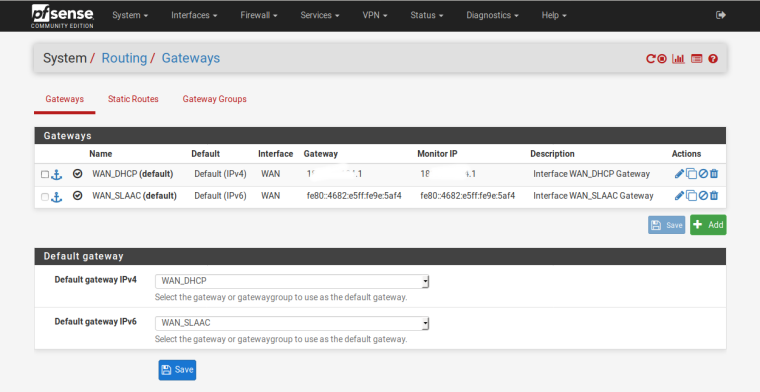
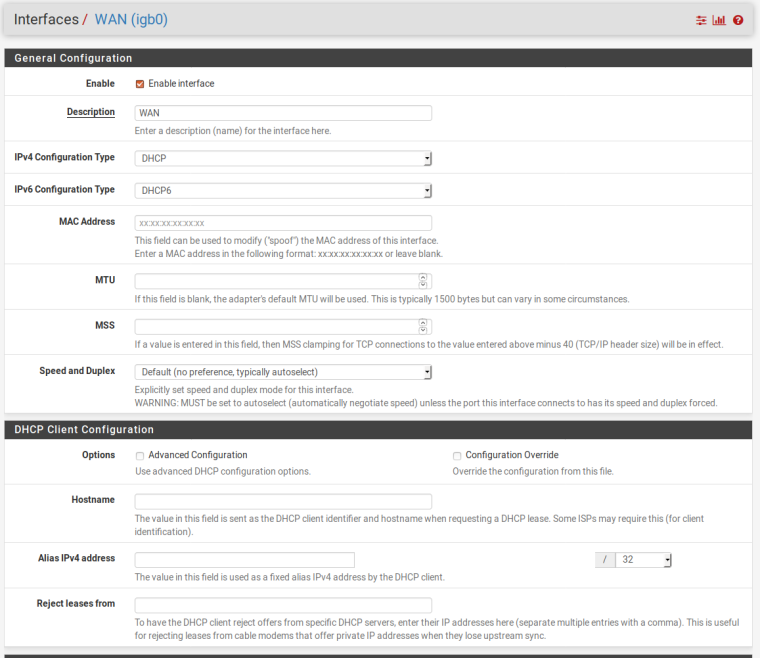
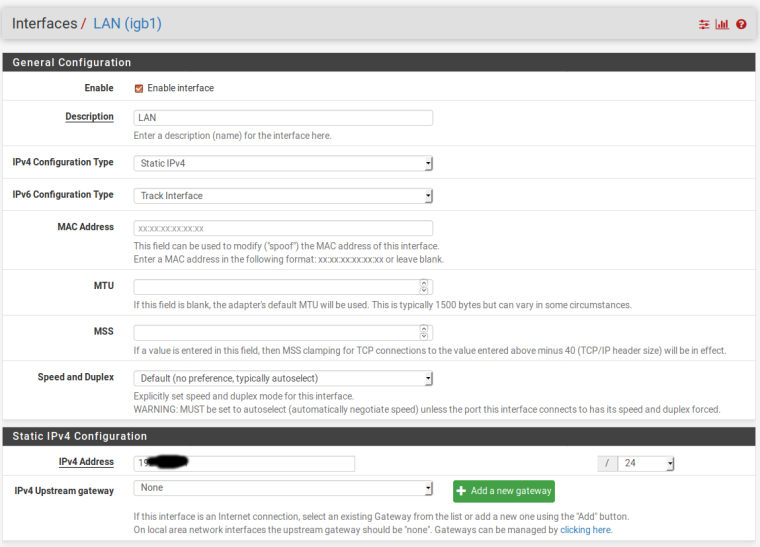
When making the update to 2.4.4 it is impossible to ping IPV6 from the WAN interface
-
@chpalmer said in When making the update to 2.4.4 it is impossible to ping IPV6 from the WAN interface:
So if mine and everyone else's works why do you think your issue is a problem caused by pfsense other than "it worked before"?
