Dynamic DNS gets cached IP as VPN client IP
-
Are you accepting a default route from the VPN service?
-
I have a rule on my lan_bridge to send all traffic to the TorGuard gateway ...when Torguard is VPN client is enabled, all traffic routes through the VPN service and when the VPN service has been disabled traffic routes directly to the WAN as expected...
The only other thing I configured for the VPN service was the NAT rules as defined in the guide I posted above
If that's not what you mean, please explain
-
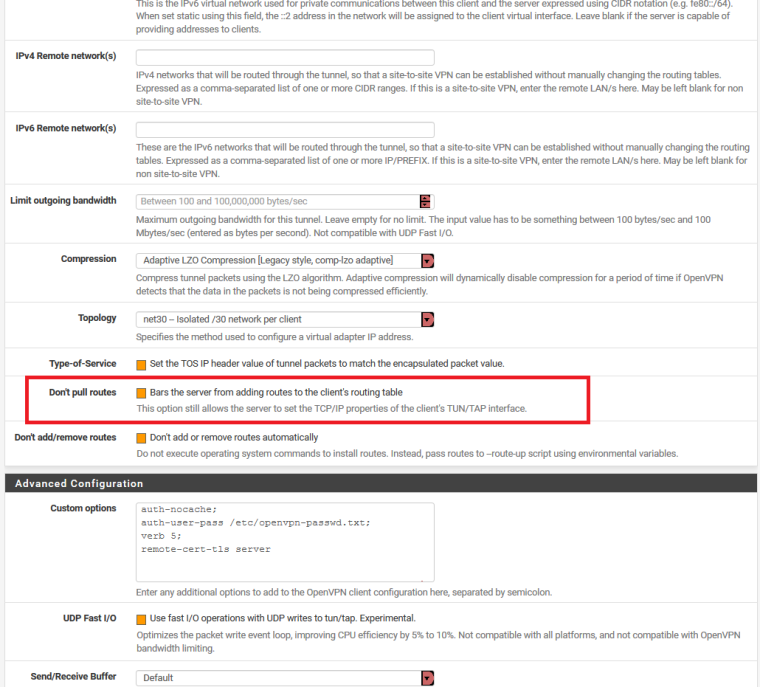
Do you have Don't pull routes checked in your VPN client config?
-
No...I have that option Unchecked
@derelict said in Dynamic DNS gets cached IP as VPN client IP:
Do you have Don't pull routes checked in your VPN client config?
-
