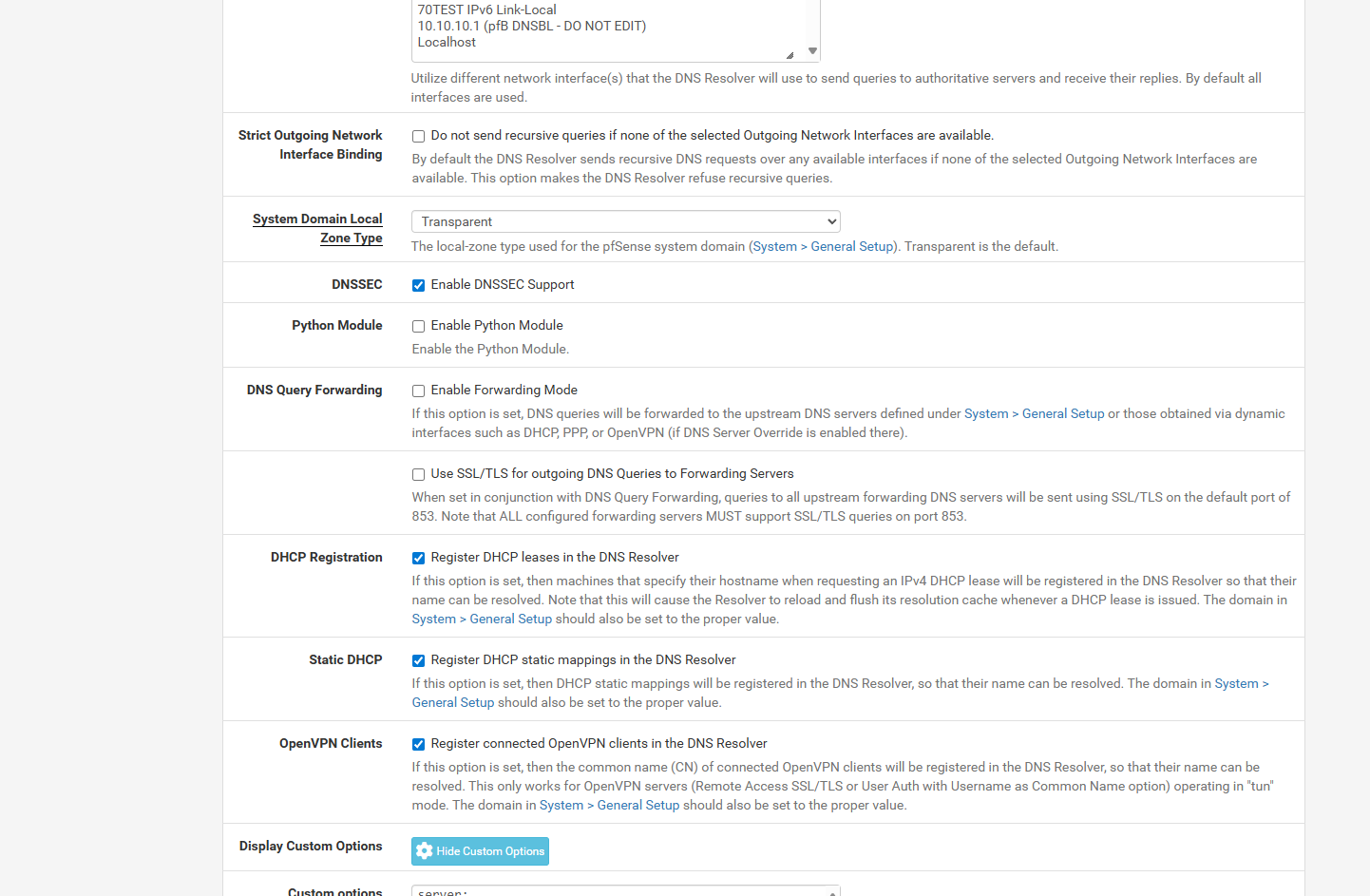
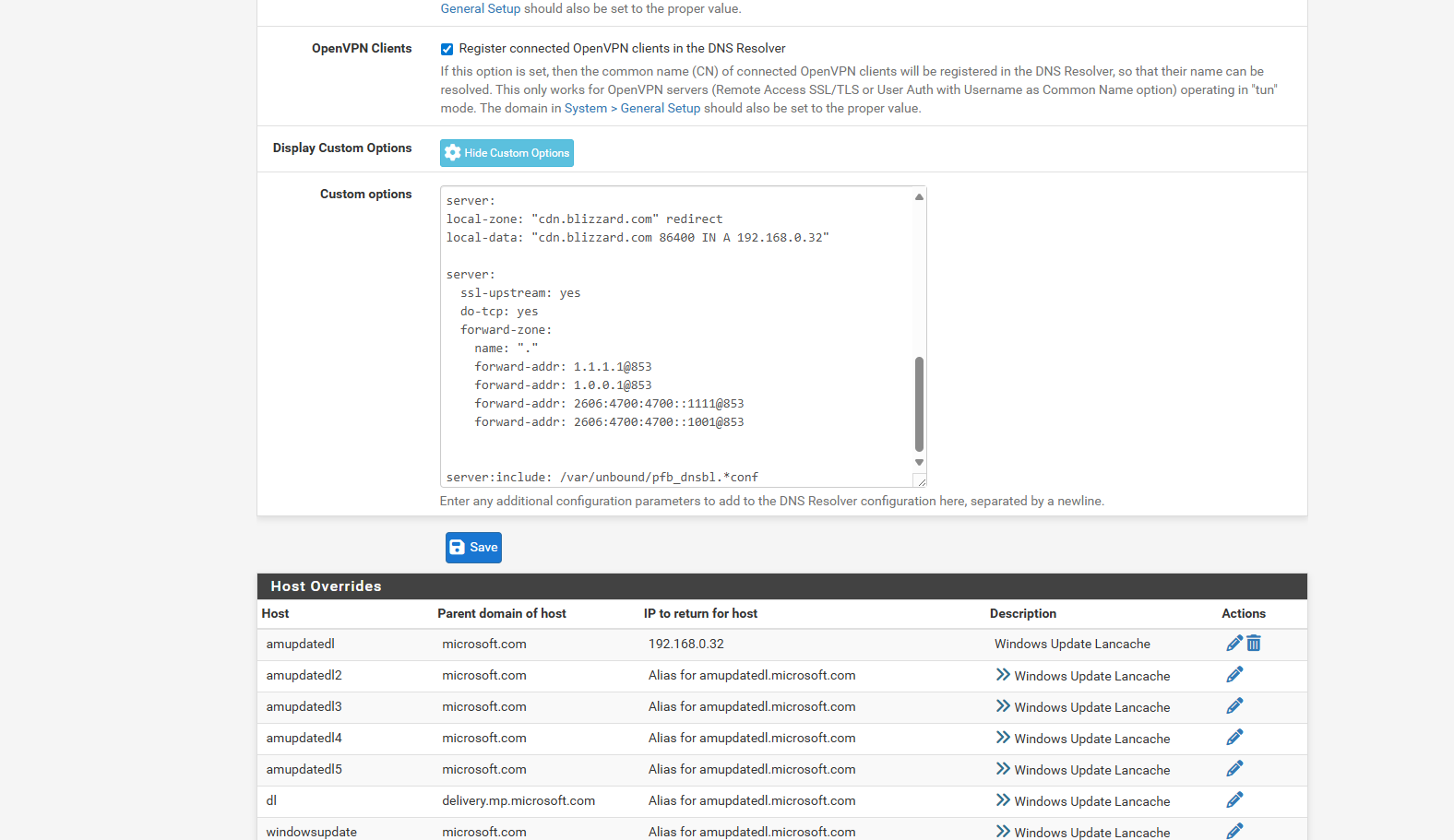
-
i cant find the 2 articles now that showed those server options
but here this article i read
https://undergroundmod.com/2023/07/15/private-internet-access-vpn-on-pfsense-last-updated-08-2023/talks about this
Important DNS Note If you are not using DNS over TLS to a trusted, privacy oriented DNS Resolver like CloudFlare’s 1.1.1.1, then you will leak your IP over DNS and this could be a problem To get around this, you should hard code PIA’s DNS servers on the system you are putting over the VPN. The DNS servers are 209.222.18.222 and 209.222.18.218 Be sure to check if your DNS requests are leaking your normal public IP: https://www.dnsleaktest.com/ Setting these DNS server will probably affect local DNS resolution, so you should really just use DNS over TLS… https://www.netgate.com/blog/dns-over-tls-with-pfsense.html You could create some NAT rules to intercept DNS requests and force them elsewhere, but it’s more work than just using DNS over TLS, which you REALLY should be doing anyway… Thats it!not 100% sure what that ment but i just tried enabling the Enable SSL/TLS Service in the dns resolver
i get confused cuz there isnt 1 straight setup for no leaking no issues lol makes you wanna drink
-
if you guys got screen shots how PIA or any VPN should be setup on the LAN like with 192.168.0.0 like i have grayed out . no_vpn_clients and vpn_clients
and what the dns resolver NAT should look like.. so i can just duplicate it.. so there is 0 dns leakage.. as these google searches arent helpingand or should i make a new post ask for anyone that has PIA and NonVPN Clients Have Screen shots for a secure network? i was hoping when i orginalyl started thread.. someone with PIA had this setup and secured and could supply screen shots..
if i ever get this solved. i going to make a thread with the right procedures so someone like me doesnt go through these headaches
-
OK adding those custom options in Unbound is forwarding all queries to Cloudflare. No matter what else you have set in the Unbound setup.
But without any DNS servers set in General setup then pfSense itself can only use Unbound. If that is configured to only use the VPN interfaces for outbound queries then it cannot resolve anything until the VPNs connect and that's a problem if the VPN servers are defined as an FQDN instead of an IP.
