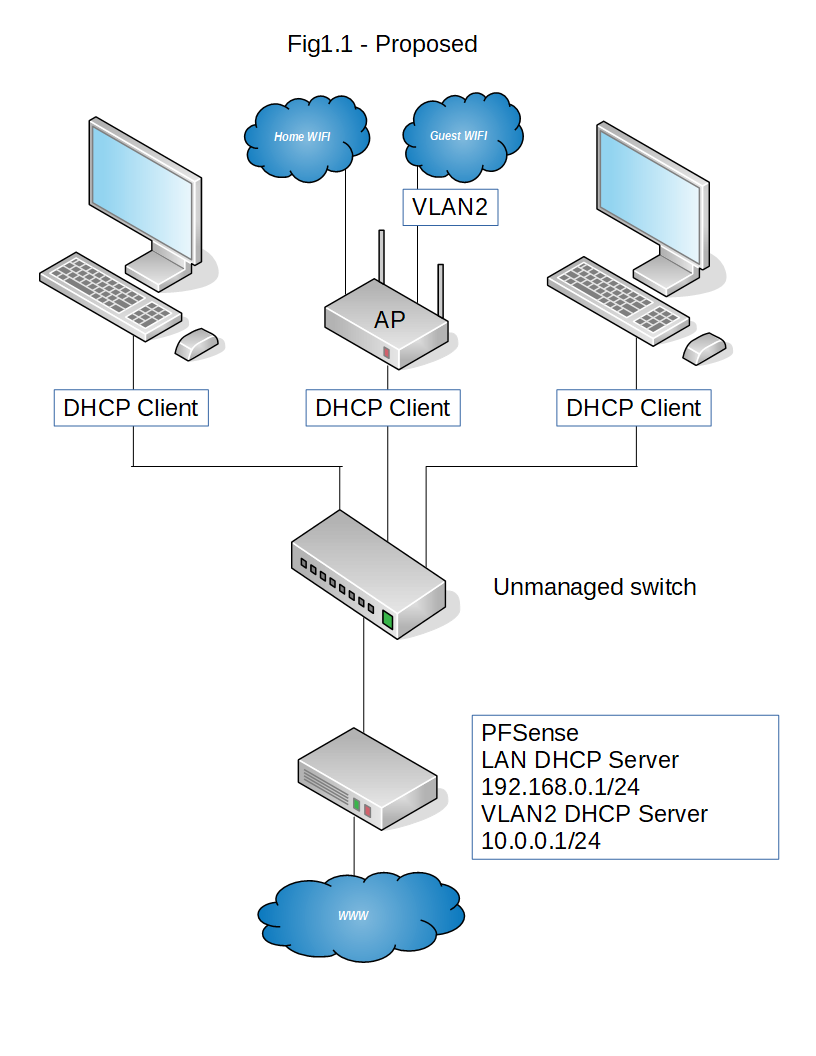
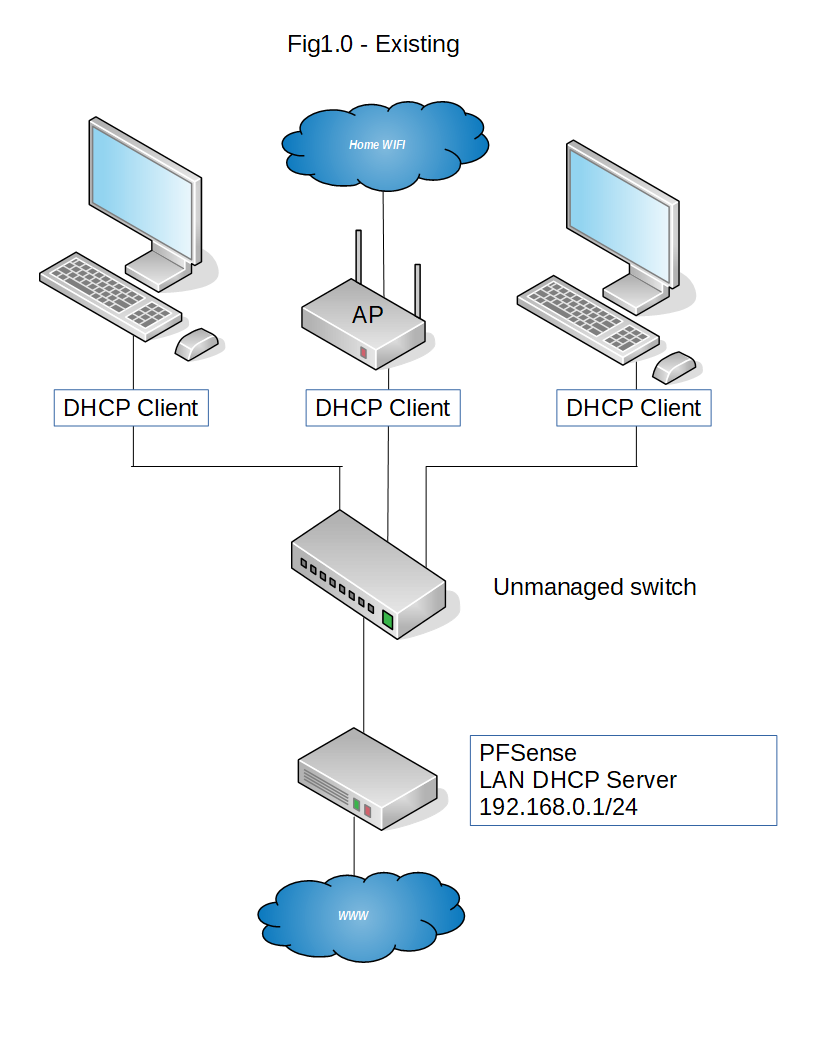
Simple VLAN for PFSense + Unifi AP-AC-LR
-
@jknott That's interesting - I'm going to go take a look at my network adapter's available settings! Thanks!
-
@bbcmodelb said in Simple VLAN for PFSense + Unifi AP-AC-LR:
What if the computer running pfSense hasn’t yet got the VLAN interface created? Will it ignore the packet?
Yes, it will ignore any VLAN frame that it's not configured for. For example, if you enable VLAN 10, frames for VLAN 11, 20, 3000 etc., will be ignored. Also, one feature of switches is they forward frames based on MAC addresses. If a device hasn't had traffic through a port, traffic for that device will not go through that. However, somethings, such as broadcasts will be sent to all ports or frames for a device that has yet to be learned about by the switch. Bottom line, devices are unlikely to see many VLAN frames that's they're not configured for.
-
In your case the AP will be doing the tagging of the packets coming from the guest Wi-Fi.
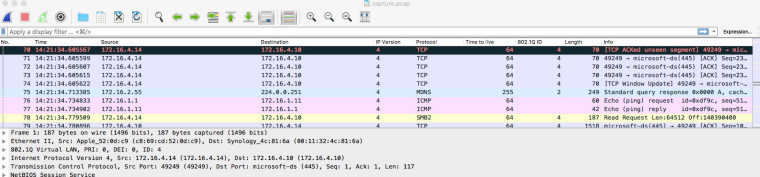
If you do a packet capture using tcdpump on eth0 you'll see tagged and untagged packets.
ssh admin@ap-1 'tcpdump -i eth0 src not 172.16.2.20 and dst not 172.16.2.20 -w -' > ~/capture.pcap
Where 172.16.2.20 is the device i'm sshing from.
-
Ah, thats interesting, so I can actually view the tagged / untagged traffic - thanks for the info
