[Resolvido] Configuração VPN IPsec Pfsense > CISCO ASA
-
wesleylc1,
Tomei a liberdade de mascarar os ips reais do seu log mas ainda tem imagem mostrando o ip real.
O log que postou, mostra troca de mensagem entre os dois peers, isso deveria estar aparecendo no log da outra ponta da vpn também.
Como tem negociação de fase2 (esp ), tem certeza que a fase1 não está fechanado?
-
Olá, boa noite Marcello.
Obrigado pela iniciativa de fazer o mascaramento nos ips que estavam nos meus logs.Com relação a sua resposta a onde voce informa que nos meus log's existe a troca entre dois peers, mas porem esqueci de mencionar que eu já tenho um outro tunel que esta fechado entre a minha matriz e filial, essa troca entre peers deve ser entre essas duas pontas, agora para facilitar o entendimento, eu desabilitei o meu tunel entre matriz e filial e deixei habilitado apenas o tunel que estou tentando fechar com meu fornecedor.
E com relação ao seu questionamento se esta com negociação com fase2 (esp) esta comunicação se refere ao tunel que já esta OK, matriz e filial.
May 17 20:57:55 charon 09[NET] <75> sending packet: from 187.75.209.xxx[500] to 200.196.59.yyy[500] (56 bytes) May 17 20:57:55 charon 09[IKE] <75> IKE_SA (unnamed)[75] state change: CONNECTING => DESTROYING May 17 20:57:57 charon 10[CFG] vici client 50 connected May 17 20:57:57 charon 09[CFG] vici client 50 registered for: list-sa May 17 20:57:57 charon 09[CFG] vici client 50 requests: list-sas May 17 20:57:57 charon 10[CFG] vici client 50 disconnected May 17 20:57:57 charon 12[CFG] vici client 51 connected May 17 20:57:57 charon 12[CFG] vici client 51 registered for: list-sa May 17 20:57:57 charon 10[CFG] vici client 51 requests: list-sas May 17 20:57:57 charon 13[CFG] vici client 51 disconnected May 17 20:57:58 charon 10[CFG] vici client 52 connected May 17 20:57:58 charon 12[CFG] vici client 52 registered for: list-sa May 17 20:57:58 charon 12[CFG] vici client 52 requests: list-sas May 17 20:57:58 charon 13[CFG] vici client 52 disconnected May 17 20:58:00 charon 13[NET] <76> received packet: from 200.196.59.yyy500] to 187.75.209.xxx[500] (176 bytes) May 17 20:58:00 charon 13[ENC] <76> parsed ID_PROT request 0 [ SA V V V V V ] May 17 20:58:00 charon 13[CFG] <76> looking for an ike config for 187.75.209.xxx...200.196.59.yyy May 17 20:58:00 charon 13[CFG] <76> candidate: %any...%any, prio 24 May 17 20:58:00 charon 13[CFG] <76> found matching ike config: %any...%any with prio 24 May 17 20:58:00 charon 13[IKE] <76> received XAuth vendor ID May 17 20:58:00 charon 13[IKE] <76> received DPD vendor ID May 17 20:58:00 charon 13[IKE] <76> received FRAGMENTATION vendor ID May 17 20:58:00 charon 13[IKE] <76> received NAT-T (RFC 3947) vendor ID May 17 20:58:00 charon 13[IKE] <76> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID May 17 20:58:00 charon 13[IKE] <76> 200.196.59.yyy is initiating a Main Mode IKE_SA May 17 20:58:00 charon 13[IKE] <76> IKE_SA (unnamed)[76] state change: CREATED => CONNECTING May 17 20:58:00 charon 13[CFG] <76> selecting proposal: May 17 20:58:00 charon 13[CFG] <76> no acceptable ENCRYPTION_ALGORITHM found May 17 20:58:00 charon 13[CFG] <76> selecting proposal: May 17 20:58:00 charon 