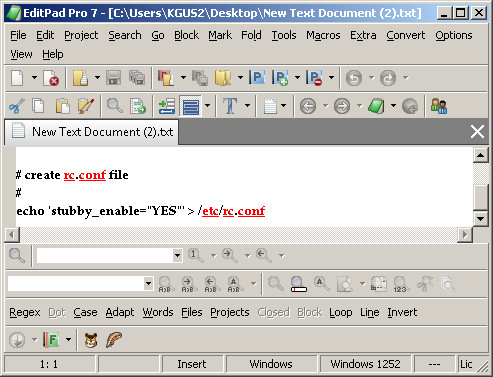
* SOLUTION POSTED* DNS TLS GETDNS/STUBBY From pfsense/FreeBSD-ports
-
here is the another tool which you have just missed http://www.vpninsights.com/dns-leak-test instead of ExpressVPN tool, its misleading users.
-
Dear kevrichards,
Hello and thanks for the heads up. I will replace ExpressVPN tool with the tool you cited:http://www.vpninsights.com/dns-leak-test
I am just curious - were you able to follow this tutorial and get everything working? I would appreciate any additional feedback you wish to share with me.
Peace and God Bless.
ubernupe aka directnupe
-
Thanks for this guide, I got it working using your instructions!
I tested my DNS on https://cmdns.dev.dns-oarc.net/
The first time testing I got a "C" - I added the lines below to unbound custom options and it went "up" to "B".
hide-identity: yes
hide-version: yes
hide-trustanchor: yes
harden-glue: yes
harden-dnssec-stripped: yes
num-threads: 2
interface-automatic: yes
msg-cache-slabs: 8m
rrset-cache-slabs: 8m
infra-cache-slabs: 8m
key-cache-slabs: 8m
rrset-cache-size: 256m
msg-cache-size: 128m
so-rcvbuf: 1m
unwanted-reply-threshold: 10000
val-clean-additional: yes
use-caps-for-id: yes
do-ip6: no
do-ip4: yes
do-tcp: yes
minimal-responses: yes
prefetch: yes
qname-minimisation: yes
qname-minimisation-strict: yes
rrset-roundrobin: yes
target-fetch-policy: "0 0 0 0 0" -
@actionhenk
Thanks for your feedback and I am glad that you got this ( DNS OVER TLS ) working on Pfsense. I have applied your tweaks in order to improve my cache performance.
Thanks for that insight and input on that front.
Also you will always get a " B " if you do not have IPV6 enabled and resolving on your Pfsense Firewall. I was getting a " B " on https://cmdns.dev.dns-oarc.net/ prior to using your tweaks due to my not allowing IPV6.
I was concerned about my instructions being clear enough - so again thanks.Peace,
ubernupe
-
Just wanted to thank you for the guide. I was able to follow along well enough (there were a few tangents that interrupt the flow of things) with the little experience I have as a hobbyist. It seems to be working beautifully. For reference, using DNS over TLS with Unbound directly resulted in uncached lookups of: Min .284 Max 1.080 Avg .485. With Stubby it went down to a highly respectable: Min .027 Max .259 Avg .072. The worst part with unbound was loading a resource that incorporated other domains resulting in several lookups occuring back-to-back as the page loaded, really bogging things down (compared to standard DNS). I am currently only using IPv4 in this implementation, but will eventually setup v6.
-
@gorlilla
I am glad to hear that you were able to get this up and running. Also, I truly appreciate your feedback and thanks. We are all in this together and when you get some time -check out some or all of the videos linked at the top of this post. The DNS Privacy Team are very serious and dedicated people and truly very skilled and adept in their mission to keep us all safe while using the web. They are the real heroes - I was just glad to be able to pass on what I learned. God's Speed- AlwaysIn Peace,
ubernupe -
I am running into a small issue, mayb you have also noticed. In pfsense development version 2.4-4 there is an option to show DNS resolver status and it shows a response status of the DNS running, in this case stubby. It is running locally however I am seeing pings between 150 and 250. Sometimes it spikes up to 5000+ and unfortunately this times out resolving.
I think its strange to have such a high ping to a locally running service.
Have you also run into this issue ? If so, were you able to solve it ?