-
@stephenw10 so i running in circles..
currently this is what i got i took out those custom options
i can get it to say not leaking if i use 103 ip address which is a nordvpn dns on the WAN
but if i use 1.1.1.1 then it leaks like a ship with 20 holes in it.. i getting frustrated.. and this article at the bottom tells you to use dns over ttls.. and use like 1.1.1.1 for a secure dns leak free but its not making sense and it leaks using 1.1.1.1
this is the article
https://undergroundmod.com/2023/07/15/private-internet-access-vpn-on-pfsense-last-updated-08-2023/this is the bottom not.. and those ips dont work
Now we have done that, you should be done. Everything on those IP’s in the alias will go over the VPN. If the VPN disconnects, no internet traffic will pass and as long as the IP doesn’t change, traffic CAN NOT go over the normal gateway Important DNS Note If you are not using DNS over TLS to a trusted, privacy oriented DNS Resolver like CloudFlare’s 1.1.1.1, then you will leak your IP over DNS and this could be a problem To get around this, you should hard code PIA’s DNS servers on the system you are putting over the VPN. The DNS servers are 209.222.18.222 and 209.222.18.218 Be sure to check if your DNS requests are leaking your normal public IP: https://www.dnsleaktest.com/ Setting these DNS server will probably affect local DNS resolution, so you should really just use DNS over TLS… https://www.netgate.com/blog/dns-over-tls-with-pfsense.html You could create some NAT rules to intercept