Should failover for WAN1 and should not failover for WAN2
-
Good day. Please help me see where I'm doing things wrong so that these two requirements will be met:
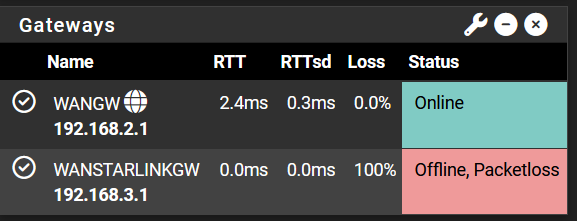
- WAN users should failover to WANSTARLINK <-this seems to work
- WANSTARLINK users should not failover to WAN, so that if WANSTARLINK link goes down then WANSTARLINK users should have no internet access <-I can't make this to work because when WANSTARLINK goes down its users continue to get internet access
I have previously submitted these related posts:
https://forum.netgate.com/topic/185136/bandwidth-segregation-needed-and-not-load-balance-or-fail-over
https://forum.netgate.com/topic/190342/newbie-bogon-not-updatingFrom my previous posts above I got that the "Default gateway" should not be set to "None" but I'm not sure which of the other values (Automatic, WANGW, gateway group "failover") to choose so I chose "failover". Please let me know if this is my mistake and let me know which is the correct value to choose:
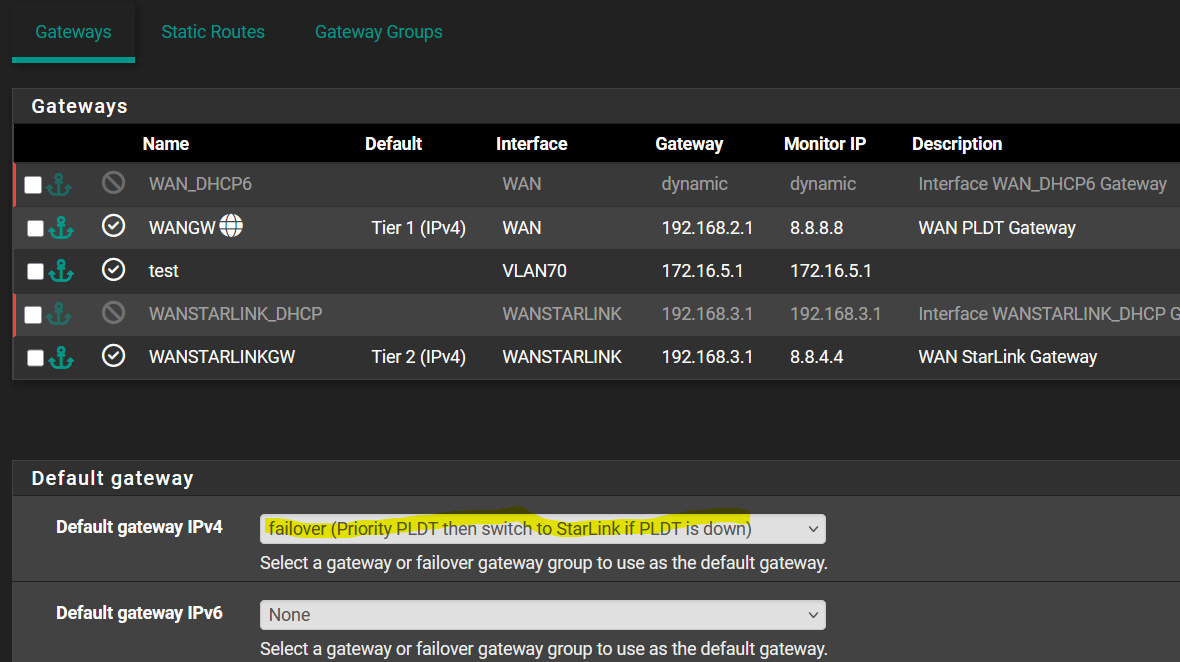
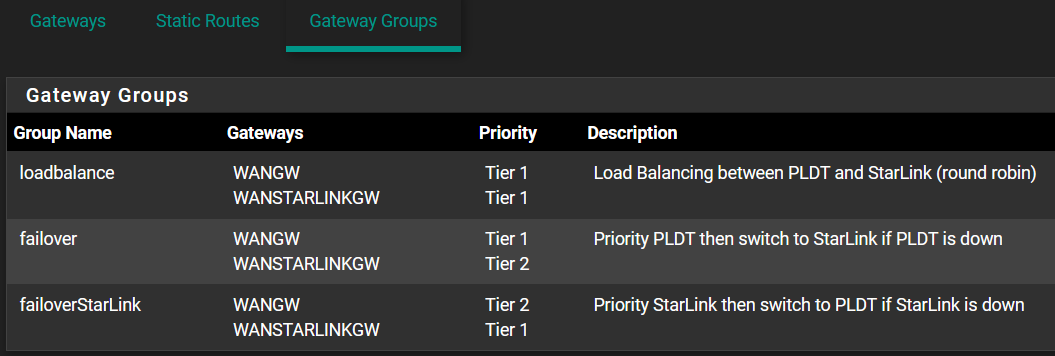
This is the VLAN rule for the WANSTARLINK users that I think should prevent it from failover to WAN because the Gateway was set to WANSTARLINK and not "failover", but WANSTARLINK users still get internet access when WANSTARLINK link is down:
