[Resolvido] Configuração VPN IPsec Pfsense > CISCO ASA
-
Marcello, bom dia.
Os erros de HASH mencionado por você na ultima interação se refere as configurações desse print anexado?

-
Após realizar alteração para IKEv2 minha internet caiu e ele começou a gerar um monte logar.
May 21 11:04:23 PRJGWSP charon: 14[IKE] <con2|51>retransmit 4 of request with message ID 0
May 21 11:04:23 PRJGWSP charon: 14[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:05:05 PRJGWSP charon: 16[IKE] <con2|51>retransmit 5 of request with message ID 0
May 21 11:05:05 PRJGWSP charon: 16[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>giving up after 5 retransmits
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>peer not responding, trying again (3/3)
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>IKE_SA con2[51] state change: CONNECTING => CREATED
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating new tasks
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_VENDOR task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_INIT task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_NATD task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_CERT_PRE task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_AUTH task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_CERT_POST task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_CONFIG task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating CHILD_CREATE task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>activating IKE_AUTH_LIFETIME task
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>initiating IKE_SA con2[51] to 201.77.217.YY
May 21 11:06:21 PRJGWSP charon: 16[IKE] <con2|51>IKE_SA con2[51] state change: CREATED => CONNECTING
May 21 11:06:21 PRJGWSP charon: 16[CFG] <con2|51>configured proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
May 21 11:06:21 PRJGWSP charon: 16[CFG] <con2|51>sending supported signature hash algorithms: sha1 sha256 sha384 sha512 identity
May 21 11:06:21 PRJGWSP charon: 16[ENC] <con2|51>generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
May 21 11:06:21 PRJGWSP charon: 16[NET] <con2|51>sending packet: from 187.75.209.XX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:06:25 PRJGWSP charon: 12[IKE] <con2|51>retransmit 1 of request with message ID 0
May 21 11:06:25 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:06:32 PRJGWSP charon: 12[IKE] <con2|51>retransmit 2 of request with message ID 0
May 21 11:06:32 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:06:45 PRJGWSP charon: 12[IKE] <con2|51>retransmit 3 of request with message ID 0
May 21 11:06:45 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:07:08 PRJGWSP charon: 12[IKE] <con2|51>retransmit 4 of request with message ID 0
May 21 11:07:08 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:07:34 PRJGWSP charon: 12[KNL] creating rekey job for CHILD_SA ESP/0xc5eb5eae/200.196.59.134
May 21 11:07:34 PRJGWSP charon: 12[IKE] <con1000|27>activating new tasks
May 21 11:07:34 PRJGWSP charon: 12[IKE] <con1000|27>nothing to initiate</con1000|27></con1000|27></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51> -
May 21 11:06:21 PRJGWSP charon: 16[NET] <con2|51>sending packet: from 187.75.209.XX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:06:25 PRJGWSP charon: 12[IKE] <con2|51>retransmit 1 of request with message ID 0
May 21 11:06:25 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:06:32 PRJGWSP charon: 12[IKE] <con2|51>retransmit 2 of request with message ID 0
May 21 11:06:32 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:06:45 PRJGWSP charon: 12[IKE] <con2|51>retransmit 3 of request with message ID 0
May 21 11:06:45 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:07:08 PRJGWSP charon: 12[IKE] <con2|51>retransmit 4 of request with message ID 0
May 21 11:07:08 PRJGWSP charon: 12[NET] <con2|51>sending packet: from 187.75.209.XXX[500] to 201.77.217.YY[500] (334 bytes)
May 21 11:07:34 PRJGWSP charon: 12[KNL] creating rekey job for CHILD_SA ESP/0xc5eb5eae/200.196.59.134</con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51></con2|51>Neste trecho do log, aparentemente a outra ponta está te ignorando. 4 transmissões sem nenhuma resposta.
-
Agora esta com comunicação porem a ponta dele por algum motivo de regra não retorna a minha solicitação?
Agora por qual motivo que esta caindo a minha internet?
-
Marcelo, agora quando eu habilito o túnel ele retorna com os logs abaixo e minha conexão para internet fica indisponível.
May 21 11:33:08 charon 08[KNL] creating acquire job for policy 187.75.209.XXX/32|/0 === 201.77.217.YY/32|/0 with reqid {31}
May 21 11:33:08 charon 12[CFG] ignoring acquire, connection attempt pending
May 21 11:33:08 charon 12[KNL] creating acquire job for policy 187.75.209.XXX/32|/0 === 201.77.217.YY/32|/0 with reqid {31}
May 21 11:33:08 charon 12[CFG] ignoring acquire, connection attempt pending
May 21 11:33:08 charon 12[KNL] creating acquire job for policy 187.75.209.XXX/32|/0 === 201.77.217.YY/32|/0 with reqid {31}
May 21 11:33:08 charon 08[CFG] ignoring acquire, connection attempt pending
May 21 11:33:08 charon 12[KNL] creating acquire job for policy 187.75.209.XXX/32|/0 === 201.77.217.YY/32|/0 with reqid {31}
May 21 11:33:08 charon 16[CFG] ignoring acquire, connection attempt pending
May 21 11:33:08 charon 16[KNL] creating acquire job for policy 187.75.209.XXX/32|/0 === 201.77.217.YY/32|/0 with reqid {31}
May 21 11:33:08 charon 16[CFG] ignoring acquire, connection attempt pending
May 21 11:33:09 charon 16[KNL] creating acquire job for policy 187.75.209.XXX/32|/0 === 201.77.217.YY/32|/0 with reqid {31} -
Marcelo, boa tarde.
você me sugere fazer mais algum procedimento?
-
Eu particularmente nunca vi a internet cair quanto habilita o ipsec.
-
Não está caindo quando habilitou o ipsec, está ficando sem conexão quando eu habilito esse túnel, eu estou com ipsec habilitado.
-
Prezados, boa tarde.
Alguém tem mais alguma dica para tentar me ajudaR?
-
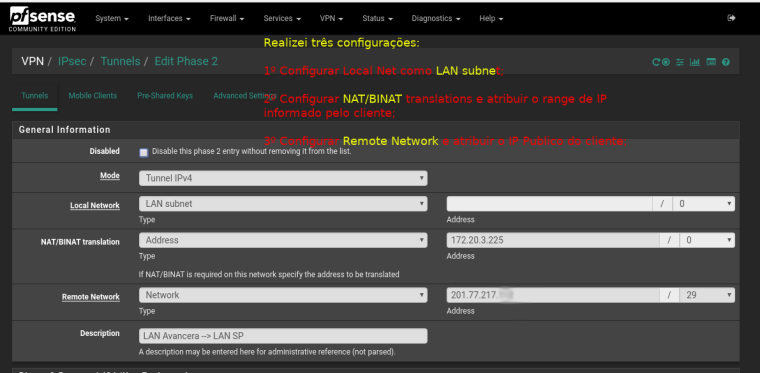
-
Precisou fazer nat no túnel?
-
@marcelloc Sim, só funcionou após a configuração do NAT.
-
@wesleylc1, só necessidade de configuração de nat quanto a sua faixa de rede também existe na outra ponta do túnel.
-
@marcelloc Sim na outra ponta do tunel tbm tem.