13[CFG] <76> proposal matches May 17 20:58:00 charon 13[CFG] <76> received proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 May 17 20:58:00 charon 13[CFG] <76> configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/CURVE_25519, IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_MD5_96/HMAC_SHA1_96/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_MD5/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_8192/MODP_2048/MODP_1024, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_MD5/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_8192/MODP_2048/MODP_1024 May 17 20:58:00 charon 13[CFG] <76> selected proposal: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 May 17 20:58:00 charon 13[IKE] <76> sending XAuth vendor ID May 17 20:58:00 charon 13[IKE] <76> sending DPD vendor ID May 17 20:58:00 charon 13[IKE] <76> sending FRAGMENTATION vendor ID May 17 20:58:00 charon 13[IKE] <76> sending NAT-T (RFC 3947) vendor ID May 17 20:58:00 charon 13[ENC] <76> generating ID_PROT response 0 [ SA V V V V ] May 17 20:58:00 charon 13[NET] <76> sending packet: from 187.75.209.xxx[500] to 200.196.59.yyy[500] (156 bytes) May 17 20:58:00 charon 13[NET] <76> received packet: from 200.196.59.yyy[500] to 187.75.209.xxx[500] (244 bytes) May 17 20:58:00 charon 13[ENC] <76> parsed ID_PROT request 0 [ KE No NAT-D NAT-D ] May 17 20:58:00 charon 13[IKE] <76> remote host is behind NAT May 17 20:58:00 charon 13[CFG] <76> candidate "bypasslan", match: 1/1/24 (me/other/ike) May 17 20:58:00 charon 13[IKE] <76> no shared key found for 187.75.209.xxx - 200.196.59.yyy May 17 20:58:00 charon 13[IKE] <76> queueing INFORMATIONAL task May 17 20:58:00 charon 13[IKE] <76> activating new tasks May 17 20:58:00 charon 13[IKE] <76> activating INFORMATIONAL task May 17 20:58:00 charon 13[ENC] <76> generating INFORMATIONAL_V1 request 564840140 [ N(INVAL_KE) ] May 17 20:58:00 charon 13[NET] <76> sending packet: from 187.75.209.xxx[500] to 200.196.59.yyy[500] (56 bytes) May 17 20:58:00 charon 13[IKE] <76> IKE_SA (unnamed)[76] state change: CONNECTING => DESTROYINGMesmo desativando os tuneis entre minha matriz e filiais eu observei que as negociações ainda continua sendo feito, conforme informações no log, nesse log eu não consigo encontrar negociações da ponta Matriz –> Fornecedor.
Eu anexei alguns print's com status da VPNS.



-
foca nesta parte aqui:
May 17 20:58:00 charon 13[IKE] <76> 200.196.59.yyy is initiating a Main Mode IKE_SA
May 17 20:58:00 charon 13[IKE] <76> IKE_SA (unnamed)[76] state change: CREATED => CONNECTING
May 17 20:58:00 charon 13[CFG] <76> selecting proposal:
May 17 20:58:00 charon 13[CFG] <76> no acceptable ENCRYPTION_ALGORITHM found -
foca nesta parte aqui:
May 17 20:58:00 charon 13[IKE] <76> 200.196.59.yyy is initiating a Main Mode IKE_SA
May 17 20:58:00 charon 13[IKE] <76> IKE_SA (unnamed)[76] state change: CREATED => CONNECTING
May 17 20:58:00 charon 13[CFG] <76> selecting proposal:
May 17 20:58:00 charon 13[CFG] <76> no acceptable ENCRYPTION_ALGORITHM foundMarcello, bom dia.
Então essa parte faze referência ao tunel que já esta funcionando, eu fiz uma outra coleta de log a onde tem a tentativa de troca entre as pontas que estão com problemas.