I do not understand this question. I think it is not a help, but it can be a difficulty with the interpretation of the language or culture, if not, I do not see how we move forward.
-
@fabianburpf said in When making the update to 2.4.4 it is impossible to ping IPV6 from the WAN interface:
@chpalmer said in When making the update to 2.4.4 it is impossible to ping IPV6 from the WAN interface:
So if mine and everyone else's works why do you think your issue is a problem caused by pfsense other than "it worked before"?
I do not understand this question. I think it is not a help, but it can be a difficulty with the interpretation of the language or culture, if not, I do not see how we move forward.
Im trying to reason with you. You obviously have a problem that we do not have. We cannot diagnose your issue because it does not exist for us.
Do you know how to take screen shots and post them?
-
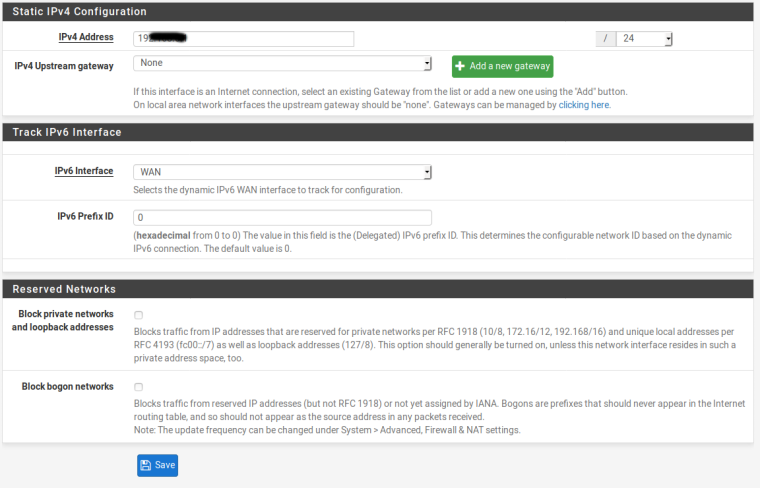
Show us this page.
-
-
@chpalmer Yes I know how to capture screens and publish them
-
@fabianburpf said in When making the update to 2.4.4 it is impossible to ping IPV6 from the WAN interface:
I get native Ipv6 through my ISP
This is what you said...
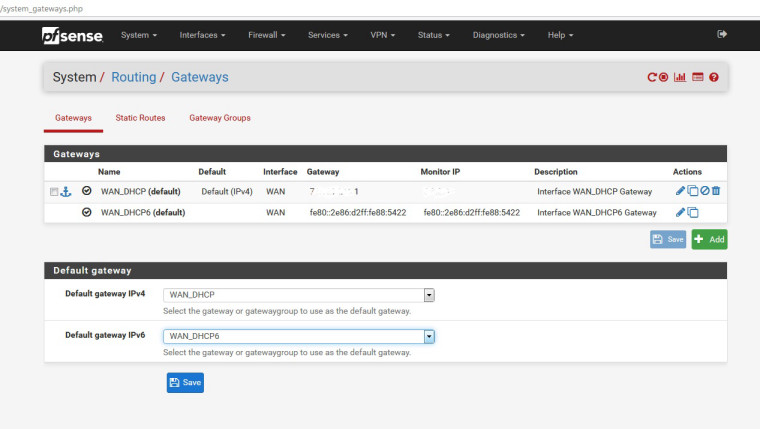
But according to your gateway your ISP is using SLAAC which is a tunneling protocol. This was important to state up front.
I do not have such a connection to test with.
-
@chpalmer Does not use SLAAC. Once I configured it that way and it stayed with that name, which I can not change from the original configuration. When performing a factory configuration, the gateway displays the correct name that is DHCP6.
-
@chpalmer said in When making the update to 2.4.4 it is impossible to ping IPV6 from the WAN interface:
I get native Ipv6 through my ISP
What I say is true
-
-
@chpalmer I do not have the slightest interest in telling lies. thanks for your help
-
@chpalmer said in When making the update to 2.4.4 it is impossible to ping IPV6 from the WAN interface:
SLAAC which is a tunneling protocol
Can you please refer me to a source that explains your say?
-
@fabianburpf said in When making the update to 2.4.4 it is impossible to ping IPV6 from the WAN interface:
@chpalmer said in When making the update to 2.4.4 it is impossible to ping IPV6 from the WAN interface:
SLAAC which is a tunneling protocol
Can you please refer me to a source that explains your say?
