Dynamic DNS gets cached IP as VPN client IP
-
This post is deleted! -
@gjaltemba said in Dynamic DNS gets cached IP as VPN client IP:
Leave your original setup asis. Just put this at the top.
outbound NAT on WAN interface source This Firewall(self) destination ?.ddns.net NAT address WAN address
It wont let me type anything but an IP in the destination box
-
@gjaltemba Outbound NAT has ZERO to do with how traffic flows. If it is routed out the OpenVPN or policy routed out another interface, Outbound NAT will not change anything. It only determines what NAT occurs when traffic flows out an interface as the routing mechanism has already decided it should.
-
@derelict said in Dynamic DNS gets cached IP as VPN client IP:
@gjaltemba Outbound NAT has ZERO to do with how traffic flows. If it is routed out the OpenVPN or policy routed out another interface, Outbound NAT will not change anything. It only determines what NAT occurs when traffic flows our an interface as the routing mechanism has already decided it should.
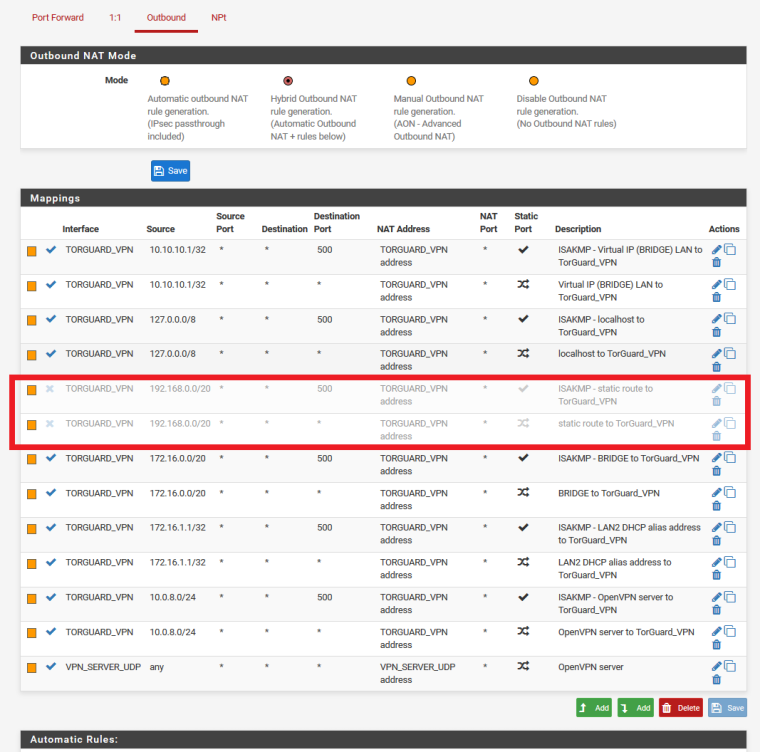
I still think there is a way...I feel I am close... I went back and UNCHECKED the "Do Not Pull Routes" option in the TorGuard OpenVPN Client settings and I just disabled the following NAT OUTBOUND Mappings
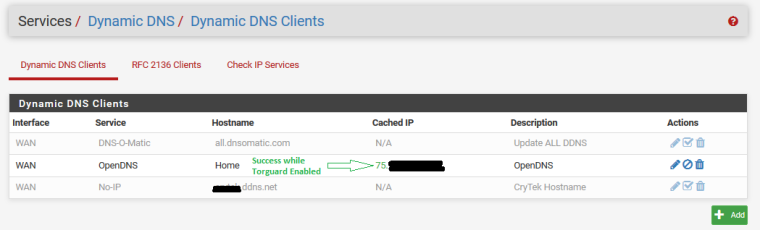
DynDNS Result is a SUCCESSFUL IP from ISP:
However there is still a bit of a DNS leak:
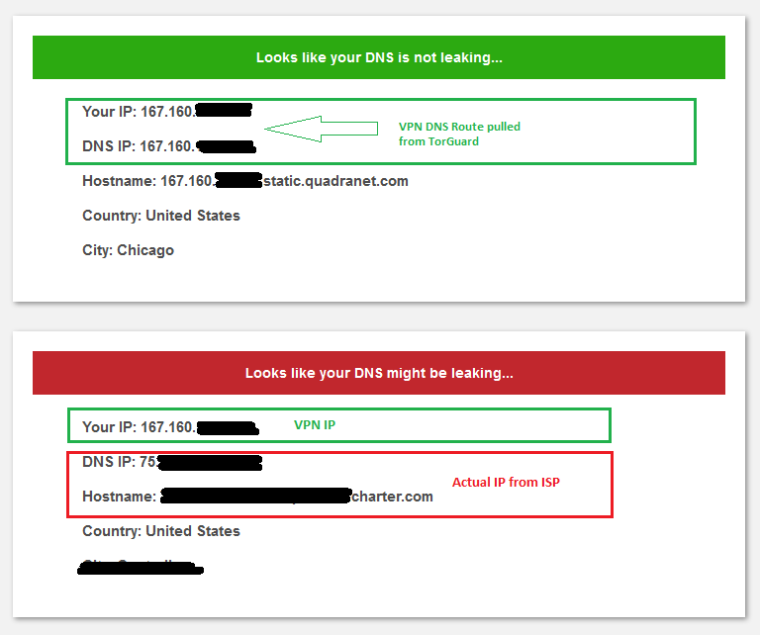
Before disabling those Outbound NAT mappings were disabled DynDNS would report the IP of the TorGuard VPN and would only have the top DNS result in green, it never listed two servers like this before when the Do Not Pull Routes option was unchecked...with the exception of the config I just tried above with (dnsmasq)
-
@teknikalcrysis said in Dynamic DNS gets cached IP as VPN client IP:
@gjaltemba said in Dynamic DNS gets cached IP as VPN client IP:
Leave your original setup asis. Just put this at the top.