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>queueing ISAKMP_VENDOR task
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>queueing ISAKMP_CERT_PRE task
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>queueing MAIN_MODE task
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>queueing ISAKMP_CERT_POST task
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>queueing ISAKMP_NATD task
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>queueing QUICK_MODE task
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>activating new tasks
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>activating ISAKMP_VENDOR task
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>activating ISAKMP_CERT_PRE task
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>activating MAIN_MODE task
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>activating ISAKMP_CERT_POST task
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>activating ISAKMP_NATD task
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>sending XAuth vendor ID
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>sending DPD vendor ID
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>sending FRAGMENTATION vendor ID
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>sending NAT-T (RFC 3947) vendor ID
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>sending draft-ietf-ipsec-nat-t-ike-02\n vendor ID
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>initiating Main Mode IKE_SA con2000[7] to 201.77.217.70
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>IKE_SA con2000[7] state change: CREATED => CONNECTING
May 18 09:23:53 PRJGWSP charon: 11[CFG] <con2000|7>configured proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
May 18 09:23:53 PRJGWSP charon: 11[ENC] <con2000|7>generating ID_PROT request 0 [ SA V V V V V ]
May 18 09:23:53 PRJGWSP charon: 11[NET] <con2000|7>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (176 bytes)
May 18 09:23:53 PRJGWSP charon: 07[NET] <con2000|7>received packet: from 201.77.217.YY[500] to 187.75.209.XXX[500] (116 bytes)
May 18 09:23:53 PRJGWSP charon: 07[ENC] <con2000|7>parsed ID_PROT response 0 [ SA V V ]
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>received NAT-T (RFC 3947) vendor ID
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>received FRAGMENTATION vendor ID
May 18 09:23:53 PRJGWSP charon: 07[CFG] <con2000|7>selecting proposal:
May 18 09:23:53 PRJGWSP charon: 07[CFG] <con2000|7>proposal matches55.248
May 18 09:23:53 PRJGWSP charon: 07[CFG] <con2000|7>received proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
May 18 09:23:53 PRJGWSP charon: 07[CFG] <con2000|7>configured proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
May 18 09:23:53 PRJGWSP charon: 07[CFG] <con2000|7>selected proposal: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>reinitiating already active tasks
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>ISAKMP_VENDOR task
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>MAIN_MODE task
May 18 09:23:53 PRJGWSP charon: 07[ENC] <con2000|7>generating ID_PROT request 0 [ KE No NAT-D NAT-D ]
May 18 09:23:53 PRJGWSP charon: 07[NET] <con2000|7>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (244 bytes)
May 18 09:23:53 PRJGWSP charon: 07[NET] <con2000|7>received packet: from 201.77.217.YY[500] to 187.75.209.XXX[500] (304 bytes)
May 18 09:23:53 PRJGWSP charon: 07[ENC] <con2000|7>parsed ID_PROT response 0 [ KE No V V V V NAT-D NAT-D ]
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>received Cisco Unity vendor ID
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>received XAuth vendor ID
May 18 09:23:53 PRJGWSP charon: 07[ENC] <con2000|7>received unknown vendor ID: fb:21:43:f4:06:1f:2b:6f:f0:1b:c0:61:cb:f7:43:df
May 18 09:23:53 PRJGWSP charon: 07[ENC] <con2000|7>received unknown vendor ID: 1f:07:f7:0e:aa:65:14:d3:b0:fa:96:54:2a:50:01:00
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>reinitiating already active tasks
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>ISAKMP_VENDOR task
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>MAIN_MODE task
May 18 09:23:53 PRJGWSP charon: 07[ENC] <con2000|7>generating ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ]
May 18 09:23:53 PRJGWSP charon: 07[NET] <con2000|7>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (100 bytes)
May 18 09:23:53 PRJGWSP charon: 07[NET] <con2000|7>received packet: from 201.77.217.YY[500] to 187.75.209.XXX[500] (84 bytes)
May 18 09:23:53 PRJGWSP charon: 07[ENC] <con2000|7>parsed ID_PROT response 0 [ ID HASH V ]
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>received DPD vendor ID
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>IKE_SA con2000[7] established between 187.75.209.246[187.75.209.246]…201.77.217.70[201.77.217.70]
