Time is not syncing
-
@brunovic said in Time is not syncing:
@johnpoz so it looks like my outbound NAT is manually configured. How will this prevent NTP from syncing?
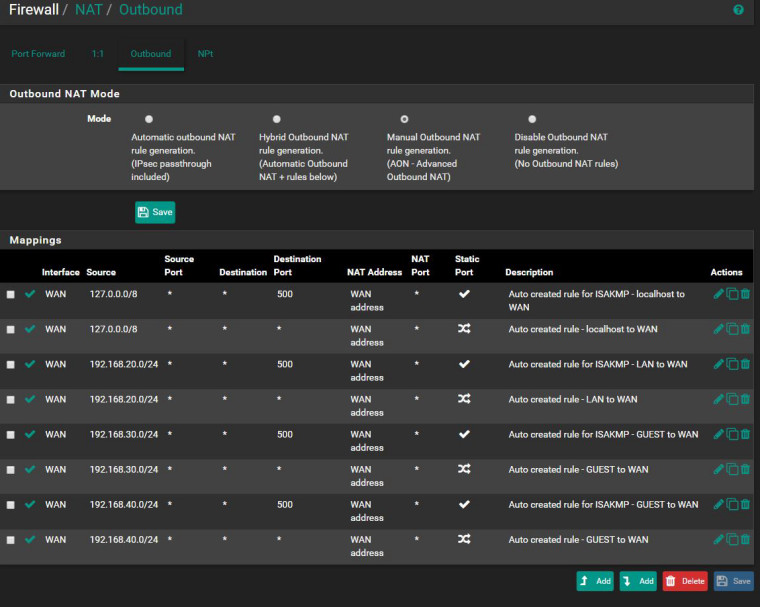
This is what you are looking for right?
-
@kpa if that is the case then why would it be listening to NTP packets on the LAN and not the WAN? That server is not on my internal network.
-
Your router can provide ntp to clients on your lan, that’s why it listens on the lan interface.
Have a look at the dhcp settings for your lan subnet.
-
Why do you have it in manual mode if all you doing is what automatic would be doing?
Where is your nat for vpn connections, your tunnel network would need to be natted? Try changing it to automatic.. You sure and the hell should not have to listen on wan to query a time server.
-
@johnpoz said in Time is not syncing:
Why do you have it in manual mode if all you doing is what automatic would be doing?
Where is your nat for vpn connections, your tunnel network would need to be natted? Try changing it to automatic.. You sure and the hell should not have to listen on wan to query a time server.
There is a reason to it. I can't remember but something was not working correctly in automatic mode.
-
Like what? Put it back.. And delete all your manual rules. You can always put it back to manual if this whatever it is comes back.. But if there is something that is not working in automatic mode that should be brought up so we can fix it, so other users using automatic don't have whatever this is issue is you think you were having.
-
@brunovic said in Time is not syncing:
There is a reason to it. I can't remember but something was not working correctly in automatic mode.
This makes me think you have some other misconfiguration as the root cause here. If your WAN is static, make sure you have a gateway set on Interfaces > WAN. And also check Interfaces > LAN and make sure you do not have a gateway set there. Same for your other local interface(s) like Guest.
-
@jimp said in Time is not syncing:
@brunovic said in Time is not syncing:
There is a reason to it. I can't remember but something was not working correctly in automatic mode.
This makes me think you have some other misconfiguration as the root cause here. If your WAN is static, make sure you have a gateway set on Interfaces > WAN. And also check Interfaces > LAN and make sure you do not have a gateway set there. Same for your other local interface(s) like Guest.
If you see my route print screen above the only quad zeros out are on the WAN interface.
-
@johnpoz said in Time is not syncing:
Like what? Put it back.. And delete all your manual rules. You can always put it back to manual if this whatever it is comes back.. But if there is something that is not working in automatic mode that should be brought up so we can fix it, so other users using automatic don't have whatever this is issue is you think you were having.
I'll keep it at manual. I am VPN into my network. If these manual routes were for that the last thing I want to to hose my own connection. All I need to know is what outbound NAT rule should I be seeing in order for NTP to work without having to select the WAN interface.
-
@brunovic said in Time is not syncing:
If you see my route print screen above the only quad zeros out are on the WAN interface.
That has nothing at all to do with what I said or why I asked. :-)
Read my message again and check the settings I mentioned.
-
@jimp said in Time is not syncing:
@brunovic said in Time is not syncing:
If you see my route print screen above the only quad zeros out are on the WAN interface.
That has nothing at all to do with what I said or why I asked. :-)
Read my message again and check the settings I mentioned.
What does the gateway setting do?
-
@brunovic said in Time is not syncing:
What does the gateway setting do?
It controls whether or not pfSense treats an interface like a "WAN" for NAT and other purposes. If you have no gateway on WAN, or a gateway set on LAN or other internal interfaces, it will confuse the code that tries to setup automatic NAT and other functions.
WANs must have a gateway selected in their interface settings (statics anyhow, dynamics will get this automatically), LANs must not have a gateway set on the interface settings.