Looks like I remembered wrong. Doesn't matter though if your not using it.
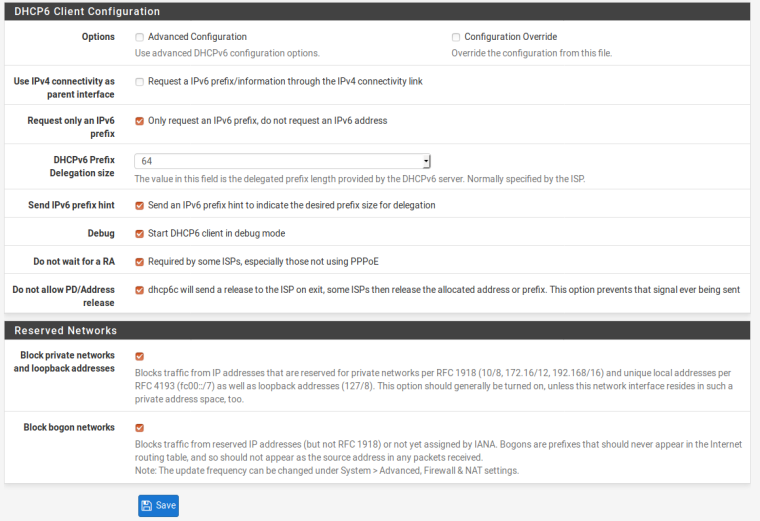
On your WAN page.. go down to DHCP6 Client Configuration.. Can you uncheck "only request an IPv6 prefix, do not request an IPv6 address" and try again..
-
@chpalmer I did it now and the result was that ipv6 address was lost in LAN and WAN
-
With a prefix of 64 you can only have global IPv6 addresses on one Interface, either WAN or LAN. If you want to have them on both you need a smaller prefix like 56.
-
@grimson Thank you for your contribution. With that configuration you get ipv6 address in wan and in lan, under Pfsense 2.4.4 there is no ping from wan, yes from LAN. With the same configuration in Pfsense 2.4.3_p1 and earlier, I got ipv6 address in wan and in lan and I could also do piing from wan and from lan
I tried your suggestion of a prefix of 56, the result was that the IPV6 address in LAN was lost. In Wan you get IPV6 address, but it does not ping.
-
@fabianburpf said in When making the update to 2.4.4 it is impossible to ping IPV6 from the WAN interface:
@nogbadthebad Please explain the packages you should capture and the way to do it. Thank you
Diagnostics -> Packet Capture
When I traceroute to the 1st & 2nd hops I get nowhere.
Am I correct in saying your in Latin America ?
Last login: Wed Nov 21 08:17:09 on console
mac-pro:~ andy$ traceroute6 2800:bf0:9fff:f100::1
traceroute6 to 2800:bf0:9fff:f100::1 (2800:bf0:9fff:f100::1) from 2a02:xxxx:xxxx:2::14, 64 hops max, 12 byte packets
1 pfsense-user 1.950 ms 1.806 ms 1.812 ms
2 * * *
^C
mac-pro:~ andy$ traceroute6 2800:bf0:9fff:f110::1
traceroute6 to 2800:bf0:9fff:f110::1 (2800:bf0:9fff:f110::1) from 2a02:xxxx:xxxx:2::14, 64 hops max, 12 byte packets
1 pfsense-user 1.998 ms 1.769 ms 1.782 ms
2 * * *
^C
mac-pro:~ andy$ -
@chpalmer said in When making the update to 2.4.4 it is impossible to ping IPV6 from the WAN interface:
But according to your gateway your ISP is using SLAAC which is a tunneling protocol
SLAAC is not a tunneling protocol. It's the usual way IPv6 works on a LAN to assign prefix and default route.
-
Can't help but... Puh. @fabianburpf please keep in mind that everyone here is a kind voluntary helping you. This is not a paid service and even with paid service you should have more understanding that a answer can take some time...
-
@nogbadthebad Thanks for your accuracy. Yes, from South America. I put the output on the screen of the packet capture, I have the file and I have opened it in wireshark, but I would not like to expose my ip the world. Could be shared by internal or look for something specific in wireshark if it is explained please.