Right. That means they are giving you a default route. That likely means your dyndns request is going that way too.
If you are policy routing traffic out the VPN by setting gateways on inside interface rules, try checking that box and seeing if dyndns now does the right thing.
-
Okay, I have CHECKED that option
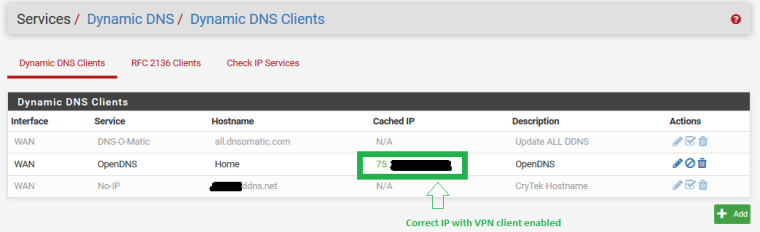
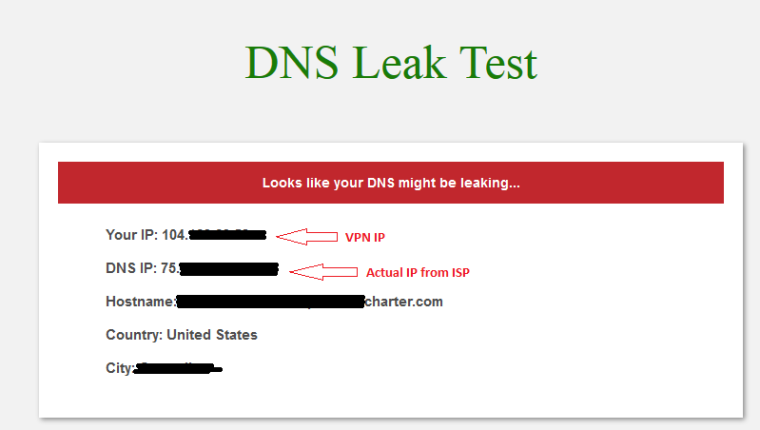
However, after Checking that box, I now have a DNS leak
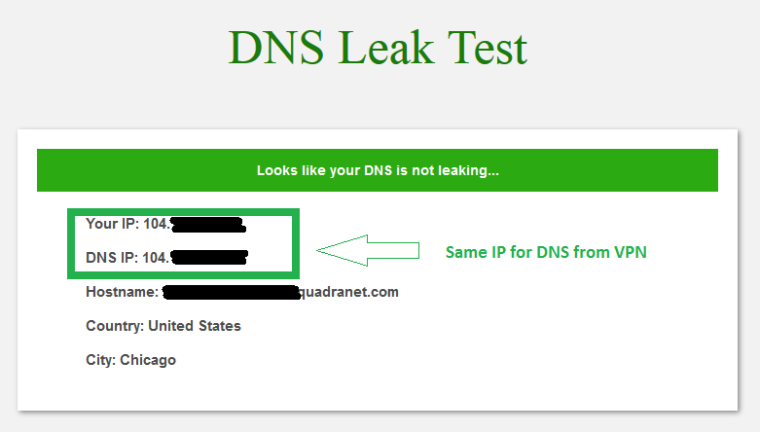
If I leave the box UNCHECKED, this is the DNS test result
-
Here are some related settings
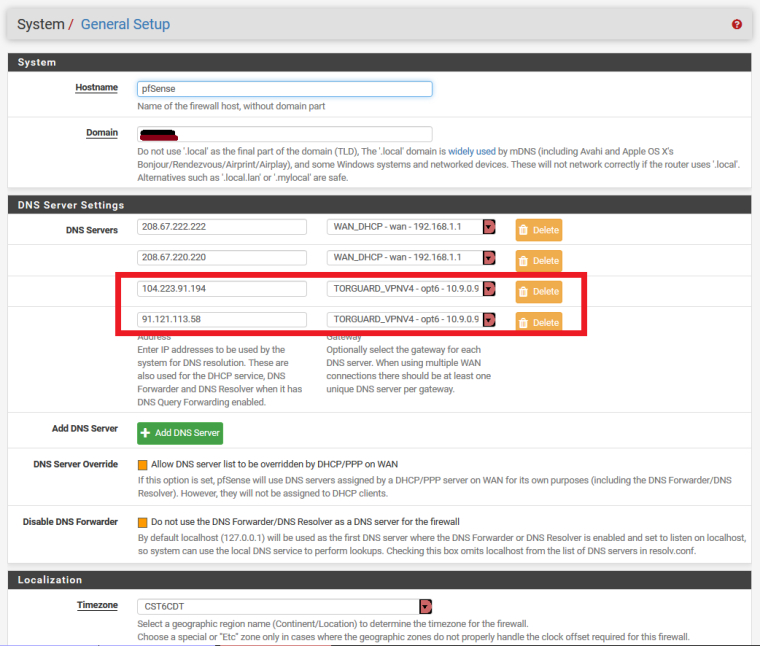
LAN Rules related to TorGuard
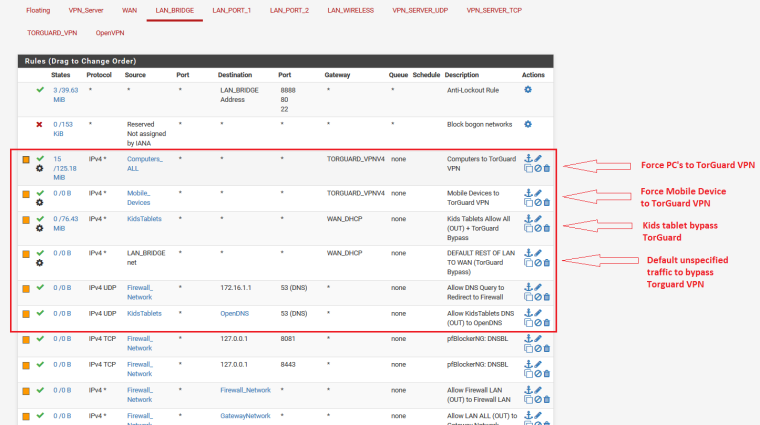
-
forgot to post the (unbound) DNS Resolver settings
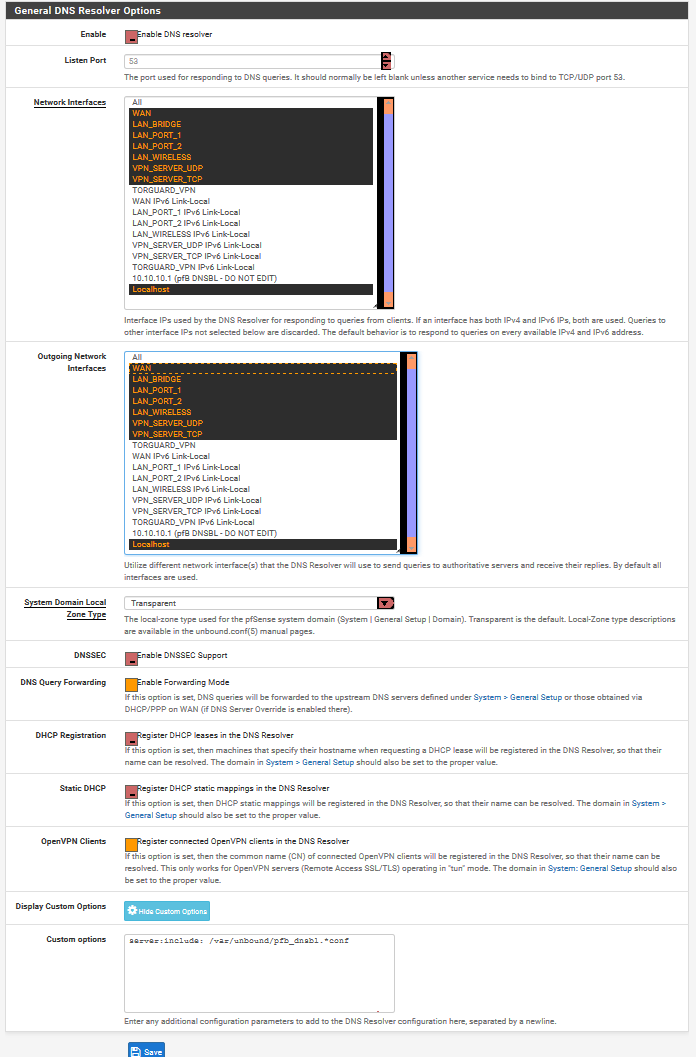
-
Set your VPN clients to use outside DNS servers instead of the DNS resolver on the local firewall.