outbound NAT on WAN interface source This Firewall(self) destination ?.ddns.net NAT address WAN address
It wont let me type anything but an IP in the destination box
I am able to type an alias for ***.ddns.net in the destination of outbound nat. The outbound NAT should register your ISP ip on ddns with openvpn client running.
To test, do a packet capture on WAN interface for traffic heading to ***.ddns.net. You see the pfSense WAN ip.
-
@gjaltemba said in Dynamic DNS gets cached IP as VPN client IP:
@teknikalcrysis said in Dynamic DNS gets cached IP as VPN client IP:
@gjaltemba said in Dynamic DNS gets cached IP as VPN client IP:
Leave your original setup asis. Just put this at the top.
outbound NAT on WAN interface source This Firewall(self) destination ?.ddns.net NAT address WAN address
It wont let me type anything but an IP in the destination box
I am able to type an alias for ***.ddns.net in the destination of outbound nat. The outbound NAT should register your ISP ip on ddns with openvpn client running.
But then at some point that alias would be obsolete, as my IP is not static and while not frequent (unless I force an ISP IP change by spoofing the MAC on the first router that is connected to the modem directly and then rebooting the modem) is does change from time to time if my power is out to long or in a few other scenarios.. when that happens, the alias would then be configured with an incorrect destination
-
@teknikalcrysis The alias can be dns name. To test include dnsleaktest.com in the alias browse to dnsleaktest.com and you will see your ISP ip. Remove dnsleaktest.com from the alias and you will see your vpn ip.