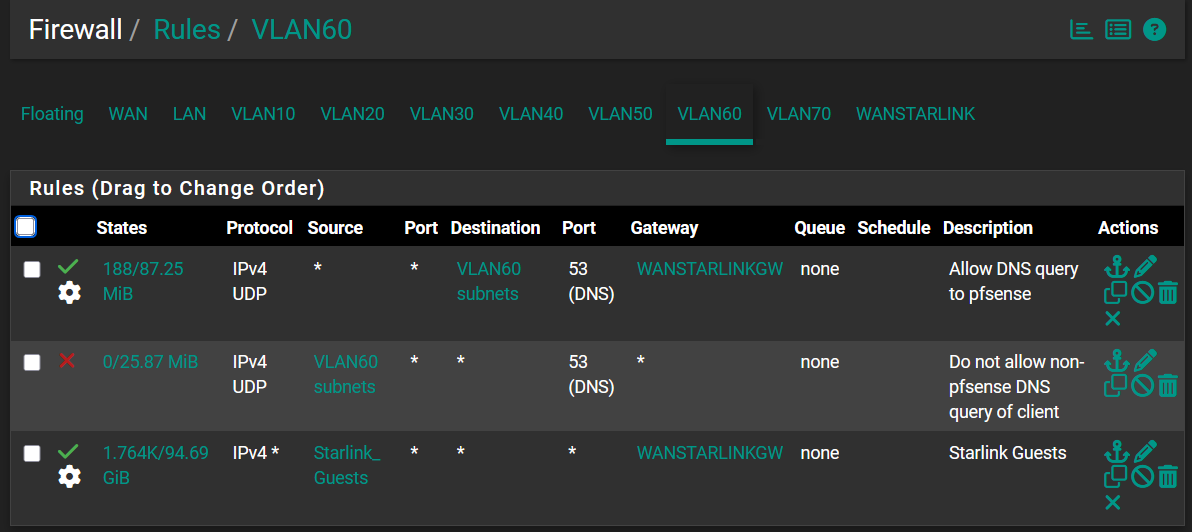
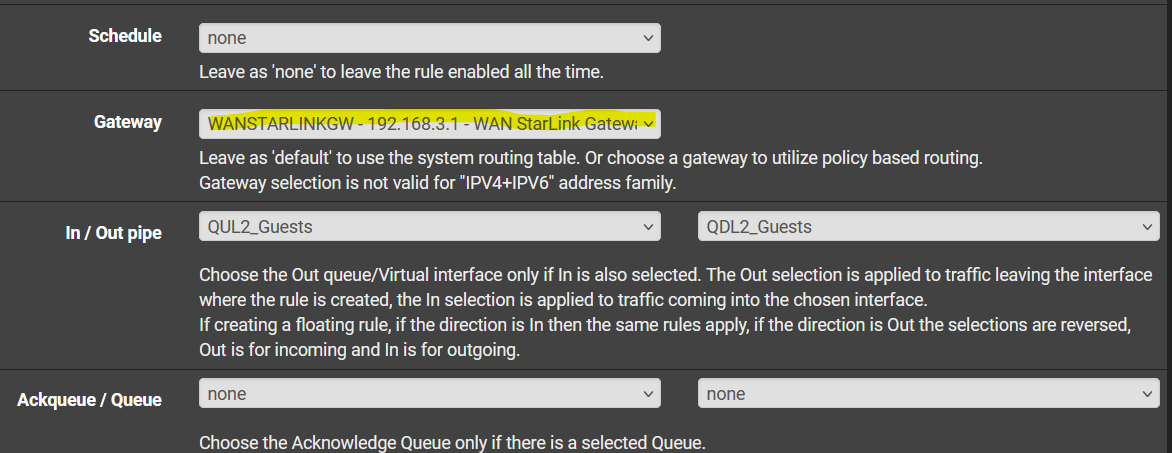
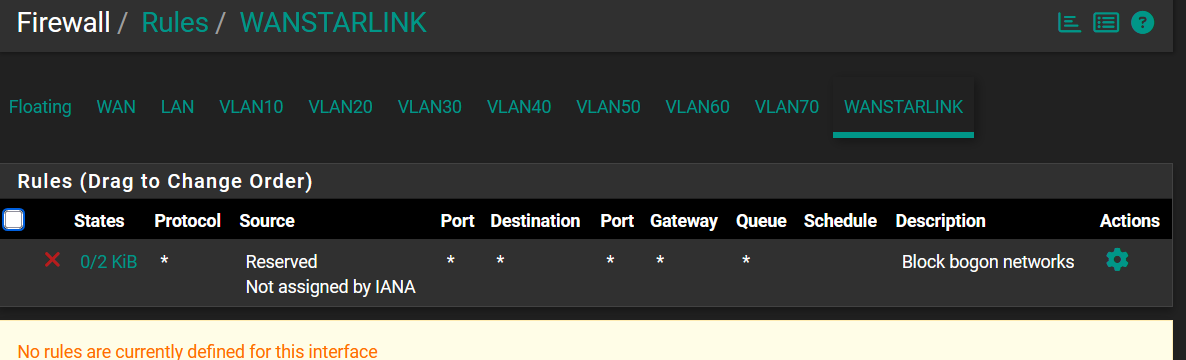
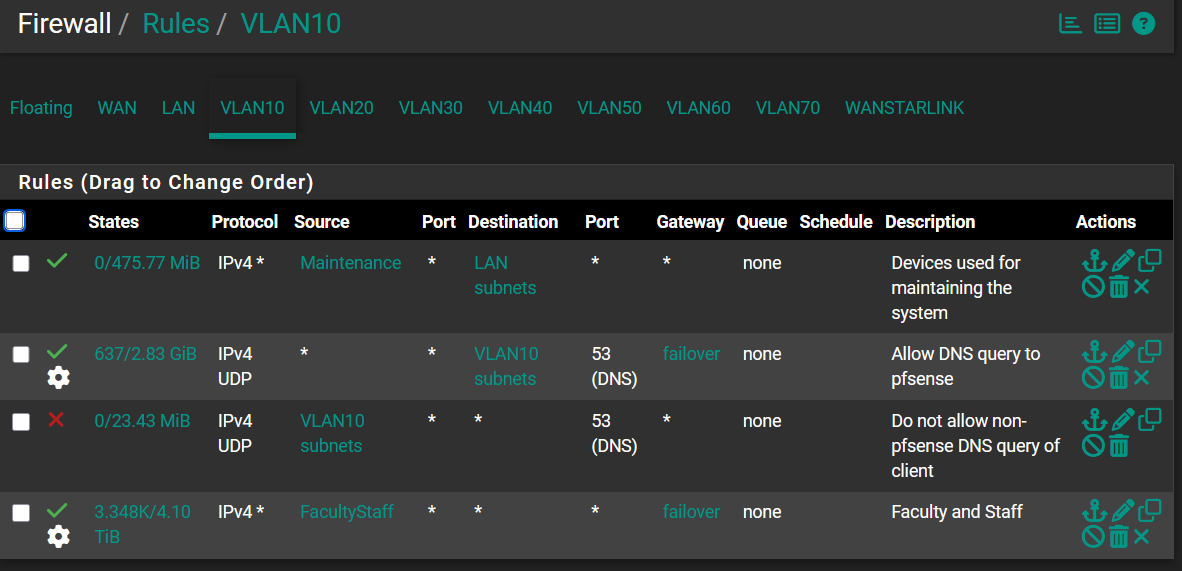
This is the VLAN rule for the WAN users that will failover to WANSTARLINK as per requirement:
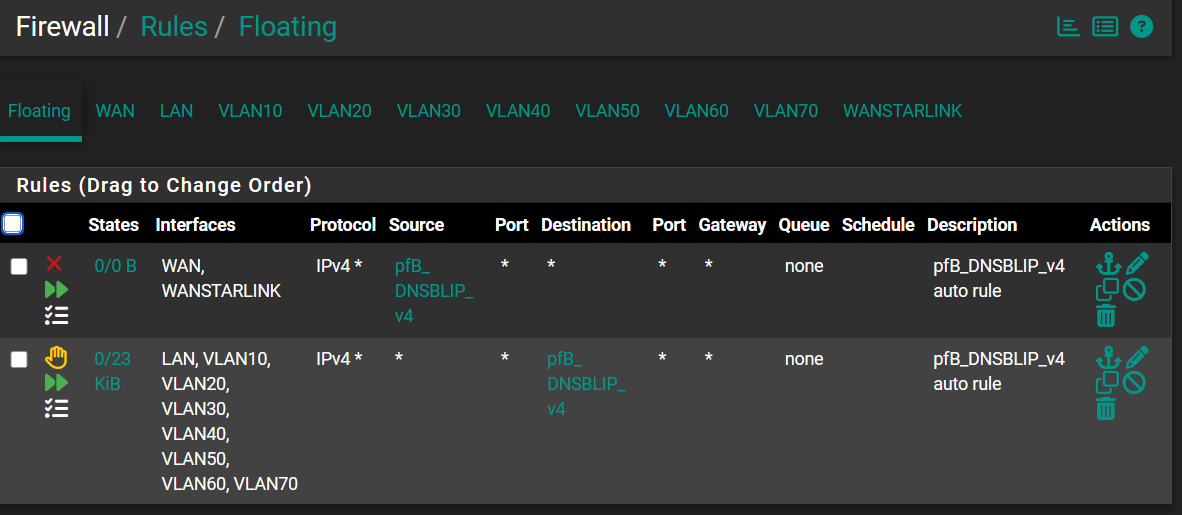
The Floating Rules contain only the entries for pfBlockerNG:
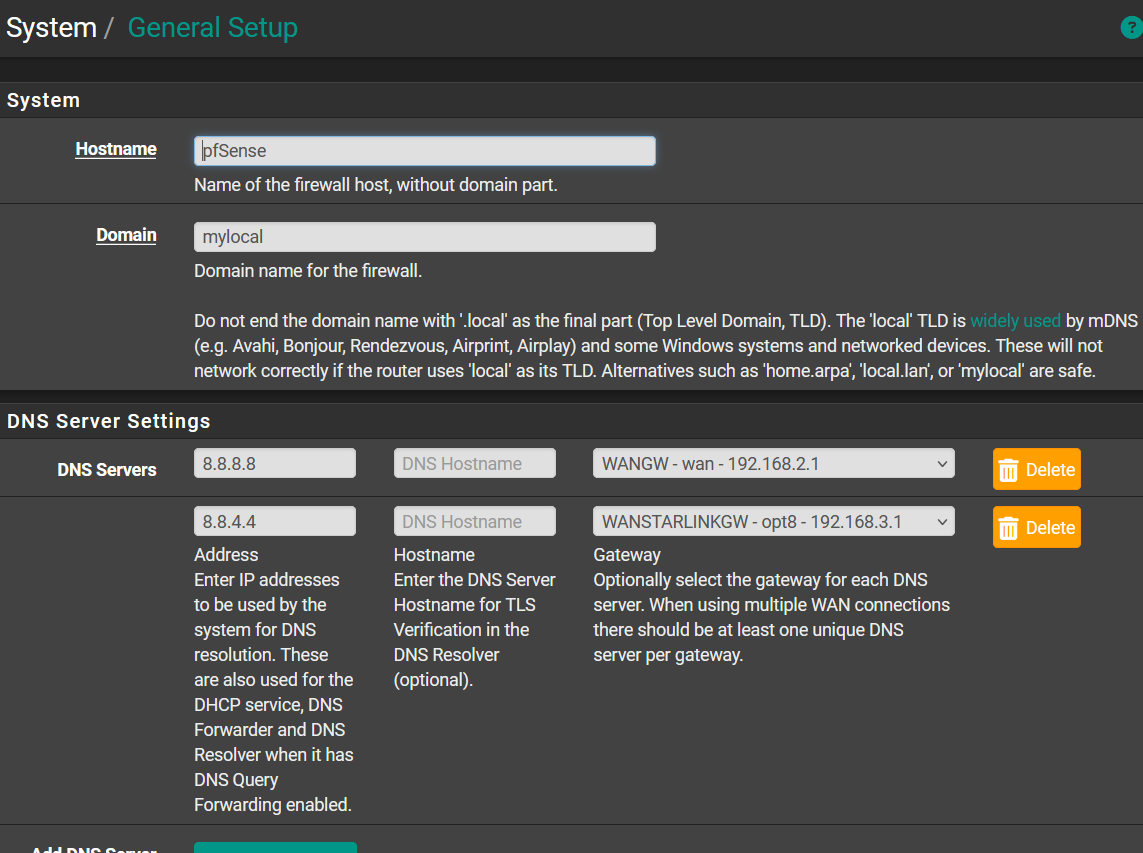
This is the DNS Server settings:
-
@richardsago
You need to check System > Advanced > Miscellaneous > Skip rules when gateway is down to avoid that pfSense routes the connection out to the remaining active gateway. -