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>IKE_SA con2000[7] state change: CONNECTING => ESTABLISHED
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>activating new tasks
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>activating QUICK_MODE task
May 18 09:23:53 PRJGWSP charon: 07[CFG] <con2000|7>configured proposals: ESP:3DES_CBC/HMAC_SHA1_96/MODP_768/NO_EXT_SEQ
May 18 09:23:53 PRJGWSP charon: 07[CFG] <con2000|7>configured proposals: ESP:3DES_CBC/HMAC_SHA1_96/MODP_768/NO_EXT_SEQ
May 18 09:23:53 PRJGWSP charon: 07[CFG] <con2000|7>configured proposals: ESP:3DES_CBC/HMAC_SHA1_96/MODP_768/NO_EXT_SEQ
May 18 09:23:53 PRJGWSP charon: 07[CFG] <con2000|7>proposing traffic selectors for us:
May 18 09:23:53 PRJGWSP charon: 07[CFG] <con2000|7>192.168.40.0/22|/0
May 18 09:23:53 PRJGWSP charon: 07[CFG] <con2000|7>proposing traffic selectors for other:
May 18 09:23:53 PRJGWSP charon: 07[CFG] <con2000|7>172.20.3.224/29|/0
May 18 09:23:53 PRJGWSP charon: 07[ENC] <con2000|7>generating QUICK_MODE request 2020508884 [ HASH SA No KE ID ID ]
May 18 09:23:53 PRJGWSP charon: 07[NET] <con2000|7>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (268 bytes)
May 18 09:23:53 PRJGWSP charon: 11[NET] <con2000|7>received packet: from 201.77.217.YY[500] to 187.75.209.XXX[500] (92 bytes)
May 18 09:23:53 PRJGWSP charon: 11[ENC] <con2000|7>parsed INFORMATIONAL_V1 request 2948734236 [ HASH N((24576)) ]
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>received (24576) notify
May 18 09:23:53 PRJGWSP charon: 11[NET] <con2000|7>received packet: from 201.77.217.YY[500] to 187.75.209.XXX[500] (308 bytes)
May 18 09:23:53 PRJGWSP charon: 11[ENC] <con2000|7>parsed INFORMATIONAL_V1 request 2489781574 [ HASH N(INVAL_ID) ]
May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>received INVALID_ID_INFORMATION error notify
May 18 09:23:53 PRJGWSP charon: 11[CHD] <con2000|7>CHILD_SA con2000{47} state change: CREATED => DESTROYING
May 18 09:23:53 PRJGWSP charon: 07[NET] <con2000|7>received packet: from 201.77.217.YY[500] to 187.75.209.XXX[500] (84 bytes)
May 18 09:23:53 PRJGWSP charon: 07[ENC] <con2000|7>parsed INFORMATIONAL_V1 request 2777439799 [ HASH D ]
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>received DELETE for IKE_SA con2000[7]
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>deleting IKE_SA con2000[7] between 187.75.209.XXX[187.75.209.XXX]…201.77.217.YY[201.77.217.YY]
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>IKE_SA con2000[7] state change: ESTABLISHED => DELETING
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>IKE_SA con2000[7] state change: DELETING => DELETING
May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>IKE_SA con2000[7] state change: DELETING => DESTROYING
May 18 09:23:53 PRJGWSP charon: 07[CFG] vici client 213 connected
May 18 09:23:53 PRJGWSP charon: 11[CFG] vici client 213 registered for: list-sa
May 18 09:23:53 PRJGWSP charon: 11[CFG] vici client 213 requests: list-sas
May 18 09:23:53 PRJGWSP charon: 11[CFG] vici client 213 disconnected
May 18 09:23:58 PRJGWSP charon: 11[CFG] vici client 214 connected
May 18 09:23:58 PRJGWSP charon: 06[CFG] vici client 214 registered for: list-sa
May 18 09:23:58 PRJGWSP charon: 06[CFG] vici client 214 requests: list-sas
May 18 09:23:58 PRJGWSP charon: 06[CFG] vici client 214 disconnected
May 18 09:24:03 PRJGWSP charon: 15[CFG] vici client 215 connected
May 18 09:24:03 PRJGWSP charon: 06[CFG] vici client 215 registered for: list-sa
May 18 09:24:03 PRJGWSP charon: 16[CFG] vici client 215 requests: list-sas
May 18 09:24:03 PRJGWSP charon: 16[CFG] vici client 215 disconnected
May 18 09:24:08 PRJGWSP charon: 15[CFG] vici client 216 connected
May 18 09:24:08 PRJGWSP charon: 10[CFG] vici client 216 registered for: list-sa
May 18 09:24:08 PRJGWSP charon: 10[CFG] vici client 216 requests: list-sas
May 18 09:24:08 PRJGWSP charon: 15[CFG] vici client 216 disconnected
May 18 09:24:13 PRJGWSP charon: 10[CFG] vici client 217 connected
May 18 09:24:13 PRJGWSP charon: 12[CFG] vici client 217 registered for: list-sa
May 18 09:24:13 PRJGWSP charon: 12[CFG] vici client 217 requests: list-sas
May 18 09:24:13 PRJGWSP charon: 12[CFG] vici client 217 disconnected
May 18 09:24:18 PRJGWSP charon: 10[CFG] vici client 218 connected
May 18 09:24:18 PRJGWSP charon: 15[CFG] vici client 218 registered for: list-sa
May 18 09:24:18 PRJGWSP charon: 10[CFG] vici client 218 requests: list-sas
May 18 09:24:18 PRJGWSP charon: 10[CFG] vici client 218 disconnected
May 18 09:24:23 PRJGWSP charon: 15[CFG] vici client 219 connected
May 18 09:24:23 PRJGWSP charon: 09[CFG] vici client 219 registered for: list-sa
May 18 09:24:23 PRJGWSP charon: 09[CFG] vici client 219 requests: list-sas
May 18 09:24:23 PRJGWSP charon: 10[CFG] vici client 219 disconnected</con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7> -
Olá, boa noite pessoal.