-
@gjaltemba I say again. Outbound NAT has nothing to do with which way traffic routes.
-
@derelict I get it but what is your point. Quick test from here tells me outbound NAT gives the desired result. To test, the source has to include the browser client ip because the firewall does not have a browser.
If for whatever reason outbound NAT does not work then there is always plan B. Setup a ddns client on the edge router outside pfSense.
-
This post is deleted! -
This post is deleted! -
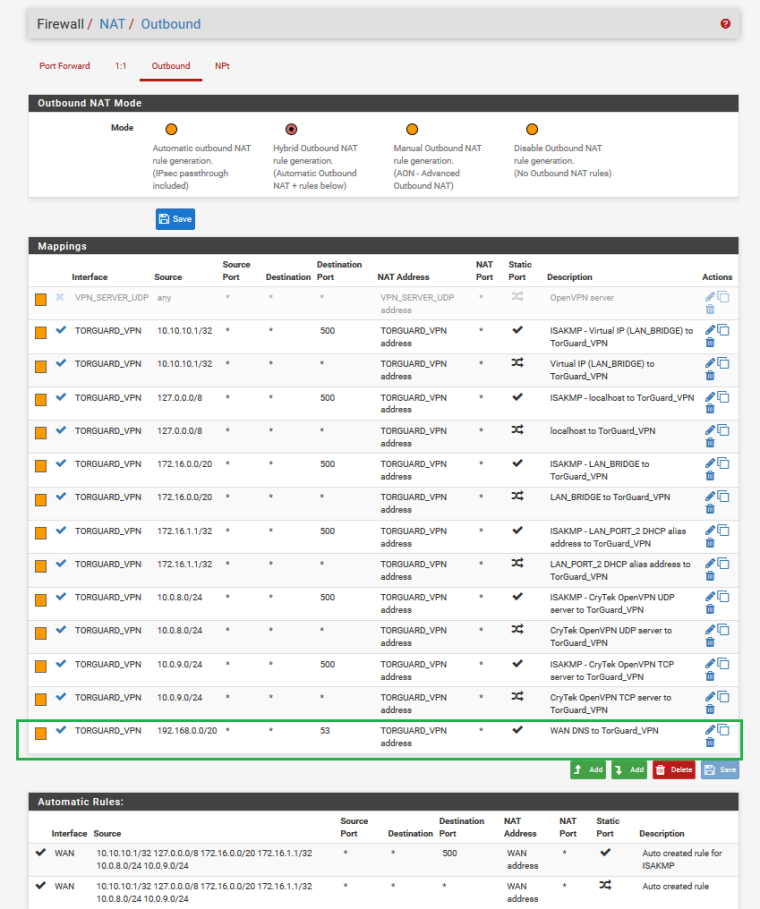
I think I fixed it....after playing around with some settings and getting close and talking about Outbound NAT and me disabling those Outbound NAT rules I highlighted earlier and managed to get DynDNS to update properly but still had it pulling two dns servers (the VPN and Unbound Resolver) causing a leak when those Outbound NAT mapping were disabled...it gave me an idea to Map Outbound NAT on TorGuard Interface from Source:WAN NET to Destination:ANY and NAT:TorGuard Address on Static Port:53 to push DNS queries back to TorGuard and stop the leak
NEW Outbound NAT Config:
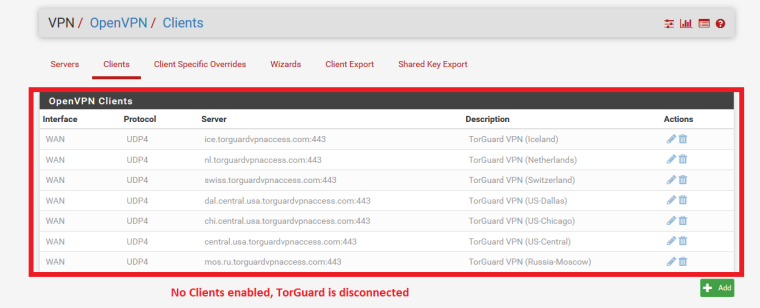
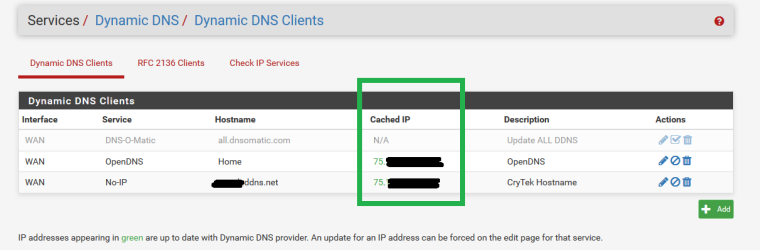
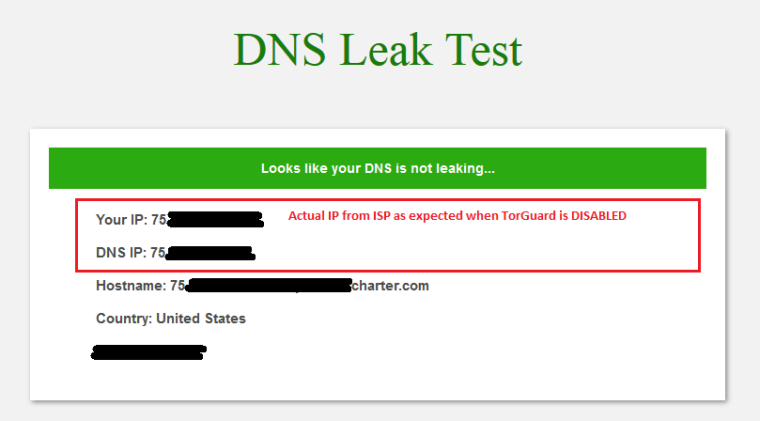
Here is what happens when I DISABLED/DISCONNECT the TorGuard VPN
DynDNS updates correctly obviously:
And DNS result is as expected and desired:
Now here is what happens when I ENABLED one of the TorGuard VPN Client connections...(drum roll please!)