-
Also if it helps one of the things I had to do was create rules that seperated VLAN traffic from one another. This is a bit reverse from Cisco where you have to assign VTI and create route statements before any VLAN can start talking with one another. However for pfsense the moment you create a VLAN everything is automatically routed between VLANs. I do not like that at all. All I want are the VLANs to be independant from each other and for them to get out to the internet on their own. If I want to route traffic between VLANs I should be able to opt-in not opt-out. As a result I ended making some janky solution where I created alias with all other VLAN networks but it's own and told it to go anywhere but those networks.
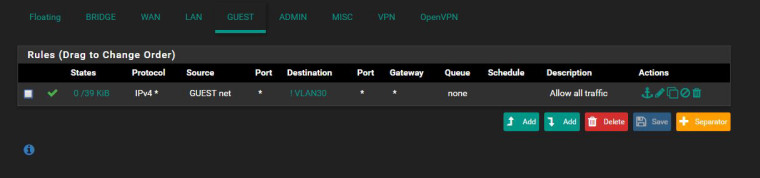
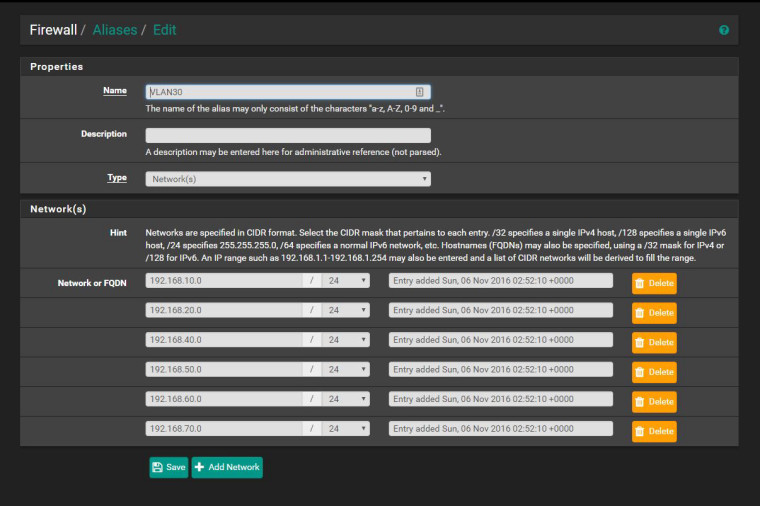
-
@brunovic said in Time is not syncing:
Also if it helps one of the things I had to do was create rules that seperated VLAN traffic from one another. This is a bit reverse from Cisco where you have to assign VTI and create route statements before any VLAN can start talking with one another. However for pfsense the moment you create a VLAN everything is automatically routed between VLANs. I do not like that at all. All I want are the VLANs to be independant from each other and for them to get out to the internet on their own. If I want to route traffic between VLANs I should be able to opt-in not opt-out. As a result I ended making some janky solution where I created alias with all other VLAN networks but it's own and told it to go anywhere but those networks.
Routing happens automatically, rules do not. They were allowed to do that because your rules allowed it. If you setup your rules properly, that won't happen. That's not related to this thread, however.
-
@jimp said in Time is not syncing:
@brunovic said in Time is not syncing:
What does the gateway setting do?
It controls whether or not pfSense treats an interface like a "WAN" for NAT and other purposes. If you have no gateway on WAN, or a gateway set on LAN or other internal interfaces, it will confuse the code that tries to setup automatic NAT and other functions.
WANs must have a gateway selected in their interface settings (statics anyhow, dynamics will get this automatically), LANs must not have a gateway set on the interface settings.
Anyways to answer your question there is no setting under the WAN interface to designate it as the gateway. And all other interface are not designated the gateway.
-
I feel like no one is talking to me like a network engineer. I never had this much difficulty trying to configure a Cisco router, firewall or switch. I may have screwed something up and I think the problem here is you guys are trying to troubleshoot my problem. I am pretty proficient enough to troubleshoot it myself. But the one answer I have not been getting it HOW exactly is the NTP communication routing? Is the NTP server sourcing the LAN interface going out the WAN or is it sending the NTP out the LAN interface. That is what is confusing me about the "interface section" under NTP Server Settings. If it is the latter then no wonder it isn't syncing because there are no NTP servers on my LAN network however IF it is the former. I have already done a ping test to the NTP server SOURCING the LAN interfaces and I got 100% replies. IF this is a NAT issued then pings would fail.
-
@brunovic said in Time is not syncing:
I feel like no one is talking to me like a network engineer. I never had this much difficulty trying to configure a Cisco router, firewall or switch. I may have screwed something up and I think the problem here is you guys are trying to troubleshoot my problem.
This isn't Cisco. And if you don't want help, I'll gladly not give it. You have precisely the kind of attitude found on a person most likely to overlook something because they think they know better, and that is why it's most important to start with the basics and work up.