-
@actionhenk
I am running the stable branch of PfSense - 2.4.3- However, I will setup 2.4.4 on a VM and test it out and get back to you like tomorrow.
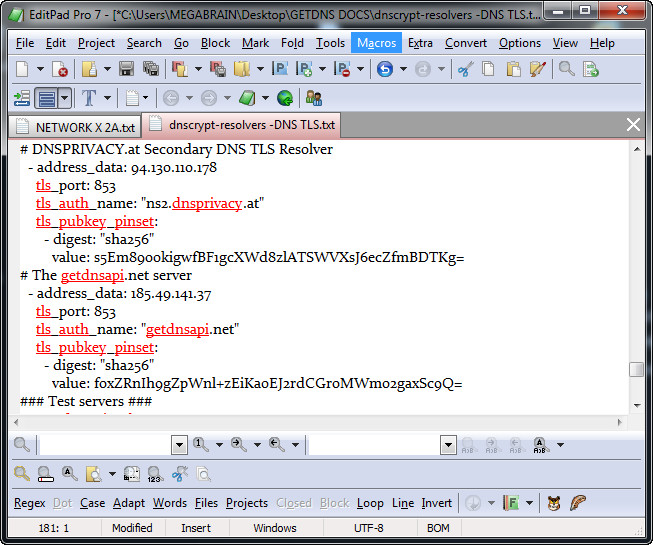
I will ask what resolvers are configured in your /usr/local/etc/stubby/stubby.yml file?
check here for my recommended resolvers in my answer to nikkon who asks a similar question to yours:
https://forum.opnsense.org/index.php?topic=8759.0 -
Below is the stubby config im using.
resolution_type: GETDNS_RESOLUTION_STUB dns_transport_list: - GETDNS_TRANSPORT_TLS tls_authentication: GETDNS_AUTHENTICATION_REQUIRED dnssec_return_status: GETDNS_EXTENSION_TRUE tls_query_padding_blocksize: 256 edns_client_subnet_private : 1 idle_timeout: 60000 listen_addresses: - 172.28.57.252@8069 dnssec_trust_anchors: "/usr/local/etc/unbound/root.key" round_robin_upstreams: 1 upstream_recursive_servers: # cloudflare1 - address_data: 1.1.1.1 tls_port: 853 tls_auth_name: "cloudflare-dns.com" tls_pubkey_pinset: - digest: "sha256" value: yioEpqeR4WtDwE9YxNVnCEkTxIjx6EEIwFSQW+lJsbc= # cloudflare2 - address_data: 1.0.0.1 tls_port: 853 tls_auth_name: "cloudflare-dns.com" tls_pubkey_pinset: - digest: "sha256" value: yioEpqeR4WtDwE9YxNVnCEkTxIjx6EEIwFSQW+lJsbc= # dot.securedns.eu - HAProxy + Bind # - address_data: 146.185.167.43 # tls_port: 853 # tls_auth_name: "dot.securedns.eu" # tls_pubkey_pinset: # - digest: "sha256" # value: h3mufC43MEqRD6uE4lz6gAgULZ5/riqH/E+U+jE3H8g= # ns1.dnsprivacy.at - Unbound - address_data: 94.130.110.185 tls_port: 853 tls_auth_name: "ns1.dnsprivacy.at" tls_pubkey_pinset: - digest: "sha256" value: vqVQ9TcoR9RDY3TpO0MTXw1YQLjF44zdN3/4PkLwtEY= # ns2.dnsprivacy.at - Unbound - address_data: 94.130.110.178 tls_port: 853 tls_auth_name: "ns2.dnsprivacy.at" tls_pubkey_pinset: - digest: "sha256" value: s5Em89o0kigwfBF1gcXWd8zlATSWVXsJ6ecZfmBDTKg= # dnsovertls.sinodun.com - HAProxy + Bind 9.12 # - address_data: 145.100.185.15 # tls_port: 853 # tls_auth_name: "dnsovertls.sinodun.com" # tls_pubkey_pinset: # - digest: "sha256" # value: 62lKu9HsDVbyiPenApnc4sfmSYTHOVfFgL3pyB+cBL4= # dnsovertls1.sinodun.com - HAProxy + Bind 9.12 # - address_data: 145.100.185.16 # tls_port: 853 # tls_auth_name: "dnsovertls1.sinodun.com" # tls_pubkey_pinset: # - digest: "sha256" # value: cE2ecALeE5B+urJhDrJlVFmf38cJLAvqekONvjvpqUA= # dnsovertls2.sinodun.com - HAProxy + Bind 9.12 # - address_data: 145.100.185.17 # tls_port: 853 # tls_auth_name: "dnsovertls2.sinodun.com" # tls_pubkey_pinset: # - digest: "sha256" # value: NAXBESvpjZMnPWQcrxa2KFIkHV/pDEIjRkA3hLWogSg= # dnsovertls3.sinodun.com - HAProxy + Bind 9.12 # - address_data: 145.100.185.18 # tls_port: 853 # tls_auth_name: "dnsovertls3.sinodun.com" # tls_pubkey_pinset: # - digest: "sha256" # value: 5SpFz7JEPzF71hditH1v2dBhSErPUMcLPJx1uk2svT8= # DKG - knot # - address_data: 199.58.81.218 # tls_port: 853 # tls_auth_name: "dns.cmrg.net" # tls_pubkey_pinset: # - digest: "sha256" # value: 