DNS requests and force them elsewhere, but it’s more work than just using DNS over TLS, which you REALLY should be doing anyway… Thats it!and here is my current setup what am i doing wrong
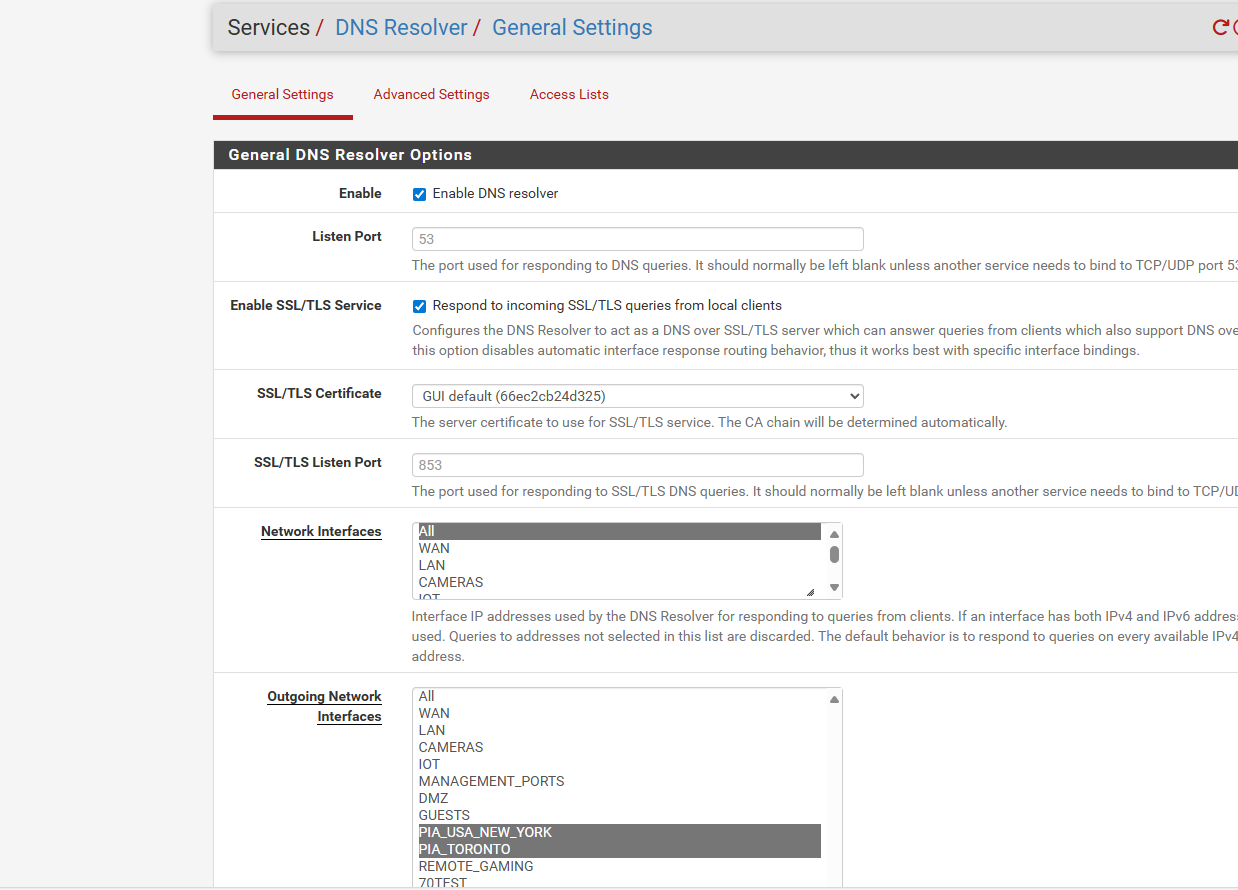
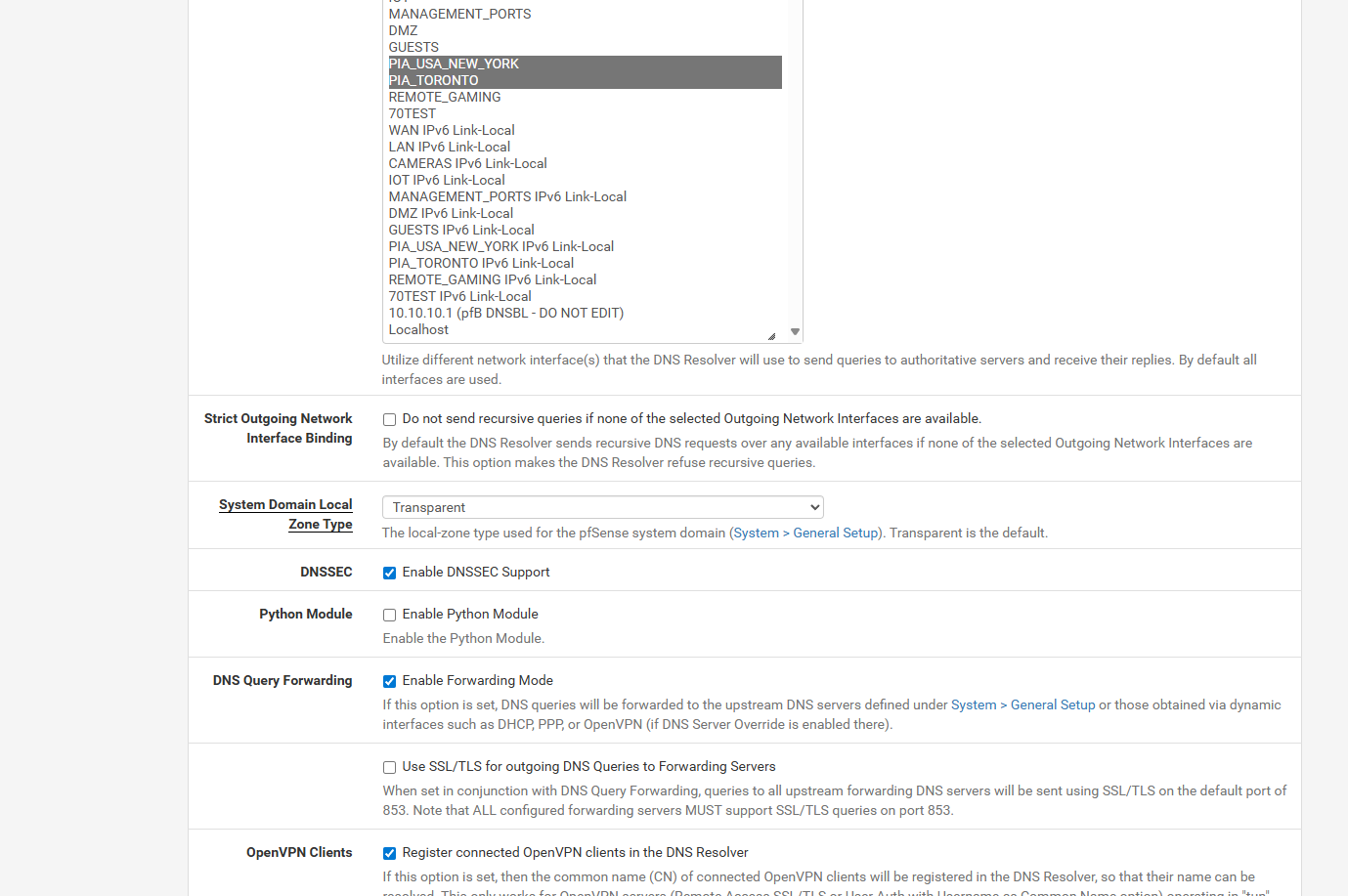
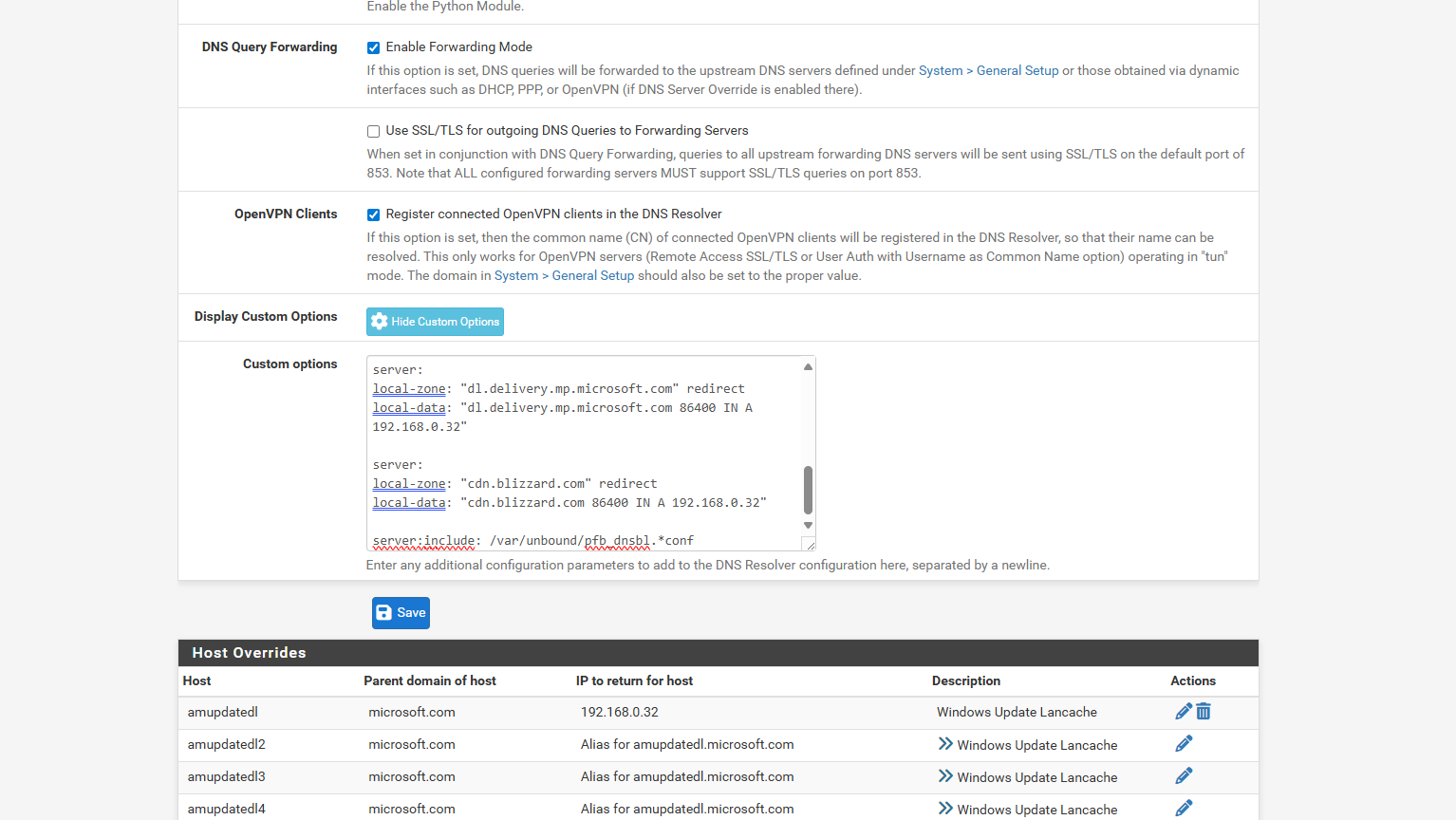
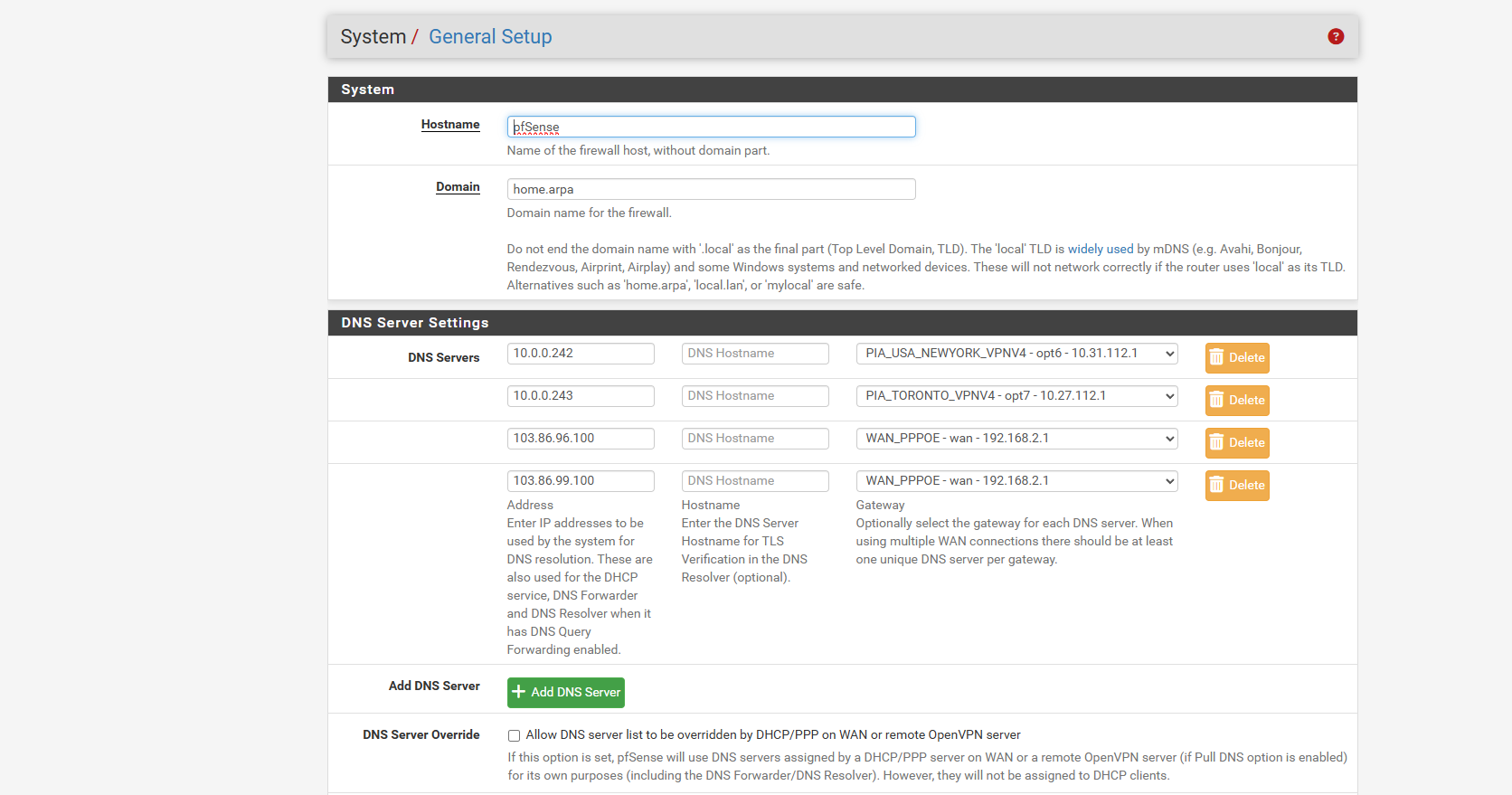
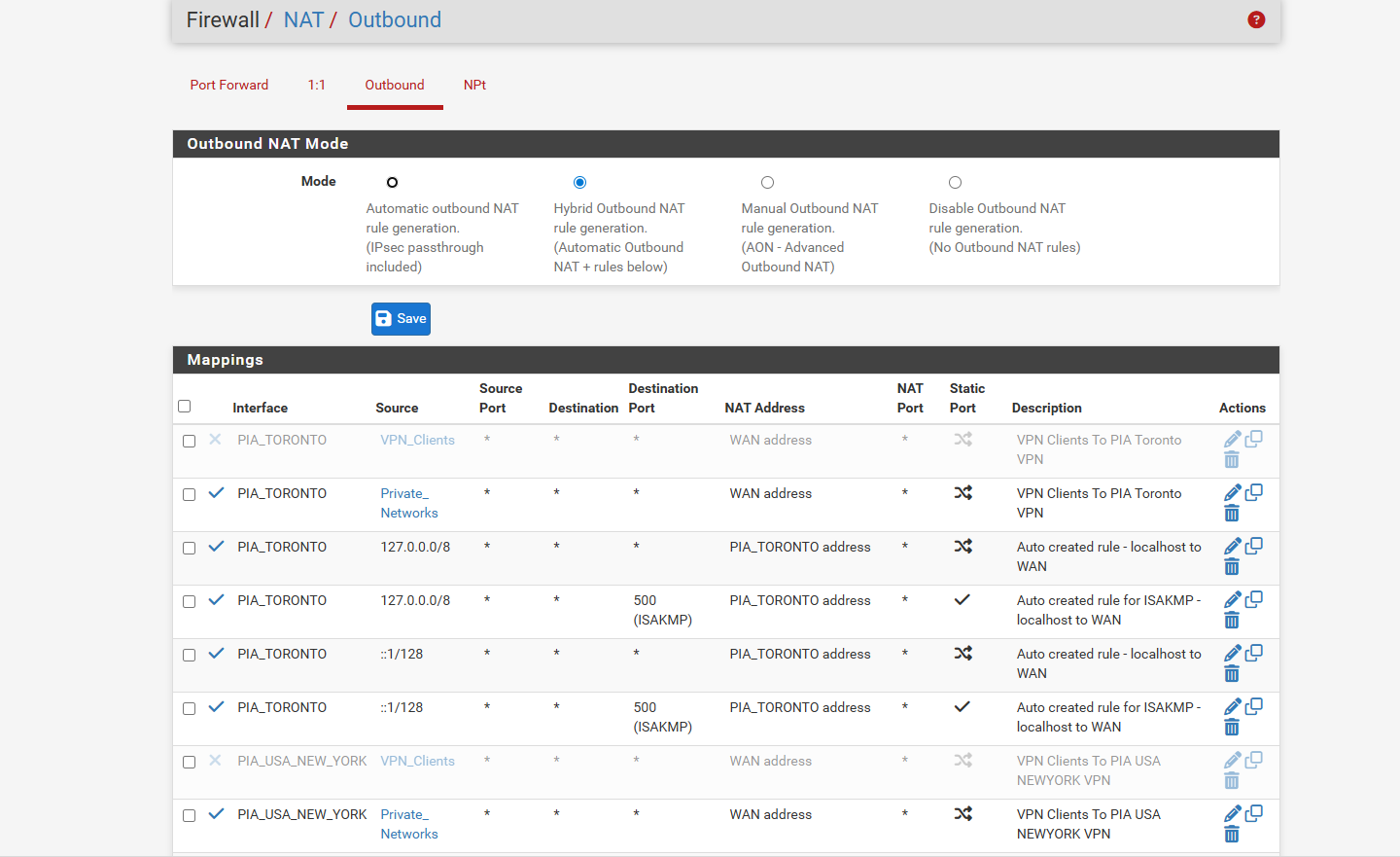
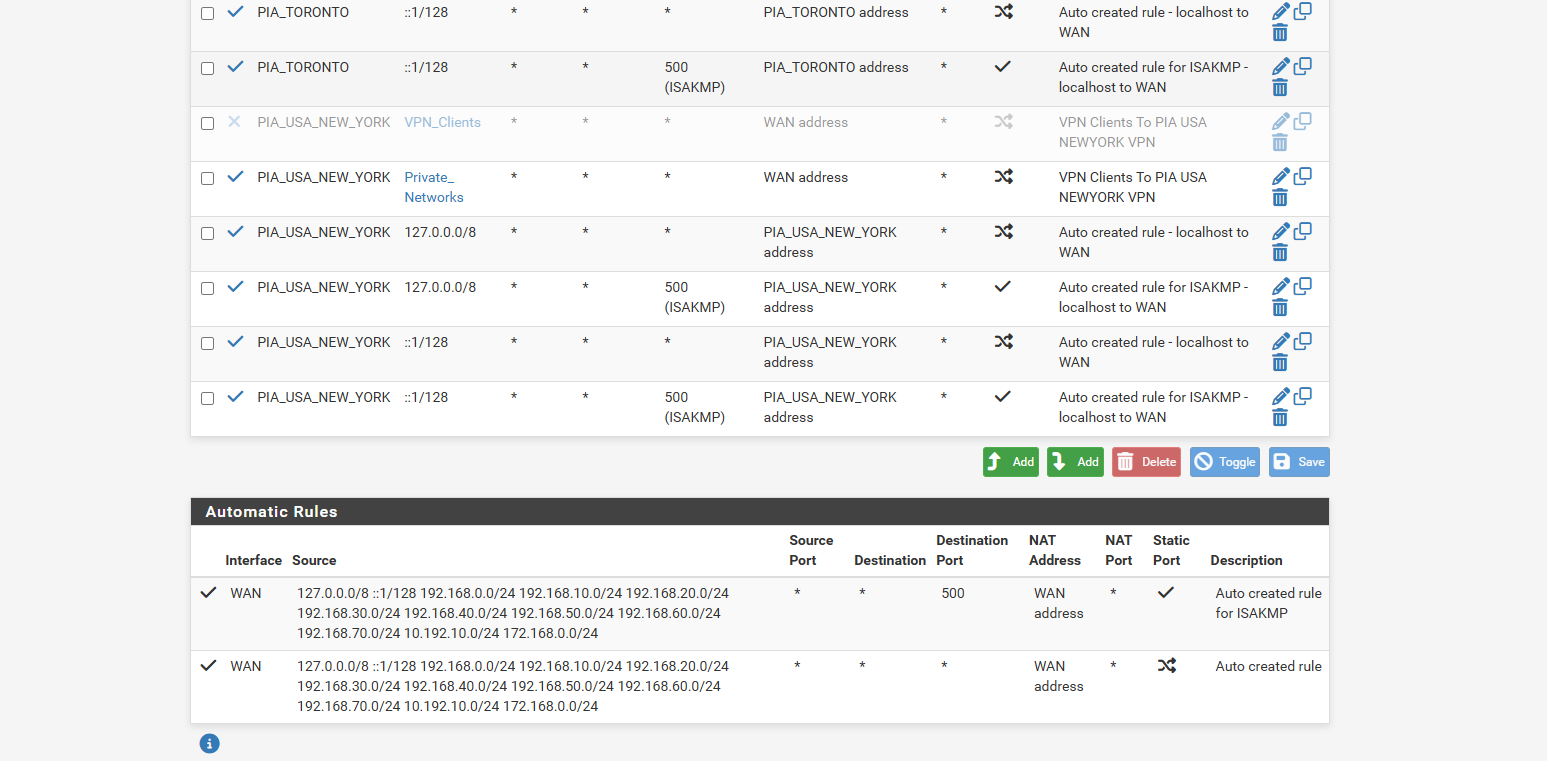
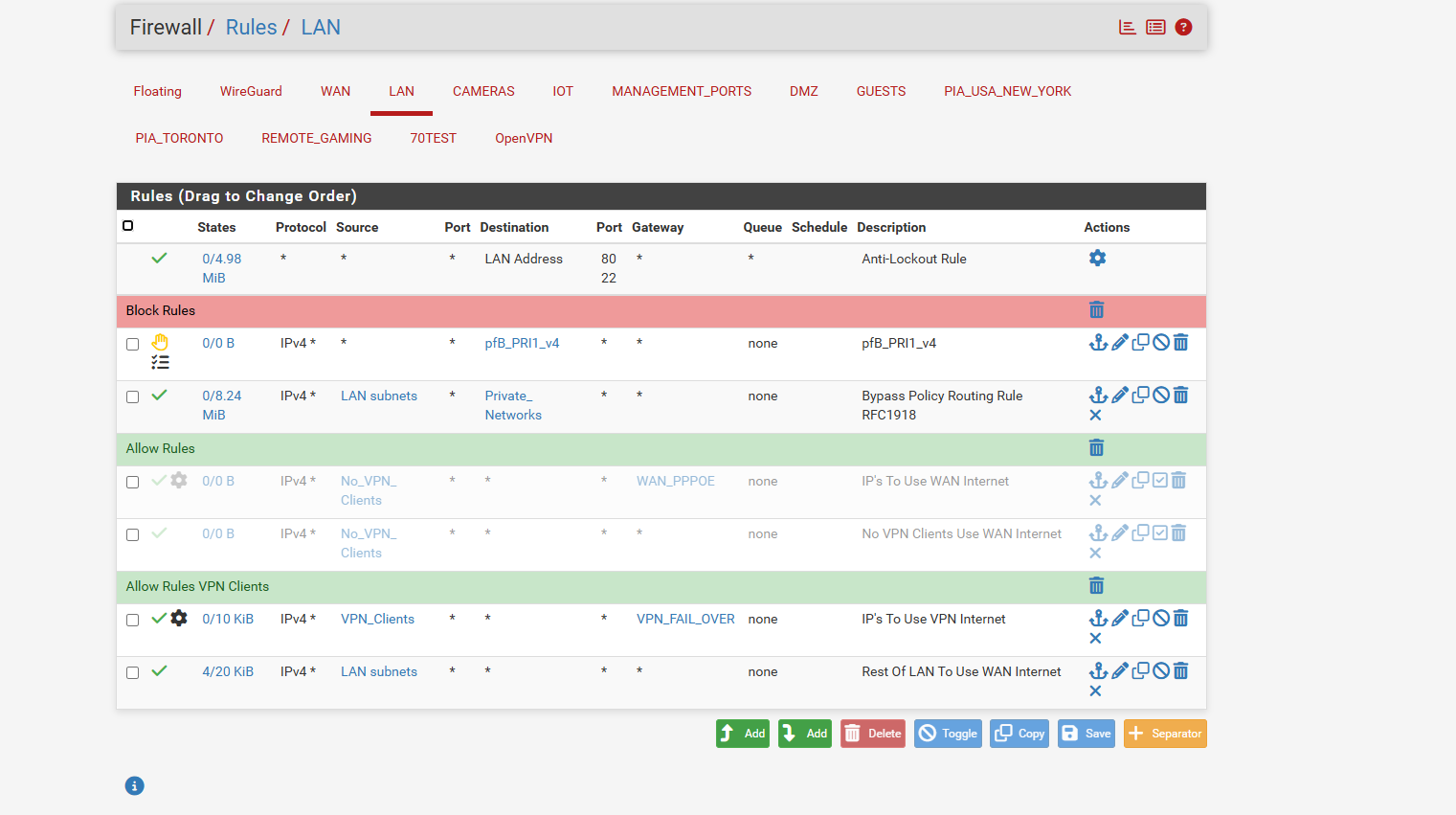
and the nat page ive done wan address and PIA address cuz in the 2 videos they go both directions one says use the wan address and the other says use the pia address
if you could provide pictures what i doing wrong would be good i know you probbably getting frustrated helping me on all this -