NTP is UDP. UDP will follow the routing table. The interface binding controls what it binds to locally, but it still respects the routing table to find the interface it will exit from. If you bind to LAN, it will source the packets using the LAN IP address but the traffic still exits the firewall through whatever route gets it to the destination (e.g. the default route). Sourcing from the LAN and exiting WAN also means that it gets NAT applied.
On my test systems here, I can select LAN only and it still can synchronize time just fine, with otherwise stock NTP settings.
-
@jimp said in Time is not syncing:
@brunovic said in Time is not syncing:
I feel like no one is talking to me like a network engineer. I never had this much difficulty trying to configure a Cisco router, firewall or switch. I may have screwed something up and I think the problem here is you guys are trying to troubleshoot my problem.
This isn't Cisco. And if you don't want help, I'll gladly not give it. You have precisely the kind of attitude found on a person most likely to overlook something because they think they know better, and that is why it's most important to start with the basics and work up.
NTP is UDP. UDP will follow the routing table. The interface binding controls what it binds to locally, but it still respects the routing table to find the interface it will exit from. If you bind to LAN, it will source the packets using the LAN IP address but the traffic still exits the firewall through whatever route gets it to the destination (e.g. the default route). Sourcing from the LAN and exiting WAN also means that it gets NAT applied.
On my test systems here, I can select LAN only and it still can synchronize time just fine, with otherwise stock NTP settings.
I understand this is not Cisco. What I am trying to do is to get you to understand that I understand the networking basics and from a network standpoint everything looks good. Now unless there is something that has been done without my knowledge THAT is what I need to know. But I would not set the internal interfaces to be the gateway because I know that will break network traffic. I've already confirmed this with you when I checked the LAN interface. Also IF this is a NAT issue the whole point of Network Address Translation is for internal class c addresses to source the WAN interface IP for external traffic. As I've demonstrated when sourcing the LAN interface IP I am able to ping the NTP server. If NAT was not working properly I should not be able to ping the NTP server from the LAN interface. So this leaves the question IF NAT is working properly and I am able to ping the NTP servers then WHY am I not able to sync with the NTP server when anything but the WAN interface is selected under the NTP Settings.
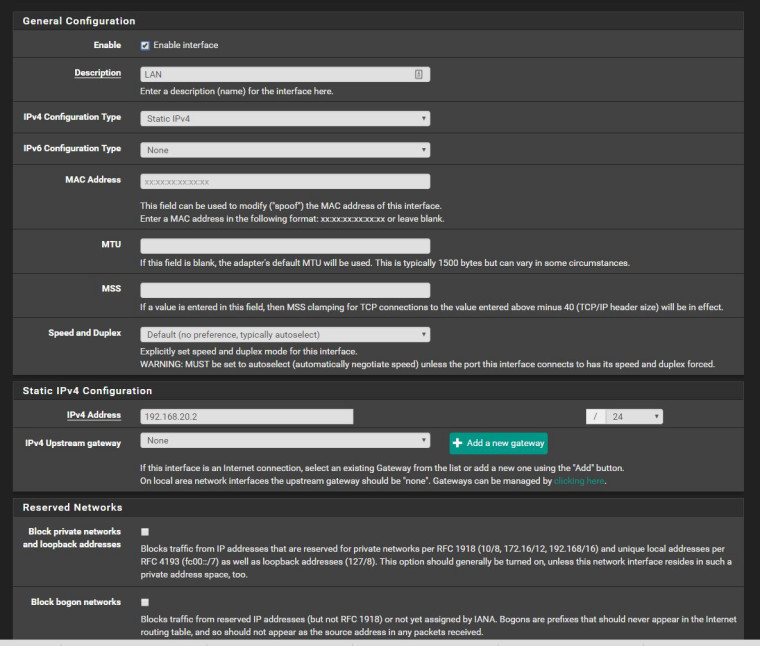
-
Boom THAT was why I had the manual NAT. Now my out-of-band management VLAN can get onto the internet and this violates DoD STIG requirements. THAT was why I was trying to keep the manual NAT. Again everything routes by default which creates THAT problem. I just need that network to be on its own separate from the rest of the networks. There are no rules on the ADMIN VLAN to allow anything so why am I able to route on the ADMIN VLAN. That was what I didn't want to do.
-
@brunovic said in Time is not syncing:
Boom THAT was why I had the manual NAT. Now my out-of-band management VLAN can get onto the internet and this violates DoD STIG requirements. THAT was why I was trying to keep the manual NAT. Again everything routes by default which creates THAT problem. I just need that network to be on its own separate from the rest of the networks. There are no rules on the ADMIN VLAN to allow anything so why am I able to route on the ADMIN VLAN. That was what I didn't want to do.
Because interface rules are checked in the inbound direction, not outbound. Through your lack of understanding of how pfSense works, you created the misconfiguration that allowed it to happen. You keep shooting your own feet and then wondering why it hurts.
You need to read through the docs more and understand how pfSense operates at a more fundamental level before ranting about how it doesn't work the way you expect. You're still applying Cisco concepts to pfSense when they do not apply at all.