3IOHSS48KOc/zlkKGtI46a9TY9PPKDVGhE3W2ZS4JZo= # dns.neutopia.org - knot # - address_data: 89.234.186.112 # tls_port: 853 # tls_auth_name: "dns.neutopia.org" # tls_pubkey_pinset: # - digest: "sha256" # value: wTeXHM8aczvhRSi0cv2qOXkXInoDU+2C+M8MpRyT3OI= # getdnsapi.net - Unbound # - address_data: 185.49.141.37 # tls_port: 853 # tls_auth_name: "getdnsapi.net" # tls_pubkey_pinset: # - digest: "sha256" # value: foxZRnIh9gZpWnl+zEiKa0EJ2rdCGroMWm02gaxSc9Q= # UncensoredDNS - ? # - address_data: 89.233.43.71 # tls_port: 853 # tls_auth_name: "unicast.censurfridns.dk" # tls_pubkey_pinset: # - digest: "sha256" # value: wikE3jYAA6jQmXYTr/rbHeEPmC78dQwZbQp6WdrseEs= -
I think im looking at this wrong, this is probably ping times from stubby to the dns servers. I removed all servers except clouddns and ping is at 30 now.
-
@actionhenk
I tried to test pfsense 2.4.4 development but I can not install the damn thing to a VMware virtual machine ( or virtualbox ) for that matter.
Can you or any else give me some step by step instructions of how to achieve this?
Pfsense in all their wisdom - Netgate - has gotten rid of the CD-rom iso. I have tried many different methods - rufus - and all of that - none worked.
As far as your setup - I notice that you are using :listen_addresses:
- 172.28.57.252@8069
By default Stubby listens on 127.0.0.1 - so I do not know if this might be giving you some of the issues you cited earlier regarding ping times. Seems like if you have it listening on your Wan - that might account for the other traffic causing some level of interference.
I set up this tutorial following the guidelines which were set forth by DNS Privacy. I do not know if your deviating from these default is a good practice or not. Maybe you can give me your rationale for doing so. I would be interested in hearing your thoughts and reasons for this. I might learn something new. Thanks and Peace Unto You and Yours,ubernupe
-
You can install the latest pfsense from the iso. After the installation you can update to development version using the update menu in general. Select it from the dropdown box.
The 172 is what i use for my lan. Im not using 127.0.0.1 because i have read, not 100% sure, that pfsense will still use root hints sometimes to resolve queries on its own.
Wanted to be sure it doesnt and using the lan address allows me to uncheck the checkbox to use localhost as resolver from the general settings and change listening and outgoing interface to not include localhost, the custom option in unbind can be changed aswell (do-not-query-localhost) so it wont use localhost anymore.
I have also tested the ping times from a fresh install and its the same, so im pretty sure the ping times are to the cloud dns server.
-
@actionhenk
Thank you - and I did as you suggested and got 2.4.4 devel installed now. Also, thanks for your thoughts on using lan. I am going to research that and I did learn something ( very enlightening )- I truly appreciate youGod Bless,
ubernupe