1 2800:bf0:9fff:f100::1 2.548 ms 2.218 ms 3.026 ms
2 fc00:0:0:600::1 1.681 ms 1.596 ms 1.445 ms
3 * * *
4 * * *
5 * * *
6 * * *
7 * * *
8 * * *
9 * * *
10 * * *
11 * * *
12 * * *
13 * * *
14 * * *
15 * * *
16 * * *
17 * * *
18 * * *07:27:06.813502 ARP, Request who-has 186.3.148.114 tell 186.3.148.1, length 46
07:27:06.813641 ARP, Request who-has 186.3.148.117 tell 186.3.148.1, length 46
07:27:07.113379 IP6 fe80::21b:21ff:fe36:8838 > fe80::4682:e5ff:fe9e:5af4: ICMP6, echo request, seq 6215, length 8
07:27:07.115516 IP6 fe80::4682:e5ff:fe9e:5af4 > fe80::21b:21ff:fe36:8838: ICMP6, echo reply, seq 6215, length 8
07:27:07.176381 IP 181.xxx.xxx.xx > 181.xxx.xxx.1: ICMP echo request, id 58440, seq 6159, length 8
07:27:07.178665 IP 181.xxx.xxx.1 > 181.xxx.xxx.xx: ICMP echo reply, id 58440, seq 6159, length 8
07:27:07.446205 ARP, Request who-has 181.199.122.186 tell 181.199.122.161, length 46
07:27:07.645626 IP6 fe80::21b:21ff:fe36:8838 > fe80::4682:e5ff:fe9e:5af4: ICMP6, echo request, seq 6216, length 8
07:27:07.647823 IP6 fe80::4682:e5ff:fe9e:5af4 > fe80::21b:21ff:fe36:8838: ICMP6, echo reply, seq 6216, length 8
07:27:07.708603 IP 181.xxx.xxx.xx > 181.xxx.xxx.1: ICMP echo request, id 58440, seq 6160, length 8
07:27:07.710832 IP 181.xxx.xxx.1 > 181.xxx.xxx.xx: ICMP echo reply, id 58440, seq 6160, length 8
07:27:07.746682 IP 181.xxx.xxx.xx.56353 > 164.73.227.4.123: UDP, length 48
07:27:07.997758 IP 164.73.227.4.123 > 181.xxx.xxx.xx.56353: UDP, length 48
07:27:08.070013 IP 181.xxx.xxx.xx.23758 > 185.61.149.247.8080: tcp 543
07:27:08.177896 IP6 fe80::21b:21ff:fe36:8838 > fe80::4682:e5ff:fe9e:5af4: ICMP6, echo request, seq 6217, length 8
07:27:08.180019 IP6 fe80::4682:e5ff:fe9e:5af4 > fe80::21b:21ff:fe36:8838: ICMP6, echo reply, seq 6217, length 8
07:27:08.211401 IP 181.xxx.xxx.xx > 181.xxx.xxx.1: ICMP echo request, id 58440, seq 6161, length 8
07:27:08.213577 IP 181.xxx.xxx.1 > 181.xxx.xxx.xx: ICMP echo reply, id 58440, seq 6161, length 8
07:27:08.264519 IP 185.61.149.247.8080 > 181.xxx.xxx.xx.23758: tcp 0
07:27:08.451285 ARP, Request who-has 181.199.122.172 tell 181.199.122.161, length 46
07:27:08.475740 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 0
07:27:08.507132 IP 181.xxx.xxx.xx.38459 > 156.154.70.22.53: UDP, length 58
07:27:08.507570 IP 181.xxx.xxx.xx.14096 > 129.250.35.250.53: UDP, length 58
07:27:08.568845 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 0
07:27:08.573122 IP 129.250.35.250.53 > 181.xxx.xxx.xx.14096: UDP, length 216
07:27:08.573325 IP 181.xxx.xxx.xx.16882 > 156.154.70.22.53: UDP, length 74
07:27:08.576859 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 0
07:27:08.576871 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 214
07:27:08.606145 IP 156.154.70.22.53 > 181.xxx.xxx.xx.38459: UDP, length 169
07:27:08.606329 IP 181.xxx.xxx.xx.22780 > 156.154.70.22.53: UDP, length 74
07:27:08.669991 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:08.670024 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:08.670041 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:08.670083 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1265
07:27:08.673056 IP 156.154.70.22.53 > 181.xxx.xxx.xx.16882: UDP, length 176
07:27:08.673293 IP 181.xxx.xxx.xx.28889 > 129.250.35.250.53: UDP, length 66
07:27:08.676331 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 0
07:27:08.676343 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 0
07:27:08.690703 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 93
07:27:08.705025 IP 156.154.70.22.53 > 181.xxx.xxx.xx.22780: UDP, length 126
07:27:08.705121 IP6 fe80::21b:21ff:fe36:8838 > fe80::4682:e5ff:fe9e:5af4: ICMP6, echo request, seq 6218, length 8
07:27:08.705203 IP 181.xxx.xxx.xx.6664 > 156.154.70.22.53: UDP, length 66
07:27:08.707243 IP6 fe80::4682:e5ff:fe9e:5af4 > fe80::21b:21ff:fe36:8838: ICMP6, echo reply, seq 6218, length 8
07:27:08.737922 IP 129.250.35.250.53 > 181.xxx.xxx.xx.28889: UDP, length 132