Estou muito precisando de uma solução para esta caso, alguem pode tentar me ajudar.At.te
Wesley -
May 18 09:23:53 PRJGWSP charon: 11[NET] <con2000|7>received packet: from 201.77.217.YY[500] to 187.75.209.XXX[500] (308 bytes) May 18 09:23:53 PRJGWSP charon: 11[ENC] <con2000|7>parsed INFORMATIONAL_V1 request 2489781574 [ HASH N(INVAL_ID) ] May 18 09:23:53 PRJGWSP charon: 11[IKE] <con2000|7>received INVALID_ID_INFORMATION error notify May 18 09:23:53 PRJGWSP charon: 11[CHD] <con2000|7>CHILD_SA con2000{47} state change: CREATED => DESTROYING May 18 09:23:53 PRJGWSP charon: 07[NET] <con2000|7>received packet: from 201.77.217.YY[500] to 187.75.209.XXX[500] (84 bytes) May 18 09:23:53 PRJGWSP charon: 07[ENC] <con2000|7>parsed INFORMATIONAL_V1 request 2777439799 [ HASH D ] May 18 09:23:53 PRJGWSP charon: 07[IKE] <con2000|7>received DELETE for IKE_SA con2000[7]</con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7></con2000|7>Se este trecho faz parte do túnel com problema, veja estes erros de HASH Invalido
-
Marcello, bom dia.
Os erros de HASH mencionado por você na ultima interação se refere as configurações desse print anexado?

-
Após realizar alteração para IKEv2 minha internet caiu e ele começou a gerar um monte logar.
May 21 11:04:23 PRJGWSP charon: 14[IKE] <con2|51>retransmit 4 of request with message ID 0
May 21 11:04:23 PRJGWSP charon: 14[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:05:05 PRJGWSP charon: 16[IKE] <con2|51>retransmit 5 of request with message ID 0
May 21 11:05:05 PRJGWSP charon: 16[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>giving up after 5 retransmits
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>peer not responding, trying again (3/3)
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>IKE_SA con2[51] state change: CONNECTING => CREATED
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating new tasks
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_VENDOR task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_INIT task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_NATD task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_CERT_PRE task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_AUTH task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_CERT_POST task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_CONFIG task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating CHILD_CREATE task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_AUTH_LIFETIME task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>initiating IKE_SA con2[51] to 201.77.217.YY
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>IKE_SA con2[51] state change: CREATED => CONNECTING
May 21 11:06:21 PRJGWSP charon: 16[CFG] <con2|51>configured proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
May 21 11:06:21 PRJGWSP charon: 16[CFG] <con2|51>sending supported signature hash algorithms: sha1 sha256 sha384 sha512 identity
May 21 11:06:21 PRJGWSP charon: 16[ENC] <con2|51>generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
May 21 11:06:21 PRJGWSP charon: 16[NET] <con2|51>sending packet: from 187.75.209.XX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:06:25 PRJGWSP charon: 12[IKE] <con2|51>retransmit 1 of request with message ID 0
May 21 11:06:25 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:06:32 PRJGWSP charon: 12[IKE] <con2|51>retransmit 2 of request with message ID 0
May 21 11:06:32 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:06:45 PRJGWSP charon: 12[IKE] <con2|51>retransmit 3 of request with message ID 0
May 21 11:06:45 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:07:08 PRJGWSP charon: 12[IKE] <con2|51>retransmit 4 of request with message ID 0
May 21 11:07:08 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:07:34 PRJGWSP charon: 12[KNL] creating rekey job for CHILD_SA ESP/0xc5eb5eae/200.196.59.134
May 21 11:07:34 PRJGWSP charon: 12[IKE] <con1000|27>activating new tasks
May 21 11:07:34 PRJGWSP charon: 12[IKE] <con1000|27>nothing to initiate</con1000|27></con1000|27></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51> -
May 21 11:06:21 PRJGWSP charon: 16[NET] <con2|51>sending packet: from 187.75.209.XX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:06:25 PRJGWSP charon: 12[IKE] <con2|51>retransmit 1 of request with message ID 0
May 21 11:06:25 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:06:32 PRJGWSP charon: 12[IKE] <con2|51>retransmit 2 of request with message ID 0
May 21 11:06:32 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:06:45 PRJGWSP charon: 12[IKE] <con2|51>retransmit 3 of request with message ID 0
May 21 11:06:45 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:07:08 PRJGWSP charon: 12[IKE] <con2|51>retransmit 4 of request with message ID 0
May 21 11:07:08 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:07:34 PRJGWSP charon: 12[KNL] creating rekey job for CHILD_SA ESP/0xc5eb5eae/200.196.59.134</con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51>Neste trecho do log, aparentemente a outra ponta está te ignorando. 4 transmissões sem nenhuma resposta.