-
@derelict You'll have to excuse my ignorance LBVS
How do I do that?I thought I was accomplishing that in the General System Settings by providing a DNS server tagged to the TorGuard VPN gateway
-
Nope. Set them in the DHCP server most likely, else static on the hosts.
The DHCP server will automatically give hosts the interface address if DNS servers are not specified.
-
So your saying I should setup the TorGuard Interface as DHCP? as I have it set to none at the moment and it just sets a Virtual IP
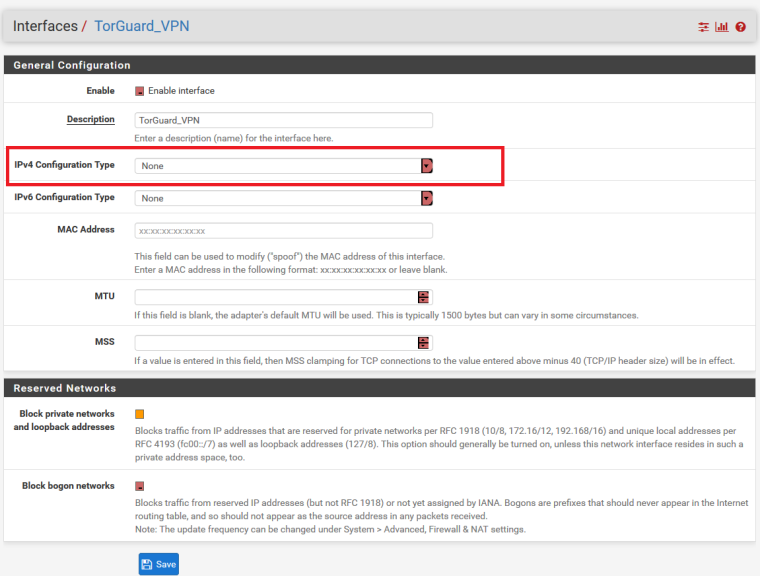
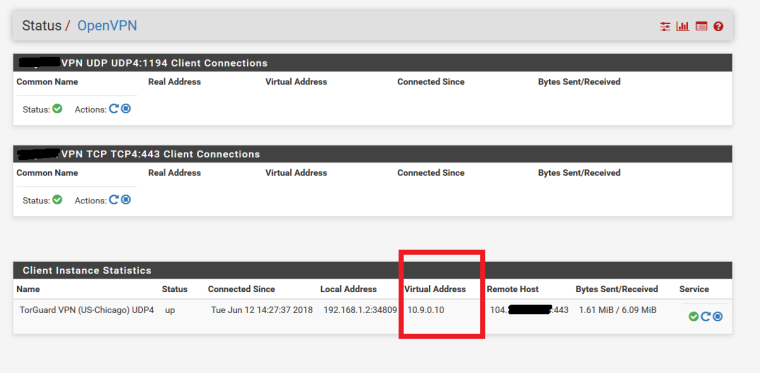
-
No. It's about what the CLIENTS that are routed over TorGuard are, themselves, configured to use as DNS servers. The DHCP configuration would be on that interface. If you only want to change certain hosts, use DHCP static mappings.