07:27:08.738023 IP 181.xxx.xxx.xx > 181.xxx.xxx.1: ICMP echo request, id 58440, seq 6162, length 8
07:27:08.740206 IP 181.xxx.xxx.1 > 181.xxx.xxx.xx: ICMP echo reply, id 58440, seq 6162, length 8
07:27:08.782830 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 51
07:27:08.791498 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 1440
07:27:08.791510 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 50
07:27:08.803703 IP 156.154.70.22.53 > 181.xxx.xxx.xx.6664: UDP, length 82
07:27:08.807853 IP 181.xxx.xxx.xx.60416 > 52.114.74.45.443: tcp 0
07:27:08.828750 IP 181.xxx.xxx.xx.54991 > 156.154.70.22.53: UDP, length 49
07:27:08.829016 IP 181.xxx.xxx.xx.28423 > 129.250.35.250.53: UDP, length 49
07:27:08.883270 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 0
07:27:08.898722 IP 129.250.35.250.53 > 181.xxx.xxx.xx.28423: UDP, length 230
07:27:08.898913 IP 181.xxx.xxx.xx.35970 > 129.250.35.250.53: UDP, length 67
07:27:08.927912 IP 156.154.70.22.53 > 181.xxx.xxx.xx.54991: UDP, length 183
07:27:08.928089 IP 181.xxx.xxx.xx.24595 > 129.250.35.250.53: UDP, length 67
07:27:08.961641 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:08.961654 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:08.961663 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:08.961672 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:08.961692 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:08.961704 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:08.961712 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:08.961721 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:08.961740 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:08.961751 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:08.961760 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:08.963040 IP 129.250.35.250.53 > 181.xxx.xxx.xx.35970: UDP, length 199
07:27:08.963165 IP 181.xxx.xxx.xx.22772 > 129.250.35.250.53: UDP, length 70
07:27:08.976321 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 0
07:27:08.976333 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 0
07:27:08.976343 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 0
07:27:08.976353 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 0
07:27:08.981977 IP 52.114.74.45.443 > 181.xxx.xxx.xx.60416: tcp 0
07:27:08.995481 IP 129.250.35.250.53 > 181.xxx.xxx.xx.24595: UDP, length 149
07:27:08.995694 IP 181.xxx.xxx.xx.14894 > 156.154.70.22.53: UDP, length 70
07:27:09.027279 IP 129.250.35.250.53 > 181.xxx.xxx.xx.22772: UDP, length 178
07:27:09.027463 IP 181.xxx.xxx.xx.28988 > 129.250.35.250.53: UDP, length 64
07:27:09.067648 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:09.067670 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:09.067686 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:09.067702 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:09.067740 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:09.067749 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:09.067844 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:09.067854 IP 52.184.162.170.443 > 181.xxx.xxx.xx.44856: tcp 1460
07:27:09.093287 IP 129.250.35.250.53 > 181.xxx.xxx.xx.28988: UDP, length 154
07:27:09.093453 IP 181.xxx.xxx.xx.46553 > 129.250.35.250.53: UDP, length 70
07:27:09.093856 IP 156.154.70.22.53 > 181.xxx.xxx.xx.14894: UDP, length 128
07:27:09.093994 IP 181.xxx.xxx.xx.27185 > 156.154.70.22.53: UDP, length 70
07:27:09.097456 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 0
07:27:09.097467 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 0
07:27:09.097478 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 0
07:27:09.097485 IP 181.xxx.xxx.xx.60416 > 52.114.74.45.443: tcp 0
07:27:09.107050 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 0
07:27:09.107067 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 0
07:27:09.107077 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 0
07:27:09.107448 IP 181.xxx.xxx.xx.44856 > 52.184.162.170.443: tcp 0 -