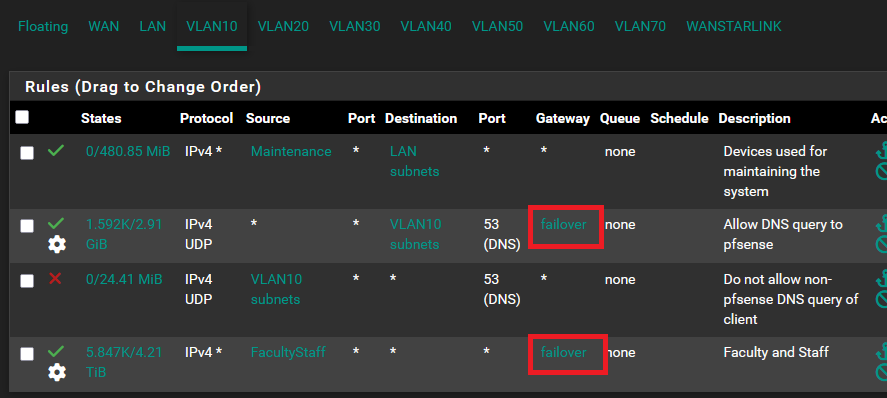
Thank you @viragomann for the reply. The WANSTARLINK users no longer received internet after applying your suggestion. Is our setting correct that our WAN users will still failover to WANSTARLINK if WAN signal goes down? This is the VLAN rule for the WAN users that should failover to WANSTARLINK:
-
@richardsago said in Should failover for WAN1 and should not failover for WAN2:
Is our setting correct that our WAN users will still failover to WANSTARLINK if WAN signal goes down?
Depends...
Your second rule for DNS forces DNS requests to the active gateway. Hence the devices in the subnet will only be able to resolve names if they use a public DNS server. If they try to resolve using a local one (pfSene Unbound) they will fail.
And it's not clear to me, what the FacultyStaff alias in the 4th rule is.
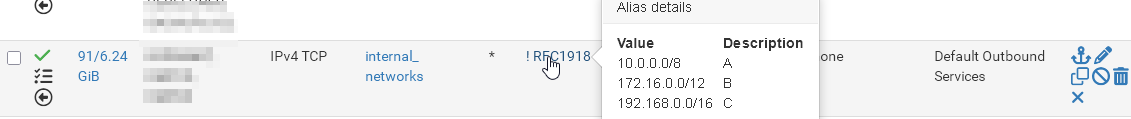
Anyway, best practice for policy routing rules to a WAN gateway is use an RFC 1918 alias with "invert match" as destination. This alias includes all private networks. The invert cares that the rule is applied only any other IP. So the rule forces only traffic, which is not destined to a private IP to the gateway.