-
Agora esta com comunicação porem a ponta dele por algum motivo de regra não retorna a minha solicitação?
Agora por qual motivo que esta caindo a minha internet?
-
Marcelo, agora quando eu habilito o túnel ele retorna com os logs abaixo e minha conexão para internet fica indisponível.
May 21 11:33:08 charon 08[KNL] creating acquire job for policy 187.75.209.XXX/32|/0 === 201.77.217.YY/32|/0 with reqid {31}
May 21 11:33:08 charon 12[CFG] ignoring acquire, connection attempt pending
May 21 11:33:08 charon 12[KNL] creating acquire job for policy 187.75.209.XXX/32|/0 === 201.77.217.YY/32|/0 with reqid {31}
May 21 11:33:08 charon 12[CFG] ignoring acquire, connection attempt pending
May 21 11:33:08 charon 12[KNL] creating acquire job for policy 187.75.209.XXX/32|/0 === 201.77.217.YY/32|/0 with reqid {31}
May 21 11:33:08 charon 08[CFG] ignoring acquire, connection attempt pending
May 21 11:33:08 charon 12[KNL] creating acquire job for policy 187.75.209.XXX/32|/0 === 201.77.217.YY/32|/0 with reqid {31}
May 21 11:33:08 charon 16[CFG] ignoring acquire, connection attempt pending
May 21 11:33:08 charon 16[KNL] creating acquire job for policy 187.75.209.XXX/32|/0 === 201.77.217.YY/32|/0 with reqid {31}
May 21 11:33:08 charon 16[CFG] ignoring acquire, connection attempt pending
May 21 11:33:09 charon 16[KNL] creating acquire job for policy 187.75.209.XXX/32|/0 === 201.77.217.YY/32|/0 with reqid {31} -
Marcelo, boa tarde.
você me sugere fazer mais algum procedimento?
-
Eu particularmente nunca vi a internet cair quanto habilita o ipsec.
-
Não está caindo quando habilitou o ipsec, está ficando sem conexão quando eu habilito esse túnel, eu estou com ipsec habilitado.
-
Prezados, boa tarde.
Alguém tem mais alguma dica para tentar me ajudaR?
-
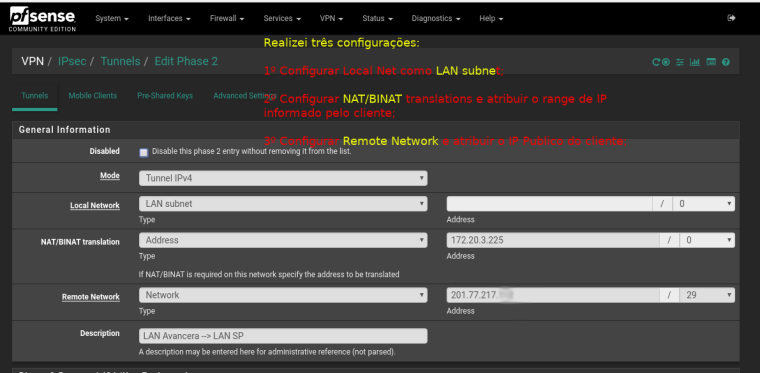
-
Precisou fazer nat no túnel?
-
@marcelloc Sim, só funcionou após a configuração do NAT.
-
@wesleylc1, só necessidade de configuração de nat quanto a sua faixa de rede também existe na outra ponta do túnel.
-
@marcelloc Sim na outra ponta do tunel tbm tem.