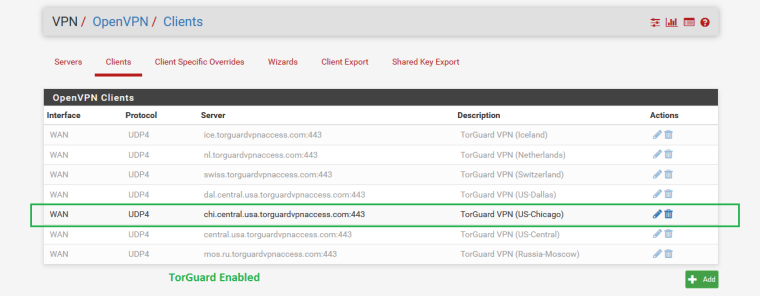
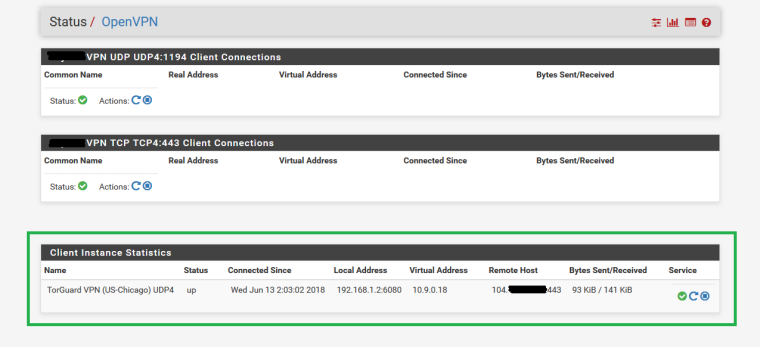
DynDNS Result is STILL actual IP as desired!!!
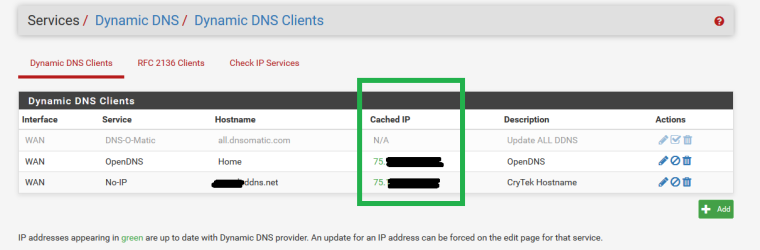
And NO DNS LEAK when TorGuard is Active!!!
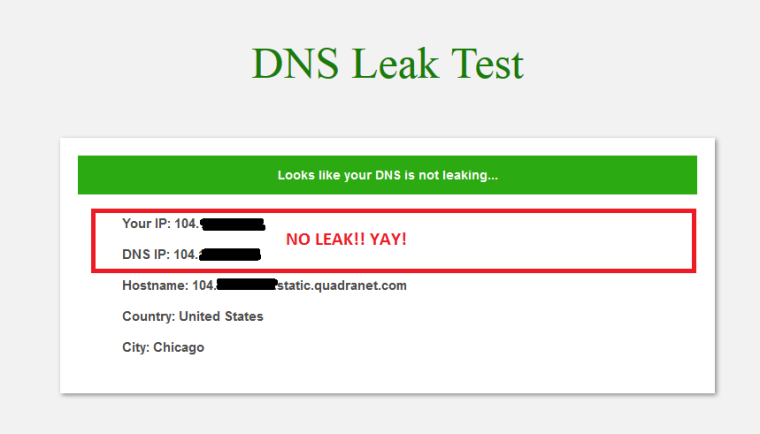
and just for a second opinion...Confirmed NO LEAKS
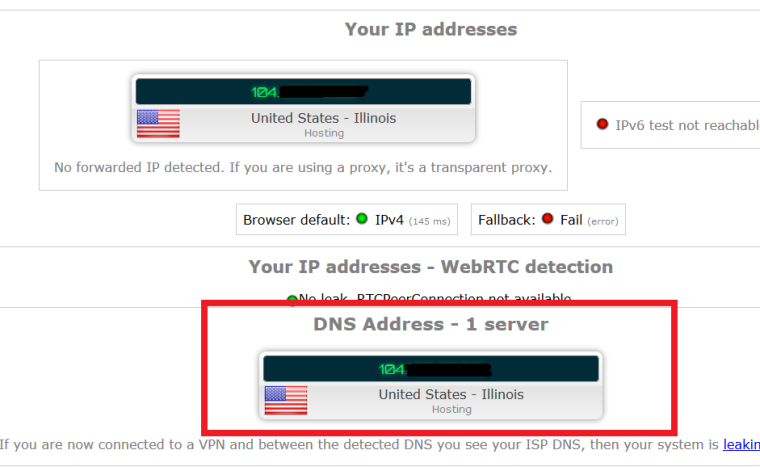
-
(NOTE: I went back an UNCHECKED the "Do Not Pull Routes" option)
I would say this issue is now resolved, thanks for throwing ideas out there with me...sometimes I'm not the brightest crayon in the box and am about as bright as a burnt out light bulb but with a little help my brain starts to rattle a bit and eventually bounces onto a good idea or two haha
but with a little help my brain starts to rattle a bit and eventually bounces onto a good idea or two hahaThanks again for the help!