-
Yes you need to find a packet with a vlan id in and add it as a column or create a new column and set it as follows:-
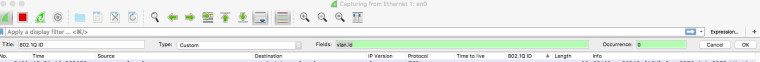
-
@bbcmodelb said in Simple VLAN for PFSense + Unifi AP-AC-LR:
Ah, thats interesting, so I can actually view the tagged / untagged traffic - thanks for the info
Yep, Wireshark is a very useful tool for understanding network issues. For example, by looking at that capture, you can see it's an Ethernet II (also known as DIX) frame, which is 1 of 2 types, the other being IEEE 802.3. The only significant difference between them is the Ethertype/length field I mentioned. If it's 1500 or less, it's the size of the data carried by the frame. If 1536 or more, it's Ethertype, which describes the payload type. In this example, a VLAN frame. When you have Wireshark running, you can expand the fields to see the actual contents. If 802.3 length, then it imposes a hard limit of 1500 bytes, which many incorrectly assume to be the maximum IP MTU. However, IP uses Ethernet II, which has no length limit and, in fact, up to 65K MTU is supported, provided layer 2 supports it. Way back in the dark ages, the hardware limited the frame size to 1518 bytes, which meant there wasn't room for both a VLAN tag and full 1500 byte MTU. However, that limit was removed 20 years ago with frame expansion, so no modern hardware should have a problem with VLAN tags.