What exactly are you counting as a leak test failure?
If you're forwarding requests to Cloudflare then DNS tests will always show Cloudflare. It just might be local servers if the query isn't over the VPN.
-
@stephenw10 well when i run website dnsleak.com or dnsleaktest.com and it shows more then just the piavpn dns server thats what i consider leaking..
that the wan clients should only get 1.1.1.1 dns and all vpn clients should get the 10.0.0.242 say and that the 1.1.1.1 should never show up on any of the vpn clients when i run dnsleaktest.com
and then dnsleak.com keeps saying your leaking dns
and using the nordvpn 103.x.x.x failed providing dns after a few days.. i could ping from the pfsense but not from the windows..
i did google for not logging dns' and ai generated said 1.1.1.1 1.0.0.1. and 9.9.9.9 are non logging non data keeping dns
so then that should be safe right to use on the wan.. as i been trying so long to keep everything seperate and make the dnsleaktest.com say its not leaking but i havent been able to -
but i guess i wrong to figure what is ok for dns leaking and what isnt for dns leaking i just tried to make sure the tests showed i wasnt leaking
-
Well if you are forwarding queries to Cloudflare over the VPN you will still see Cloudflare as the resolver. It will just be an anycast endpoint local to the VPN server.
-
@stephenw10 and what is anycast? i thought using the cloudflare was bad cuz i tried to make sure 1 dns for wan clients and 1 dns for the vpn but its like its just not possible to have it split right...
and seems cloudflare is vpn safe as i googled and found this site
https://bitlaunch.io/blog/the-best-dns-servers-for-privacy/i was just trying to make it secure as possible and pia doesnt even reply ever might be ok service just really bad customer service
-
Anycast is a routing method for sending traffic to the nearest servers using the same IP. So here when you connect to 1.1.1.1 it goes to the closest servers. And when you connect to it over a VPN it goes to the closest servers to the other end of the VPN. That's important because if you check the resolve location it appears to be close the VPN location which is your source IP. Differences there can be used to detect connections using a VPN.