You need additional rules to permit local traffic (e.g. DNS) of course.See one of my rules:
-
Thank you @viragomann for the reply. I will look into your suggestion. For my setup I copy-pasted the 2nd to 4th line from a youtuber who said the 2nd and 3rd lines will allow users to connect to the internet only if they set pfsense as their DNS Server. And if they manually set a different DNS Server in their browser then they cannot connect to the internet. I think the FacultyStaff alias is the same as VLAN10 subnets and will test during school break. Thank you again
-
@richardsago said in Should failover for WAN1 and should not failover for WAN2:
For my setup I copy-pasted the 2nd to 4th line from a youtuber
You should not believe any bullshit on YT.
@richardsago said in Should failover for WAN1 and should not failover for WAN2:
For my setup I copy-pasted the 2nd to 4th line from a youtuber who said the 2nd and 3rd lines will allow users to connect to the internet only if they set pfsense as their DNS Server
As mentioned above, the second rule will force any UDP DNS traffic destined to pfSense interface to the WAN gateway.
The 3rd rule blocks any DNS (UDP) from VLAN 10.
Hence the devices will not be able to resolve host names, at least not via UDP.Note that DNS may also use TCP. So you should use "TCP/UDP" as protocol in DNS rules.
Best way to ensure, that all your devices use your local DNS is redirecting the traffic to your server.
Here is my port forwarding rule for this purpose:
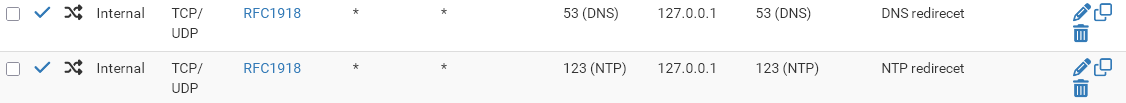
My Unbound is listening on localhost.
With this rule no matter, which server the client requests, it is rediected to Unbond and the client gets the respond from it with the origin requested IP as souce IP and is happy.As you can see, I do the same with NTP.
-
Thank you @viragomann for the reply. I have added TCP to the DNS lines. I'm having trouble with the port forwarding part so please let me know where I'm doing it wrong. Below is a screenshot of port forward that is not applied because I can't set it to "Internal" like in your screenshot, but the other columns are already the same. I set the Interface to "LAN" because it sounded to me closest to "Internal". Please let me know which of the choices below I need to choose. Thank you
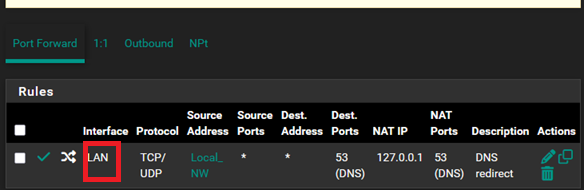
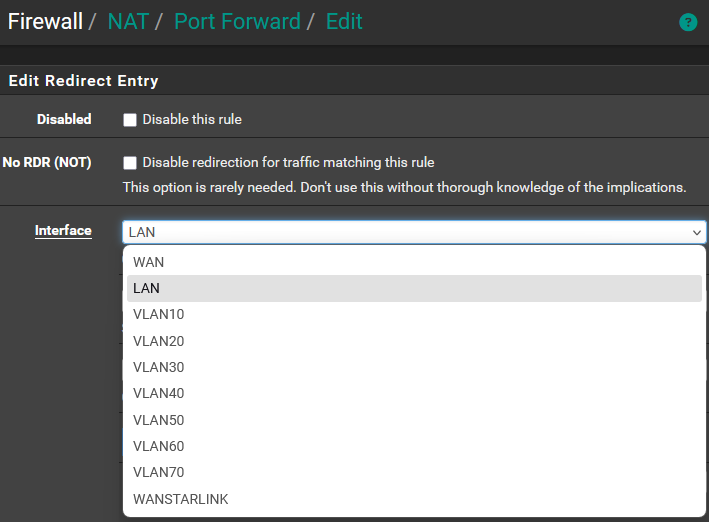
-
@richardsago
"Internal" in my rule is just a custom interface group I've created with all my internal interfaces.
So I've defined my rule on the interface group called "Internal". -
Thank you @viragomann for the reply. I'll test this fully on school break. My quick test on setting this to our VLANs (replace "Internal" with VLANs) resulted in no internet. But I'll check also with the other posts on port forwarding. Thank you again for your help with this and the "Skip rules when gateway is down"
-
R richardsago referenced this topic