BTW, pfSense includes "Packet Capture", which can be used to capture frames. However, it doesn't display as much as Wireshark, so you may want to capture with Packet Capture and then download the capture to view with Wireshark.
-
Hmmm, I've implemented a solution using unmanaged switches, and connected my smartphone to the new GUEST wifi, where the pfsense box IS giving it the correct IP address 10.0.0.x, but when I try to access a website, nothings appearing almost as if its a firewall / nat issue?
pfSense box config
interfaces > interfaces assignments > vlans > add >
tag, 2
parent interface, em3 (lan)
priority, 0interfaces > interfaces assignements > add >
description, GUEST
ipv4 config, static
ipv4 addr, 10.0.0.1
upstream gateway, nonefirewall > nat > outbound > add
10.0.0.0 / 24
src * dest *
Nat address, Wan Addressfirewall > rules > add
source, GUEST address
dest *
gateway WAN_DHCP
passservices > DHCP server > GUEST
scope 10.0.0.10 - 10.0.0.254Anything I've missed?
-
FOUND IT!!!
firewall > rules > add
source, GUEST address
dest *
gateway WAN_DHCP
passshould be
firewall > rules > add
source, GUEST net
dest *
gateway WAN_DHCP
pass -
Thanks for all your help guys, you were great!
-
@bbcmodelb said in Simple VLAN for PFSense + Unifi AP-AC-LR:
Thanks for all your help guys, you were great!
You may want to fire up Wireshark or Packet capture, so that you can see all the things you learned in action. A couple of years ago, I bought a cheap managed switch, configured for port mirroring, so that I could watch any connection. I could, for example, insert it between the AP and switch or pfSense and switch.
-
You may also want to put a block above your pass rule to block the home network access from the guest network , something like :-
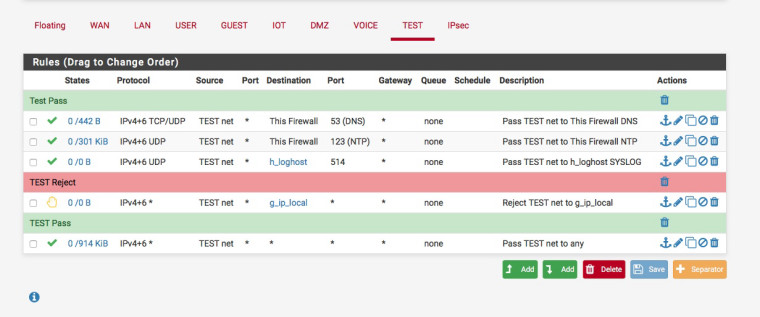
g_ip_local is an alias that contains IPv4 & IPv6 local subnets.
-
@jknott said in Simple VLAN for PFSense + Unifi AP-AC-LR:
@bbcmodelb said in Simple VLAN for PFSense + Unifi AP-AC-LR:
Thanks for all your help guys, you were great!
You may want to fire up Wireshark or Packet capture, so that you can see all the things you learned in action. A couple of years ago, I bought a cheap managed switch, configured for port mirroring, so that I could watch any connection. I could, for example, insert it between the AP and switch or pfSense and switch.
Yes, I'll do that
-
@nogbadthebad said in Simple VLAN for PFSense + Unifi AP-AC-LR:
You may also want to put a block above your pass rule to block the home network access from the guest network , something like :-

g_ip_local is an alias that contains IPv4 & IPv6 local subnets.
Will do