-
You're talking about here?
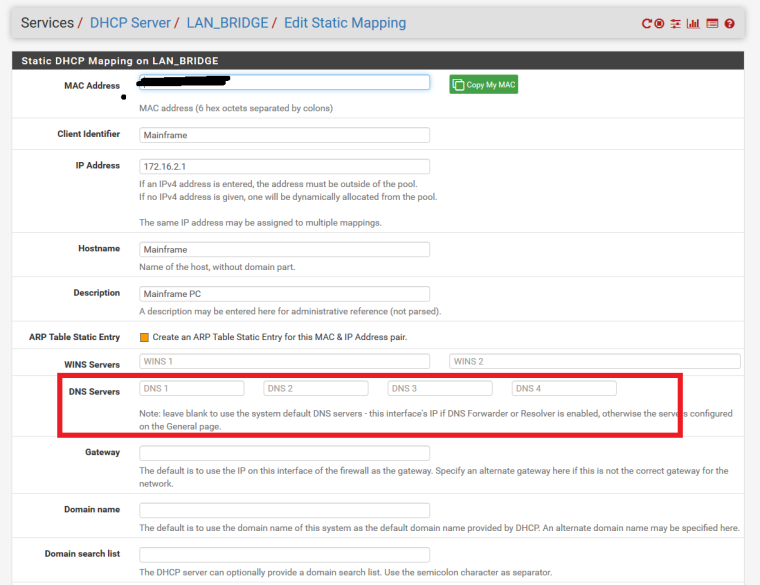
If I do that, then when the TorGuard Service has been disabled/disconnected, won't the PC constantly use those specific DNS servers rather than Only use the TorGuard Servers when the service is enabled and default to using Unbound DNS Resolver when TorGuard is disconnected like it performed before the "Do Not Pull Routes" option was checked?
-
Yup.
You can't have everything.
The most straightforward option I can think of is to run a DNS server off the firewall. That way DNS queries get policy routed like all other traffic.
Some people set the OpenVPN interface as the outgoing interface in DNS Resolver but, when you do that, all DNS can go south when the VPN is not connected.
If you're concerned about DNS leaks, policy route, and choose to use a DNS resolver on the firewall, there are compromises. If you otherwise choose to accept a default route from a VPN provider, there are compromises.
Maybe someone else has a better idea.
-
@teknikalcrysis said in Dynamic DNS gets cached IP as VPN client IP:
Here are some related settings

LAN Rules related to TorGuard

Have you tried a pass rule for source This Firewall(self) destination ?.ddns.net gateway WAN_DHCP
-
It won't matter because the dyndns session doesn't arrive into LAN where it can be policy routed. It is sourced from the firewall itself.
A dyndns client on the inside that updates that name and could be policy routed could perhaps solve the problem being seen when the VPN connection is active with def1 routes accepted.
-
@derelict said in Dynamic DNS gets cached IP as VPN client IP:
It won't matter because the dyndns session doesn't arrive into LAN where it can be policy routed. It is sourced from the firewall itself.
A dyndns client on the inside that updates that name and could be policy routed could perhaps solve the problem being seen when the VPN connection is active with def1 routes accepted.
Oops. How about outbound NAT on WAN interface source This Firewall(self) destination ?.ddns.net gateway WAN_DHCP?
It may be simpler just to run ddns client on the outside edge router if it has one.
-
Outbound NAT does not have anything to do with where traffic goes (routing). It only determines what NAT happens when traffic flows that way according to policy routing and the routing table.
-
@derelict said in Dynamic DNS gets cached IP as VPN client IP:
Outbound NAT does not have anything to do with where traffic goes (routing). It only determines what NAT happens when traffic flows that way according to policy routing and the routing table.
Oops again should be. How about outbound NAT on WAN interface source This Firewall(self) destination ?.ddns.net NAT address WAN address?